IPMI
Nmap discovered an unknown service on the target port 623
It initially claimed to be asf-rmcp
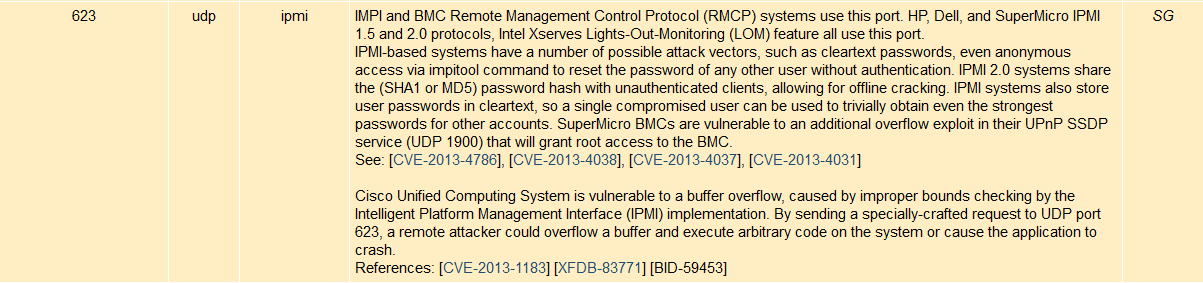 checking the port online reveals that UDP port
checking the port online reveals that UDP port 623 is mostly used by IPMI service
Intelligent Platform Management Interface (IPMI) is a protocol that provides remote management and monitoring capabilities for servers and computing systems. It allows administrators to monitor the health of hardware components like temperature, fan speed, and power supply, even when the system is not fully operational. IPMI can be used to remotely control system power, view system event logs, and manage firmware updates. It is a standardized protocol used by many server vendors, making it a widely adopted solution for remote system management. IPMI can enhance system reliability and reduce downtime by allowing administrators to proactively monitor and manage system health.
┌──(kali㉿kali)-[~/archive/htb/labs/shibboleth]
└─$ sudo nmap -sU --script ipmi-version -p623 $IP
starting nmap 7.93 ( https://nmap.org ) at 2023-04-17 18:01 CEST
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.093s latency).
PORT STATE SERVICE VERSION
623/udp open asf-rmcp
| ipmi-version:
| version:
| IPMI-2.0
| userauth: password, md5, md2, null
| passauth: auth_msg, auth_user, non_null_user
|_ level: 1.5, 2.0
service detection performed. please report any incorrect results at https://nmap.org/submit/ .
nmap done: 1 IP address (1 host up) scanned in 5.73 secondsPerforming an additional Nmap script scan on the port 632 indeed confirms the IPMI service
It seems to be running IPMI-2.0 while allowing both version 1.5 and 2.0 for authentication
As shown above earlier, IMPI version 2.0 is known for its vulnerabilities
Vulnerability
┌──(kali㉿kali)-[~/archive/htb/labs/shibboleth]
└─$ sudo nmap -sU --script ipmi-* -p623 $IP
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-17 17:54 CEST
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.094s latency).
PORT STATE SERVICE VERSION
623/udp open asf-rmcp
| ipmi-brute:
| Accounts: No valid accounts found
|_ Statistics: Performed 50009 guesses in 487 seconds, average tps: 102.4
| ipmi-cipher-zero:
| VULNERABLE:
| IPMI 2.0 RAKP Cipher Zero Authentication Bypass
| State: VULNERABLE
| Risk factor: High
|
| The issue is due to the vendor shipping their devices with the
| cipher suite '0' (aka 'cipher zero') enabled. This allows a
| remote attacker to authenticate to the IPMI interface using
| an arbitrary password. The only information required is a valid
| account, but most vendors ship with a default 'admin' account.
| This would allow an attacker to have full control over the IPMI
| functionality
|
| References:
| https://www.us-cert.gov/ncas/alerts/TA13-207A
|_ http://fish2.com/ipmi/cipherzero.html
| ipmi-version:
| Version:
| IPMI-2.0
| UserAuth: password, md5, md2, null
| PassAuth: auth_msg, auth_user, non_null_user
|_ Level: 1.5, 2.0
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 493.01 secondsWhile Nmap failed to find a valid username, it appears that the target IMPI instance is vulnerable to IPMI 2.0 Cipher Zero Authentication Bypass, which is also known as [[Shibboleth_CVE-2013-4782#CVE-2013-4782|CVE-2013-4782]]
Additionally, since the target IMPI instance is the version 2.0, it may be vulnerable to [[Shibboleth_CVE-2013-4786#CVE-2013-4786|CVE-2013-4786]]