Web
Nmap discovered a web server on the target port 8808
 Webroot
It’s the default IIS installation page.
Webroot
It’s the default IIS installation page.
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/secnotes]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://$IP:8808/FUZZ -ic -e .txt,.php,.html
________________________________________________
:: Method : GET
:: URL : http://10.10.10.97:8808/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
:: Progress: [882188/882188] :: Job [1/1] :: 1331 req/sec :: Duration: [0:12:08] :: Errors: 0 ::Fuzzing reveals absolutely nothing.
Served/Mirrored from SMB
It was suspected that the //secnotes.htb/new-site SMB share is serving/mirroring the web server running on the target port 8808
A test file was uploaded to the SMB share, I will now navigate to it to check my theory
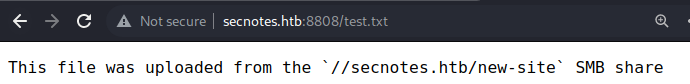 The theory is confirmed.
The
The theory is confirmed.
The //secnotes.htb/new-site SMB share is serving/mirroring the web root here.
I will get straights to the exploitation