Web
Nmap Horizontall a web server on the target port 80
the running service is nginx 1.14.0
 Webroot
I am redirected to a domain and the browser failed to resolve it;
Webroot
I am redirected to a domain and the browser failed to resolve it; horizontall.htb
 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resolution
 Webroot
The platform to be providing a website building service
Webroot
The platform to be providing a website building service
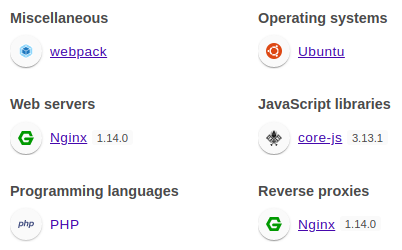 Wappalyzer identified technologies involved.
The web application is written in PHP
Wappalyzer identified technologies involved.
The web application is written in PHP
 While there is a input form in the Contact us section at the bottom, it is not functional
While there is a input form in the Contact us section at the bottom, it is not functional
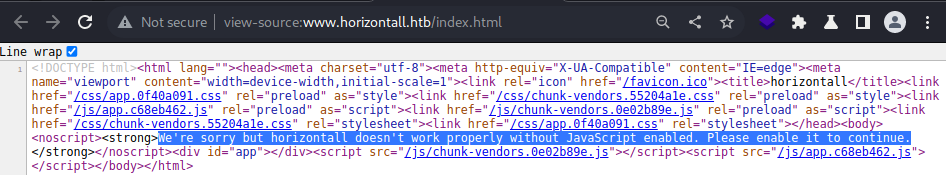 The source code has some interesting information that the web application requires JavaScript enabled.
The source code has some interesting information that the web application requires JavaScript enabled.
 and it points to this JS file
and it points to this JS file
app.c68eb462.js
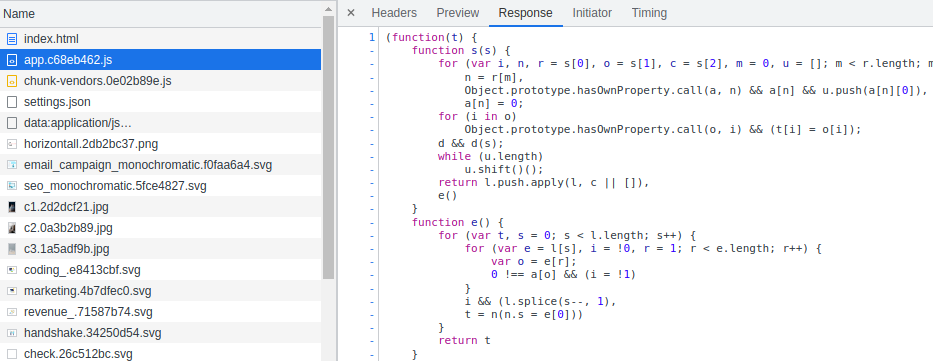 Checking the source code of the JS file through the dev mode reveals some information
Checking the source code of the JS file through the dev mode reveals some information
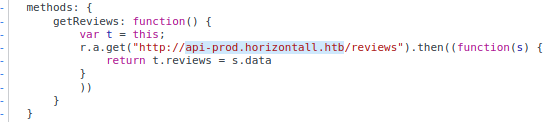 One of the function is pointing to a sub-domain / virtual host;
One of the function is pointing to a sub-domain / virtual host; apt-prod.horizontall.htb
Based on the naming, I’d assume that this is the production endpoint for the application API
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/horizontall]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -u http://horizontall.htb/FUZZ -ic -e .php,.txt,.html
________________________________________________
:: Method : GET
:: URL : http://horizontall.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .txt .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
index.html [status: 200, Size: 901, Words: 43, Lines: 2, Duration: 94ms]
img [status: 301, Size: 194, Words: 7, Lines: 8, Duration: 93ms]
css [status: 301, Size: 194, Words: 7, Lines: 8, Duration: 96ms]
js [status: 301, Size: 194, Words: 7, Lines: 8, Duration: 92ms]
:: Progress: [882188/882188] :: Job [1/1] :: 430 req/sec :: Duration: [0:34:48] :: Errors: 0 ::It’s empty as far as the word list covered.
I will fuzz for virtual host / sub-domain as they could be more.
