Web
Nmap discovered a Web server on the target port 80
The running service is Microsoft IIS httpd 10.0
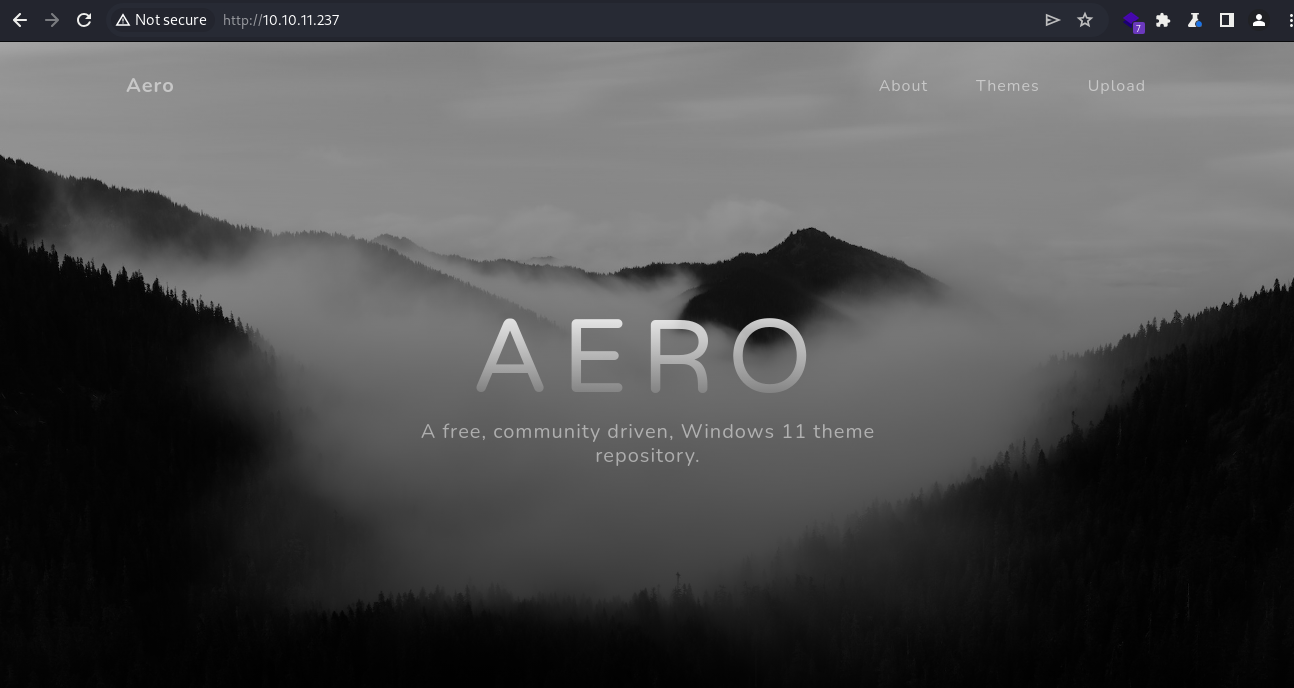 Webroot
It claims to be a Windows 11 theme repository
Webroot
It claims to be a Windows 11 theme repository
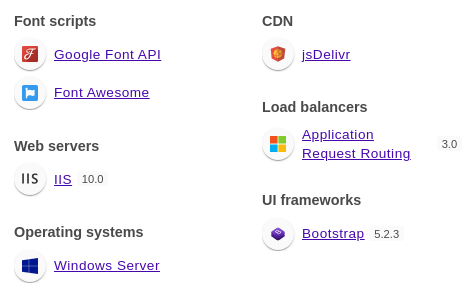 Wappalyzer identified technologies involved
Interestingly, it uses
Wappalyzer identified technologies involved
Interestingly, it uses Application Request Routing (ARR) 3.0 extension for load balancing
About
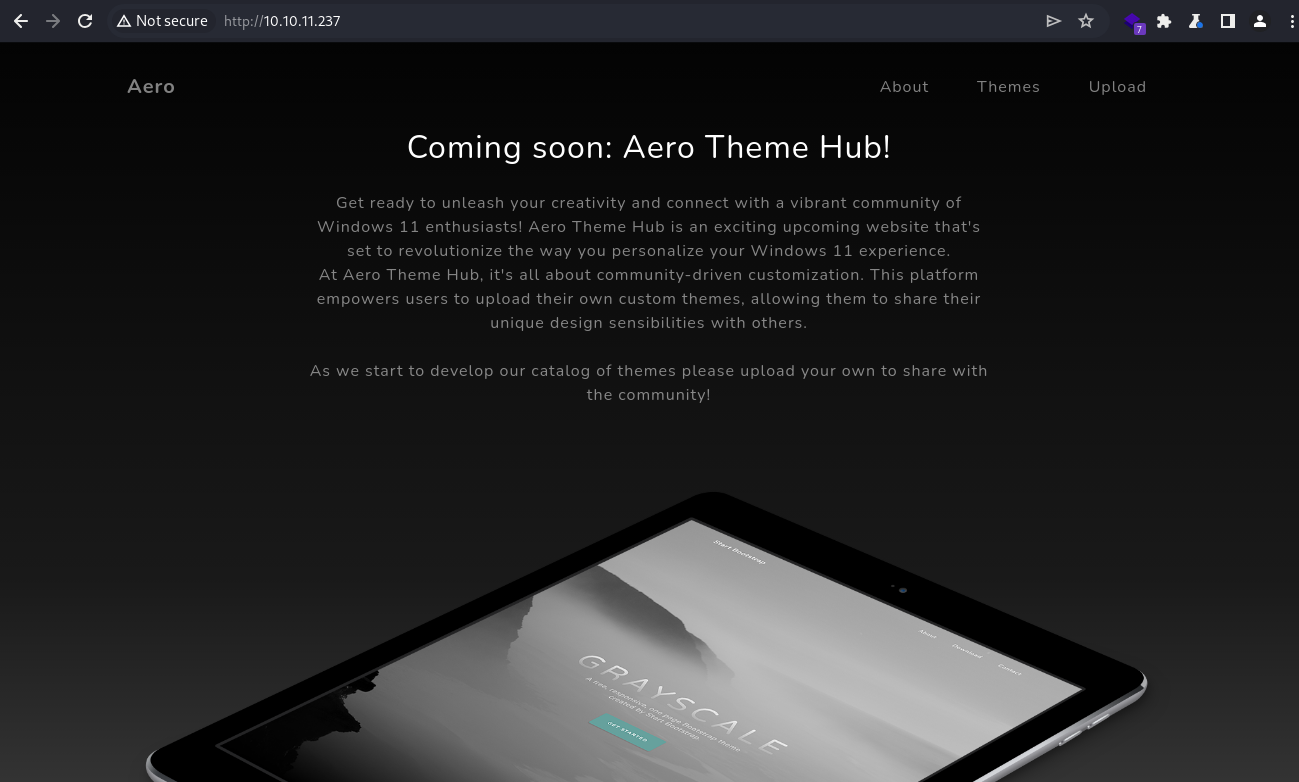 The “About” section states that the website is a community-driven hub for sharing Windows 11 themes
