Web
Nmap discovered a web server on the target port 80
The running service is Apache httpd 2.4.41
 Webroot
The web server responses with the code 302, pointing to a domain;
Webroot
The web server responses with the code 302, pointing to a domain; forge.htb
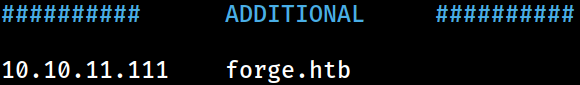 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resolution
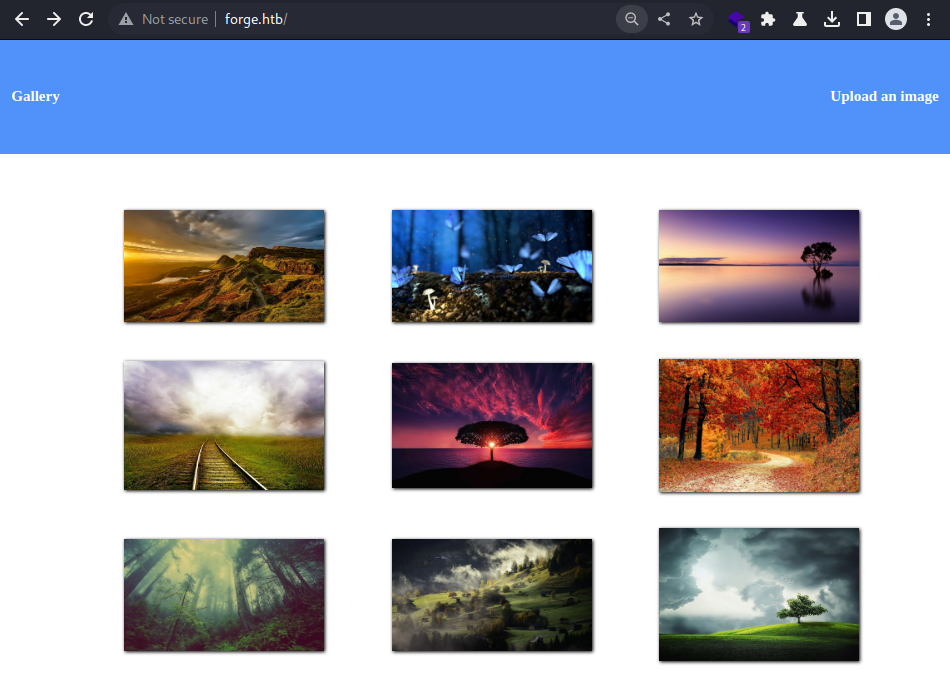 Webroot
It appears to be a gallery
Webroot
It appears to be a gallery
 The button at the right-top corner leads to
The button at the right-top corner leads to /upload
/upload
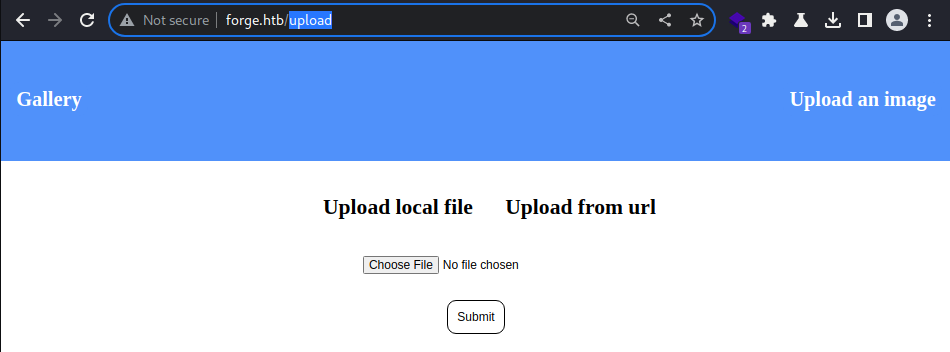
/upload features file upload.