Virtual Host / sub-domain discovery
┌──(kali㉿kali)-[~/archive/htb/labs/horizontall]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://$IP/ -H 'Host: FUZZ.horizontall.htb' -fs 194
________________________________________________
:: Method : GET
:: URL : http://10.10.11.105/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.horizontall.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 194
________________________________________________
www [Status: 200, Size: 901, Words: 43, Lines: 2, Duration: 97ms]
api-prod [Status: 200, Size: 413, Words: 76, Lines: 20, Duration: 121ms]
:: Progress: [114441/114441] :: Job [1/1] :: 427 req/sec :: Duration: [0:04:30] :: Errors: 0 ::ffuf found 2 virtual hosts / sub-domains; www.horizontall.htb and api-prod.horizontall.htb
api-prod.horizontall.htb was already discovered by checking the source code of the JS file earlier
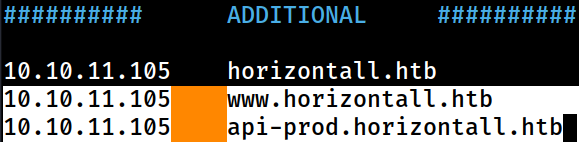 Those have been appended to the
Those have been appended to the /etc/hosts file on Kali for local DNS resolution
www.horizontall.htb
┌──(kali㉿kali)-[~/archive/htb/labs/horizontall]
└─$ curl -s http://www.horizontall.htb/
<!DOCTYPE html><html lang=""><head><meta charset="utf-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width,initial-scale=1"><link rel="icon" href="/favicon.ico"><title>horizontall</title><link href="/css/app.0f40a091.css" rel="preload" as="style"><link href="/css/chunk-vendors.55204a1e.css" rel="preload" as="style"><link href="/js/app.c68eb462.js" rel="preload" as="script"><link href="/js/chunk-vendors.0e02b89e.js" rel="preload" as="script"><link href="/css/chunk-vendors.55204a1e.css" rel="stylesheet"><link href="/css/app.0f40a091.css" rel="stylesheet"></head><body><noscript><strong>We're sorry but horizontall doesn't work properly without JavaScript enabled. Please enable it to continue.</strong></noscript><div id="app"></div><script src="/js/chunk-vendors.0e02b89e.js"></script><script src="/js/app.c68eb462.js"></script></body></html>
┌──(kali㉿kali)-[~/archive/htb/labs/horizontall]
└─$ curl -s http://horizontall.htb/
<!DOCTYPE html><html lang=""><head><meta charset="utf-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width,initial-scale=1"><link rel="icon" href="/favicon.ico"><title>horizontall</title><link href="/css/app.0f40a091.css" rel="preload" as="style"><link href="/css/chunk-vendors.55204a1e.css" rel="preload" as="style"><link href="/js/app.c68eb462.js" rel="preload" as="script"><link href="/js/chunk-vendors.0e02b89e.js" rel="preload" as="script"><link href="/css/chunk-vendors.55204a1e.css" rel="stylesheet"><link href="/css/app.0f40a091.css" rel="stylesheet"></head><body><noscript><strong>We're sorry but horizontall doesn't work properly without JavaScript enabled. Please enable it to continue.</strong></noscript><div id="app"></div><script src="/js/chunk-vendors.0e02b89e.js"></script><script src="/js/app.c68eb462.js"></script></body></html>www.horizontall.htb is virtually no different than horizontall.htb
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/horizontall]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://www.horizontall.htb/FUZZ -ic -e .php,.txt,.html
________________________________________________
:: Method : GET
:: URL : http://www.horizontall.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .txt .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
index.html [Status: 200, Size: 901, Words: 43, Lines: 2, Duration: 95ms]
img [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 93ms]
css [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 93ms]
js [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 93ms]
:: Progress: [882188/882188] :: Job [1/1] :: 428 req/sec :: Duration: [0:34:18] :: Errors: 0 ::no difference from horizontal.htb
Moving on
api-prod.horizontall.htb
 Webroot
It just says Welcome.
Webroot
It just says Welcome.
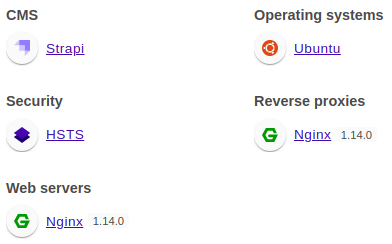 Wappalyzer identified technologies involved
while it uses hsts for security, It’s important to note that it is Strapi, which means that it’s a Node.js application
strapi is a free and open-source headless CMS (Content Management System) that allows developers to easily create and manage APIs and content for their applications. It provides a flexible and customizable admin panel for managing content, and supports various databases including MongoDB, PostgreSQL, and MySQL. Strapi is built on top of Node.js and uses GraphQL or RESTful APIs to communicate with applications. With Strapi, developers can create API-driven projects more efficiently and focus on developing features, rather than spending time on creating an API from scratch. It is a popular choice for building scalable, modular, and fast web applications.
