PEAS
Basic enumeration could always miss out some details.
 Executing PEAS
Executing PEAS
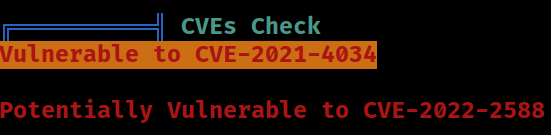 The target system is vulnerable to
The target system is vulnerable to CVE-2021-4034
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
exposure: less probable
tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
download url: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
details: https://www.openwall.com/lists/oss-security/2022/08/29/5
exposure: less probable
tags: ubuntu=(20.04){kernel:5.12.13}
download url: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
exposure: less probable
tags: ubuntu=20.04{kernel:5.8.0-*}
download url: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
comments: ip_tables kernel module must be loaded
[+] [CVE-2019-15666] XFRM_UAF
details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
exposure: less probable
download url:
comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2018-18955] subuid_shell
details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
exposure: less probable
tags: ubuntu=18.04{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
download url: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
comments: CONFIG_USER_NS needs to be enabledMore vulnerabilities