PowerShell History
After performing some basic enumeration, scanning the target system with PEAS resulted a PowerShell history file for the current user
*evil-winrm* ps c:\Users\henry.vinson_adm\AppData> cat Roaming/Microsoft/Windows/PowerShell/PSReadline/ConsoleHost_history.txt
$Cred = get-credential administrator
invoke-command -credential $cred -computername localhost -scriptblock {set-itemproperty -path "hklm:\SYSTEM\CurrentControlSet\Control\Lsa" lmcompatibilitylevel -Type DWORD -Value 2 -Force}The file reveals that the current user, henry.vinson_adm, had previously changed the registry value for NTLM authentication as the administrator user
Specifically, lmcompatibilitylevel, set to 2
Network Authentication
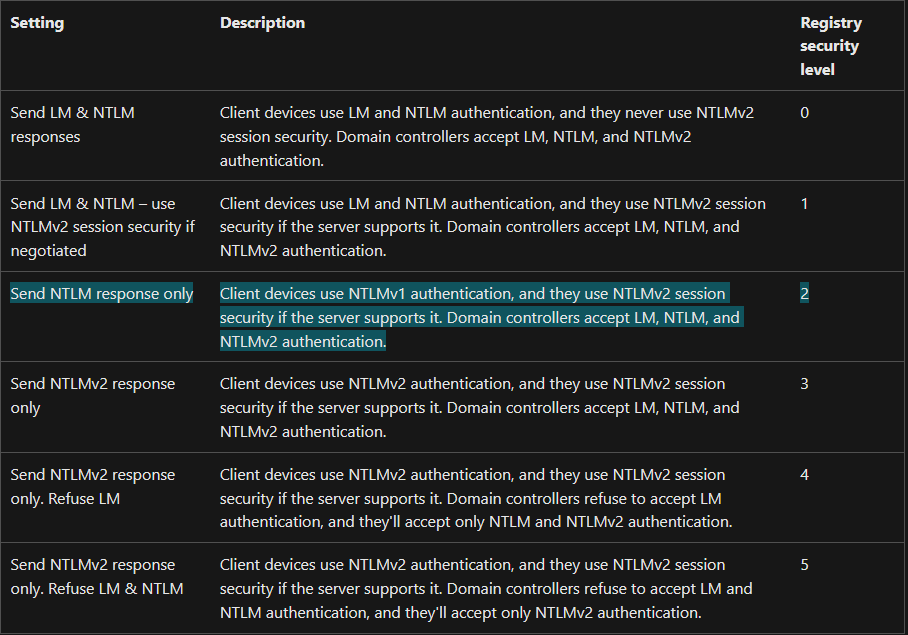 Referring to the official Microsoft documentation for the NTLM authentication reveals that the
Referring to the official Microsoft documentation for the NTLM authentication reveals that the lmcompatibilitylevel registry value set to 2 indicates the target system is configured to support authentication with the insecure NTLMv1 (or Net-NTLMv1) protocol for network authentication, which is known to be obsolete and vulnerable for cracking
This would essentially mean that I can invoke the target system to authenticate to an attacker-controlled arbitrary SMB server. The target system, as configured by the lmcompatibilitylevel registry value set to 2, would make an authentication attempt to it via the Net-NTLMv1 protocol that I can attempt to crack offline, effectively resulting a “half-way” NTLM relay attack
In order to make this work, the authentication attempt must be made with a higher privilege than the current user, henry.vinson_adm.
Thankfully, there is a good resource that list all the methods to leak NTLM hashes. Pretty much anything in the list would work, but the current system is heavily guarded by the Defender. So I will go with the Defender option as it would bypass the its own execution