Web
Nmap discovered a web server on the port 443
Requests to the web server on the port 80 is being re-directed to here
 Webroot
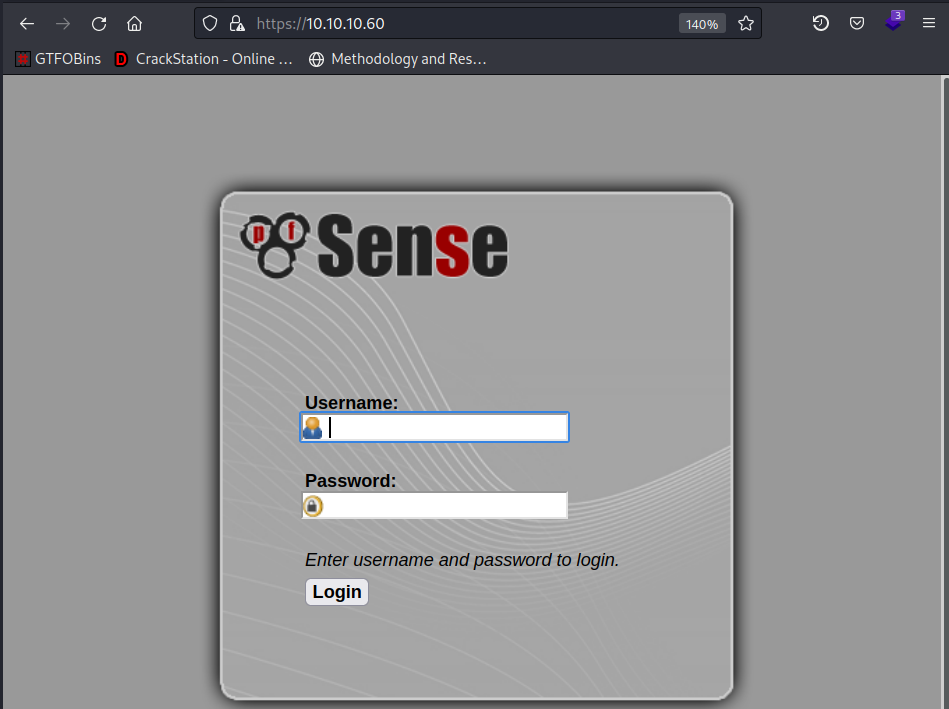
It’s pfSense login page
pfSense is an open source firewall
Based on the design, it’s quite old
Webroot
It’s pfSense login page
pfSense is an open source firewall
Based on the design, it’s quite old
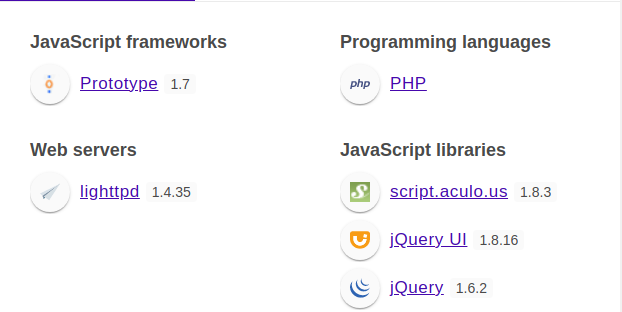 Wappalyzer also identified the technologies involved
Wappalyzer also identified the technologies involved
I tried logging in with some default credentials and wasn’t successful
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/sense]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -u https://$IP/FUZZ -ic -e .txt,.php,.html
________________________________________________
:: Method : GET
:: URL : https://10.10.10.60/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
index.html [status: 200, Size: 329, Words: 32, Lines: 25, Duration: 31ms]
index.php [status: 200, Size: 6690, Words: 907, Lines: 174, Duration: 112ms]
help.php [status: 200, Size: 6689, Words: 907, Lines: 174, Duration: 38ms]
themes [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 33ms]
stats.php [status: 200, Size: 6690, Words: 907, Lines: 174, Duration: 48ms]
css [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 29ms]
edit.php [status: 200, Size: 6689, Words: 907, Lines: 174, Duration: 43ms]
includes [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 29ms]
license.php [status: 200, Size: 6692, Words: 907, Lines: 174, Duration: 38ms]
system.php [status: 200, Size: 6691, Words: 907, Lines: 174, Duration: 39ms]
status.php [status: 200, Size: 6691, Words: 907, Lines: 174, Duration: 41ms]
javascript [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 31ms]
