Web
Nmap discovered a web server running on the target port 80
 Webroot
it appears to be a custom website featuring phpbash
Webroot
it appears to be a custom website featuring phpbash
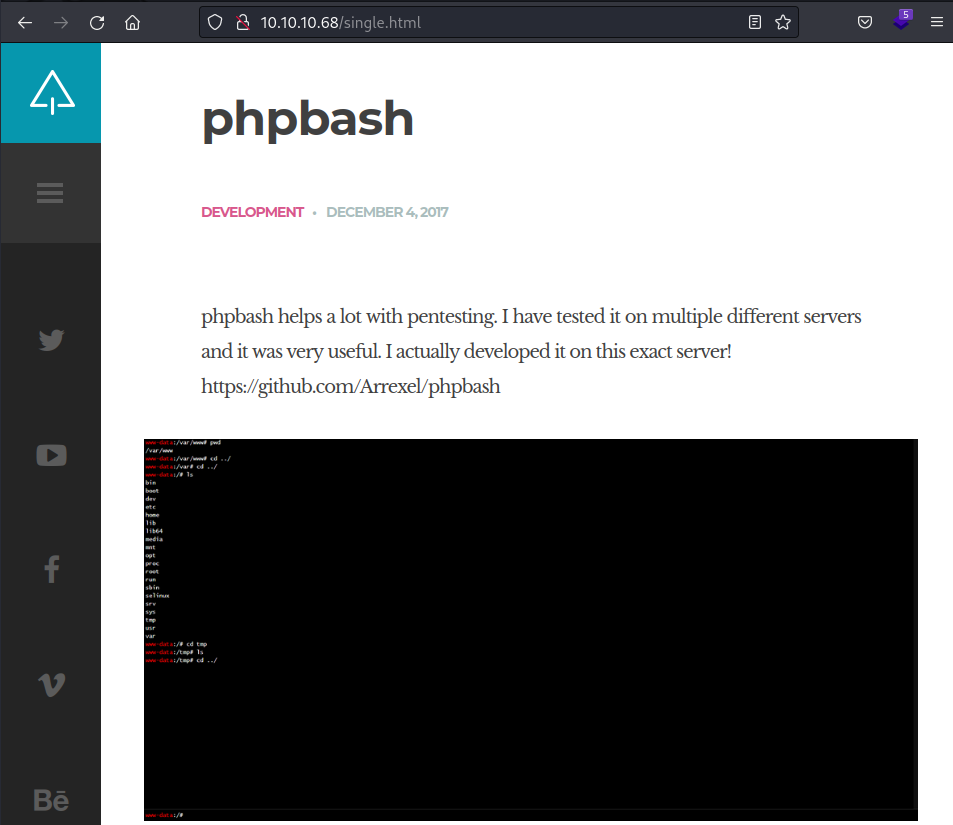
/single.html goes over the feature in-depth
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/bashed]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-files-lowercase.txt -u http://$IP/FUZZ -ic
________________________________________________
:: Method : GET
:: URL : http://10.10.10.68/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-files-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
config.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 31ms]
index.html [Status: 200, Size: 7743, Words: 2956, Lines: 162, Duration: 31ms]
contact.html [Status: 200, Size: 7805, Words: 2630, Lines: 157, Duration: 29ms]
style.css [Status: 200, Size: 24164, Words: 4814, Lines: 1412, Duration: 30ms]
about.html [Status: 200, Size: 8193, Words: 2878, Lines: 155, Duration: 30ms]
scroll.html [Status: 200, Size: 10863, Words: 4284, Lines: 196, Duration: 30ms]
:: Progress: [35325/35325] :: Job [1/1] :: 1326 req/sec :: Duration: [0:00:27] :: Errors: 1 ::Fuzzing the web server revealed a few more files
config.php seems interesting but the returned size is 0
┌──(kali㉿kali)-[~/archive/htb/labs/bashed]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://$IP/FUZZ/ -ic
________________________________________________
:: Method : GET
:: URL : http://10.10.10.68/FUZZ/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 7743, Words: 2956, Lines: 162, Duration: 35ms]
images [Status: 200, Size: 1564, Words: 91, Lines: 20, Duration: 33ms]
uploads [Status: 200, Size: 14, Words: 1, Lines: 2, Duration: 33ms]
php [Status: 200, Size: 939, Words: 64, Lines: 17, Duration: 30ms]
css [Status: 200, Size: 1758, Words: 99, Lines: 21, Duration: 27ms]
dev [Status: 200, Size: 1148, Words: 76, Lines: 18, Duration: 30ms]
js [Status: 200, Size: 3165, Words: 190, Lines: 27, Duration: 31ms]
fonts [Status: 200, Size: 2095, Words: 124, Lines: 22, Duration: 32ms]
demo-images [Status: 200, Size: 3240, Words: 165, Lines: 28, Duration: 32ms]
:: Progress: [1273820/1273820] :: Job [1/1] :: 1350 req/sec :: Duration: [0:16:27] :: Errors: 0 ::ffuf found some more directories
uplodas, php, and dev seem particularly interesting
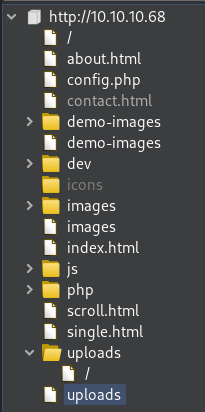 This is the overall web structure by far.
This is the overall web structure by far.
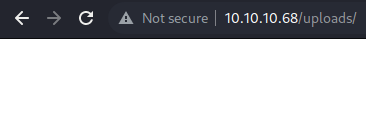
/uploads/ appears to be empty
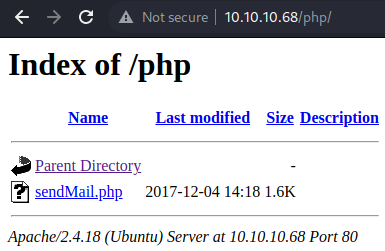
/php/ has directory indexing enabled and contains a single file; /php/sendMail.php
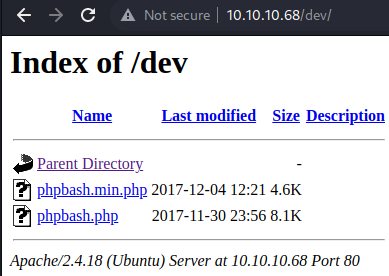
/dev/ also has directory indexing enabled and contains 2 files within
They are the main feature of this website
phpbash
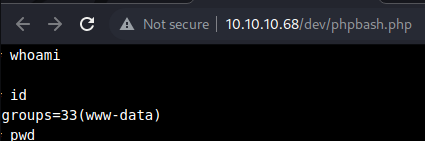 Browsing to the
Browsing to the /dev/phpbash.php file, reveals the feature itself.
A shell session through a web GUI,
I guess there is no such exploitation at this point as I can just interact with the system through here. But I feel rather limited with a webshell so I will migrate to a better PTY session