Overview
- 1-Recon
- 2-Enumeration
- 3-Exploitation
- 4-Post_Enumeration
- 5-Privilege_Escalation
- attachments
Target IP
10.10.10.97
Credentials
tyler:92g!mA8BGjOirkL%OG*&(sys)
administrator:u6!4ZwgwOM#^OBf#Nwnh(sys)
some_notes
I initially gain a foothold as iis apppool\newsite because the PHP reverse shell that I remotely invoked was executed as part of a process under IIS APPPOOL/newsite.
This comes very tricky.
But then when I read about the intended route by the author, I realized that I was supposed to gain an initial foothold as thetyler user by creating an interactive shell session through a webshell. NOT through a direct PHP reverse shell.
I am writing this after gaining the SYSTEM level access to the target host. I went ahead and ran through some logs and configuration files in order to really understand the environment.
I will go side by side in depth here.
The Initial Foothold as IIS APPPOOL/newsite
┌──(kali㉿kali)-[~/archive/htb/labs/secnotes]
└─$ smbclient //$IP/new-site -U SECNOTES/tyler
Password for [SECNOTES\tyler]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Oct 28 22:31:45 2022
.. D 0 Fri Oct 28 22:31:45 2022
iisstart.htm A 696 Thu Jun 21 17:26:03 2018
iisstart.png A 98757 Thu Jun 21 17:26:03 2018
Microsoft D 0 Fri Oct 28 22:31:45 2022
shell.php A 9289 Fri Oct 28 23:32:01 2022
webshell.php A 39 Fri Oct 28 23:31:57 2022
7736063 blocks of size 4096. 3342122 blocks availableThis SMB share, \\SECNOTES.HTB\new-site, is serving of the web server running on port 8808
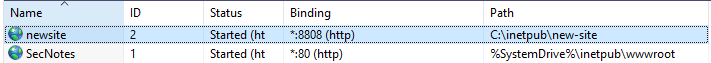 This is a screenshot taken directly from
This is a screenshot taken directly from inetmgr with the administrative level of access
As can be seen, there are 2 web servers running on the target system.
The webserver, SecNotes, the note-taking application running on the standard port 80, with its path set to C:\inetpub\wwwroot, which is the default path of the IIS installation.
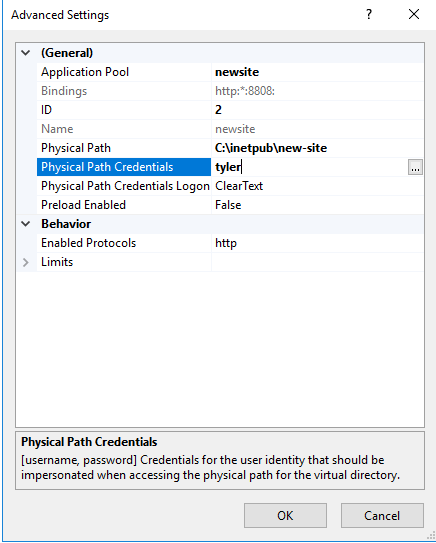 However, the other one,
However, the other one, newsite, is the one that has its path shared with the SMB share.
It also shows that it has its Physical Path Credentials bit set to the tyler user. This is super important later.