The “About” section states that the website is a community-driven hub for sharing Windows 11 themes
Themes
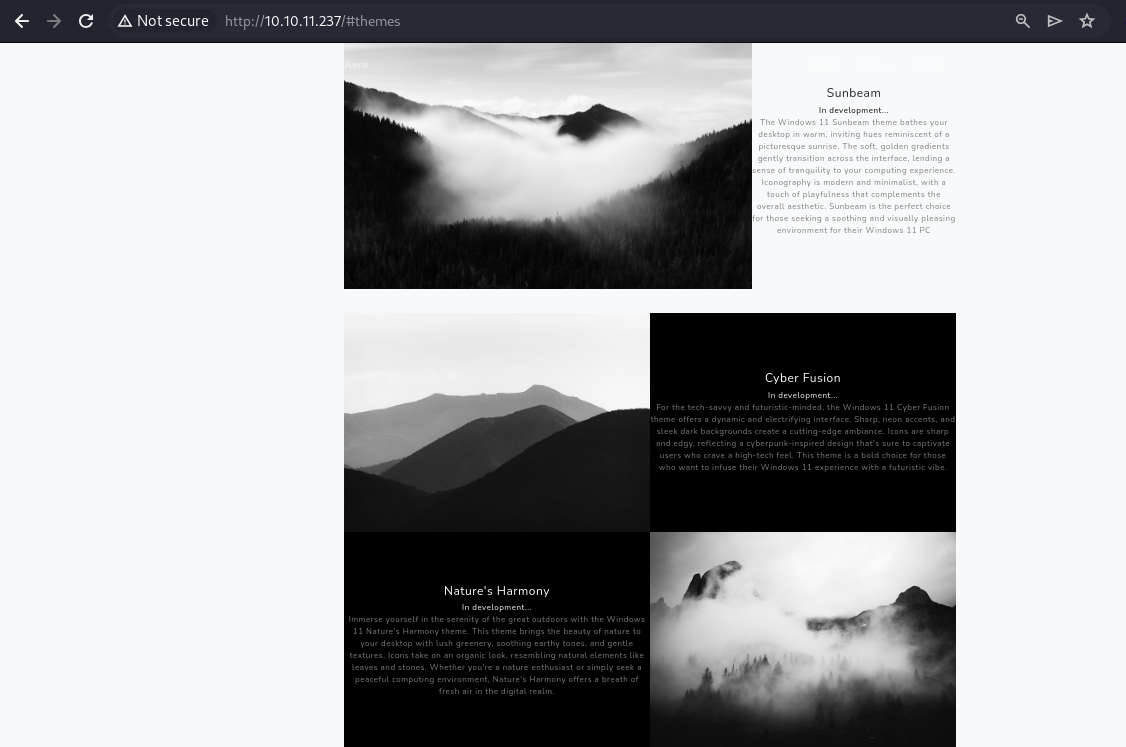 The “Themes” section showcases 3 themes that are still in development
The “Themes” section showcases 3 themes that are still in development
Upload
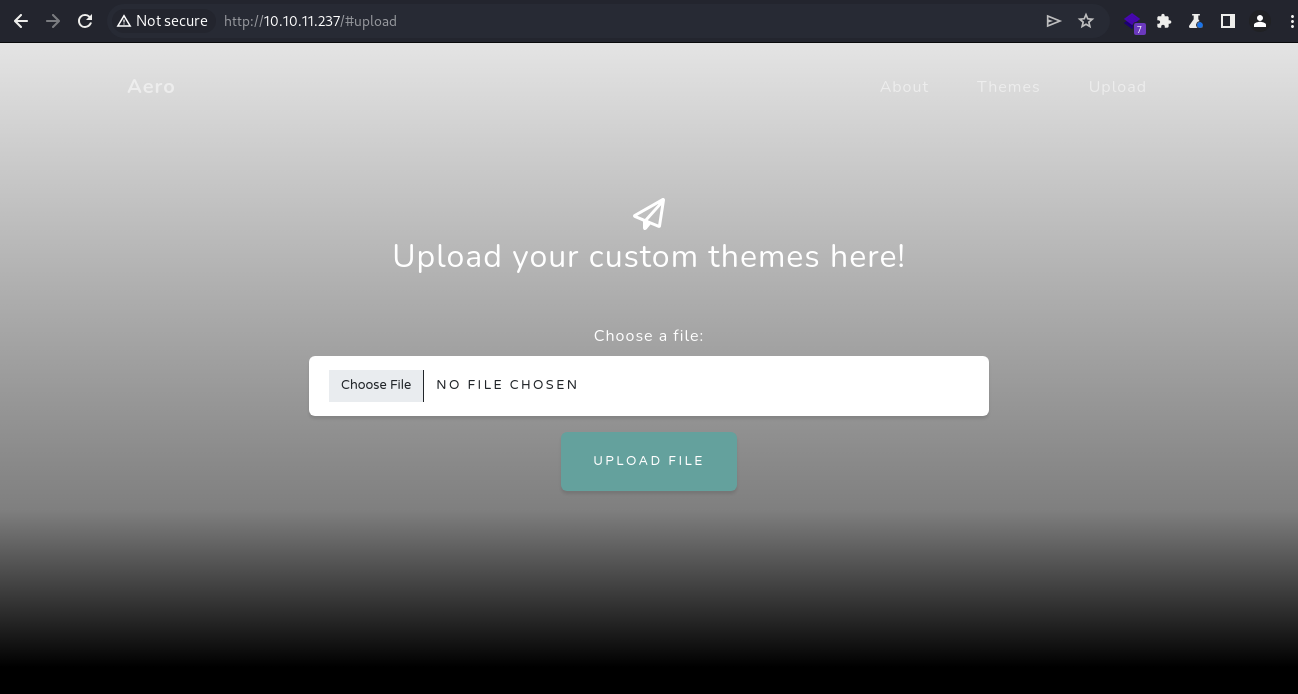 Most importantly, there is an “Upload” section that supports file upload
Presumably, custom Windows 11 themes are supposed to be uploaded here as this is the “hub” for sharing
Most importantly, there is an “Upload” section that supports file upload
