BloodHound
The default password for the target domain was hard-coded into the Description attribute of a user. While the password did not work for the original user, a simple password spray attack revealed that it worked for another user; melanie. It was later then validated and used to request for a TGT
Here, I will get bloodhound going to understand the target domain better
Ingestion
┌──(kali㉿kali)-[~/…/htb/labs/resolute/bloodhound]
└─$ KRB5CCNAME=../melanie.ccache bloodhound-python -u melanie -d MEGABANK.LOCAL -k -ns $IP -dc resolute.megabank.local --dns-tcp --zip -no-pass -c All
Password:
INFO: Found AD domain: megabank.local
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: resolute.megabank.local
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: resolute.megabank.local
INFO: Found 28 users
INFO: Found 54 groups
INFO: Found 2 gpos
INFO: Found 6 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: MS02.megabank.local
INFO: Querying computer: Resolute.megabank.local
INFO: Done in 00M 18S
INFO: Compressing output into 20230610191407_bloodhound.zipUsing the TGT of the melanie user, I am able to authenticate to the target KDC to run the ingestor for bloodhound
Although bloodhound-python prompted me for password, I did not provide any, and it worked out just fine.
Additionally, the -no-pass flag of bloodhound-python doesn’t seem to be functional
BloodHound
┌──(kali㉿kali)-[~/…/htb/labs/resolute/bloodhound]
└─$ sudo neo4j console
[sudo] password for kali:
directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /usr/share/neo4j/run
Starting Neo4j.
┌──(kali㉿kali)-[~/…/htb/labs/resolute/bloodhound]
└─$ bloodhound Firing up neo4j and bloodhound
 Ingested data uploaded
Ingested data uploaded
melanie
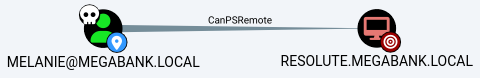 The current user,
The current user, melanie, doesn’t appear to have any outbound object control
This leaves me only to connect directly to the DC host via WinRM
ryan
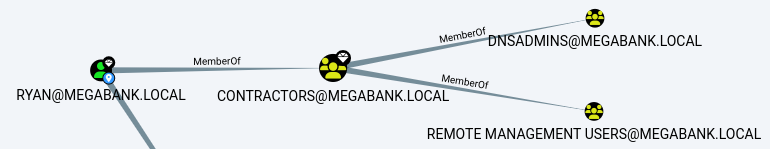 The
The ryan user being part of the Contractors group provides a transitive group membership to the DnsAdmins group.
This is worth noting since the Contractors group is a none default group as initially discovered earlier via ldapdomaindump