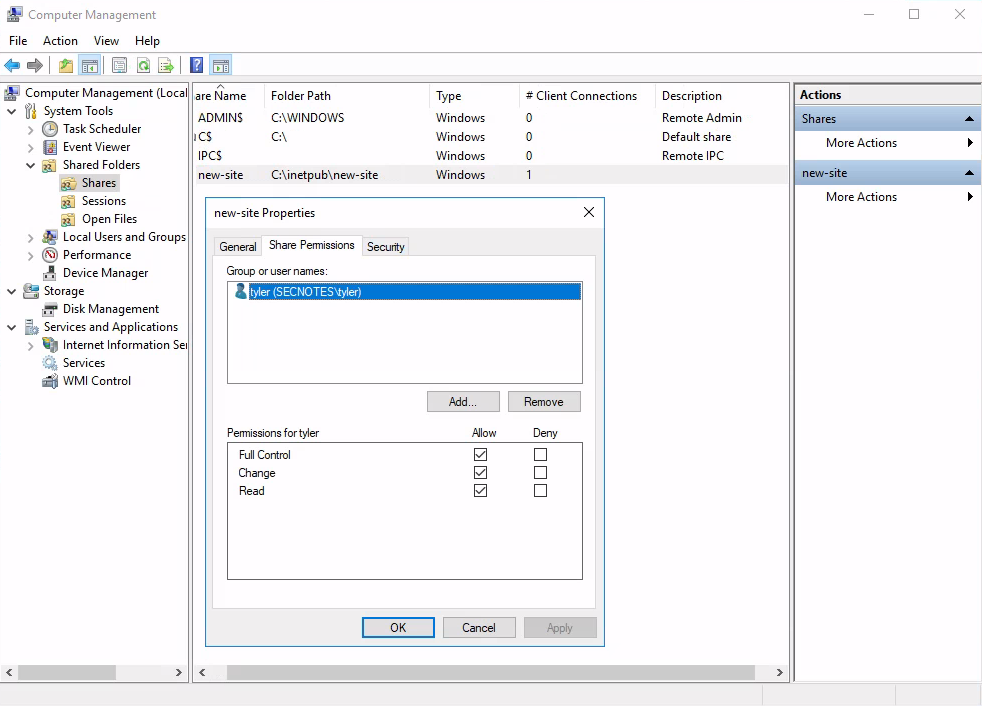 This screenshot was taken from
This screenshot was taken from compmgmt.msc to demonstrate the configuration for the system shares
The SMB share, new-site, has its Folder Path parameter set to C:\inetpub\new-site
It exactly matches the path of web server running on port 8808 above
When I check for details, the prompt pops open, showing the Share Permission, which exclusively is set to the tyler user
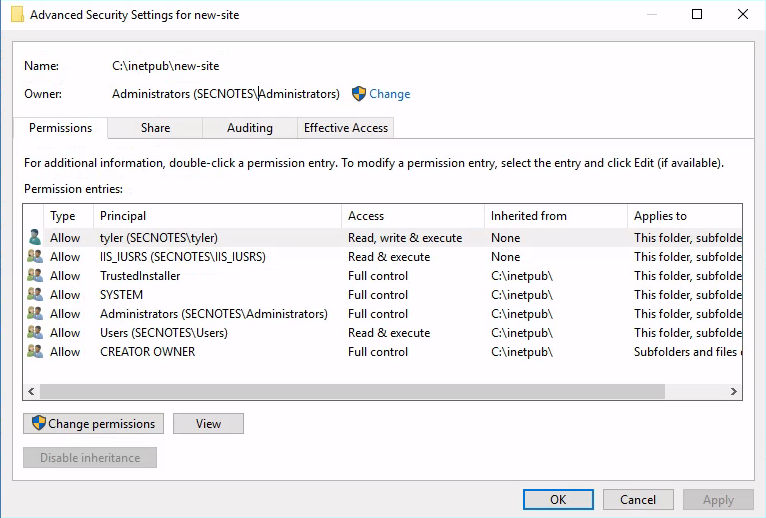 When I check for security configuration for the directory,
When I check for security configuration for the directory, C:\inetpub\new-site, the whole directory has its ownership set to the Administrators group.
These are all very much confusing as the whole newsite application of the IIS service has its ownership and permission bit set to the tyler user. However, the actual directory is owned by the Administrators group.
On top of that, the newsite directory is also a SMB share as well.
How come then when I set off the reverse shell, I get a shell as iis apppool\newsite?