It seems that I am able to upload files from a local source as well as from a remote location
This feature may present a few vulnerabilities
Local
┌──(kali㉿kali)-[~/archive/htb/labs/forge]
└─$ echo 'uploading a local resource' > local.txtI will first create an arbitrary file that contains some text
 I will then upload the
I will then upload the local.txt file using the web GUI
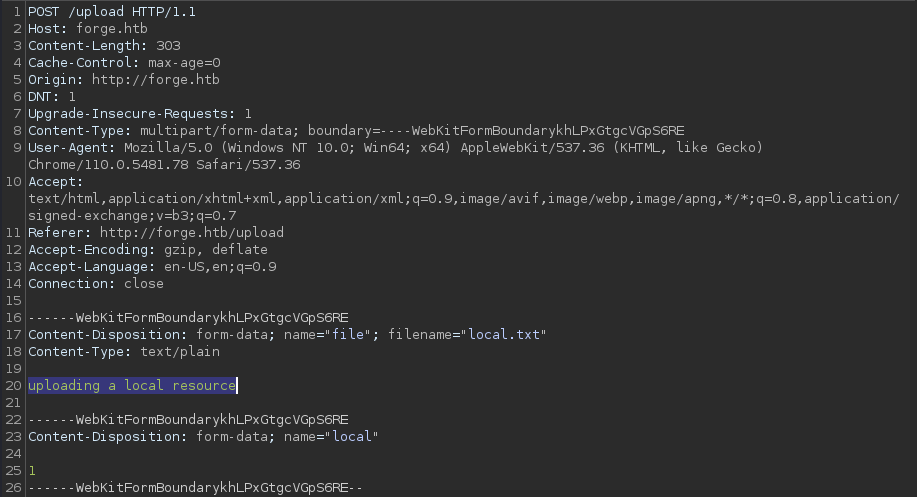 The Burp Suite interceptor shows that it does that by sending a POST request to
The Burp Suite interceptor shows that it does that by sending a POST request to /upload
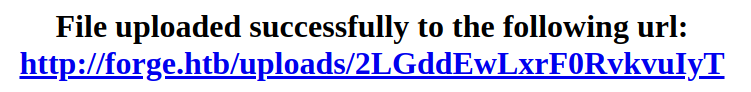 Then, I get this location at
Then, I get this location at /uploads/2LGddEwLxrF0RvkvuIyT
Whatever is in the backend is re-naming the uploaded files
 While following the link provided above indeed reveals something, it just appears to be missing
While following the link provided above indeed reveals something, it just appears to be missing
┌──(kali㉿kali)-[~/archive/htb/labs/forge]
└─$ curl -s http://forge.htb/uploads/2LGddEwLxrF0RvkvuIyT
uploading a local resourceThe uploaded file indeed contains the content that I placed earlier.
I would need to find out about the programming language the backend is using in order to exploit it if that’s even possible
Remote
┌──(kali㉿kali)-[~/archive/htb/labs/forge]
└─$ echo 'uploading a remote resource' > remote.txtI will test out the remote resource uploading
┌──(kali㉿kali)-[~/archive/htb/labs/forge]
└─$ nnc 80
listening on [any] 80 ...Start a “web server” on Kali
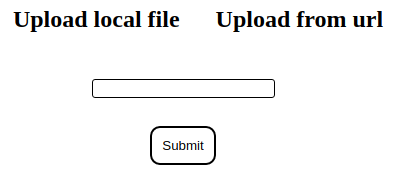 Clicking into the Upload from url button reveals a type bar
I am assuming here is where I can type the remote resource
Clicking into the Upload from url button reveals a type bar
I am assuming here is where I can type the remote resource
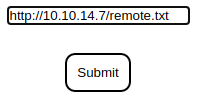 Sending
Sending
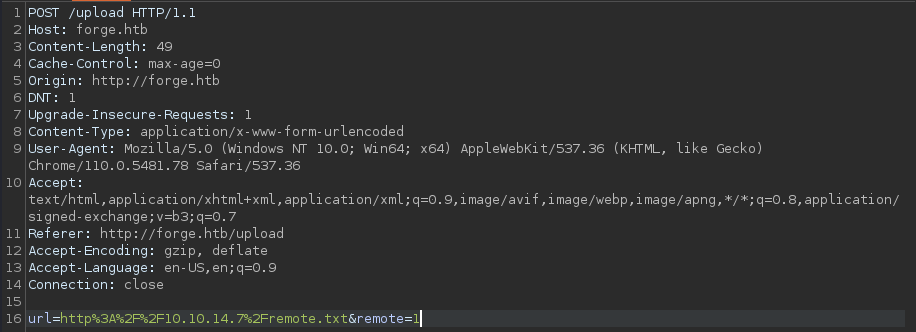 While it also send out a POST request to
While it also send out a POST request to /upload, the data is in a bit different structure
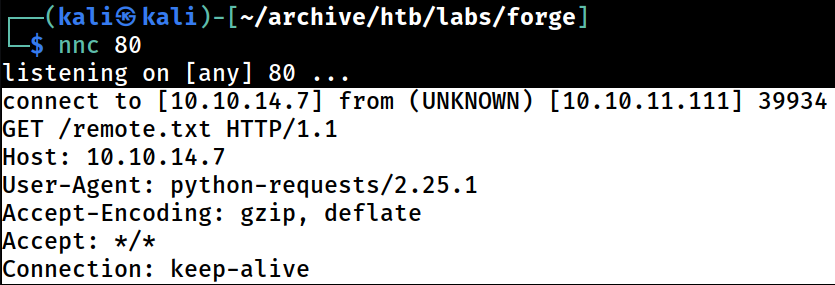 I got a hit on the Kali web server