Wappalyzer identified technologies involved
while it uses hsts for security, It’s important to note that it is Strapi, which means that it’s a Node.js application
strapi is a free and open-source headless CMS (Content Management System) that allows developers to easily create and manage APIs and content for their applications. It provides a flexible and customizable admin panel for managing content, and supports various databases including MongoDB, PostgreSQL, and MySQL. Strapi is built on top of Node.js and uses GraphQL or RESTful APIs to communicate with applications. With Strapi, developers can create API-driven projects more efficiently and focus on developing features, rather than spending time on creating an API from scratch. It is a popular choice for building scalable, modular, and fast web applications.
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/horizontall]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://api-prod.horizontall.htb/FUZZ -ic -e .php,.txt,.html
________________________________________________
:: Method : GET
:: URL : http://api-prod.horizontall.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .txt .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
index.html [Status: 200, Size: 413, Words: 76, Lines: 20, Duration: 186ms]
reviews [Status: 200, Size: 507, Words: 21, Lines: 1, Duration: 121ms]
users [Status: 403, Size: 60, Words: 1, Lines: 1, Duration: 118ms]
admin [Status: 200, Size: 854, Words: 98, Lines: 17, Duration: 103ms]
robots.txt [Status: 200, Size: 121, Words: 19, Lines: 4, Duration: 95ms]
:: Progress: [882188/882188] :: Job [1/1] :: 422 req/sec :: Duration: [0:35:52] :: Errors: 0 ::Fuzzing the web root indeed reveals some additional files and directories, one of which are already known; /reviews
/robots.txt
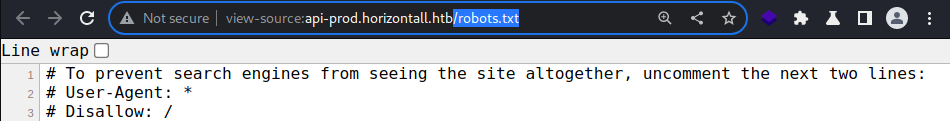 The
The robots.txt file doesn’t contain anything useful
/reviews
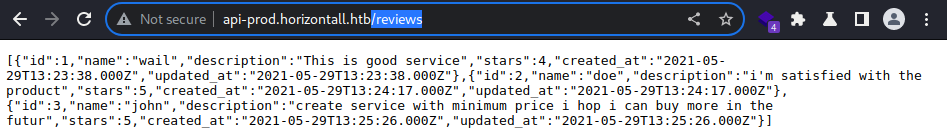 While it is obvious to assume that
While it is obvious to assume that /reviews likely is mapped to the review section of the web application, the content is a single JSON array containing 3 JSON objects.