changelog.txt [status: 200, Size: 271, Words: 35, Lines: 10, Duration: 30ms]
classes [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 33ms]
exec.php [status: 200, Size: 6689, Words: 907, Lines: 174, Duration: 43ms]
widgets [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 29ms]
graph.php [status: 200, Size: 6690, Words: 907, Lines: 174, Duration: 41ms]
tree [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 27ms]
wizard.php [status: 200, Size: 6691, Words: 907, Lines: 174, Duration: 39ms]
shortcuts [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 31ms]
pkg.php [status: 200, Size: 6688, Words: 907, Lines: 174, Duration: 93ms]
installer [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 32ms]
wizards [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 264ms]
xmlrpc.php [status: 200, Size: 384, Words: 78, Lines: 17, Duration: 44ms]
reboot.php [status: 200, Size: 6691, Words: 907, Lines: 174, Duration: 38ms]
interfaces.php [status: 200, Size: 6695, Words: 907, Lines: 174, Duration: 47ms]
csrf [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 27ms]
system-users.txt [status: 200, Size: 106, Words: 9, Lines: 7, Duration: 32ms]
filebrowser [status: 301, Size: 0, Words: 1, Lines: 1, Duration: 29ms]
%7echeckout%7e [status: 403, Size: 345, Words: 33, Lines: 12, Duration: 32ms]
:: Progress: [882188/882188] :: Job [1/1] :: 810 req/sec :: Duration: [0:16:36] :: Errors: 0 ::
ffuf fuzzed the web server and returned some interesting information Some of which are part of the default installation of pfSense, and some are not.
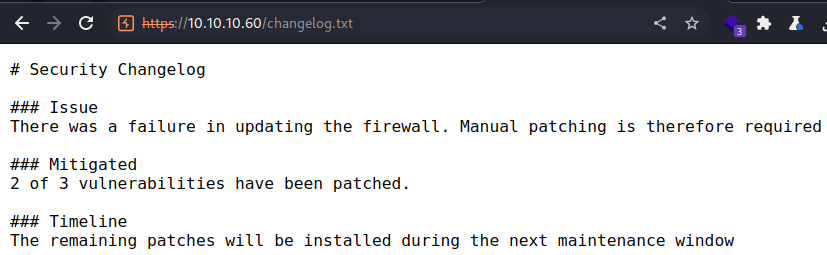
/changelog.txt
 The
The /changelog.txt file appears to have been created by an end user
It notes that the application failed to update and now is required manual patching
There still is one vulnerability remaining.
