ldapdomaindump
Using the valid domain credential, I can use ldapdomaindump to get a graphical overview about the target domain
┌──(kali㉿kali)-[~/…/htb/labs/cascade/ldapdomaindump]
└─$ ldapdomaindump CASCADE.LOCAL -u 'CASCADE.LOCAL\r.thompson' -p 'rY4n5eva' -n $IP --no-json --no-grep
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finishedDone
Computers
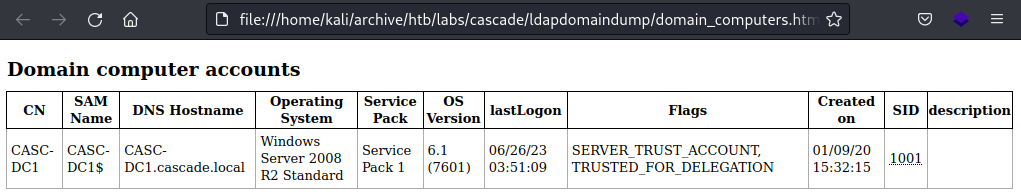 There’s only the DC host
There’s only the DC host
Groups
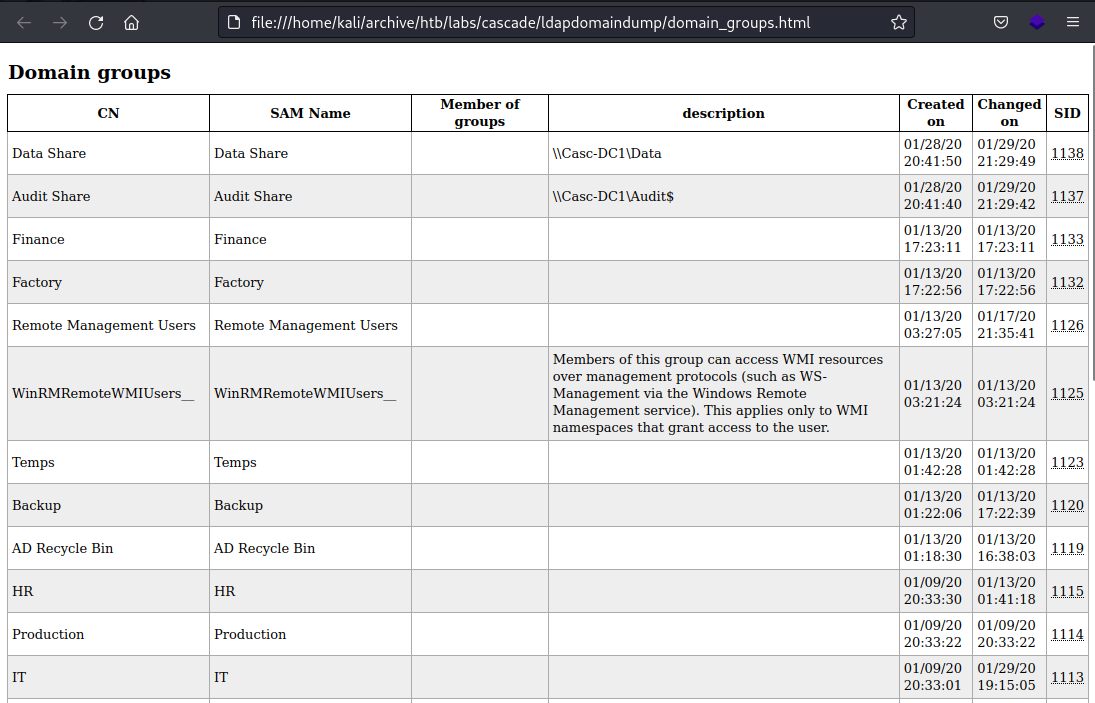 These are none default domain groups
These are none default domain groups
Users
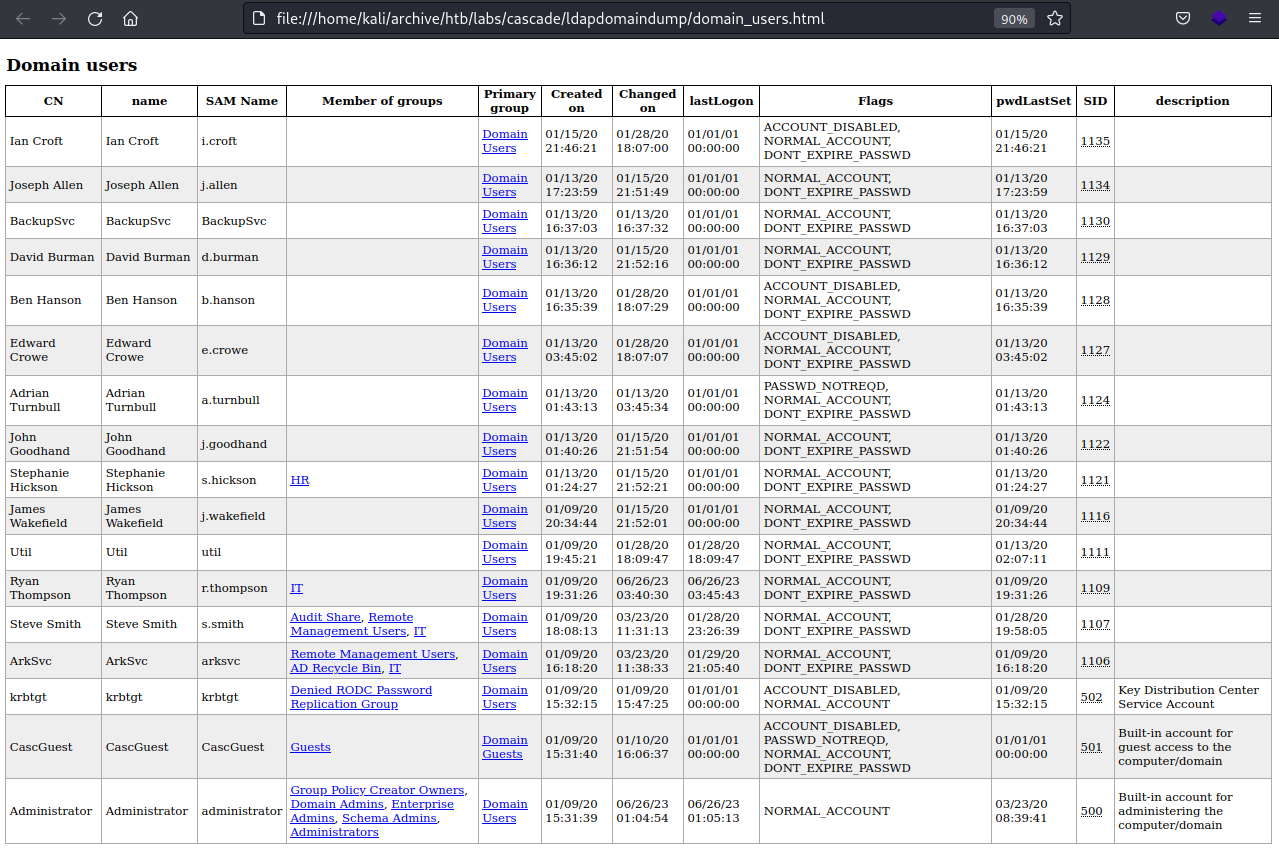 There are a number of users that appear most valuable
There are a number of users that appear most valuable