The answer is in how the Windows processes work
The reason why I get the shell as the iis apppool\newsite user is because the process itself is running under that user
Processes
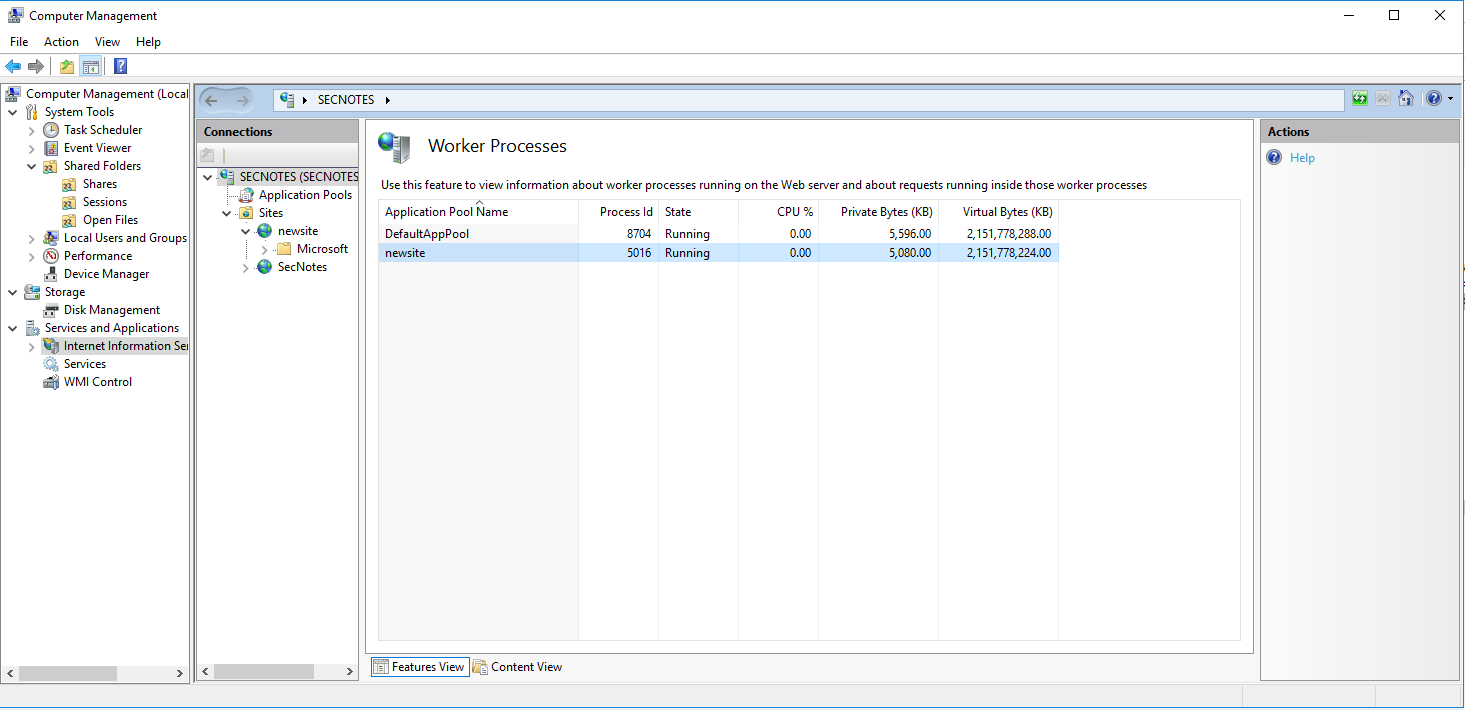 It shows that the
It shows that the newsite application of the IIS service has the PID 5016
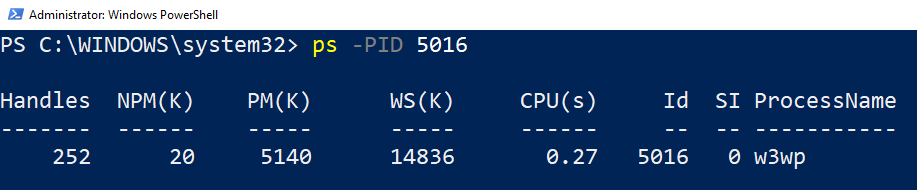 When I look up the PID via PowerShell command, it shows that the process is running as
When I look up the PID via PowerShell command, it shows that the process is running as w3wp.
w3wp.exe is the binary running the Windows IIS worker processes.
