Home Directory
Gaining a foothold as the tyler user gave me an access to the user’s home directory.
ps c:\Users\tyler> dir
directory: C:\Users\tyler
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 8/19/2018 3:51 PM 3D Objects
d----- 8/19/2018 11:10 AM cleanup
d-r--- 8/19/2018 3:51 PM Contacts
d-r--- 8/19/2018 3:51 PM Desktop
d-r--- 8/19/2018 3:51 PM Documents
d-r--- 8/19/2018 3:51 PM Downloads
d-r--- 8/19/2018 3:51 PM Favorites
d-r--- 8/19/2018 3:51 PM Links
d-r--- 8/19/2018 3:51 PM Music
d-r--- 4/9/2021 6:09 AM OneDrive
d-r--- 8/19/2018 3:51 PM Pictures
d-r--- 8/19/2018 3:51 PM Saved Games
d-r--- 8/19/2018 3:51 PM Searches
d----- 1/24/2023 3:16 PM secnotes_contacts
d-r--- 8/19/2018 3:51 PM Videos
-a---- 8/19/2018 10:49 AM 0 .php_history
-a---- 6/22/2018 4:29 AM 8 0There are two directories that certainly look unique to this user
cleanupsecnotes_contacts
cleanup
PS C:\Users\tyler> cd cleanup ; dir
Directory: C:\Users\tyler\cleanup
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/19/2018 11:08 AM 237 cleanup.ps1There is a PowerShell script inside the cleanup directory
PS C:\Users\tyler\cleanup> cat cleanup.ps1
while($true) {
Write-Host "Cleaning up new-site!"
Get-ChildItem -Path "C:\inetpub\new-site" -Exclude iisstart.* | Select -ExpandProperty FullName | Remove-Item -Force
Write-Host "Sleeping for 5 minutes..."
Start-Sleep -s 300
}Oh so this is the PowerShell script that was periodically deleting every file inside the \\secnotes.htb\new-site SMB share or the empty web server on the port 8808.
It basically leaves out only the iisstart.* files and deletes everything else every 5 minutes.
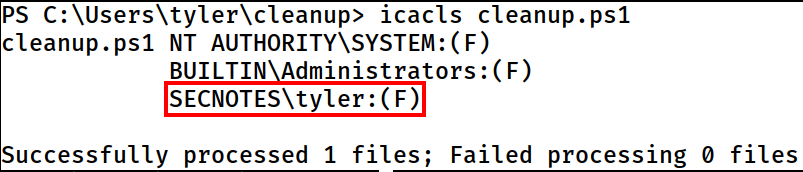 While I was unable to locate the scheduled task that is running this script in the background, I found out that I have the full permission over the script.
While I was unable to locate the scheduled task that is running this script in the background, I found out that I have the full permission over the script.
I might as well change it
PS C:\Users\tyler\cleanup> move cleanup.ps1 stop.ps1
PS C:\Users\tyler\cleanup> dir
Directory: C:\Users\tyler\cleanup
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/19/2018 11:08 AM 237 stop.ps1Hopefully this will do the trick as the scheduled task won’t be able to locate the script now
secnotes_contacts
ps c:\Users\tyler\cleanup> cd ..\secnotes_contacts ; dir
directory: C:\Users\tyler\secnotes_contacts
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/9/2021 4:09 AM 1743 check-messages-orig.ps1
-a---- 4/9/2021 8:42 AM 1928 check-messages.ps1 The secnotes_contacts directory has two PowerShell scripts.
Based on the naming of them, I guess it was originally copied from somewhere.
I will check the check-messages.ps1 file
check-messages.ps1
PS C:\Users\tyler\secnotes_contacts> cat check-messages.ps1
$resp = Invoke-WebRequest 'http://127.0.0.1/' -UseBasicParsing -sessionvariable session
$ip = ((ipconfig | findstr [0-9].\.)[0]).Split()[-1]
while($true) {
$found_url = 0;
$locs = @($ip, '127.0.0.1', 'secnotes.htb', 'localhost')
ForEach ($loc in $locs) {
$resp = Invoke-WebRequest "http://$loc/" -UseBasicParsing -WebSession $session
if ($resp.RawContent -like '*Please fill in your credentials to login*') {
Write-Host "Reseting password and getting cookie for $loc"
# reset tylers password to forested85sunk
& 'C:\Program Files\MySQL\MySQL Server 8.0\bin\mysql.exe' -u secnotes -pq8N#9Eos%JinE57tke72 secnotes -e 'update users set password = \"$2y$10$q6EzQPEssjjQ7J5bdMTbQ.GGQaBTVZZ.hSO04gJkr9U0DCqxB2oL.\" where username = \"tyler\";'
# login
$resp = Invoke-WebRequest "http://$loc/login.php" -UseBasicParsing -WebSession $session -Method POST -Body @{username='tyler';password='forested85sunk'};
}
}
$file = Get-ChildItem "C:\Users\tyler\secnotes_contacts\" -Filter *.txt | Sort-Object CreationTime | Select-Object -First 1
if ($file) {
Write-Host "Opening file $($file)..."
