Web
Nmap scan revealed that HttpFileServer httpd 2.3 is running on the target port 80
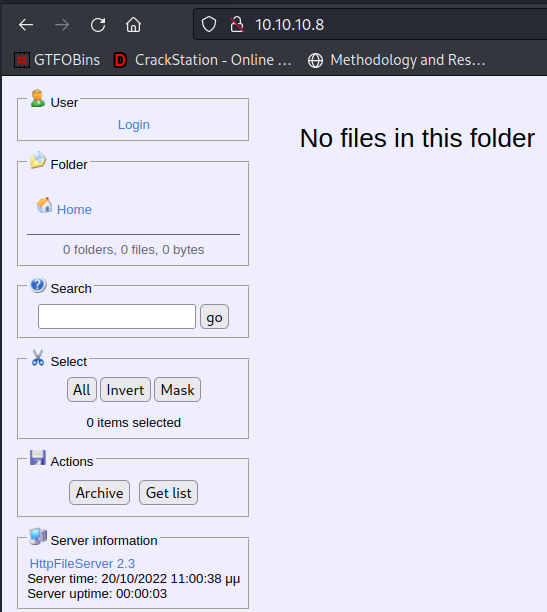 Webroot
it is indeed httpfileserver
it’s also known as hfs as well
Webroot
it is indeed httpfileserver
it’s also known as hfs as well
searchsploit
┌──(kali㉿kali)-[~/archive/htb/labs/optimum]
└─$ searchsploit httpfileserver 2.3
--------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------- ---------------------------------
Rejetto HttpFileServer 2.3.x - Remote Command Execution | windows/webapps/49125.py
--------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No ResultsChecking the application on the exploit database shows an RCE exploit