CVE-2016-3714
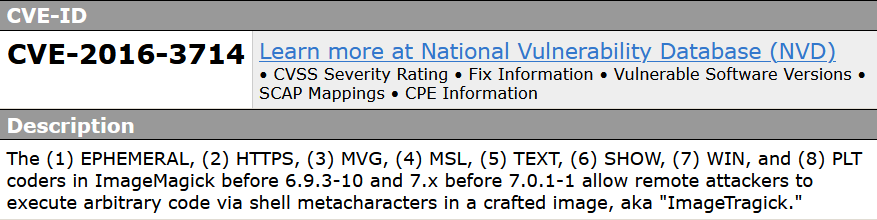 It was discovered that certain ImageMagick coders and pseudo-protocols did not properly prevent security sensitive operations when processing specially crafted images. A remote attacker could create a specially crafted image that, when processed by an application using ImageMagick or an unsuspecting user using the ImageMagick utilities, would allow the attacker to move arbitrary files.
Exploiting this vulnerability may allow the attacker to move files on the filesystem. However, the trigger for the exploit is highly complex, while the affected files are limited and have a low impact of file integrity on the system.
It was discovered that certain ImageMagick coders and pseudo-protocols did not properly prevent security sensitive operations when processing specially crafted images. A remote attacker could create a specially crafted image that, when processed by an application using ImageMagick or an unsuspecting user using the ImageMagick utilities, would allow the attacker to move arbitrary files.
Exploiting this vulnerability may allow the attacker to move files on the filesystem. However, the trigger for the exploit is highly complex, while the affected files are limited and have a low impact of file integrity on the system.
note: This vulnerability is one of the series of vulnerabilities known as ImageTragick.