$content = Get-Content $file.FullName
$content.split(' ') | ForEach-Object {
if ($_ -match "^https?://((([\w-]+\.)+[\w-]+)|localhost)(:\d+)?([\w- ./?&%=]*)$") {
$url = $matches[0];
Write-Host "Visiting $($url)"
try {
(iwr $url -WebSession $session -TimeoutSec 1 -UseBasicParsing).content
} catch {
Write-Host "Page not found"
}
if ($url -match "change_pass.php") {
Write-Host "Found change_pass.php... will sleep 30"
$found_url = 1
}
}
}
Write-Host "Deleting file $($file)"
Remove-Item $file.FullName
}
if ($found_url -eq 1) {
Write-Host "Sleeping for 30 seconds"
Start-Sleep -s 30
} else {
Write-Host "Sleeping for 5 seconds"
Start-Sleep -s 5
}
}- The script uses the
Invoke-WebRequestcmdlet to make a request to the local host (http://127.0.0.1/) and stores the response in the variable$resp - It uses the
ipconfigcommand to get the local IP address and stores it in the variable$ip - The script enters an infinite loop
- Within the loop, it creates an array of locations
(the local IP, '127.0.0.1', 'secnotes.htb', and 'localhost')and iterates through them, sending a request to each location - If the response from a location contains the text
"Please fill in your credentials to login", it runs a MySQL command to reset the password of thetyleruser to a specific value, and then sends a POST request to login with that user’s credentials - The script then gets the most recently created file in the folder;
C:\Users\tyler\secnotes_contacts - If a file is found, it opens the file and splits the content by spaces
- For each word in the file, it checks if it’s a valid URL
- If it’s a valid URL, it sends a GET request to the URL and if it’s
change_pass.phpit sets a variable$found_urlas 1 - If it’s a
change_pass.phpit sleeps for 30 seconds before continuing the loop, else it sleeps for 5 seconds. - After that, it deletes the file
- The script repeats this loop indefinitely.
This script is responsible for that CSRF vulnerability. I knew that there was a time-based PowerShell script running in the back from the header.
bash?
ps c:\Users\tyler\Desktop> dir
directory: C:\Users\tyler\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/22/2018 3:09 AM 1293 bash.lnk
-a---- 8/2/2021 3:32 AM 1210 Command Prompt.lnk
-a---- 4/11/2018 4:34 PM 407 File Explorer.lnk
-a---- 6/21/2018 5:50 PM 1417 Microsoft Edge.lnk
-a---- 6/21/2018 9:17 AM 1110 Notepad++.lnk
-ar--- 1/24/2023 1:30 PM 34 user.txt
-a---- 8/19/2018 10:59 AM 2494 Windows PowerShell.lnkI found a shortcut file named, `bash.lnk Why would there be bash in Windows?
ps c:\Users\tyler\Desktop> cat bash.lnk
l?f w??????v? ?v(??? ??9p?o? ?:i?+00?/C:\V1?LIWindows@ ???L???LI.h???&WindowsZ1?L<System32B ???L???L<.p?k?System32Z2??LP? bash.exeB ???L<??LU.?Y????bash.exeK-J????C:\Windows\System32\bash.exe"..\..\..\Windows\System32\bash.exeC:\Windows\System32?%?
?wn?�?]n?d.??q???`?xsecnotesx?<saa??????o?:u??'?/?x?<sAA??????o?:u??'?/?= ?Y1SPS?0??C?G????sf"=dSystem32 (C:\Windows)?1SPS??XF?L8C???&?m?q/S-1-5-21-1791094074-1363918840-4199337083-1002?1SPS0?%??G�??`????%
bash.exe@??????
?)
application@v(??? ?i1sps?jc(=?????o??mc:\Windows\System32\bash.exe91SPS?mD??pH?H@.?=x?hH?(?bPWhile it’s mostly impossible to read shortcut files as they are in the binary format, but I notice some readable strings there.
it points to c:\Windows\System32\bash.exe
ps c:\Users\tyler\Desktop> cmd /c where /R \ bash.exe
c:\Windows\System32\bash.exe
c:\Windows\WinSxS\amd64_microsoft-windows-lxss-bash_31bf3856ad364e35_10.0.17134.1_none_251beae725bc7de5\bash.exeThere are 2 files named, bash.exe, at 2 different locations
ps c:\inetpub\new-site> C:\Windows\System32\bash.exe
ps c:\inetpub\new-site> C:\Windows\WinSxS\amd64_microsoft-windows-lxss-bash_31bf3856ad364e35_10.0.17134.1_none_251beae725bc7de5\bash.exe
Both of them just hang upon execution. No responses