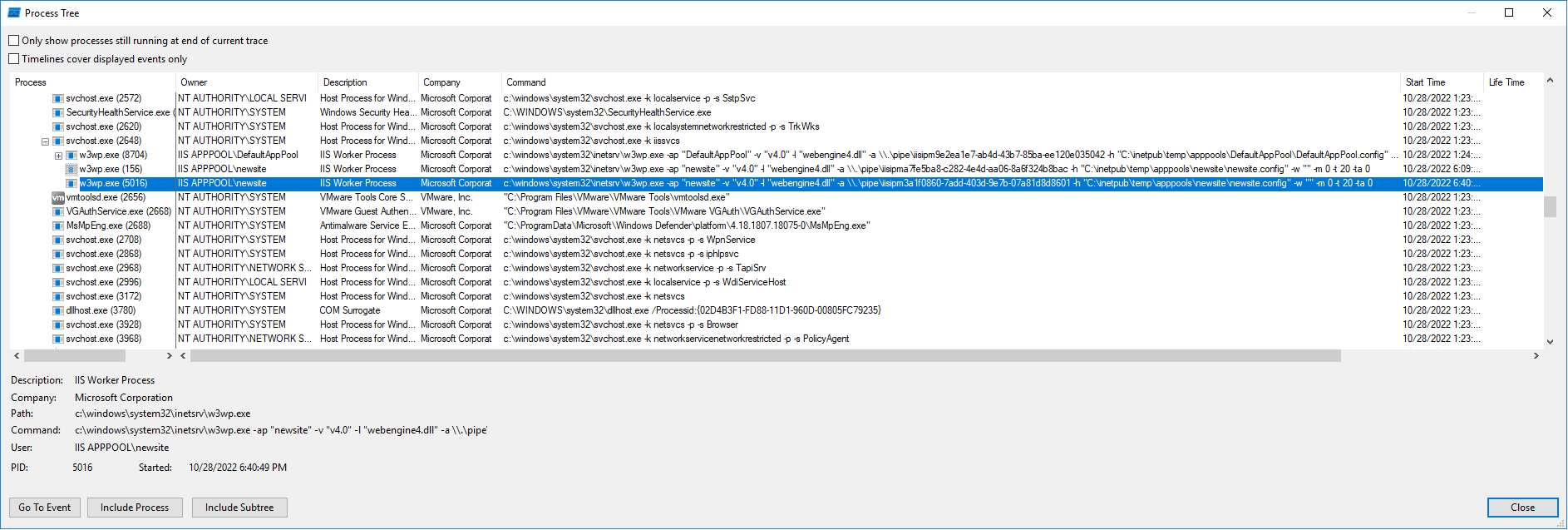
 Screenshots was taken from
Screenshots was taken from Procmon.exe
More detailed assessment is achieved via Procmon.exe.
I can clearly see that there is w3wp.exe with PID 5016 owned by IIS APPPOOL\newsite, which also has its parent process, svchost.exe with PID 2648, and there is even more to that above. It’s the services.exe with PID 624
Should I keep going? How far can this go?
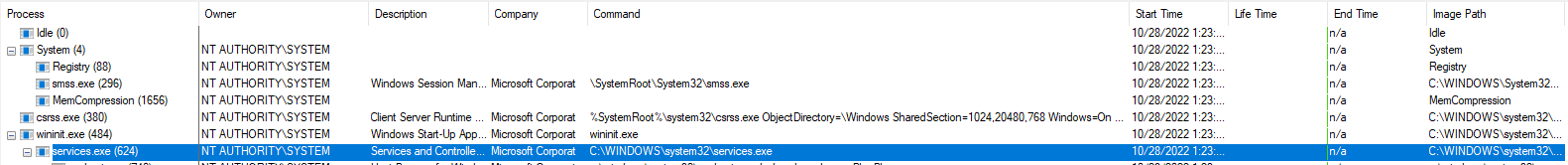
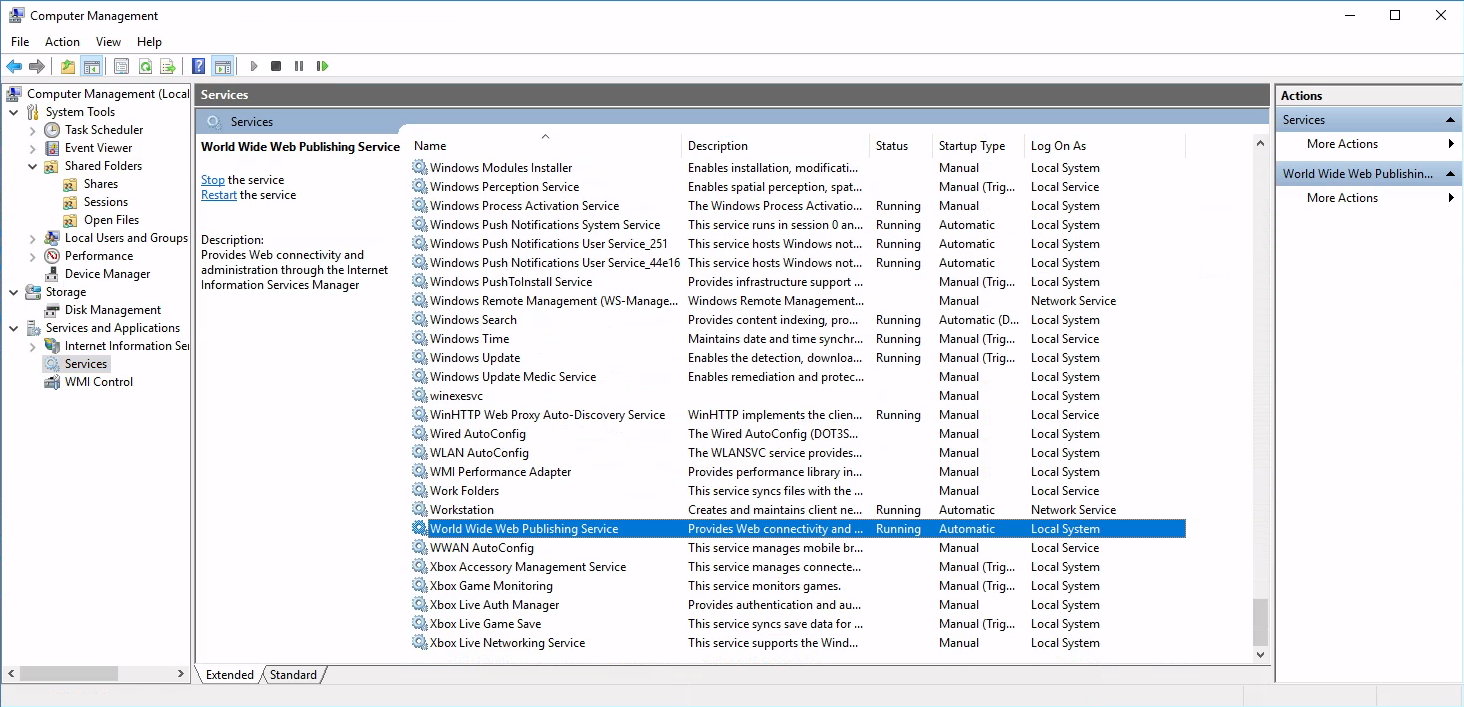 World Wide Web Publishing Service
World Wide Web Publishing Service
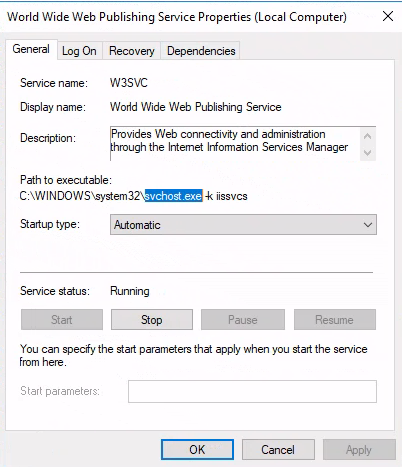 In details with its
In details with its Path to executable parameter matching that of the PID 2648 running as svchost.exe from Procmon.exe
Any parent process above the w3wp.exe is rather out-of-scope as the initial objective was to find out why I get the shell as IIS APPPOOL\newsite, but digging is fun as I get to learn more.