Presumably, custom Windows 11 themes are supposed to be uploaded here as this is the “hub” for sharing
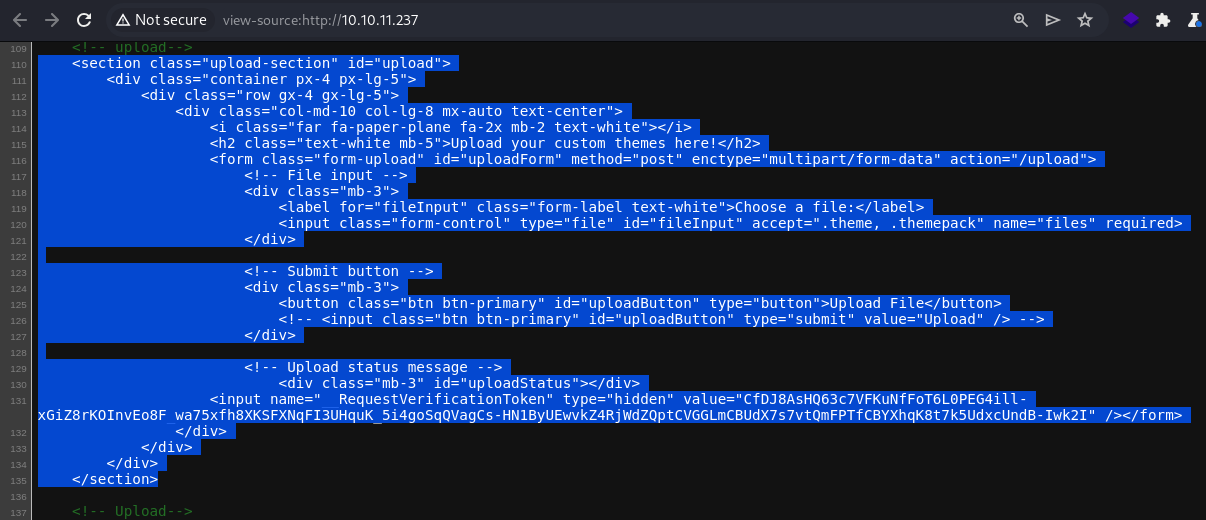 Checking the source code reveals the file upload feature
It accepts
Checking the source code reveals the file upload feature
It accepts .theme and .themepack extensions
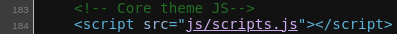 It also loads a JS file at
It also loads a JS file at js/scripts.js
js/scripts.js
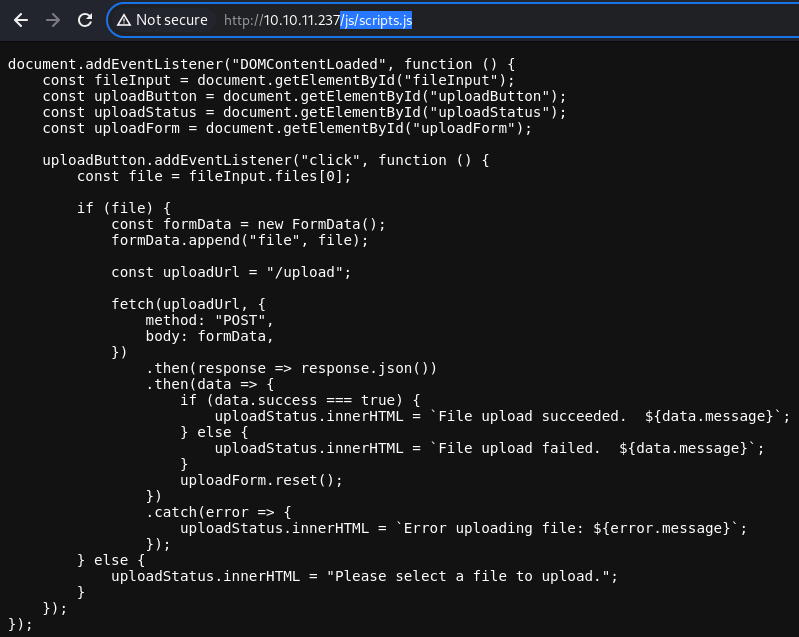 It would appear that the POST request from the file upload feature above is made to the
It would appear that the POST request from the file upload feature above is made to the /upload endpoint
