LDAPDomainDump
┌──(kali㉿kali)-[~/…/htb/labs/forest/ldapdomaindump]
└─$ ldapdomaindump ldap://$IP:389 -u 'htb.local\svc-alfresco' -p s3rvice -n $IP --no-json --no-grep
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finishedWith a valid credential, I can now request a domain dump data with LDAPDomainDump to see the general view about the domain. A bird-eye picture view if you like.
Machine Account
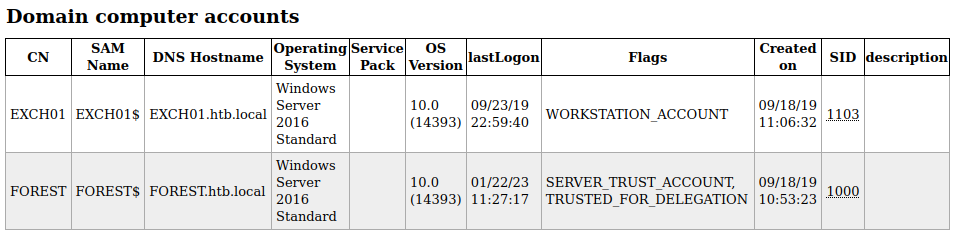 It would appear that there is another machine within the domain
It would appear that there is another machine within the domain
EXCH01.htb.local appears to be a Microsoft Exchange server
Groups
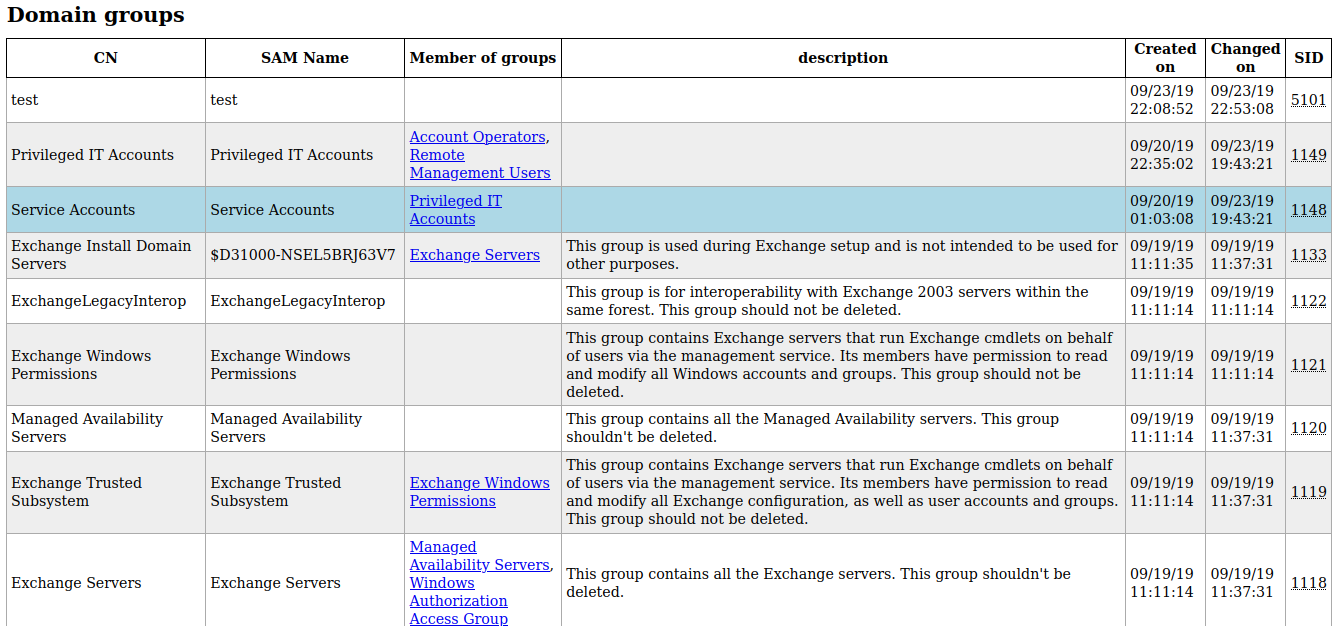 There are a lot more groups than what’s shown in the screenshot above.
The 3 groups from the top aren’t part of the installation default. They are user-created groups
I can see some other groups that are related to the Exchange server.
There are a lot more groups than what’s shown in the screenshot above.
The 3 groups from the top aren’t part of the installation default. They are user-created groups
I can see some other groups that are related to the Exchange server.
Users
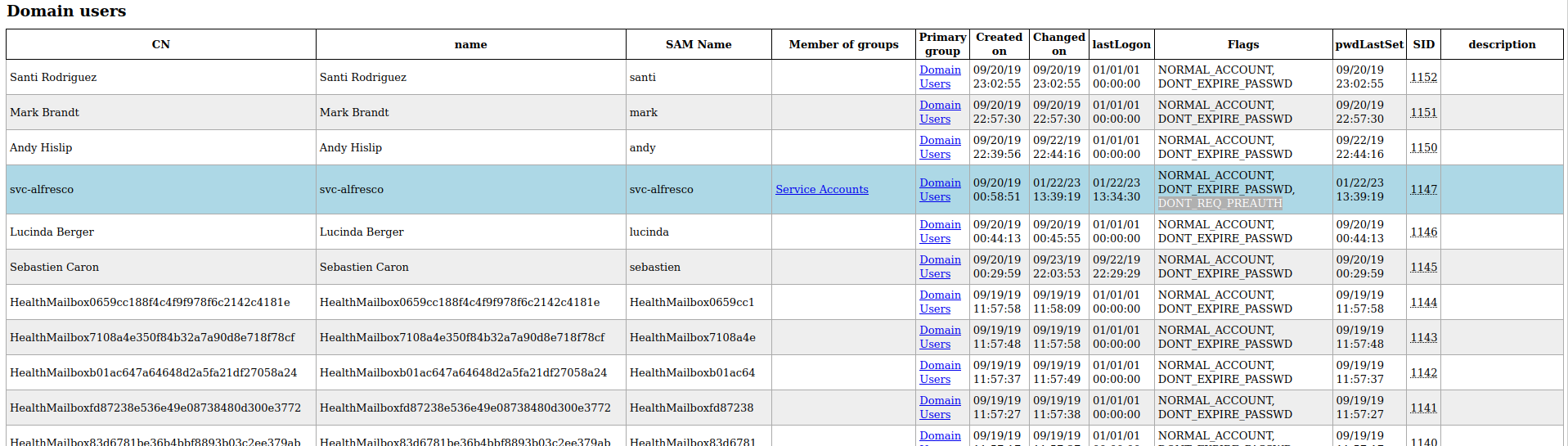 A nice list of domain users.
I can also see the
A nice list of domain users.
I can also see the svc-alfresco user with the DON'T REQ PREAUTH flag, which I exploited earlier
Those usernames starting with HealthMailbox are likely relevant to the Exchange server
 The
The$331000-VK4ADACQNUCA account turns out to be service account for the Exchange server. I was initially wondering what it was.
Now that I have seen the domain on the general term, I need to prepare for an attack route