I got a hit on the Kali web server
While it is clear that the backend is using Python-requests library, I cannot figure out if the version information, 2.25.1, is for Python or the library
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/forge]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -u http://forge.htb/FUZZ -ic -e .php,.txt,.html
________________________________________________
:: Method : GET
:: URL : http://forge.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .txt .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
uploads [status: 301, Size: 224, Words: 21, Lines: 4, Duration: 100ms]
static [status: 301, Size: 307, Words: 20, Lines: 10, Duration: 92ms]
upload [status: 200, Size: 929, Words: 267, Lines: 33, Duration: 105ms]
server-status [status: 403, Size: 274, Words: 20, Lines: 10, Duration: 95ms]ffuf did not find anything additional
Sub-Domain / Virtual Host Discovery
┌──(kali㉿kali)-[~/archive/htb/labs/forge]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://$IP/ -H 'Host: FUZZ.forge.htb' -fw 18
________________________________________________
:: Method : GET
:: URL : http://10.10.11.111/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.forge.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response words: 18
________________________________________________
admin [Status: 200, Size: 27, Words: 4, Lines: 2, Duration: 507ms]
:: Progress: [114441/114441] :: Job [1/1] :: 415 req/sec :: Duration: [0:04:29] :: Errors: 0 ::ffuf found a sub-domain / virtual host; admin.forge.htb
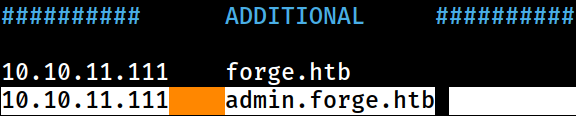 I appended the domain information to the
I appended the domain information to the /etc/hosts file on Kali
admin.forge.htb
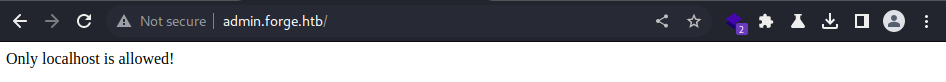 Browsing to the web root of the newly discovered sub-domain / virtual hosts;
Browsing to the web root of the newly discovered sub-domain / virtual hosts; admin.forge.htb
It appears to be only accessible through localhost
The uploading feature that is available at forge.htb/upload, fetches user input URL and stores it.
I may be able to access the admin.forge.htb sub-domain / virtual host through SSRF