Web
Nmap discovered a Web server on the target port 10000
The running service is MiniServ 1.910 (Webmin httpd)
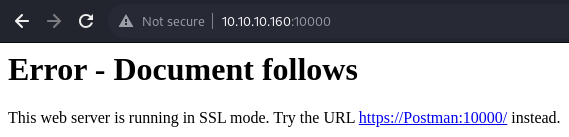 Heading over to the web root reveals that the web server is running over SSL
It also shows the hostname;
Heading over to the web root reveals that the web server is running over SSL
It also shows the hostname; Postman
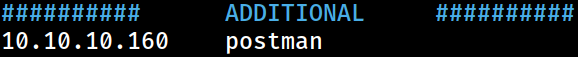 The host information has been appended to the
The host information has been appended to the /etc/hosts file on Kali for local DNS resolution
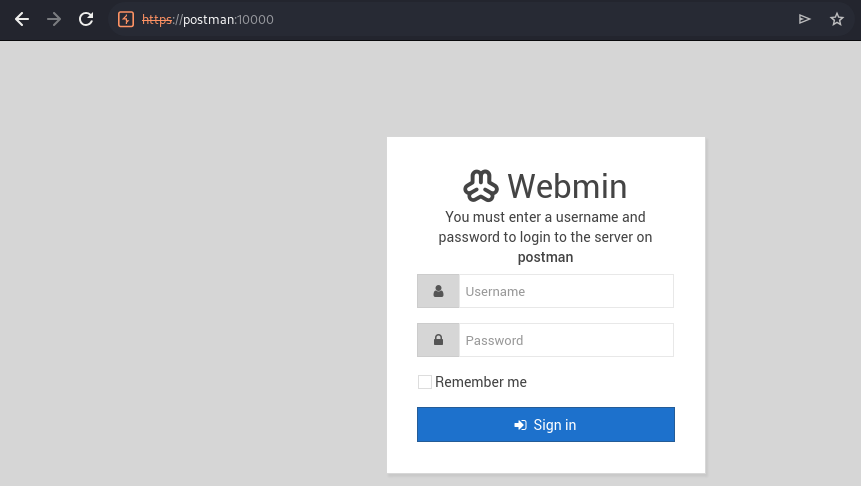 as expected, the web root is a login page for webmin
as expected, the web root is a login page for webmin
 webmin is a web-based server management control panel for unix-like systems. Webmin allows the user to configure operating system internals, such as users, disk quotas, services and configuration files, as well as modify and control open-source apps, such as BIND, Apache HTTP Server, PHP, and MySQL
webmin is a web-based server management control panel for unix-like systems. Webmin allows the user to configure operating system internals, such as users, disk quotas, services and configuration files, as well as modify and control open-source apps, such as BIND, Apache HTTP Server, PHP, and MySQL
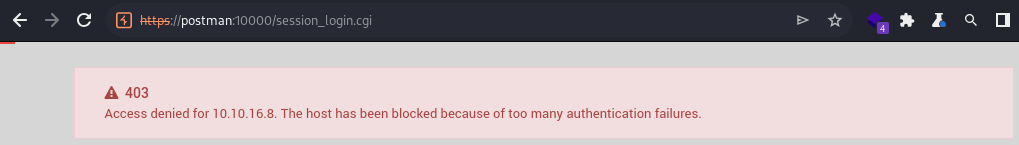 I got IP-blocked while I was trying a few known default credentials.
This would mean that brute-forcing the login page is pretty much out of the window due to the presence of the security restriction
I got IP-blocked while I was trying a few known default credentials.
This would mean that brute-forcing the login page is pretty much out of the window due to the presence of the security restriction
Vulnerabilities
┌──(kali㉿kali)-[~/archive/htb/labs/postman]
└─$ searchsploit Webmin 1.910
------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------ ---------------------------------
Webmin 1.910 - 'Package Updates' Remote Command Execution (Metasploit) | linux/remote/46984.rb
Webmin < 1.920 - 'rpc.cgi' Remote Code Execution (Metasploit) | linux/webapps/47330.rb
------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No ResultsIt would appear that the target Webmin instance suffers from a RCE vulnerability However, it requires authentication and I don’t have a valid credential