The PHP reverse shell that I planted and invoked remotely was executed as part of the w3wp.exe process, which was owned by and running as IIS APPPOOL\newsite.
Foothold as Tyler
┌──(kali㉿kali)-[~/archive/htb/labs/secnotes]
└─$ curl http://secnotes.htb:8808/webshell.php?cmd=whoami
secnotes\tylerThrough a PHP webshell, I get a very different result in comparison to the first initial foothold above
I am the tyler user
Why is that?
The reason is still quite unclear but it is likely due to the web shell being an active a session
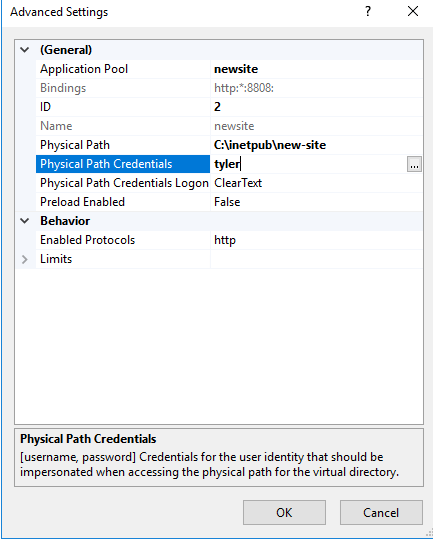 Remember earlier that there is
Remember earlier that there is Physical Path Credentials parameter set to the tyler user on the advance setting for the newsite? It’s literally written at the bottom that the set user is impersonated when accessing the physical path for the virtual directory. This is likely the reason why I get the session as tyler
It is not 100% certainty though. Just a plain half-ass educated guess.