/index.html
 the
the /index.html file displays the dragon fly bsd logo
It also has an external link to installation
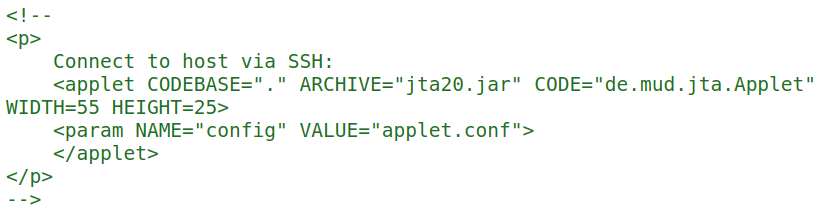 It has an interesting comment in the source code
It has an interesting comment in the source code
/tree/
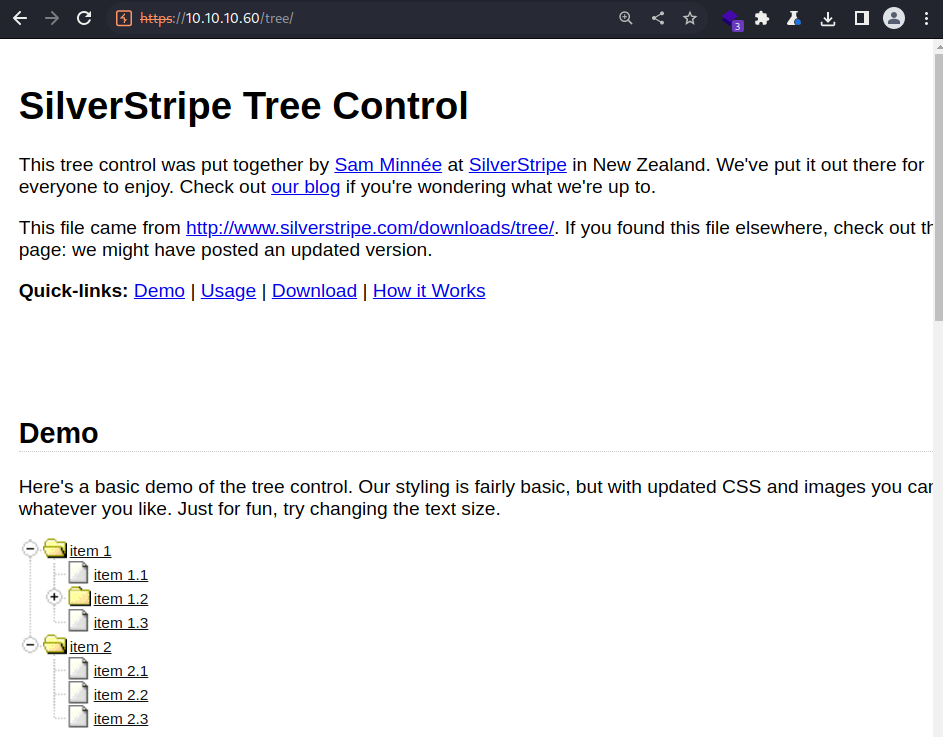 The
The /tree/ directory appears to be some kind of designing module that works alongside with CSS
 There is the version information
There is the version information
SilverStripe Tree Control 0.1
SilverStripe Tree Control is a user interface component that allows users to interact with a hierarchical tree structure in a web-based content management system (CMS). It is a feature of the SilverStripe CMS, which is an open-source web content management system written in the PHP programming language. The Tree Control is used to manage the hierarchical relationships between pages, files, and other types of content in the CMS. It allows users to move, delete, and organize content within the tree structure, and also provides a way to navigate the tree and access the content.
/system-users.txt
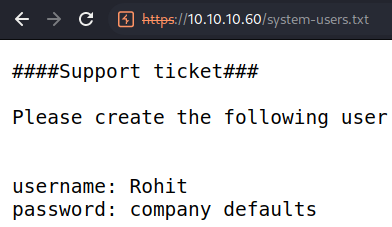 Navigating to the
Navigating to the /system-users.txt file reveals a potential user
Rohit
It also notes that the password is company defaults
CSRF Protection
I was looking for a way to get in, then I found out that the authentication has CSRF protection implemented. This means brute-forcing would be difficult.
 This file right here.
This file right here.