┌──(kali㉿kali)-[~/archive/htb/labs/aero]
└─$ curl -s -i http://10.10.11.237/upload
HTTP/1.1 405 Method Not Allowed
allow: POST
content-length: 0
server: Microsoft-IIS/10.0
x-powered-by: ARR/3.0
date: Tue, 16 Jan 2024 07:41:00 GMT
┌──(kali㉿kali)-[~/archive/htb/labs/aero]
└─$ curl -x post -s -i http://10.10.11.237/upload
HTTP/1.1 411 Length Required
content-type: text/html; charset=us-ascii
server: Microsoft-HTTPAPI/2.0
date: Tue, 16 Jan 2024 07:41:08 GMT
connection: close
content-length: 344The /upload endpoint only accepts POST method and requires length
testing
┌──(kali㉿kali)-[~/archive/htb/labs/aero]
└─$ echo blahblah > test.themeI will first create a testing file; test.theme
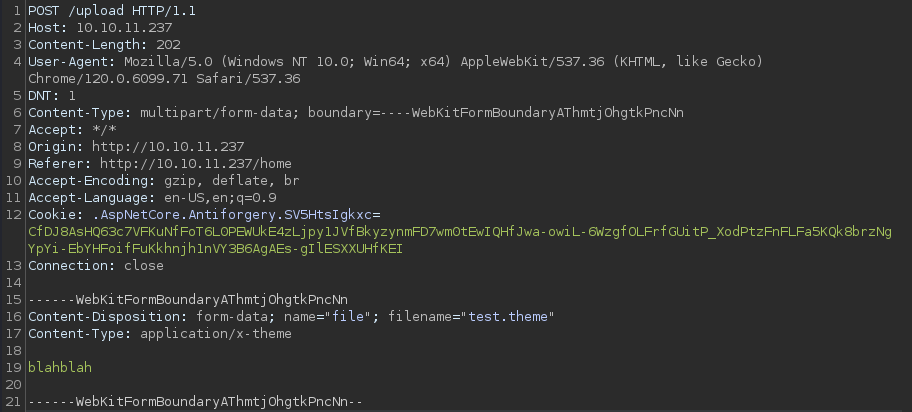
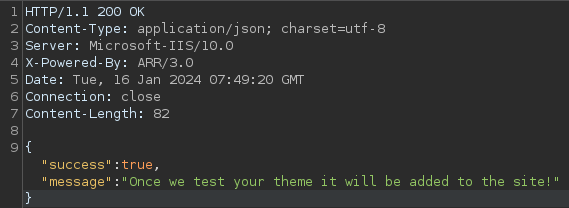
 Upon submitting the test file, the web server provided a JSON response, indicating that the uploaded file or “theme” would be incorporated into the website following a testing process
Upon submitting the test file, the web server provided a JSON response, indicating that the uploaded file or “theme” would be incorporated into the website following a testing process
The duration of this process is unspecified, but it can be inferred that the backend is likely undergoing a series of file executions for testing purposes.
