PEAS
While I was initially Beep the target system, I discovered that it is severely old. Older systems tend to have a large amount of vulnerabilities
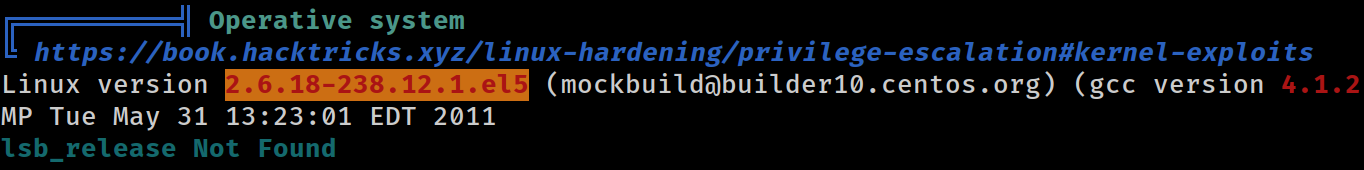 PEAS was able to identify the kernel version, which is clearly vulnerable as highlighted
PEAS was able to identify the kernel version, which is clearly vulnerable as highlighted
╔══════════╣ Executing Linux Exploit Suggester 2
╚ https://github.com/jondonas/linux-exploit-suggester-2
base64: invalid input
[1] american-sign-language
CVE-2010-4347
source: http://www.securityfocus.com/bid/45408
[2] can_bcm
CVE-2010-2959
source: http://www.exploit-db.com/exploits/14814
[3] do_pages_move
alt: sieve CVE-2010-0415
source: Spenders Enlightenment
[4] ftrex
CVE-2008-4210
source: http://www.exploit-db.com/exploits/6851
[5] half_nelson1
alt: econet CVE-2010-3848
source: http://www.exploit-db.com/exploits/17787
[6] half_nelson2
alt: econet CVE-2010-3850
source: http://www.exploit-db.com/exploits/17787
[7] half_nelson3
alt: econet CVE-2010-4073
source: http://www.exploit-db.com/exploits/17787
[8] msr
CVE-2013-0268
source: http://www.exploit-db.com/exploits/27297
[9] pipe.c_32bit
CVE-2009-3547
source: http://www.securityfocus.com/data/vulnerabilities/exploits/36901-1.c
[10] pktcdvd
CVE-2010-3437
source: http://www.exploit-db.com/exploits/15150
[11] reiserfs
CVE-2010-1146
source: http://www.exploit-db.com/exploits/12130
[12] sock_sendpage
alt: wunderbar_emporium CVE-2009-2692
source: http://www.exploit-db.com/exploits/9435
[13] sock_sendpage2
alt: proto_ops CVE-2009-2692
source: http://www.exploit-db.com/exploits/9436
[14] udp_sendmsg_32bit
CVE-2009-2698
source: http://downloads.securityfocus.com/vulnerabilities/exploits/36108.c
[15] video4linux
CVE-2010-3081
source: http://www.exploit-db.com/exploits/15024
[16] vmsplice1
alt: jessica biel CVE-2008-0600
source: http://www.exploit-db.com/exploits/5092This is the list of vulnerabilities identified by PEAS
 Cronjob.
Cronjob.
 Init.d
Init.d
There are a LOT more. But I would assume that the asterisk user, at this point, is basically root