Each object represents a review of a service or product and contains the same set of keys: “id”, “name”, “description”, “stars”, “created_at”, and “updated_at”
wail, doe, and john are potential usernames
/admin
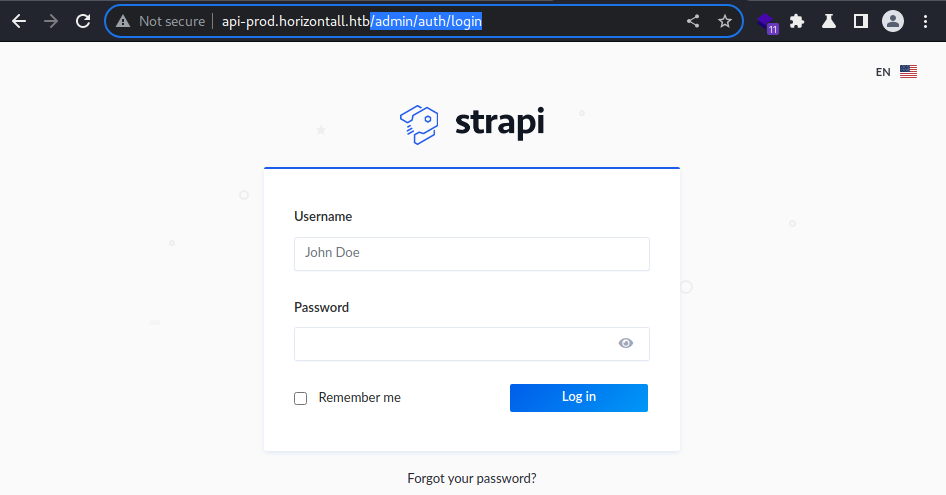 Browsing to
Browsing to /admin, I get redirected to a login page located at /admin/auth/login
it’s a login page to the strapi administrative panel
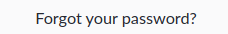
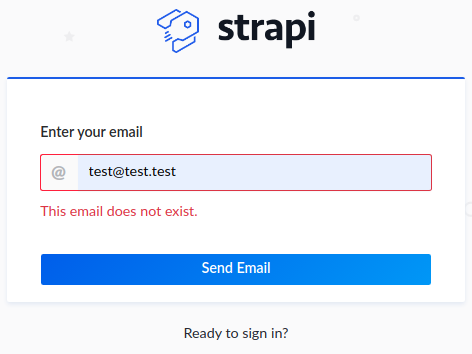 There is the Forgot your password? button leading to
There is the Forgot your password? button leading to /admin/auth/forgot-password
However, it requires a full registered email address
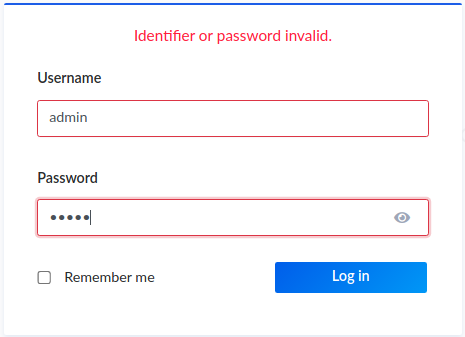 i tried default / weak credentials and none of them worked
i tried default / weak credentials and none of them worked
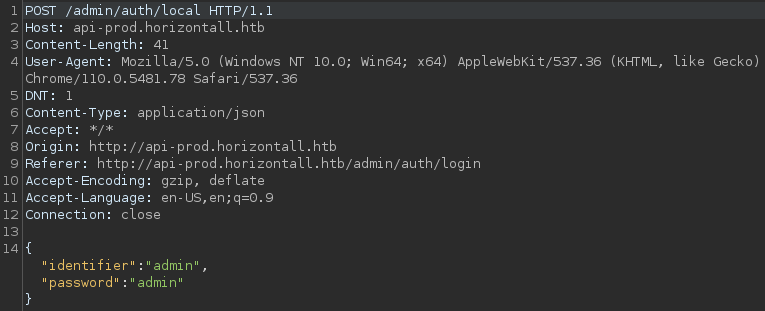 Intercepting the request reveals that It’s sending out POST request to
Intercepting the request reveals that It’s sending out POST request to /admin/auth/local with a JSON data
While I was unable to find a way bypass the authentication here. I found something else
Vulnerability
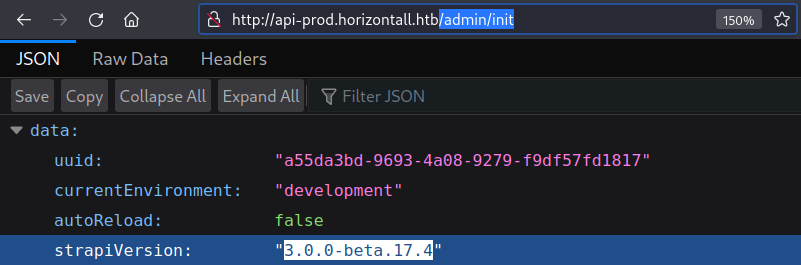 The endpoint located at
The endpoint located at /admin/init reveals the version information
The version is 3.0.0-beta.17.4
┌──(kali㉿kali)-[~/archive/htb/labs/horizontall]
└─$ searchsploit 3.0.0-beta.17.4
------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------ ---------------------------------
Strapi CMS 3.0.0-beta.17.4 - Remote Code Execution (RCE) (Unauthenticated) | multiple/webapps/50239.py
Strapi CMS 3.0.0-beta.17.4 - Set Password (Unauthenticated) (Metasploit) | nodejs/webapps/50716.rb
------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No ResultsStrapi CMS 3.0.0-beta.17.4 is suffering from a form of RCE vulnerability that doesn’t require any authentication
Looking further into it, I found out that the Python script shown above chains both [[Horizontall_CVE-2019-18818#CVE-2019-18818|CVE-2019-18818]] and [[Horizontall_CVE-2019-19609#CVE-2019-19609|CVE-2019-19609]]