dev
Checking for sudo privileges of the dev user after making the lateral movement
dev@yummy:/dev/shm$ sudo -l
Matching Defaults entries for dev on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User dev may run the following commands on localhost:
(root : root) NOPASSWD: /usr/bin/rsync -a --exclude\=.hg /home/dev/app-production/* /opt/app/The dev user is able to execute /usr/bin/rsync -a --exclude\=.hg /home/dev/app-production/* /opt/app/ as the root account
It basically copies the /home/dev/app-production/* to the /opt/app directory while excluding the .hg directory within.
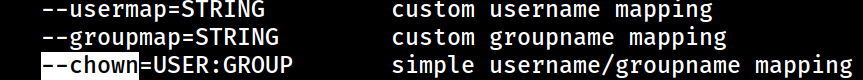 Since I have write access to the
Since I have write access to the /home/dev/app-production directory, I can easily exploit the sudo privileged-command by creating a SUID bash because rsync also supports --chown flag, making the destination directory owned by the root account, effectively turning the SUID bash into root SUID bash.
Moving on to Privilege Escalation phase