/csrf/csrf-magic.js
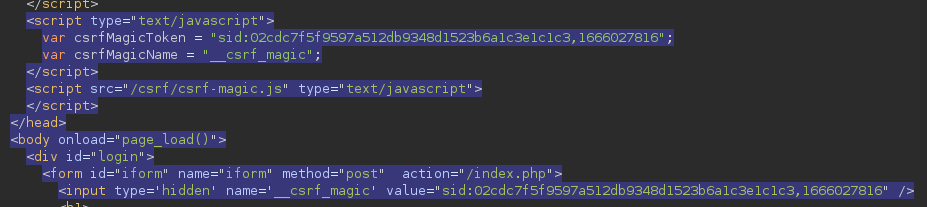 The login page draws the CSRF protection token from the
The login page draws the CSRF protection token from the /csrf/csrf-magic.js file upon loading
CSRF Magic is a feature of the PHP-based web development framework CodeIgniter, which is designed to make it easy to implement CSRF protection in web applications. The feature automatically generates and adds the security token to forms and URLs, and also provides a simple way to validate the token on the server.
The idea behind this technique is that when a user submits a form, the token is also sent with the form data. The server then checks if the token is valid before processing the form. This way, even if an attacker manages to create a malicious form, the form will be rejected by the server if the attacker doesn’t have the token.
Admin Panel
 Password turned out to be the default password of pfSense;
Password turned out to be the default password of pfSense; pfsense
the initial credential of pfsense is, by default; admin:pfsense
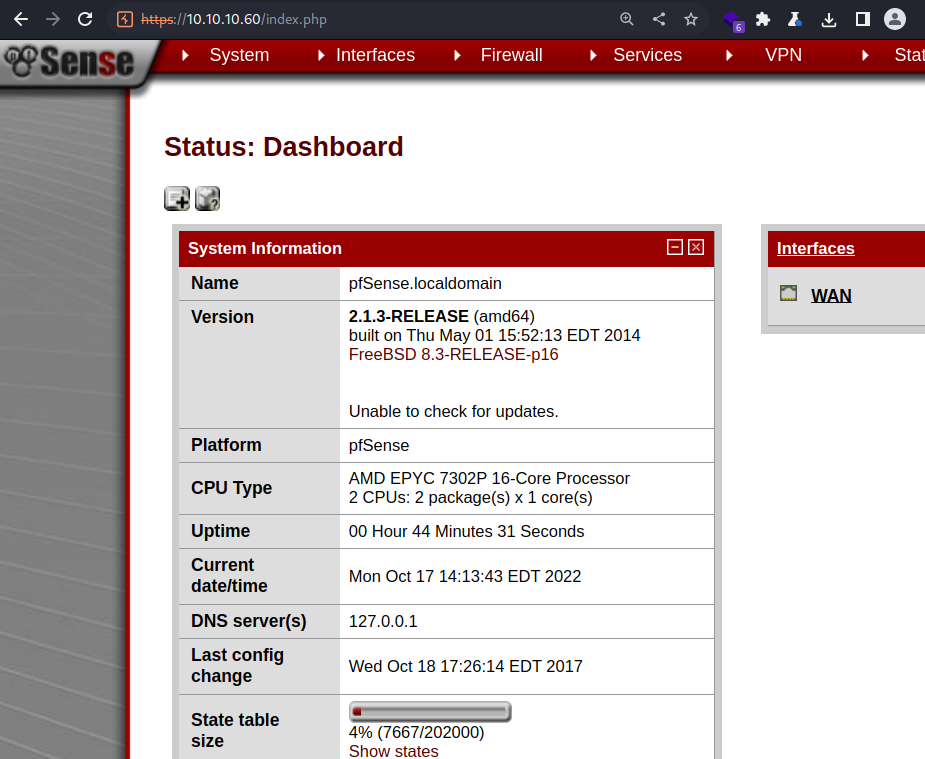
Logged in to the admin panel as the rohit user
I can see the version information
2.1.3-RELEASE
┌──(kali㉿kali)-[~/archive/htb/labs/sense]
└─$ searchsploit pfsense 2.1.3
------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------ ---------------------------------
pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection | php/webapps/43560.py
------------------------------------------------------------------ ---------------------------------
shellcodes: No Results
papers: No ResultsLooking it up on searchsploit reveals that it is vulnerable to injection