Since the system exclusively handles .theme and .themepack files, it is evident that the testing revolves around Windows 11 themes.
Vulnerability
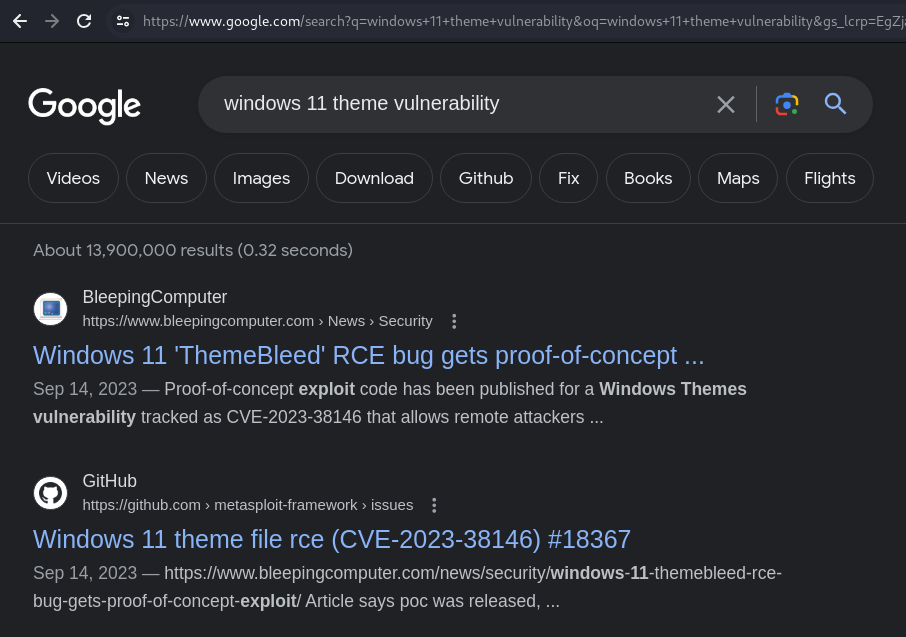 Looking up online for Windows 11 theme vulnerability reveals an interesting entry named, ThemeBleed, or [[Aero_CVE-2023-38146#[CVE-2023-38146](https //nvd.nist.gov/vuln/detail/CVE-2023-38146)|CVE-2023-38146]]
The target system might be vulnerable
Looking up online for Windows 11 theme vulnerability reveals an interesting entry named, ThemeBleed, or [[Aero_CVE-2023-38146#[CVE-2023-38146](https //nvd.nist.gov/vuln/detail/CVE-2023-38146)|CVE-2023-38146]]
The target system might be vulnerable
Footer
 The footer contains a potential username,
The footer contains a potential username, support, along with a domain; aerohub.htb
 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resolution
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/aero]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-lowercase-2.3-medium.txt -t 200 -u http://$IP/FUZZ -ic -ic
________________________________________________
:: Method : GET
:: URL : http://10.10.11.237/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[status: 200, Size: 11650, Words: 3468, Lines: 187, Duration: 86ms]
home [status: 200, Size: 11650, Words: 3468, Lines: 187, Duration: 141ms]
upload [status: 405, Size: 0, Words: 1, Lines: 1, Duration: 107ms]
:: Progress: [207630/207630] :: Job [1/1] :: 875 req/sec :: Duration: [0:02:59] :: Errors: 0 ::Nothing new
Virtual Host / Sub-domain Discovery
┌──(kali㉿kali)-[~/archive/htb/labs/aero]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -t 200 -u http://$IP/ -H 'Host: FUZZ.aerohub.htb' -ic -mc all -fs 11650
________________________________________________
:: Method : GET
:: URL : http://10.10.11.237/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.aerohub.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: all
:: Filter : Response size: 11650
________________________________________________
:: Progress: [114437/114437] :: Job [1/1] :: 314 req/sec :: Duration: [0:05:54] :: Errors: 0 ::Nothing found